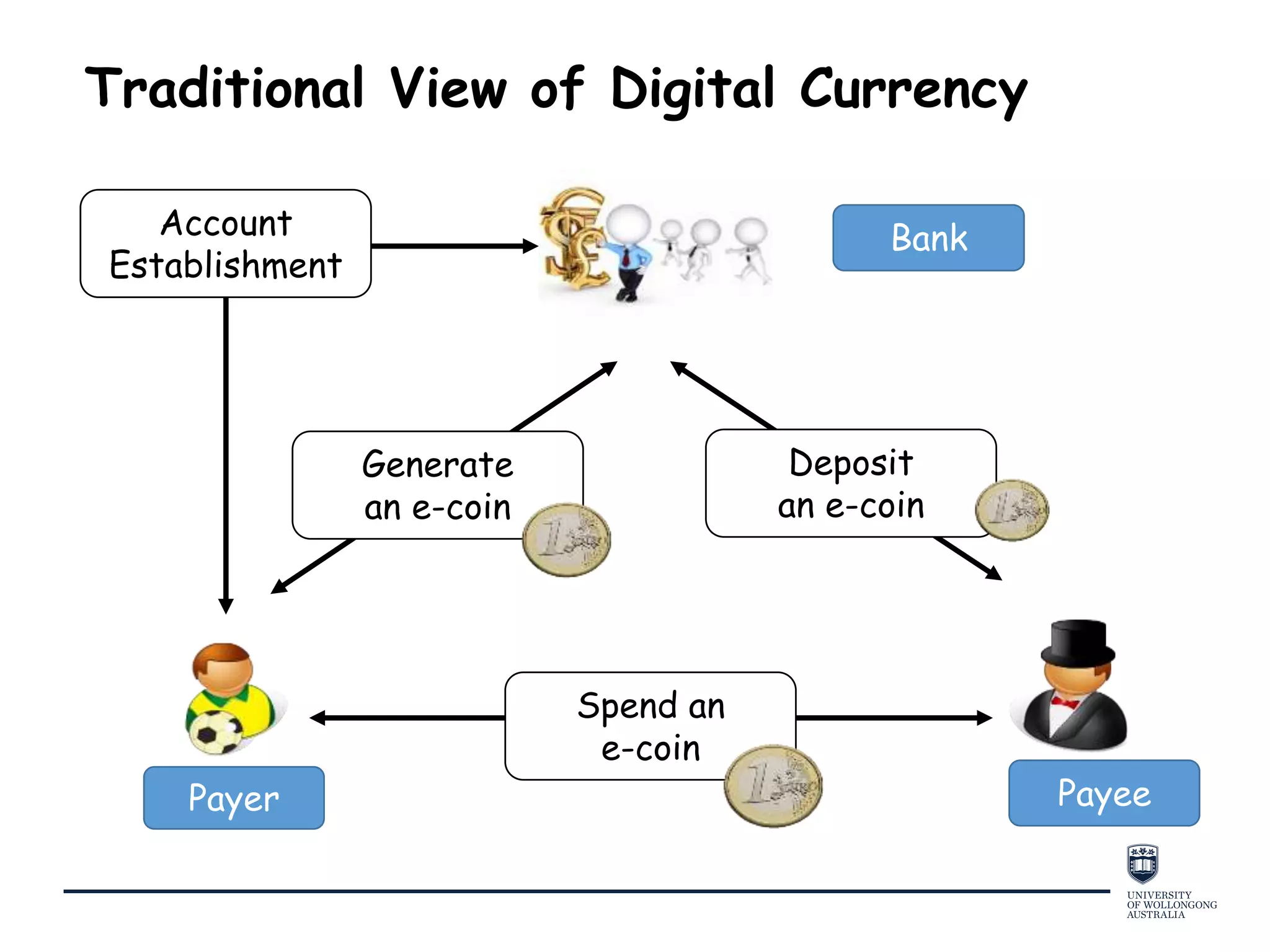
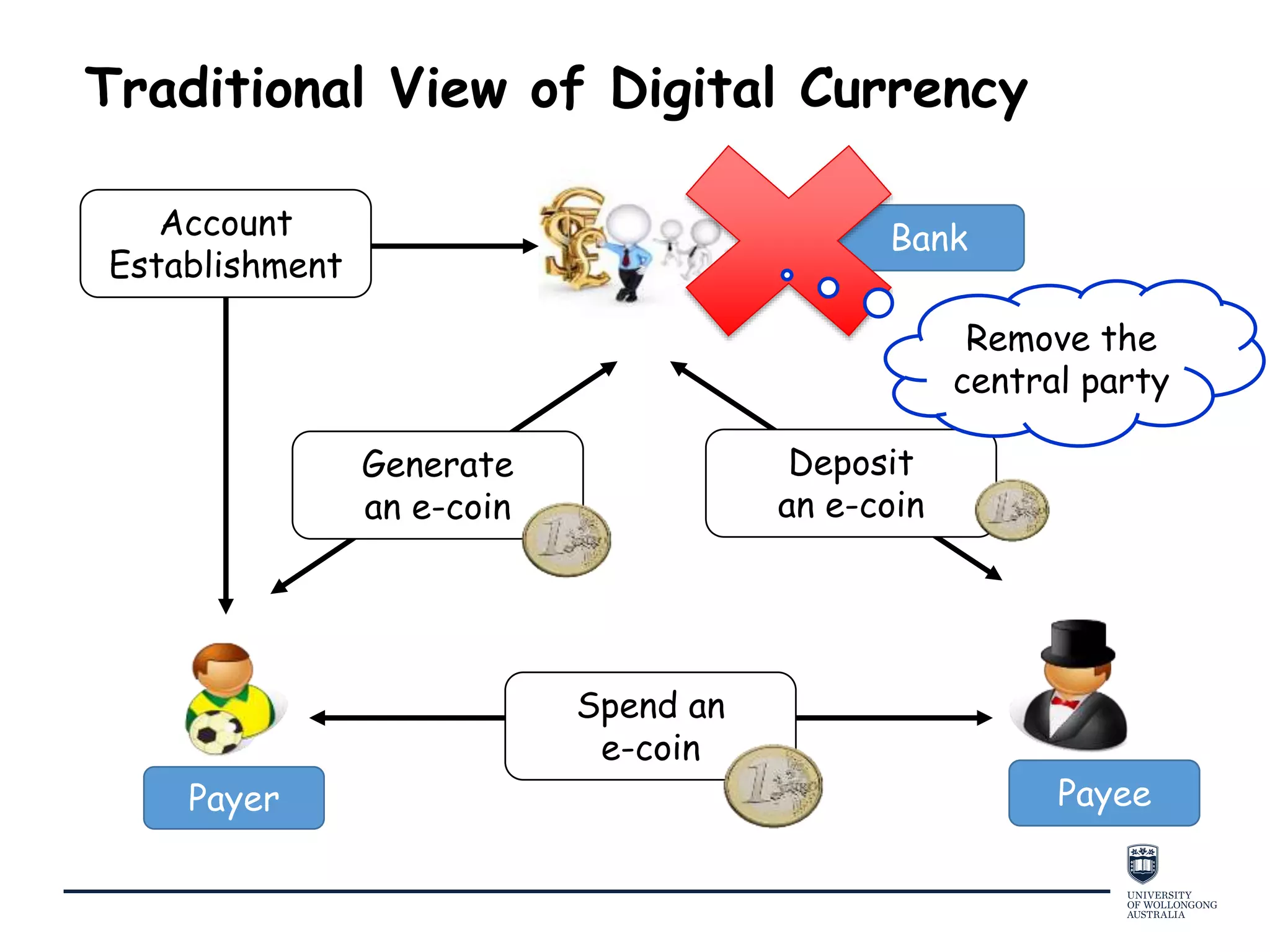
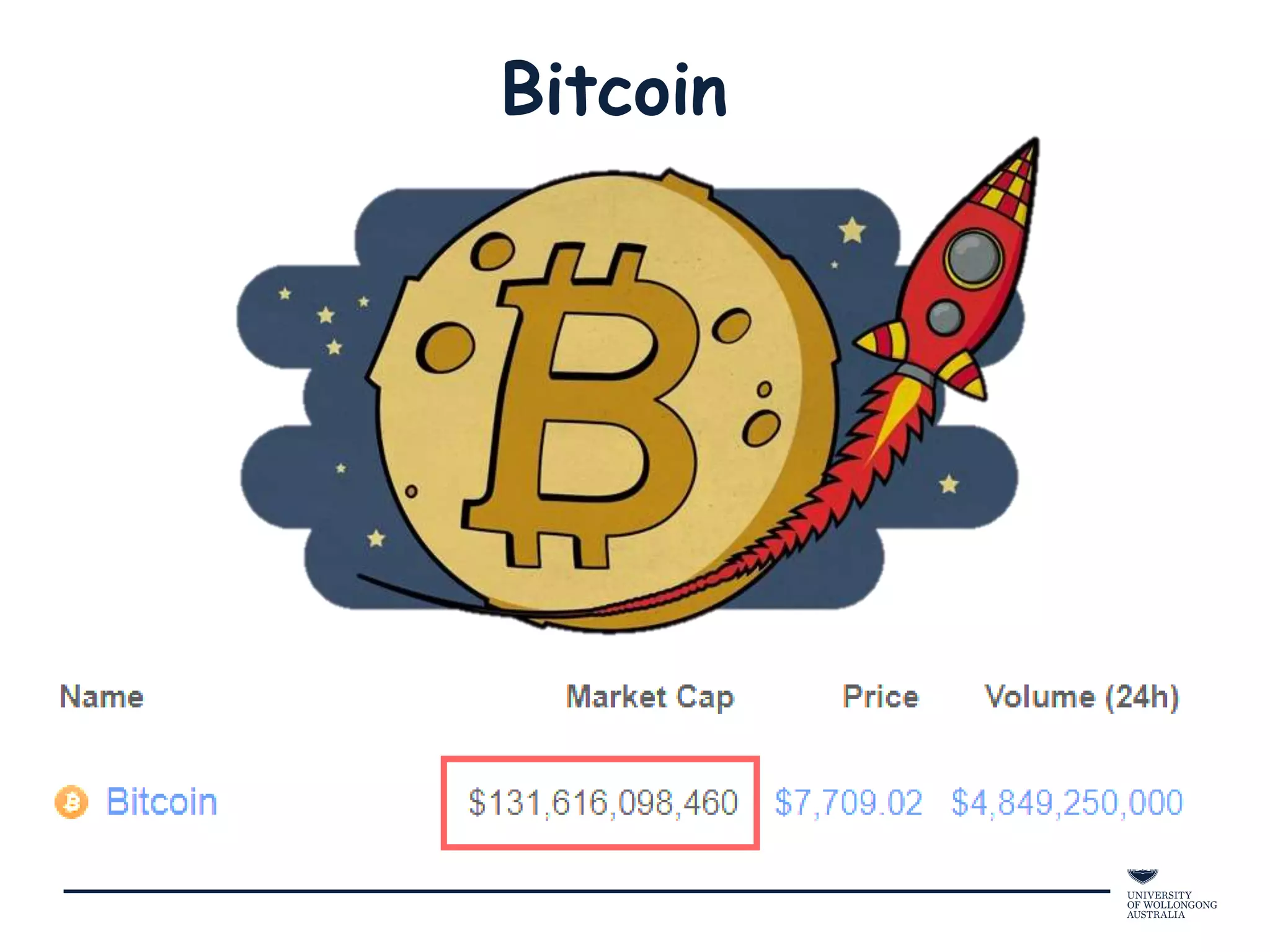
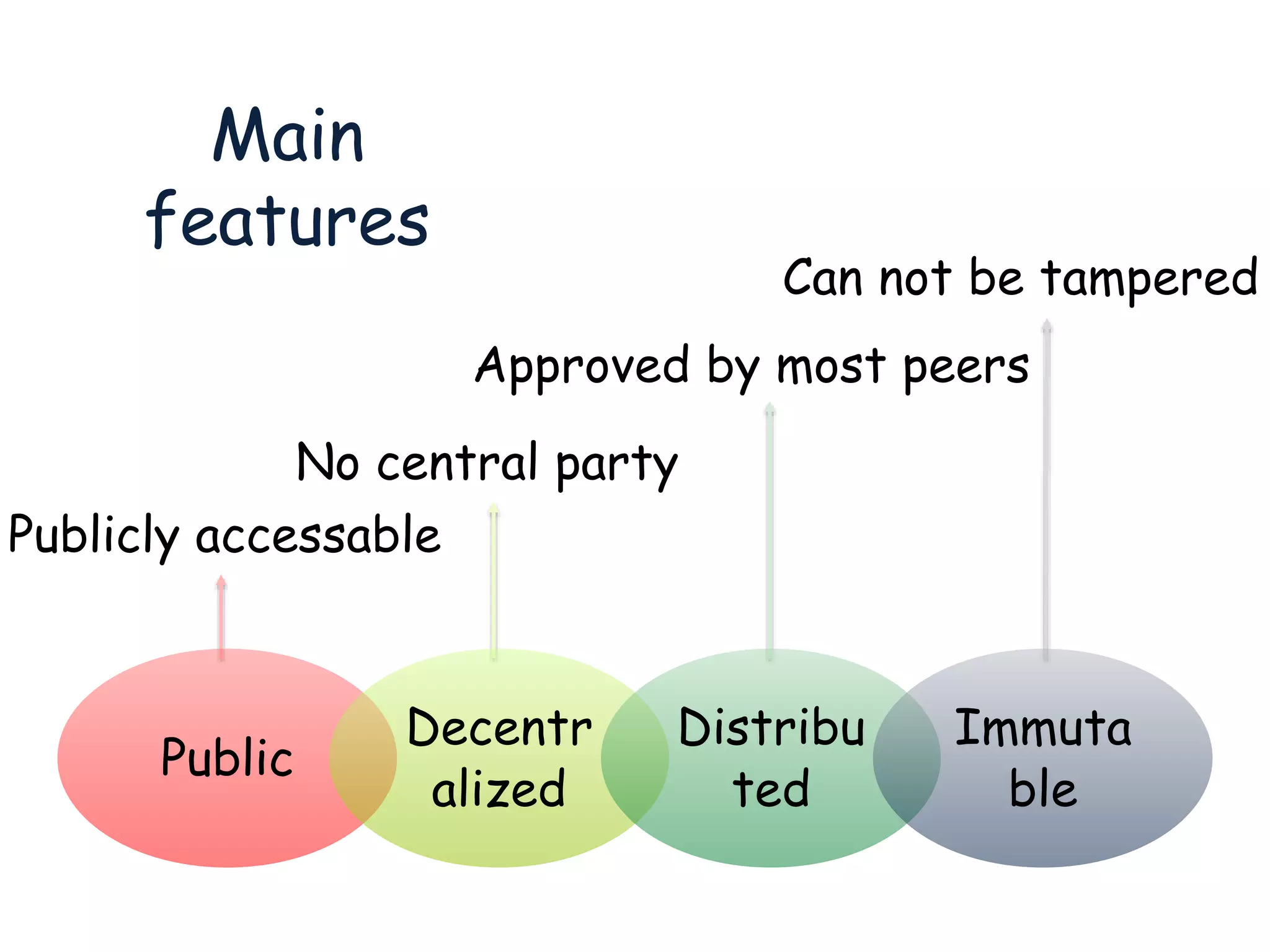
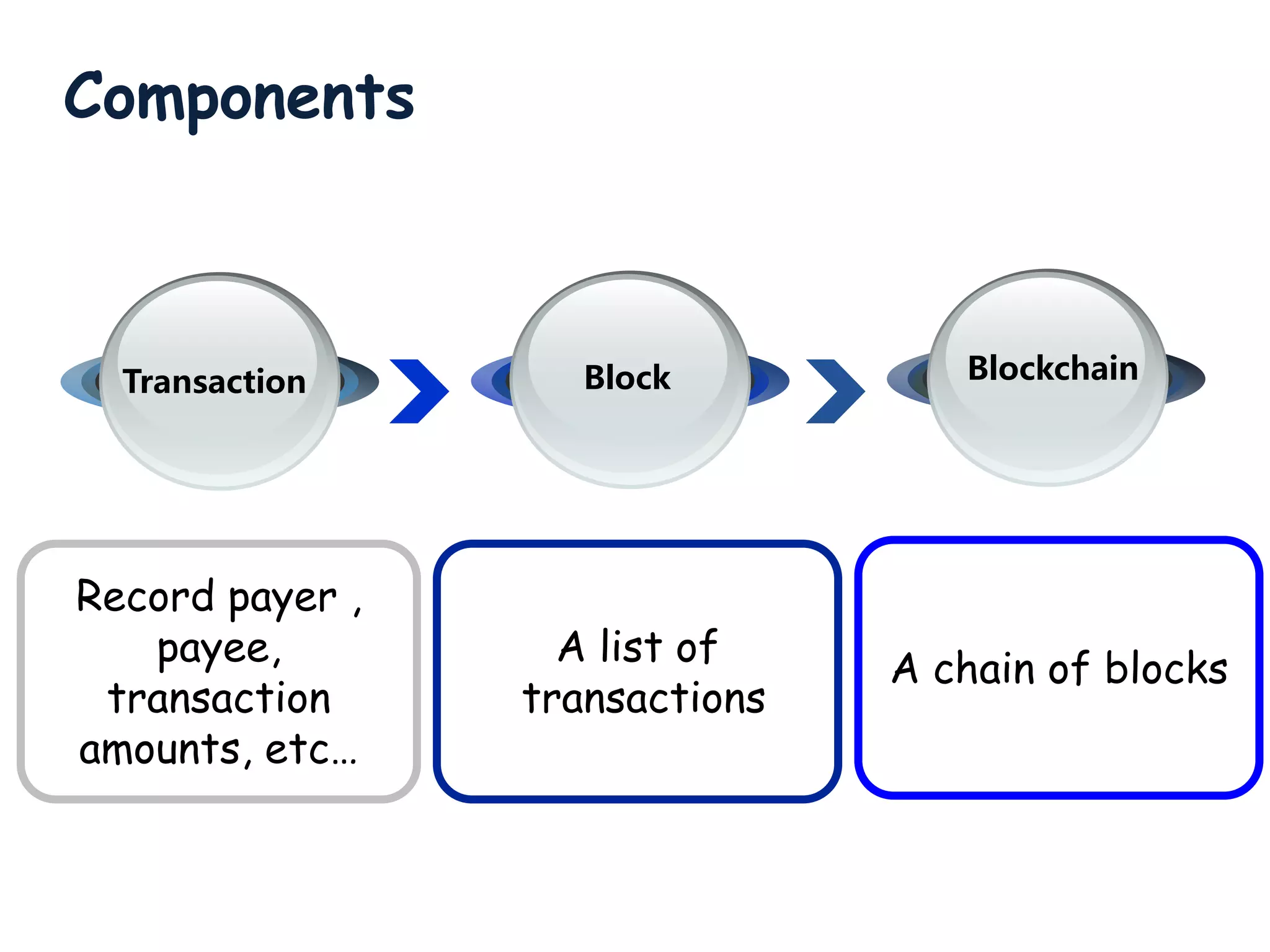
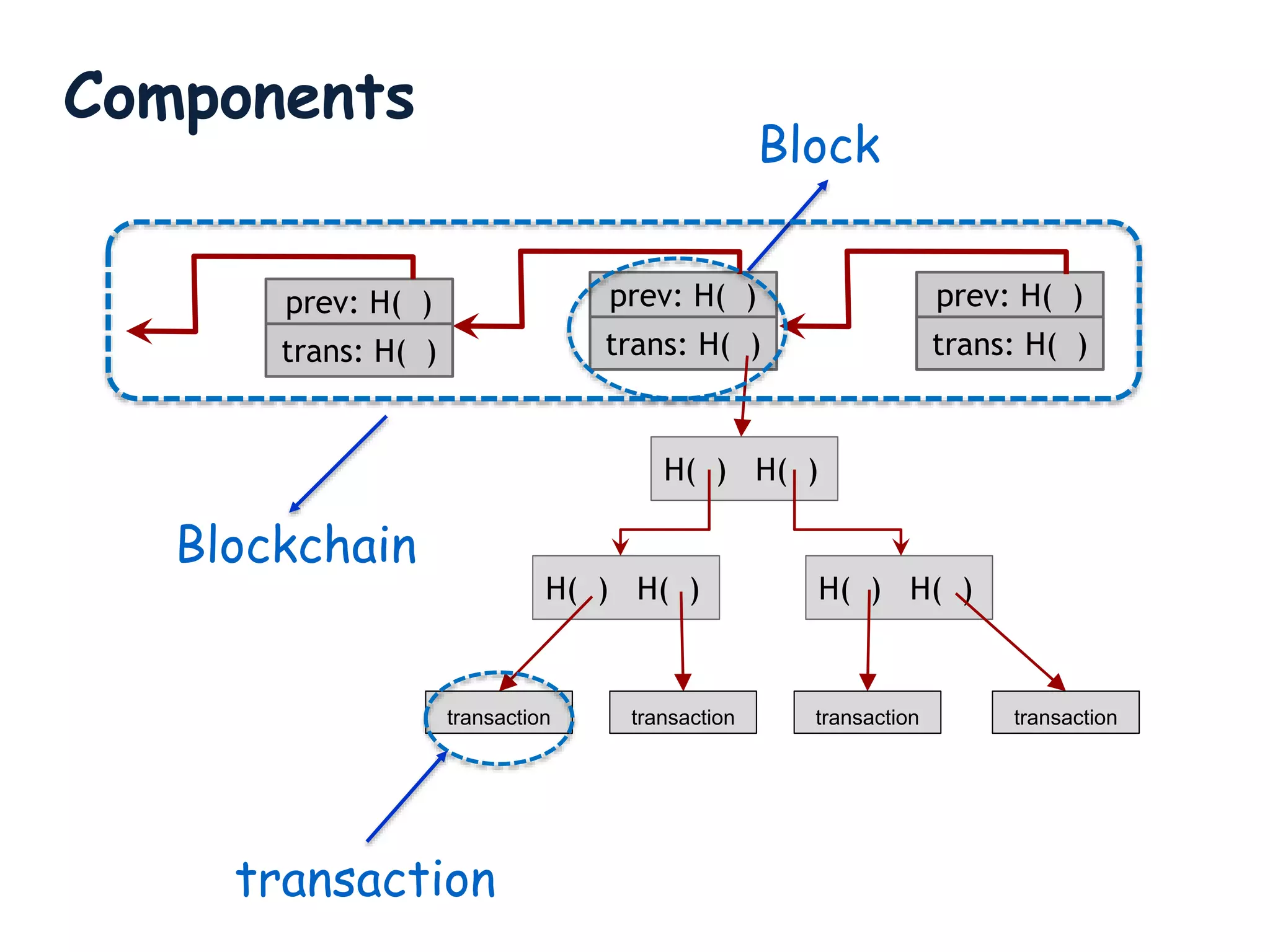
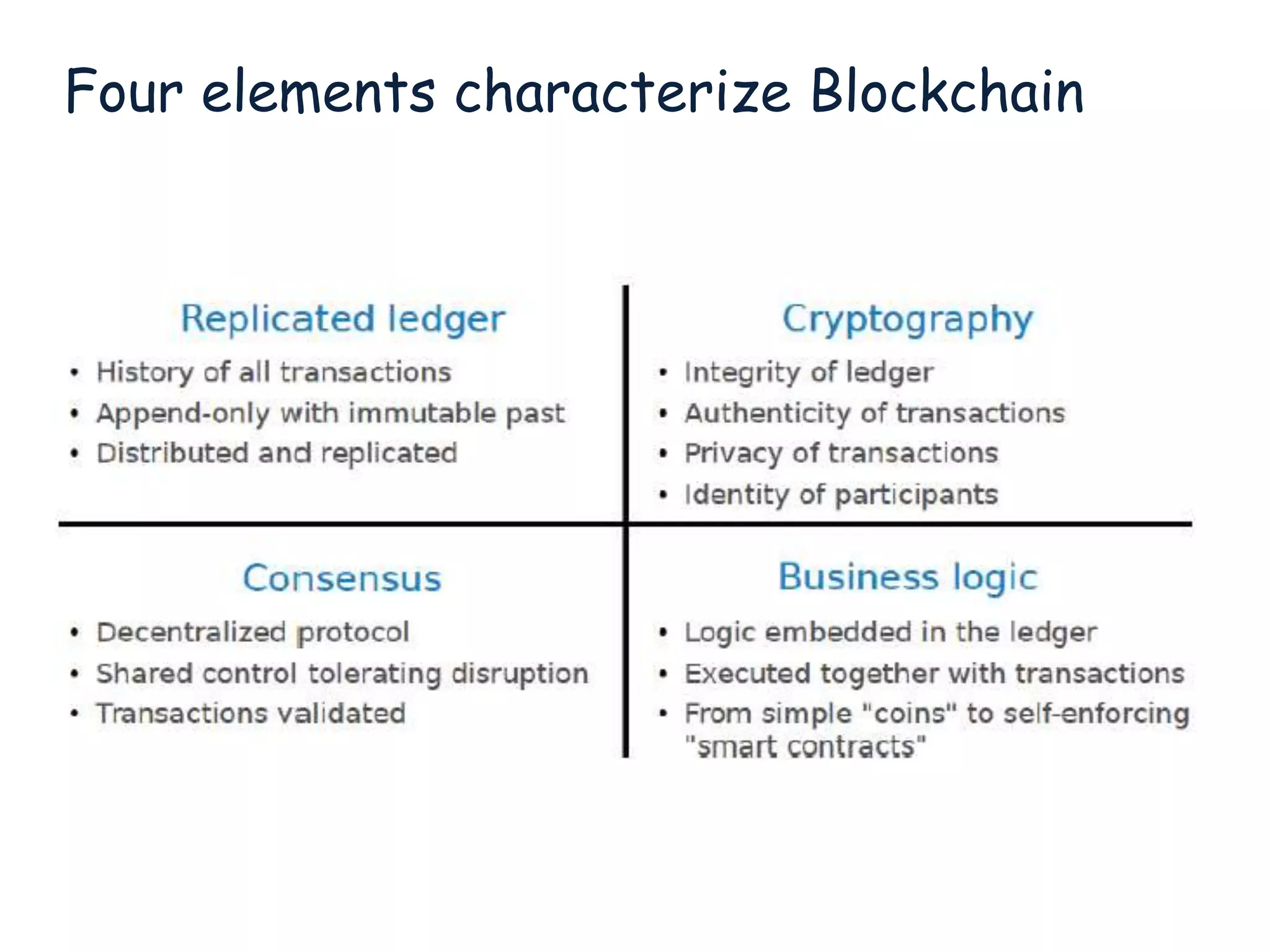
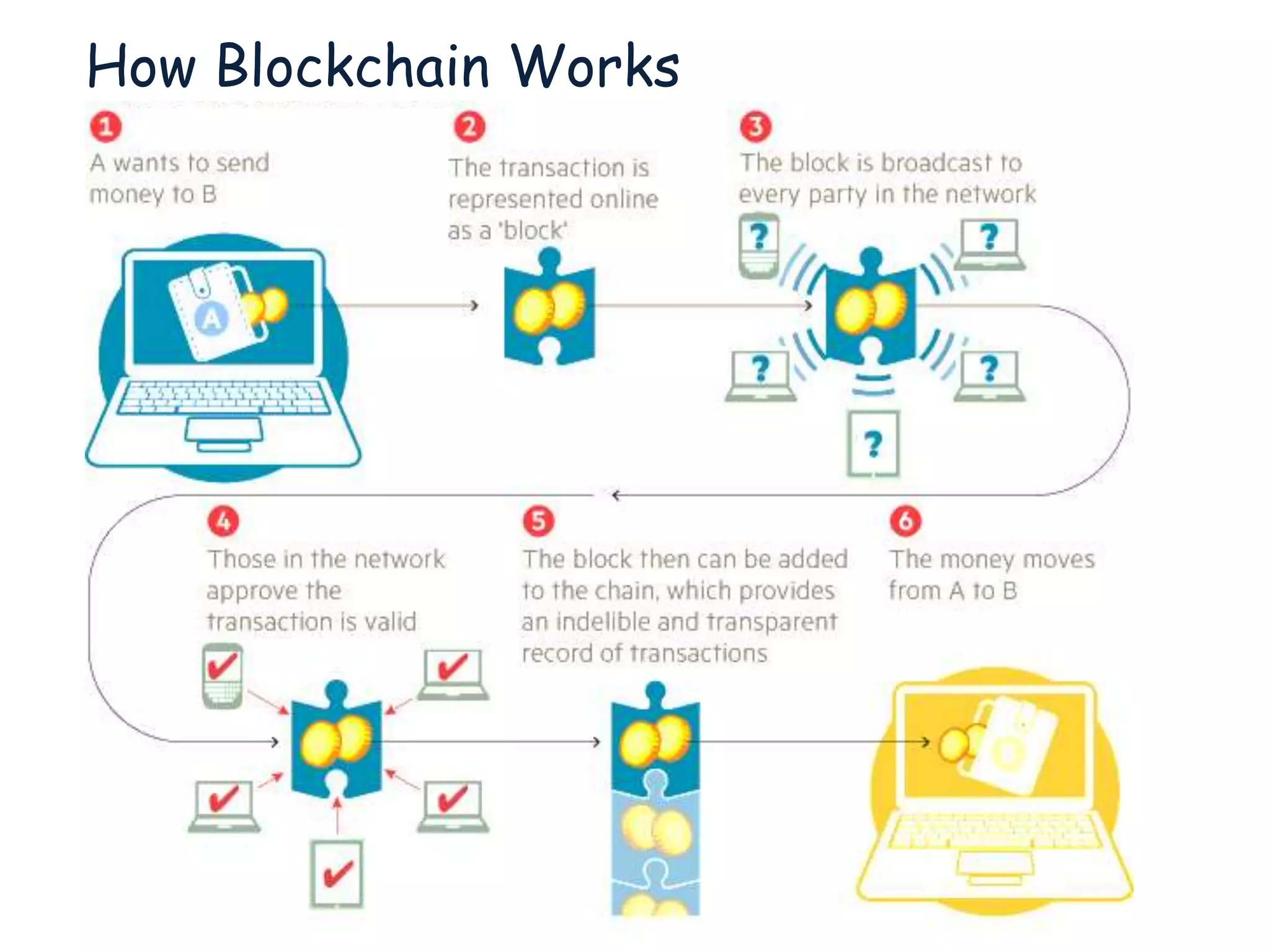
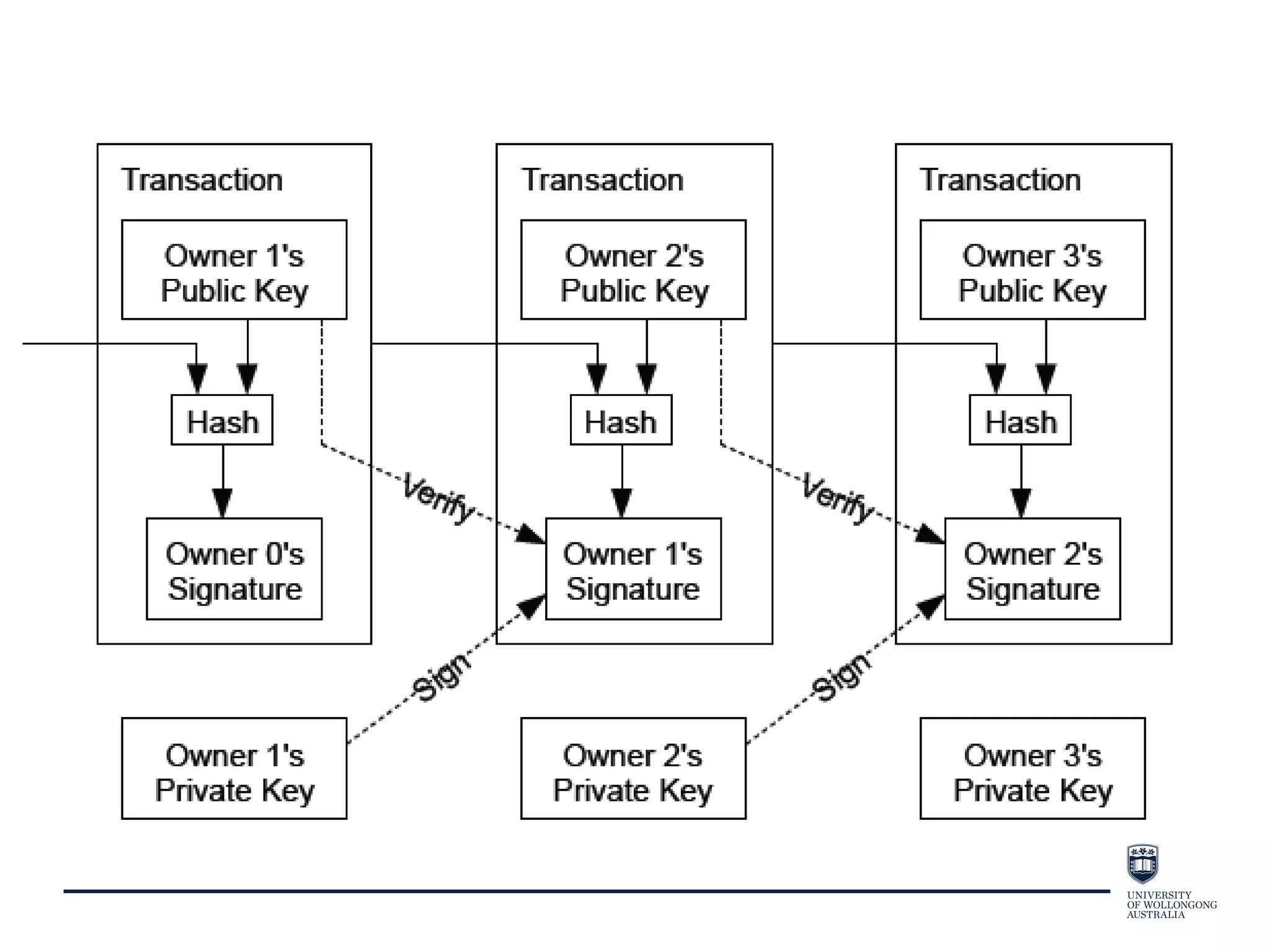
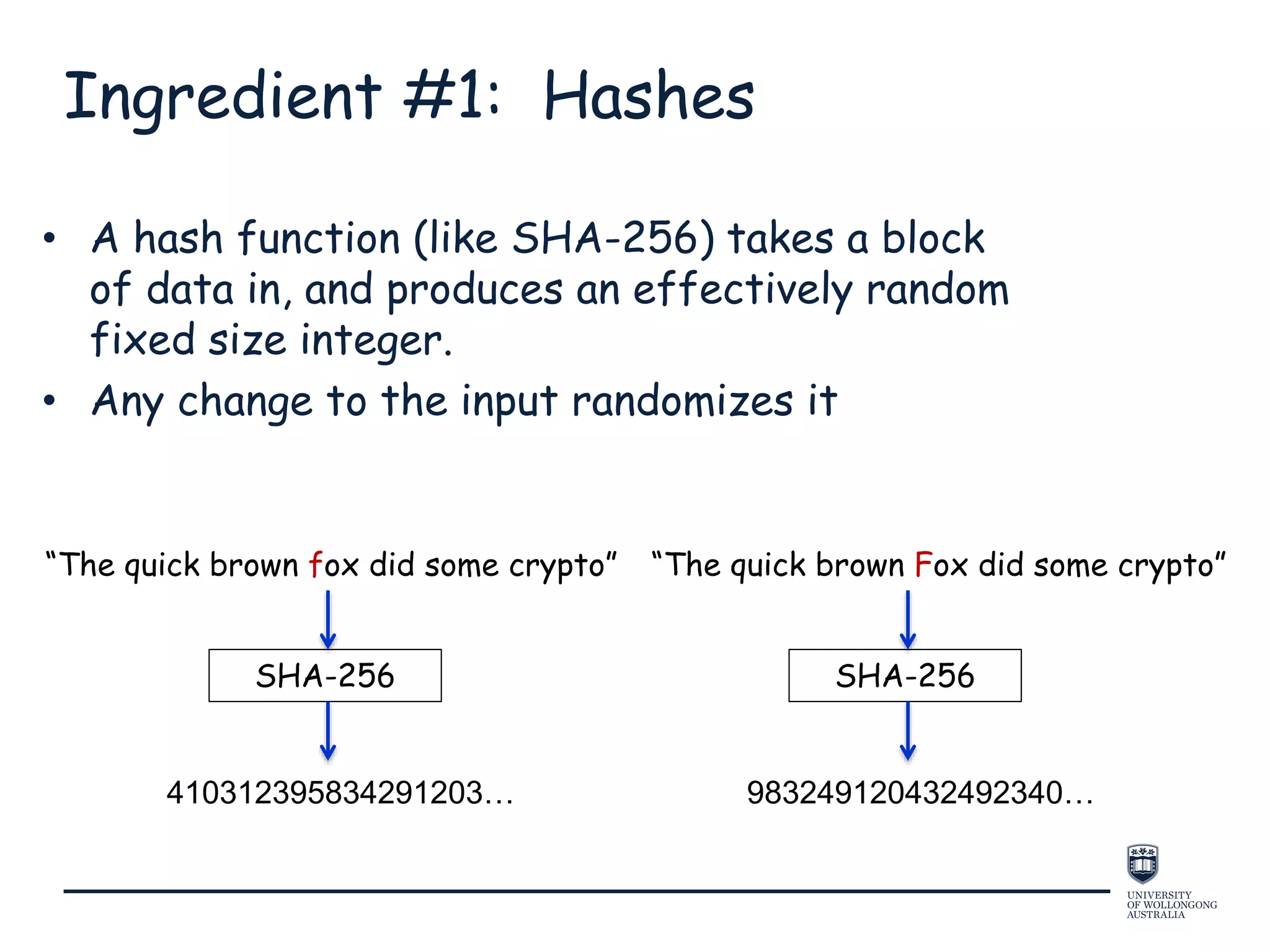
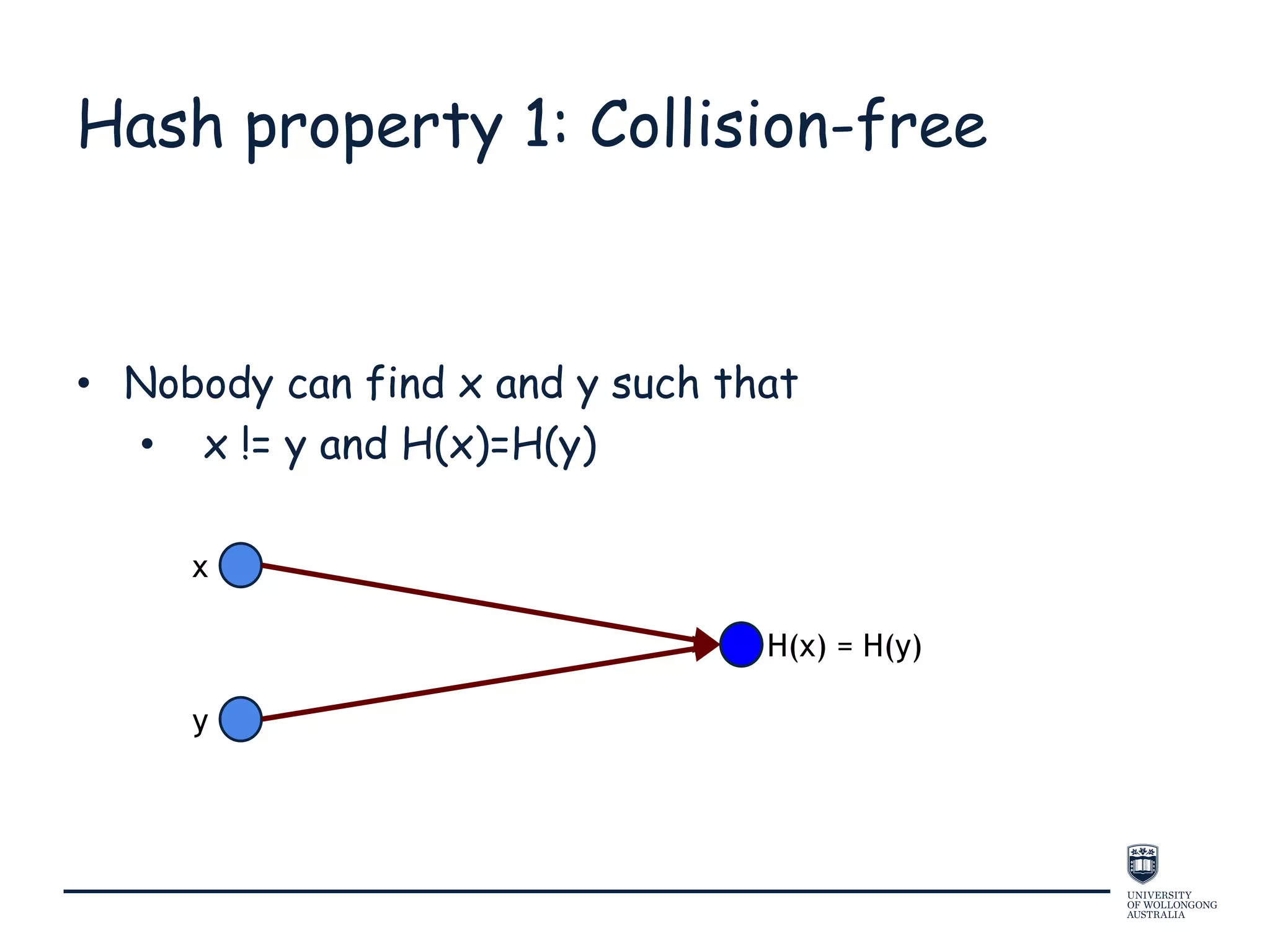
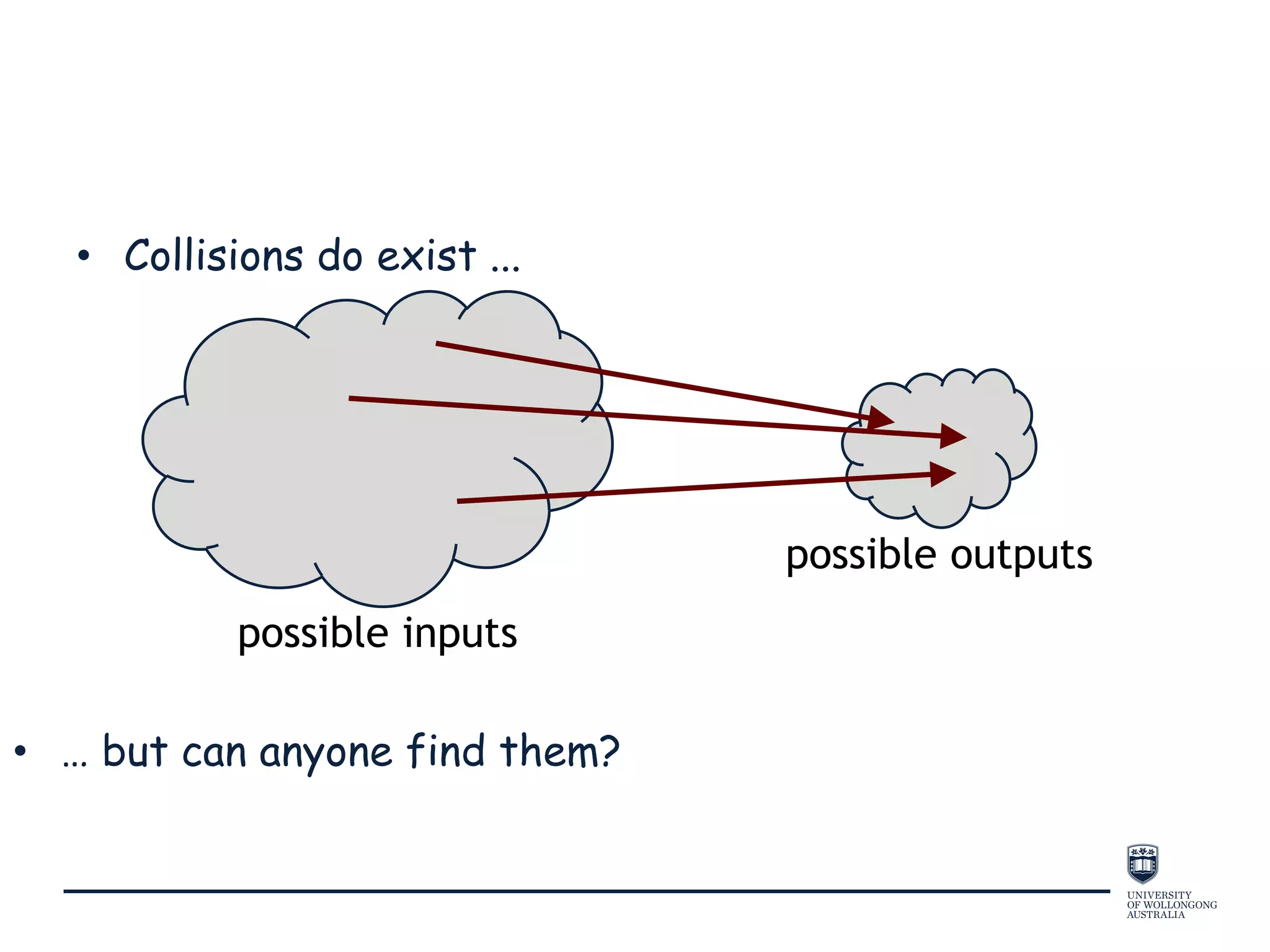
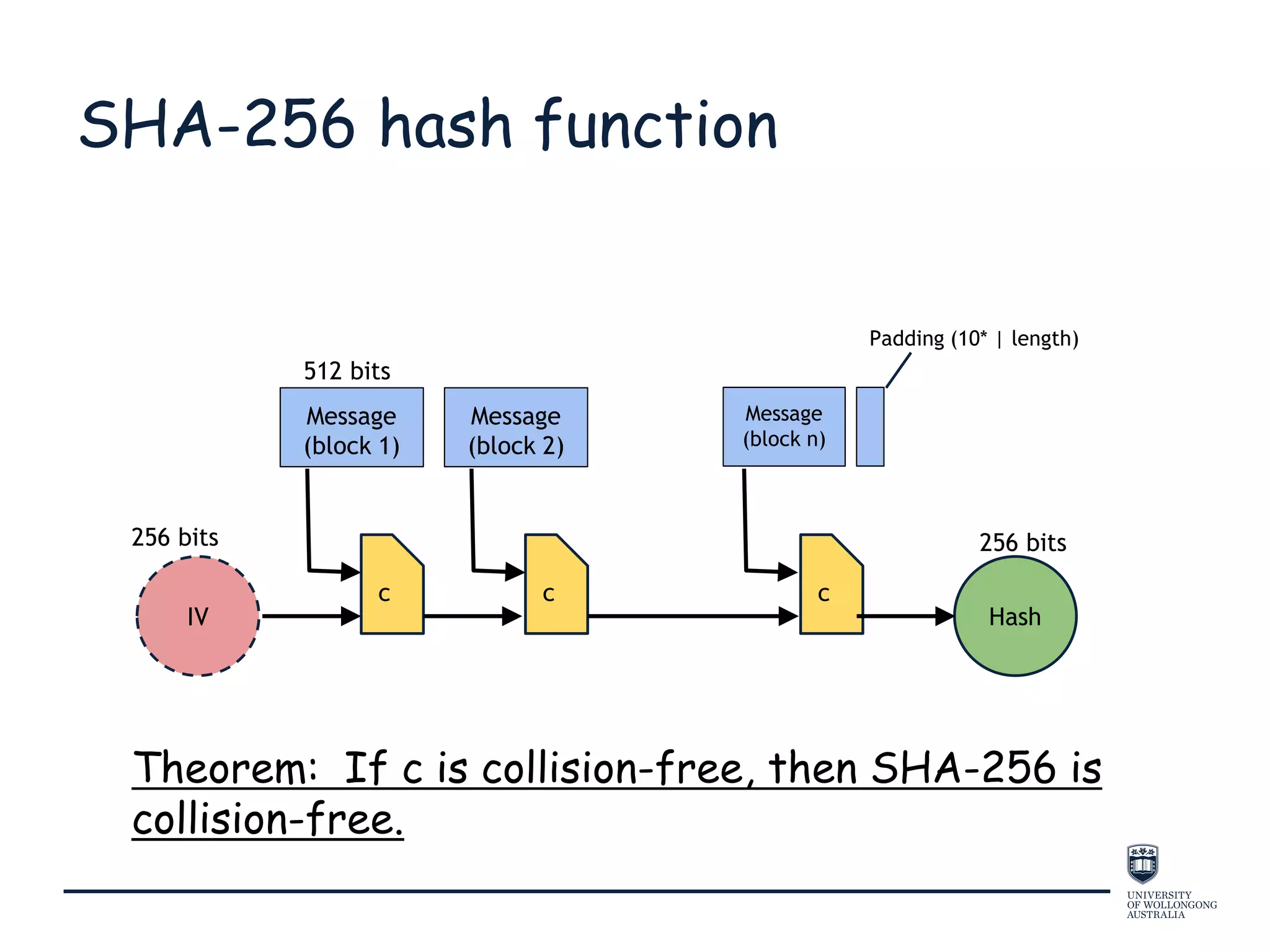
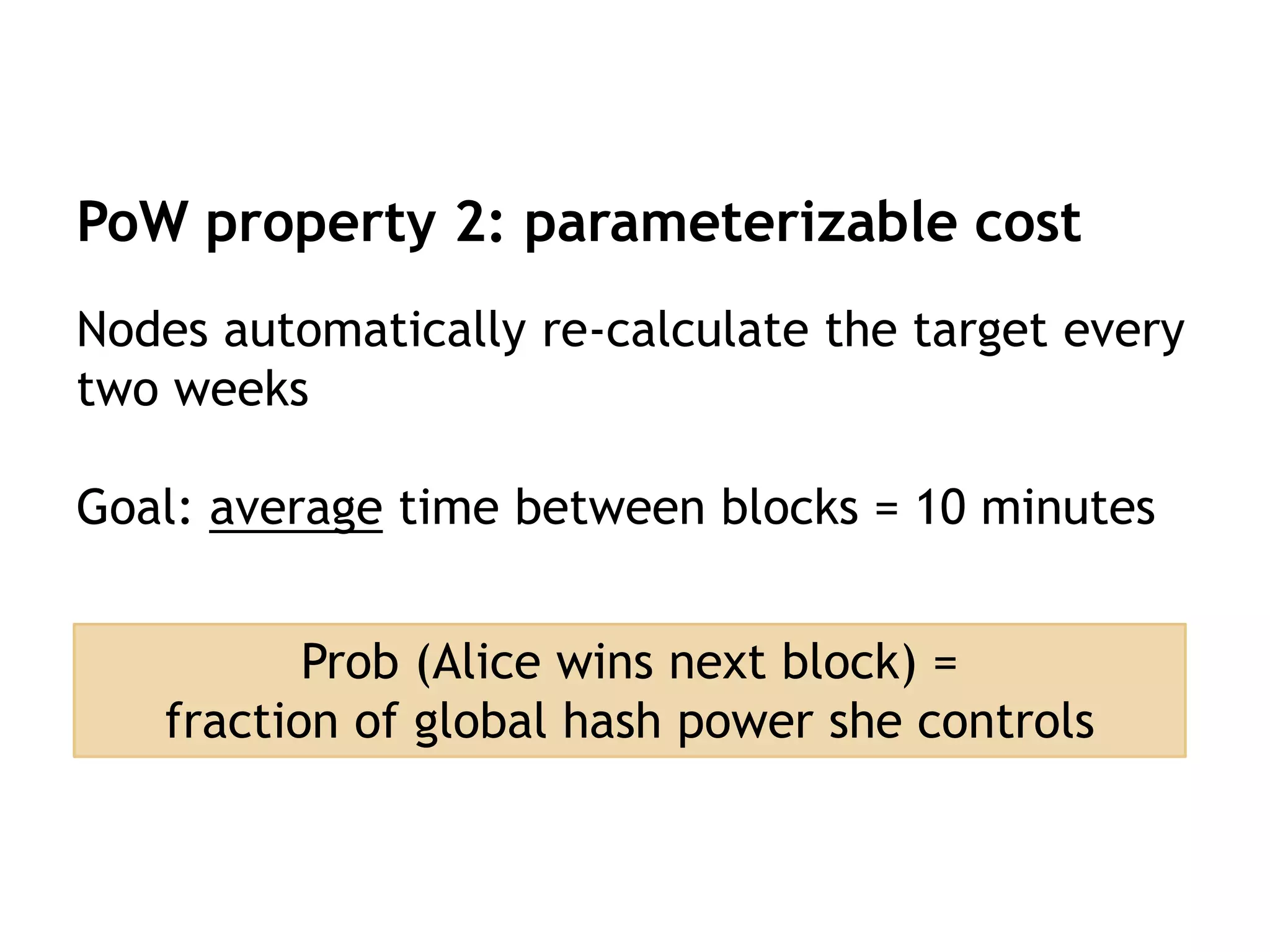
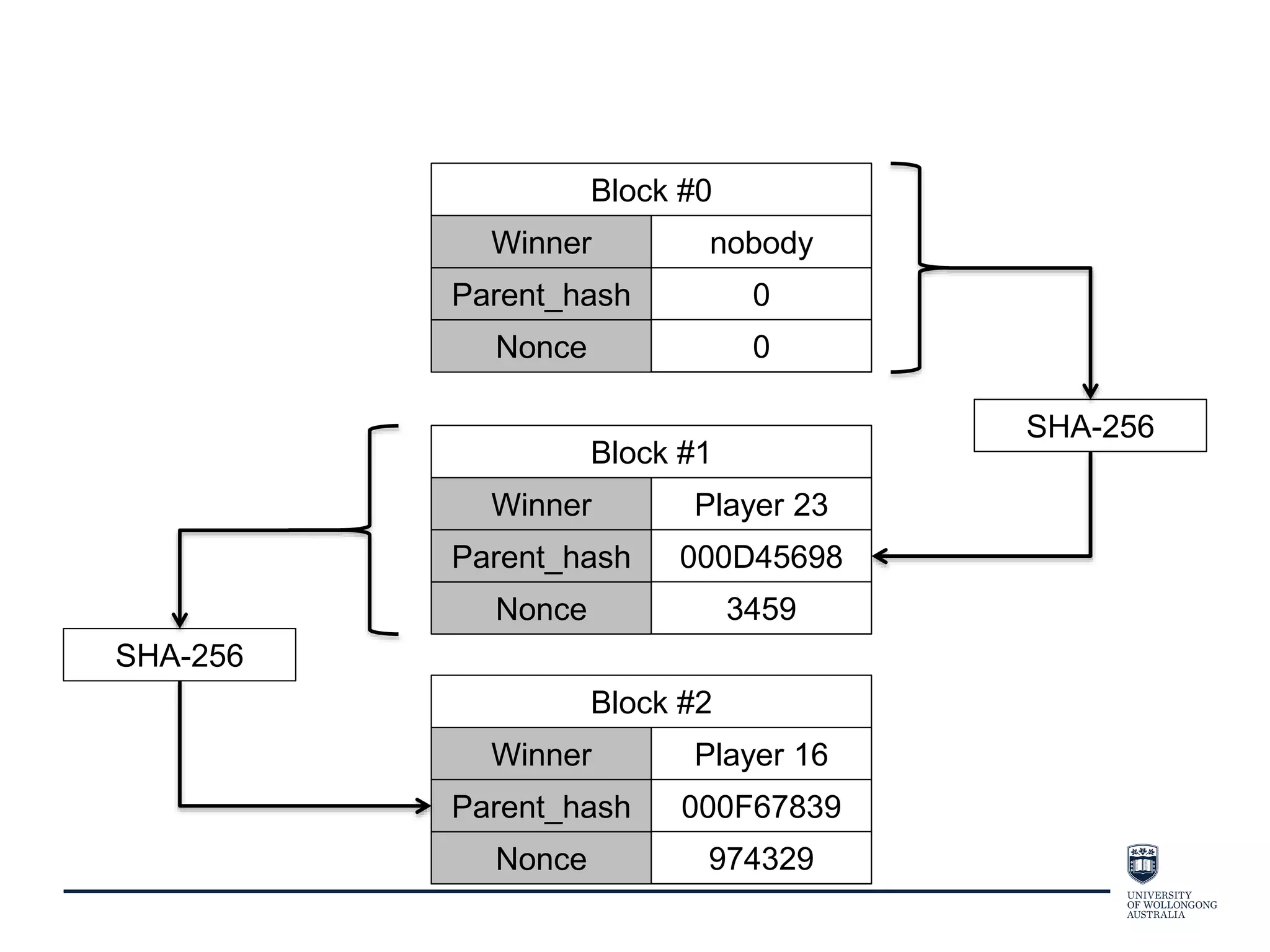
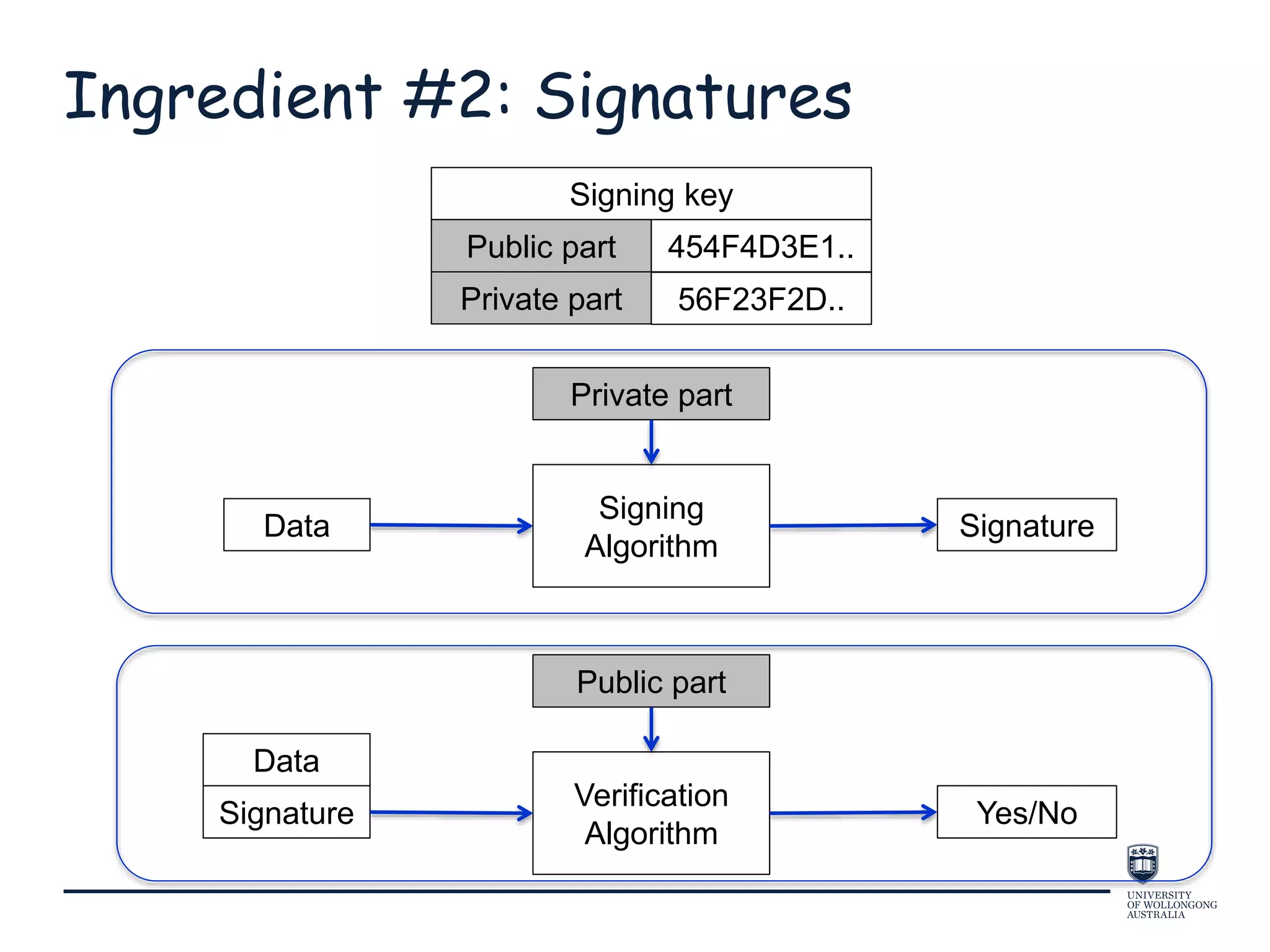
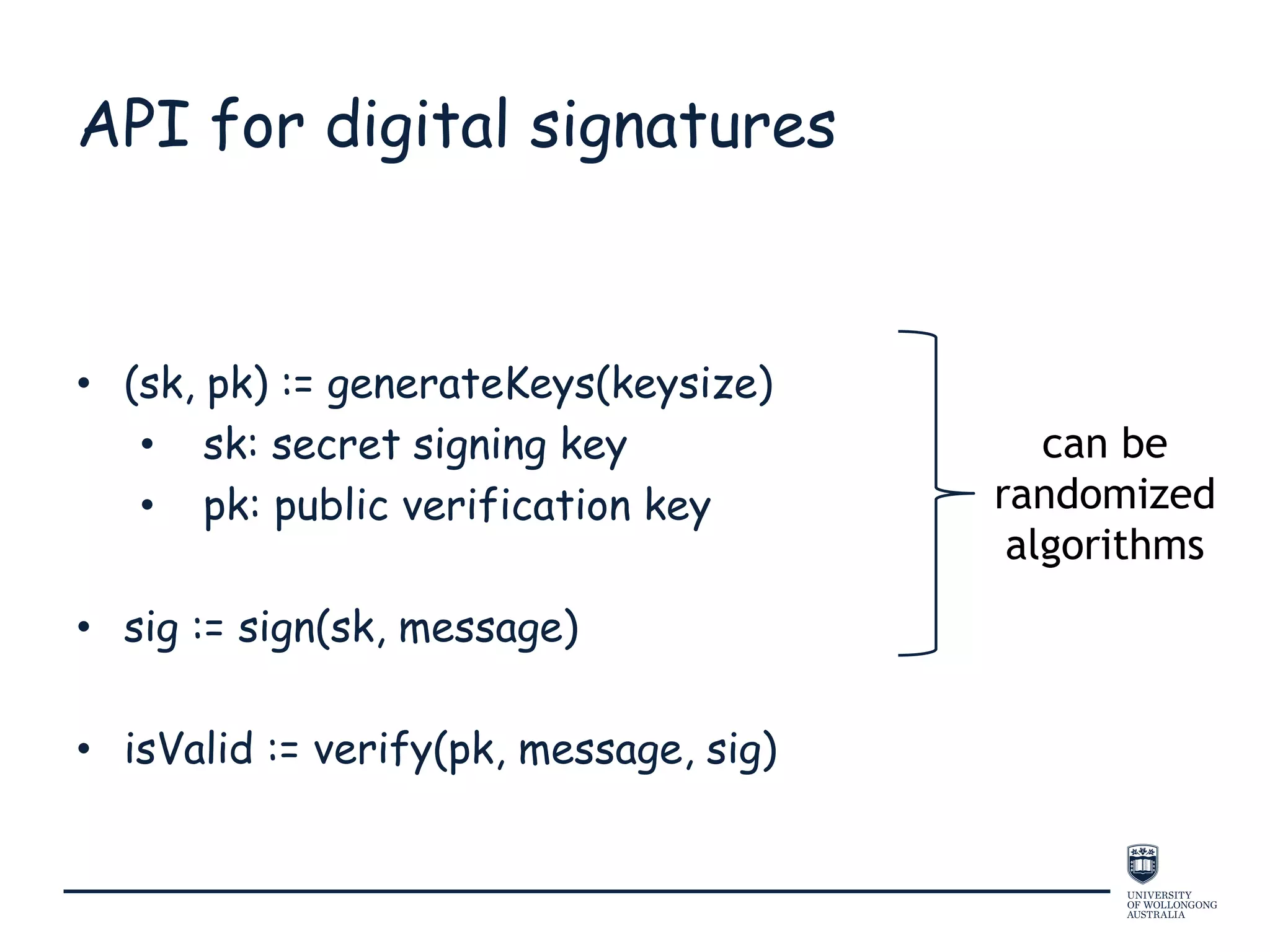
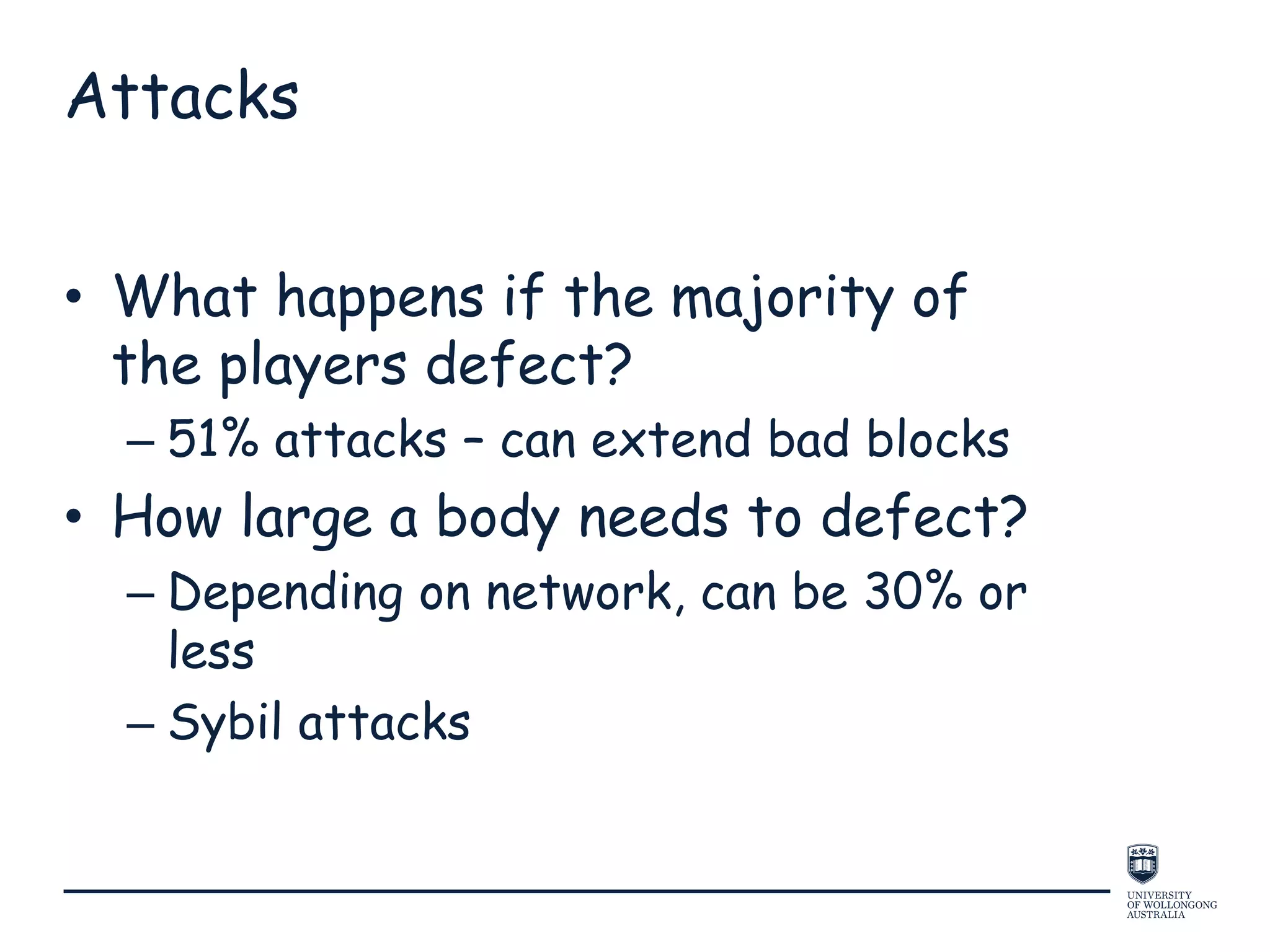
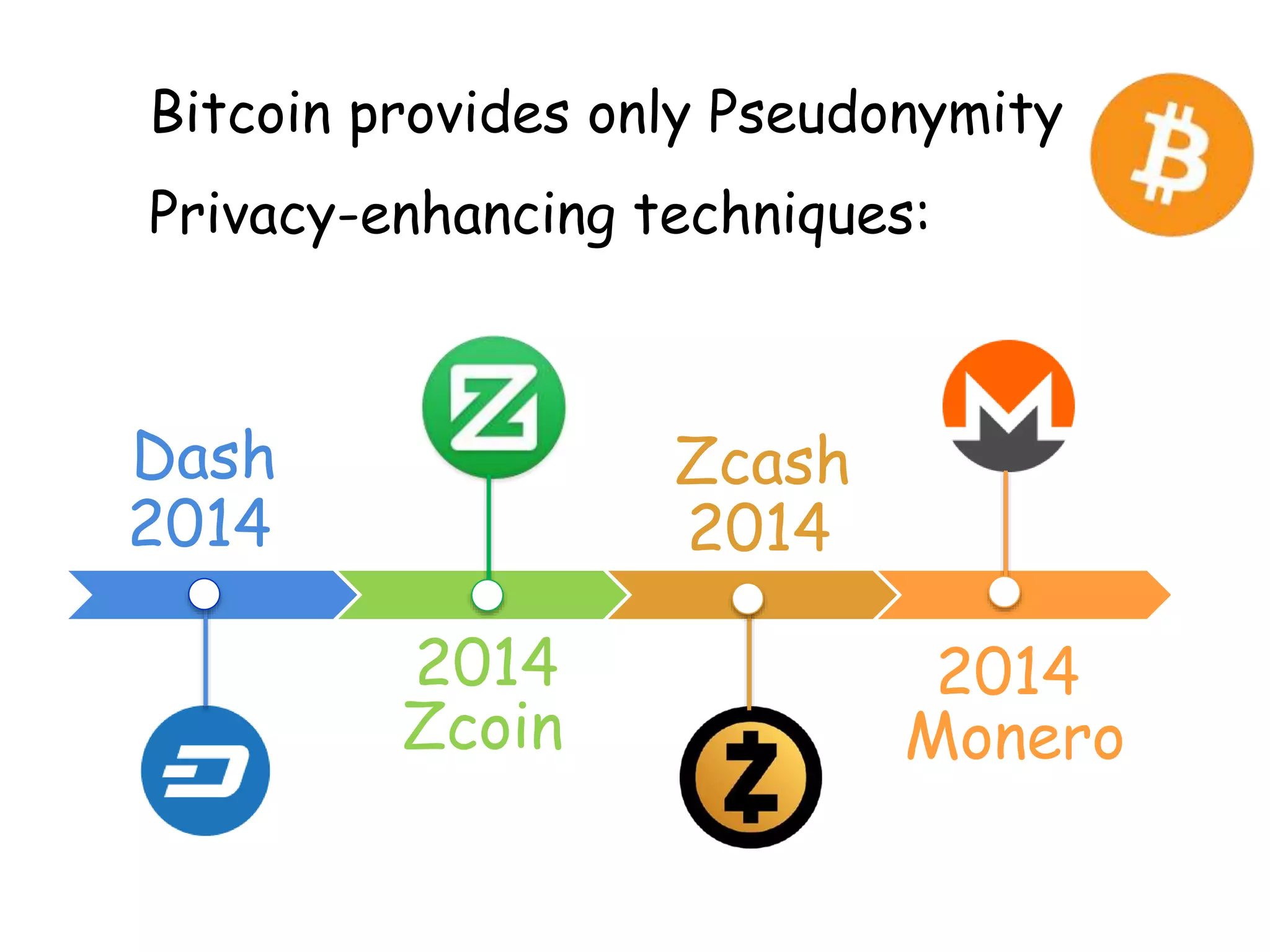
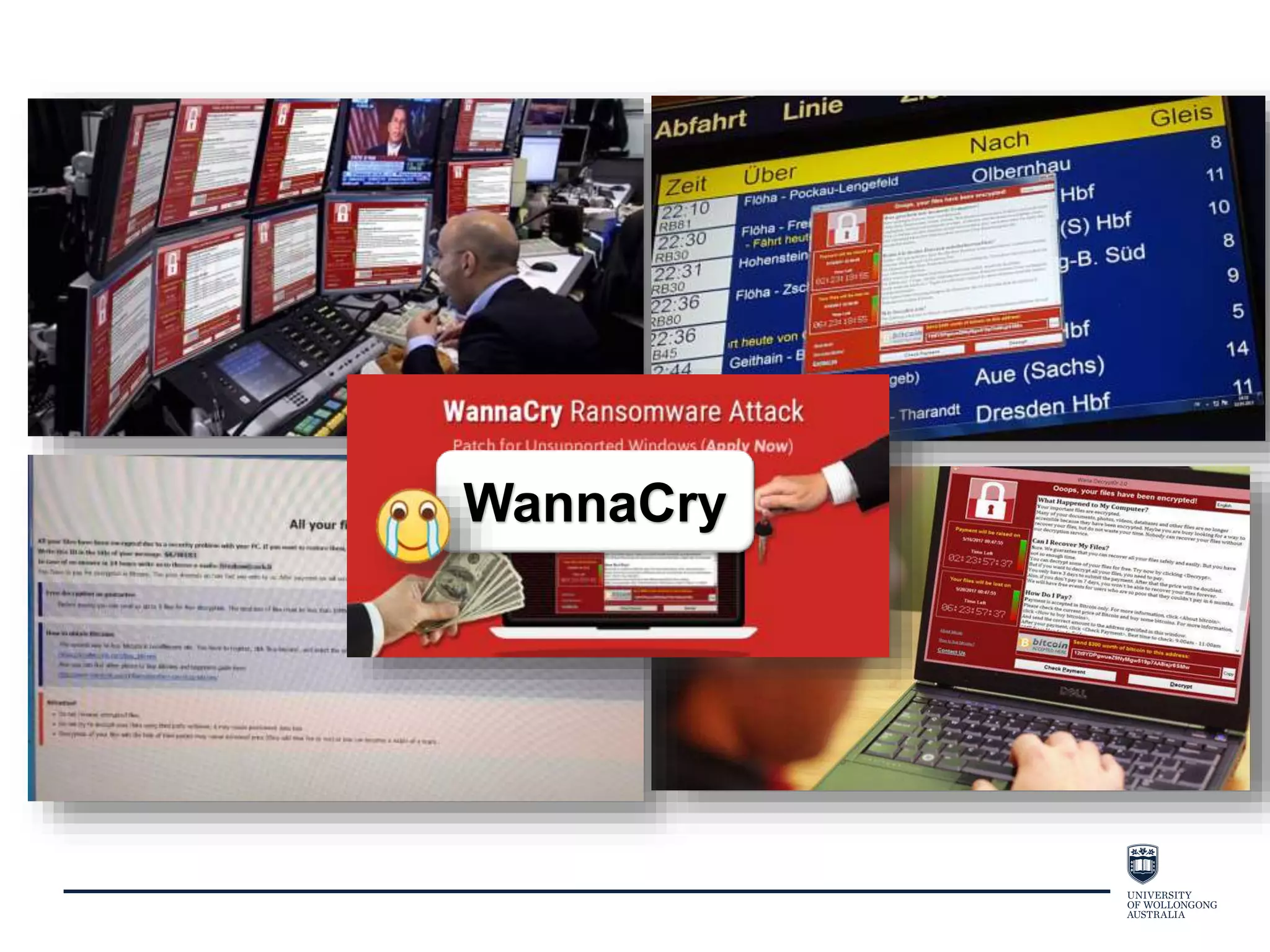
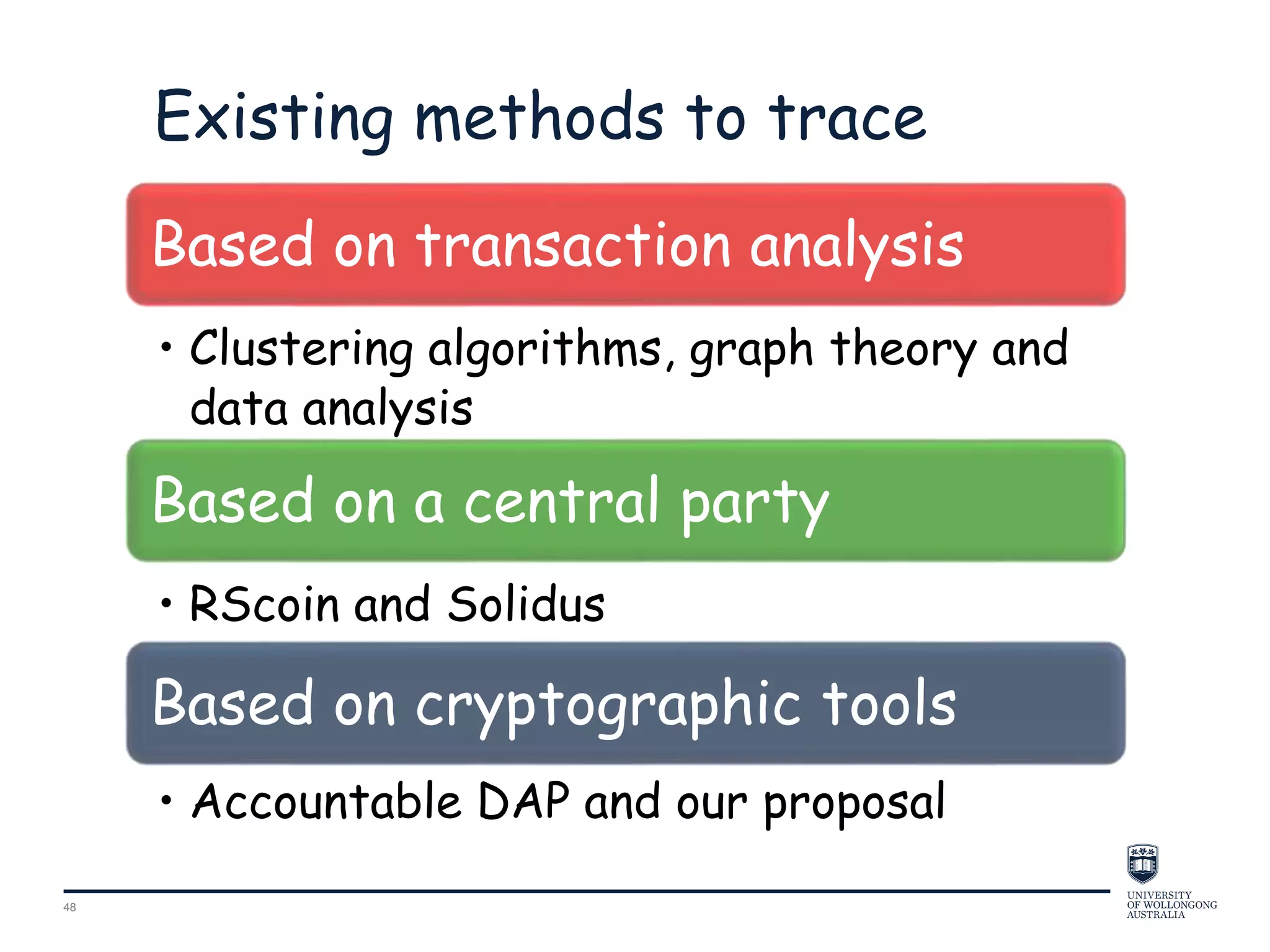
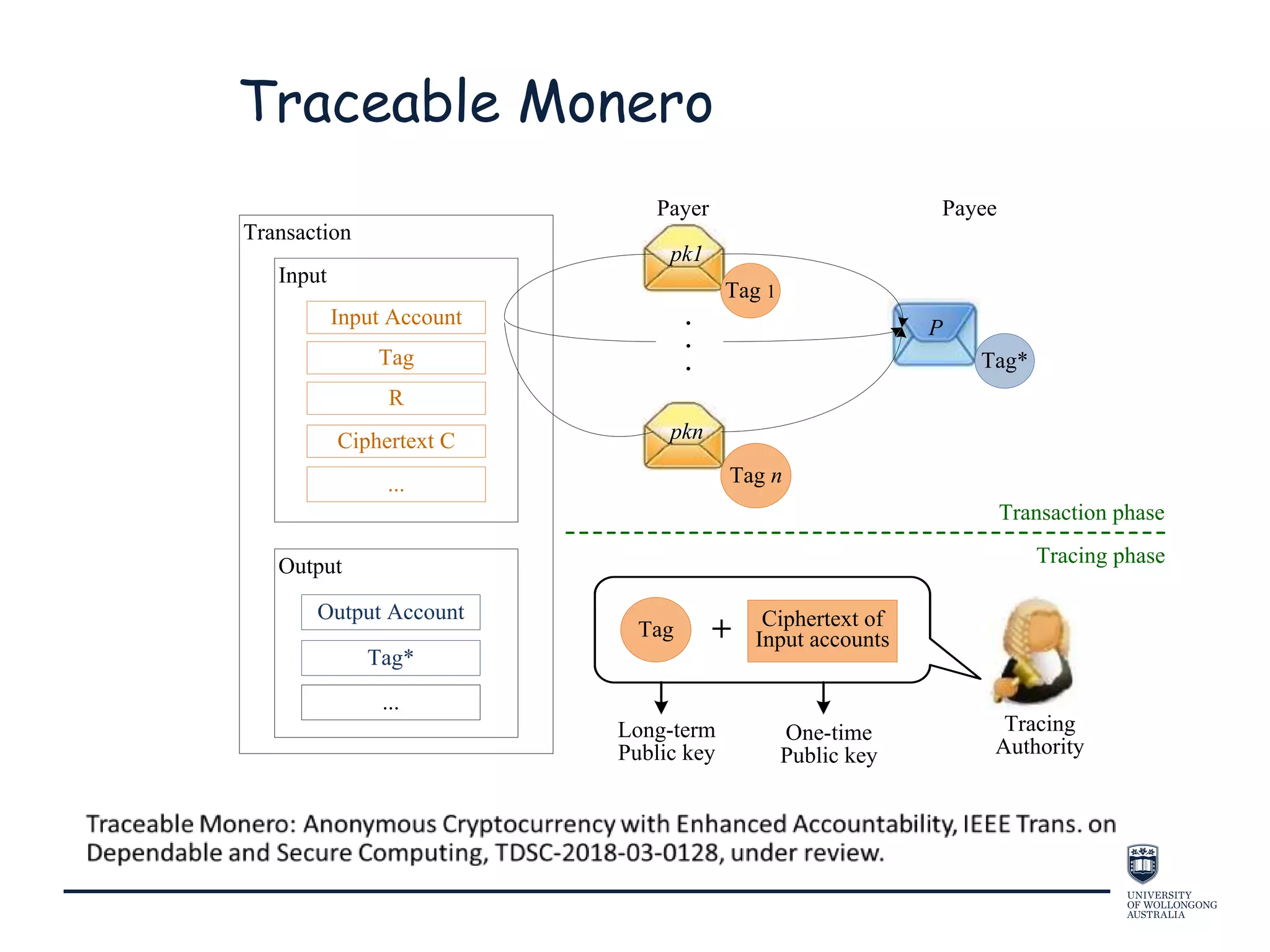
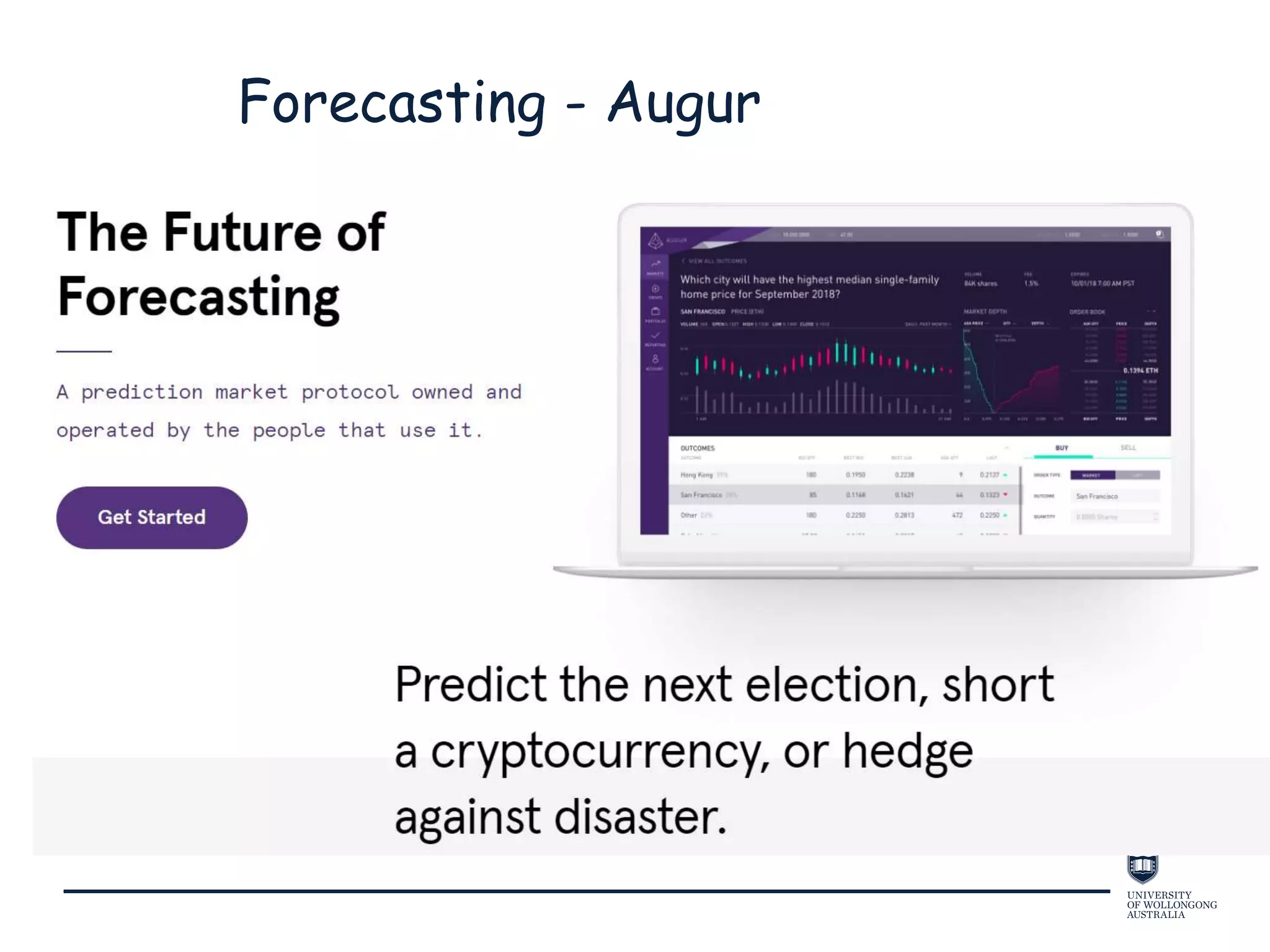
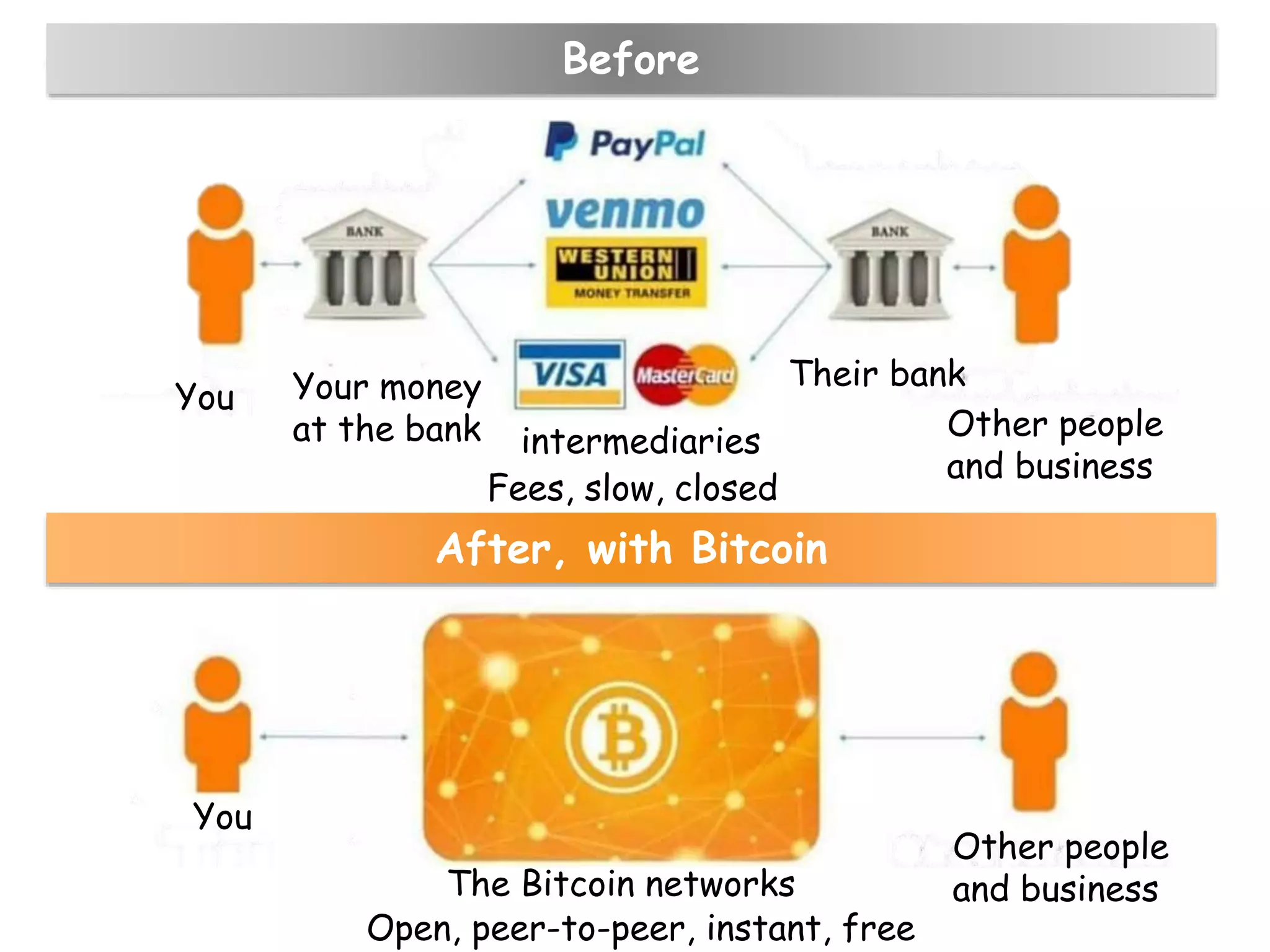
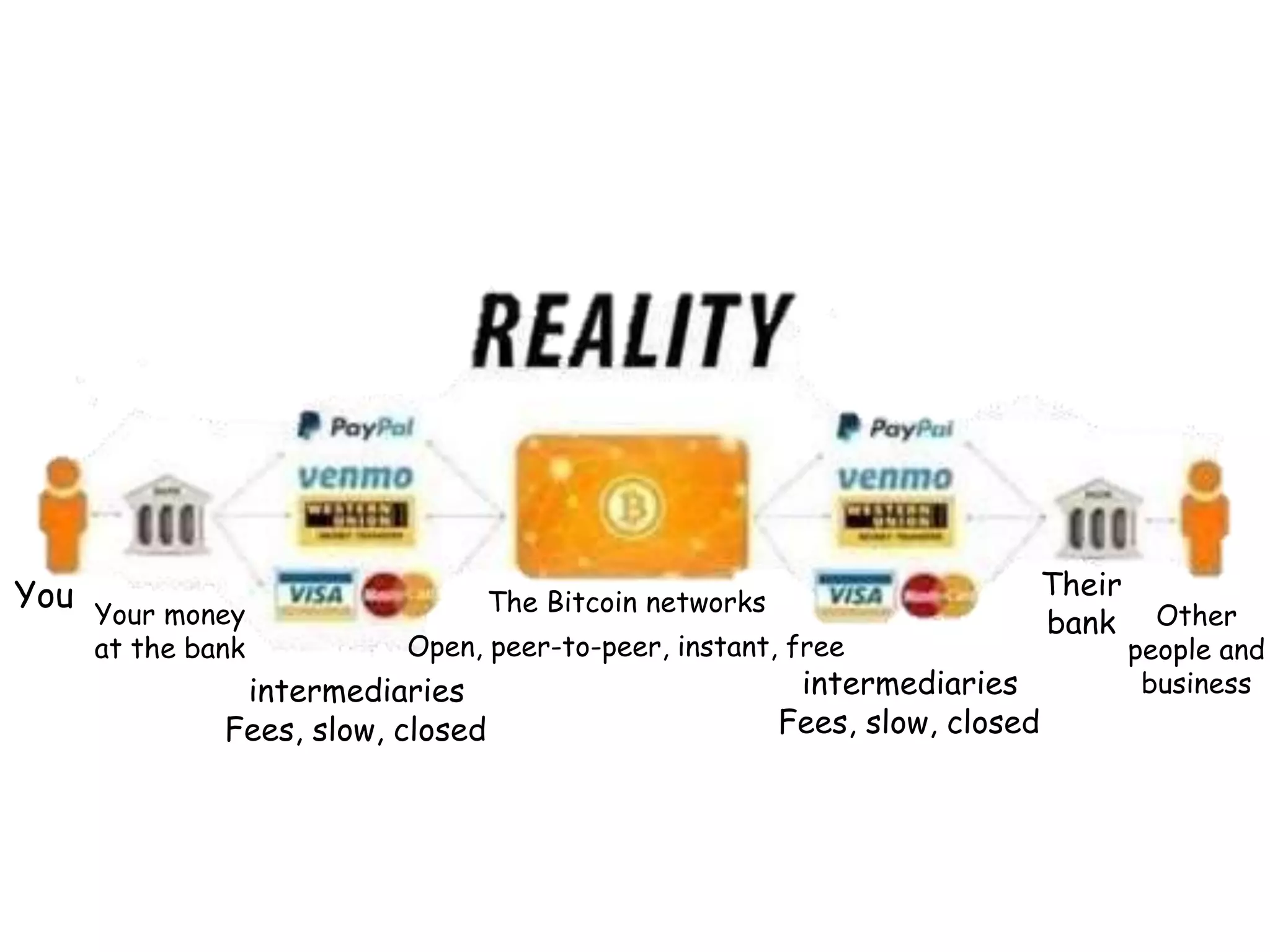
This document provides an overview of blockchain technology, its functionality, and its applications, citing Bitcoin and Ethereum as primary examples. It covers key components such as hashing, consensus mechanisms, and digital signatures, along with discussions on security and potential applications in various sectors like healthcare and finance. Additionally, it addresses ongoing research and future considerations for the technology, including issues of privacy and scalability.