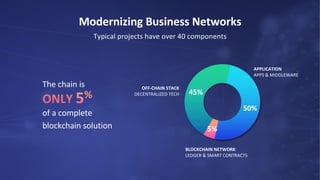
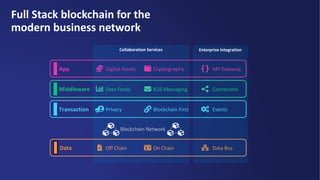
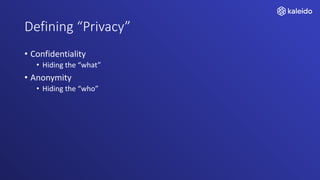
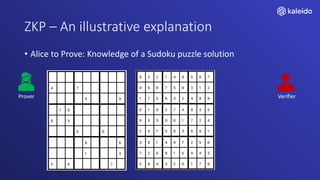
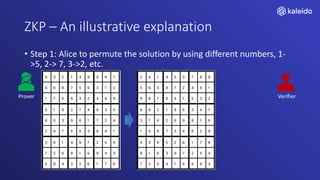
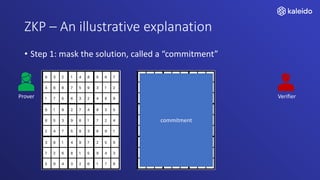
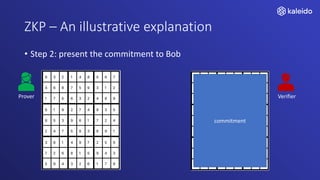
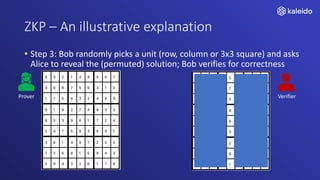
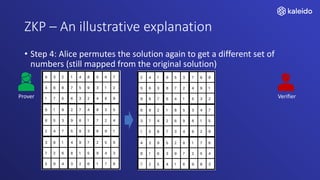
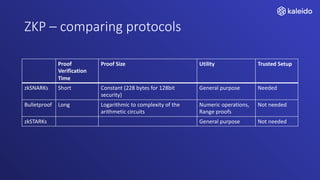
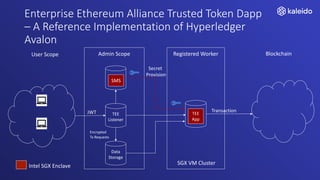
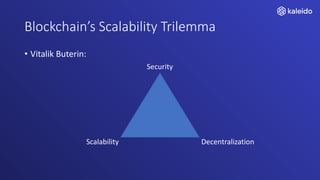
Kaleido offers a comprehensive blockchain business cloud platform that emphasizes privacy and scalability for enterprise applications. It provides solutions for data isolation, separate blockchains, and trusted computing techniques like zero knowledge proofs to enhance privacy in decentralized networks. The platform also facilitates hybrid deployments across multiple cloud providers, ensuring seamless integration for business networks.