This document summarizes Corda's cryptographic agility features:
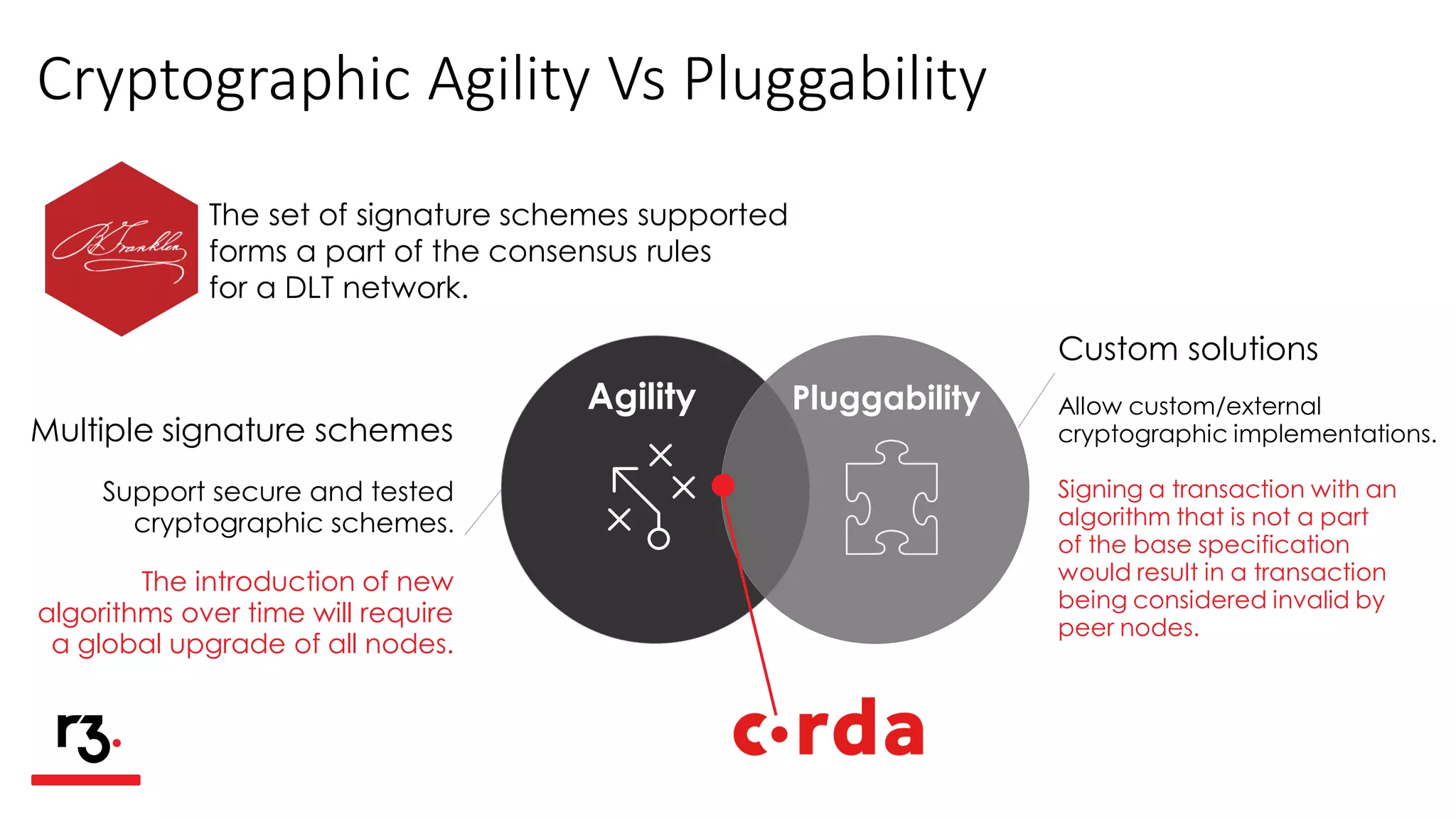
- Corda supports multiple signature schemes so it can adapt to new cryptographic standards over time without requiring a global upgrade. This allows "cryptographic agility".
- It also allows for custom cryptographic implementations through "pluggability" but custom algorithms that are not part of the base specification would result in invalid transactions.
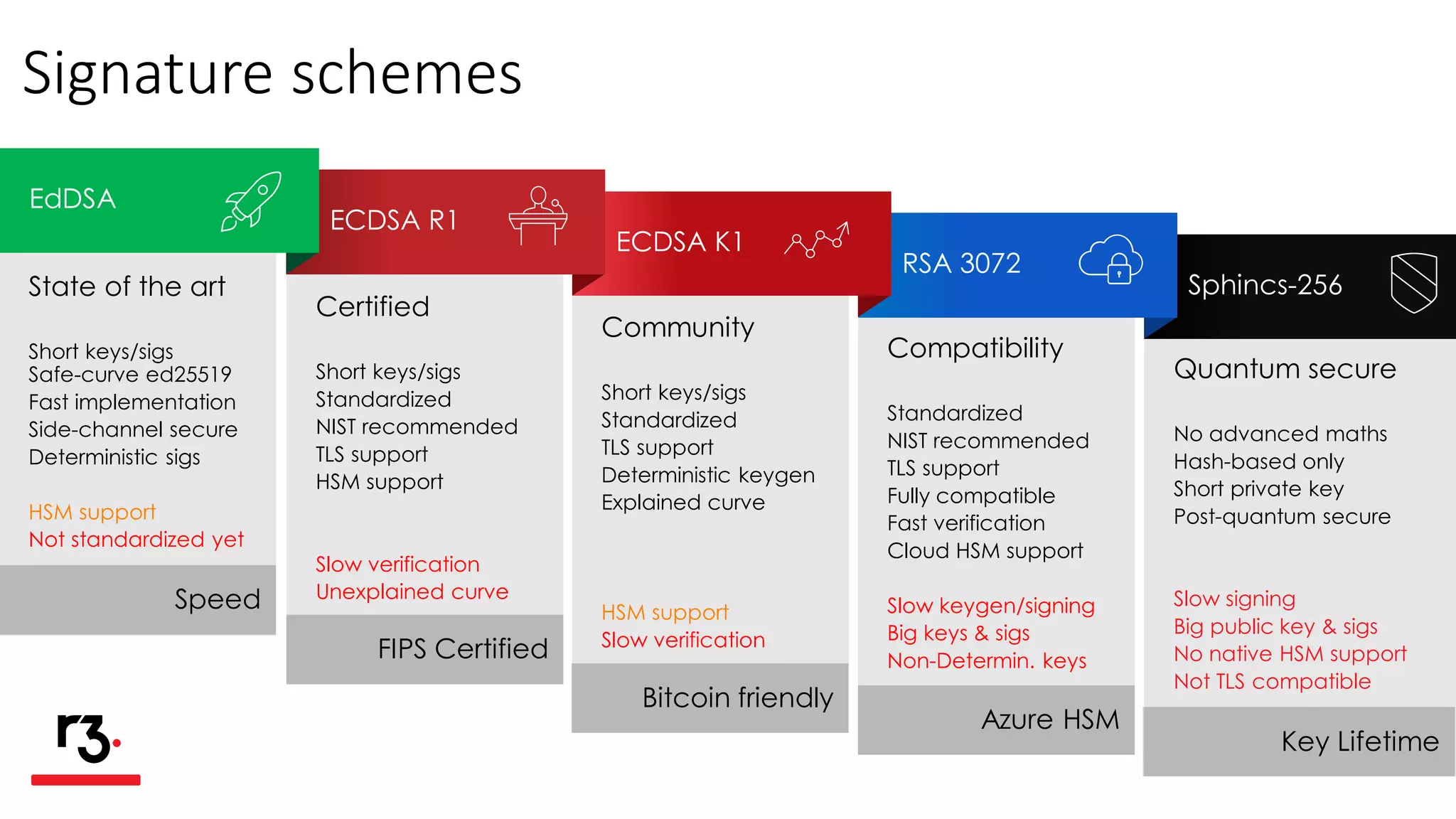
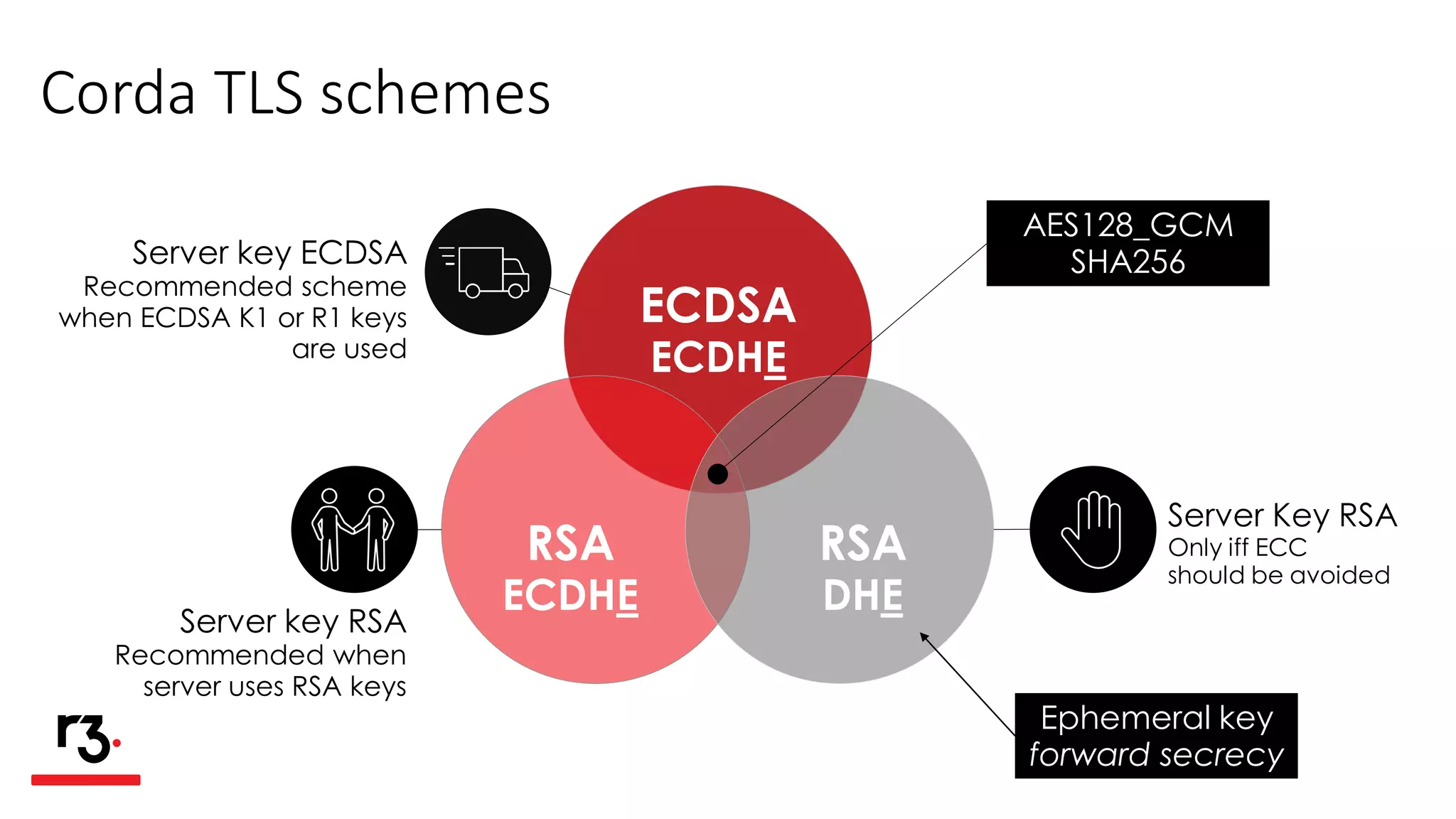
- The document discusses various signature schemes like RSA, ECDSA, and Sphincs-256 that Corda supports and their tradeoffs in terms of speed, security, and other factors. It provides recommendations on which schemes to use based on different criteria.















![[a][b][c]
ZKP
Create Circuit (logical gates)
Usually thousands of them
Convert each gate to R1CS
3 (sparse) vectors that satisfy a simple equation (dot products)
R1CS to Arithmetic Quadratic Program
dot product -> polynomials
Polynomials to EC points
+ using params from trusted setup
zkSNARK
01
02
03
05zkSNARK proof generation
04](https://image.slidesharecdn.com/nyccordameetup15052018-180517202103/75/Cryptographic-Agility-in-Corda-19-2048.jpg)












