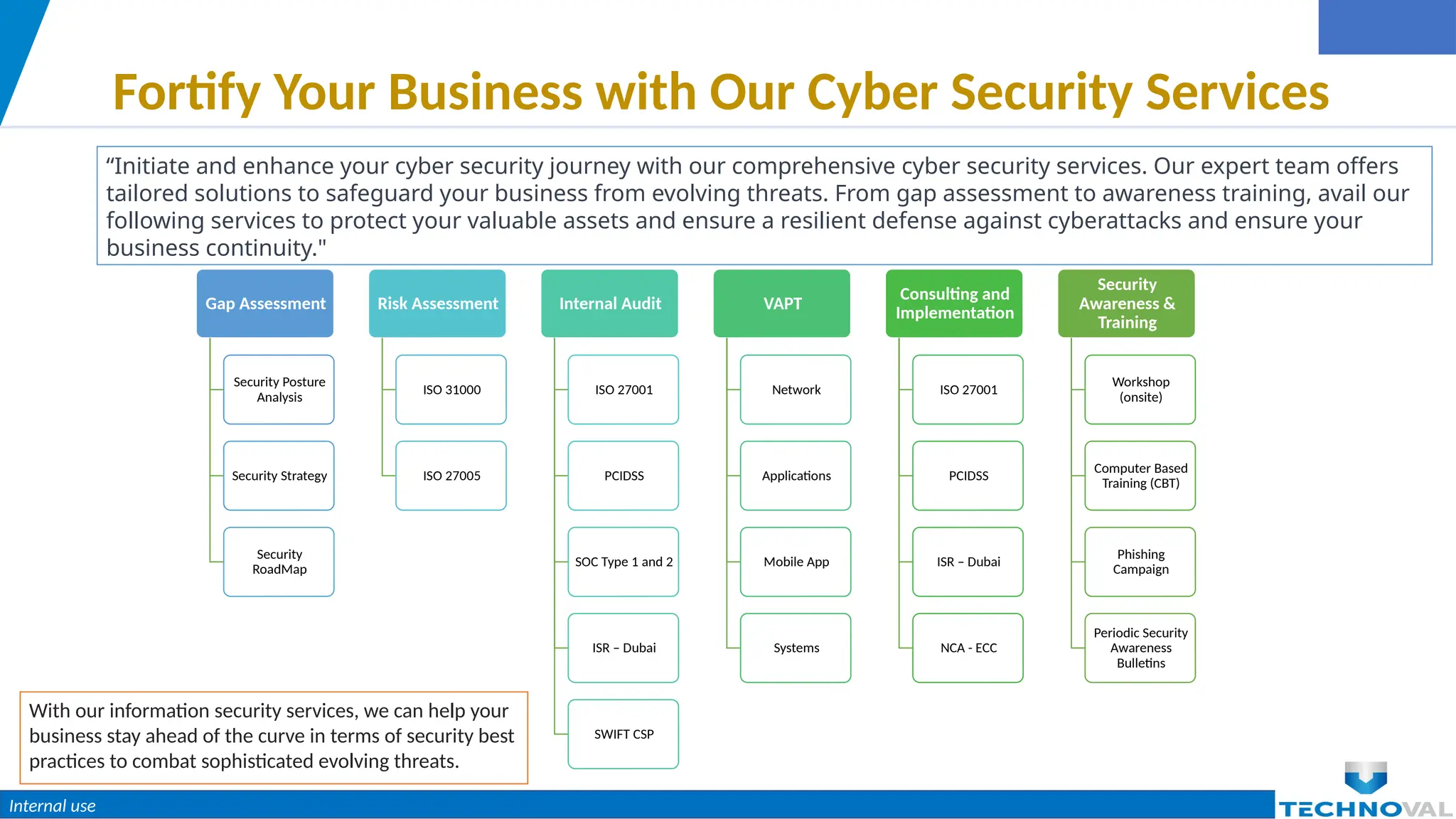
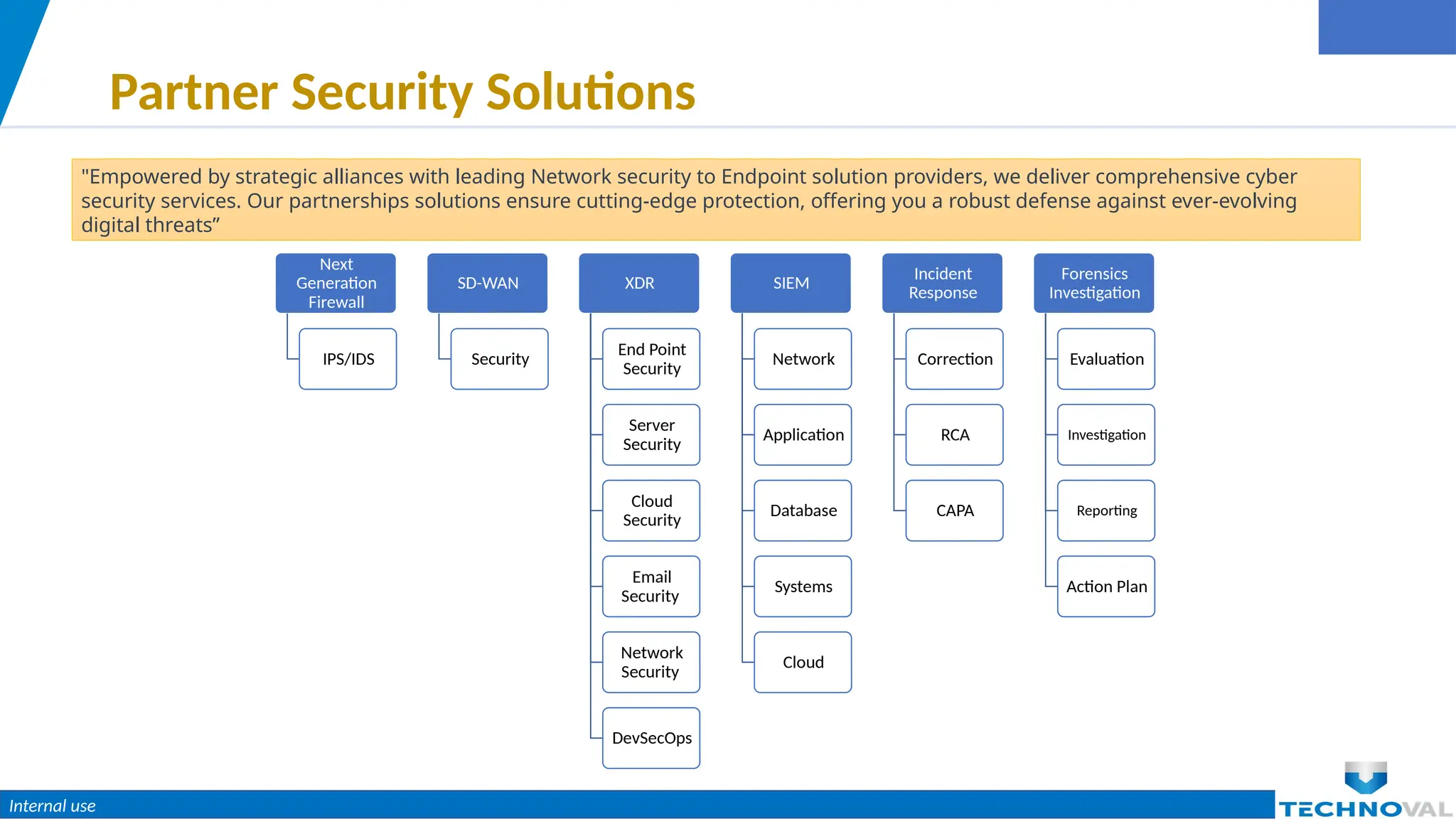
The document outlines the critical importance of cybersecurity for organizations in light of expanding digital threats, emphasizing the necessity of protecting sensitive data and maintaining customer trust. It addresses common myths about cybersecurity, details essential actions businesses should take (such as adopting a layered security approach and continuous monitoring), and highlights available cybersecurity services and solutions. The document concludes by encouraging proactive engagement with cybersecurity measures to guard against potential attacks.