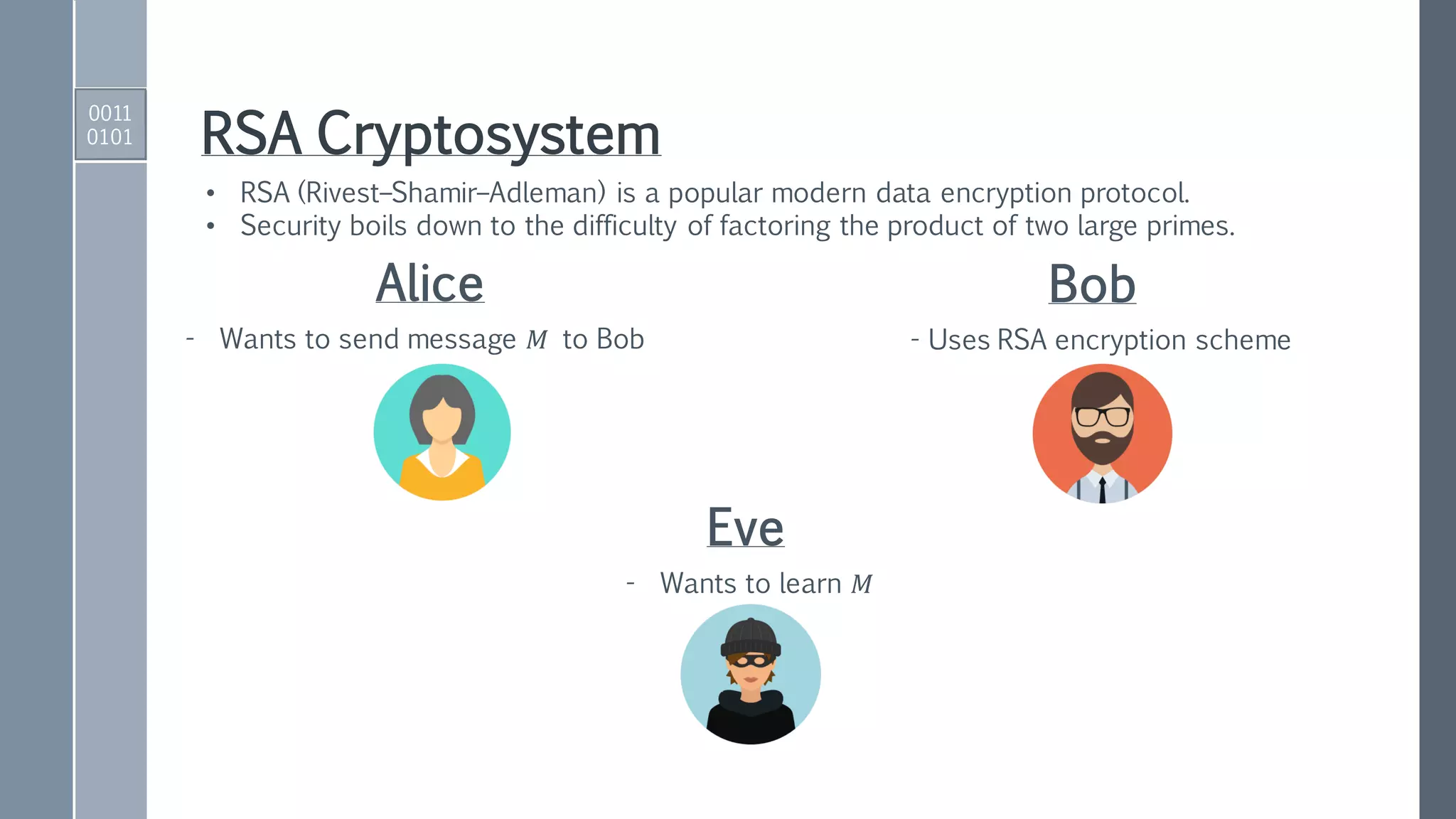
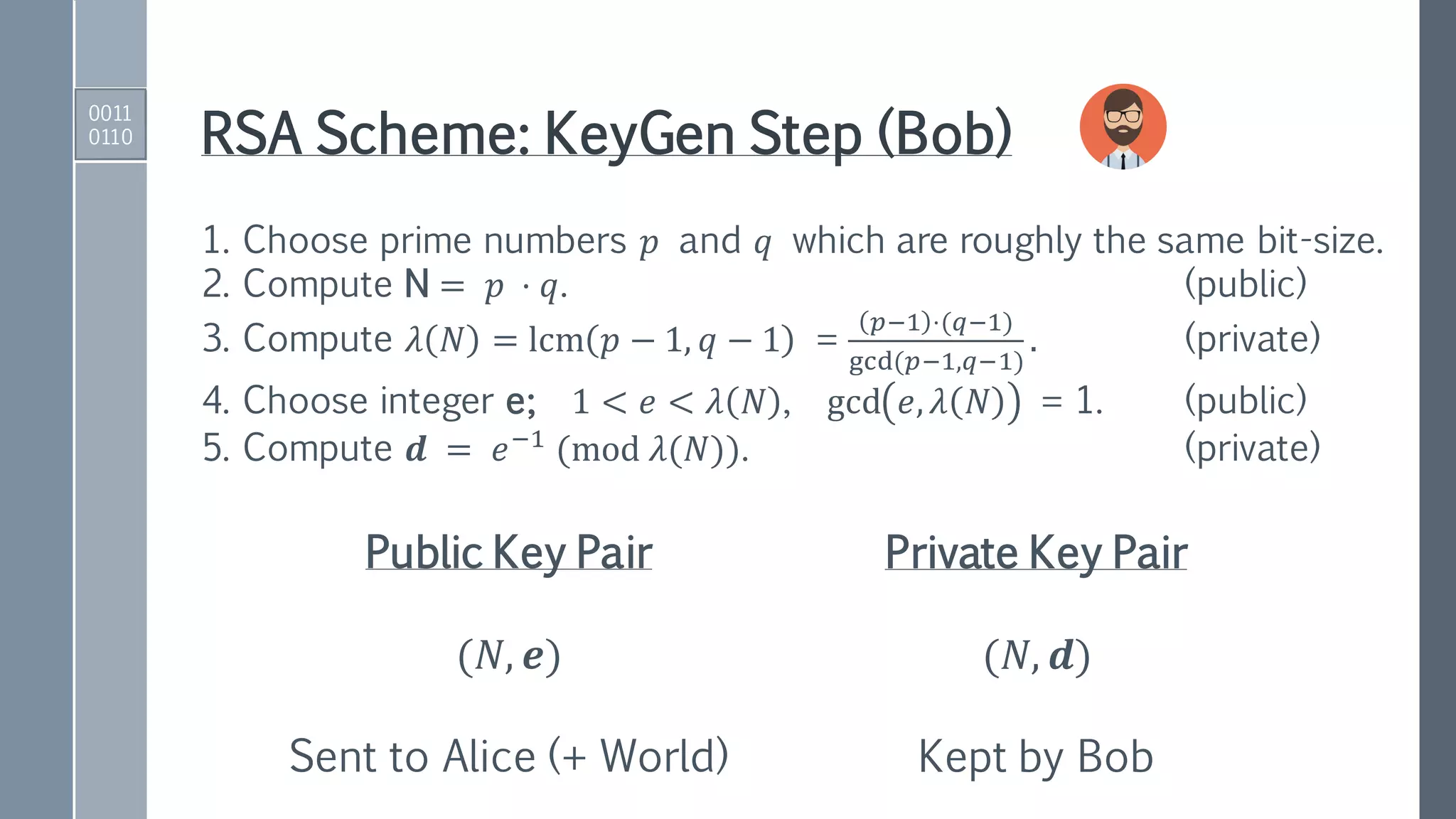
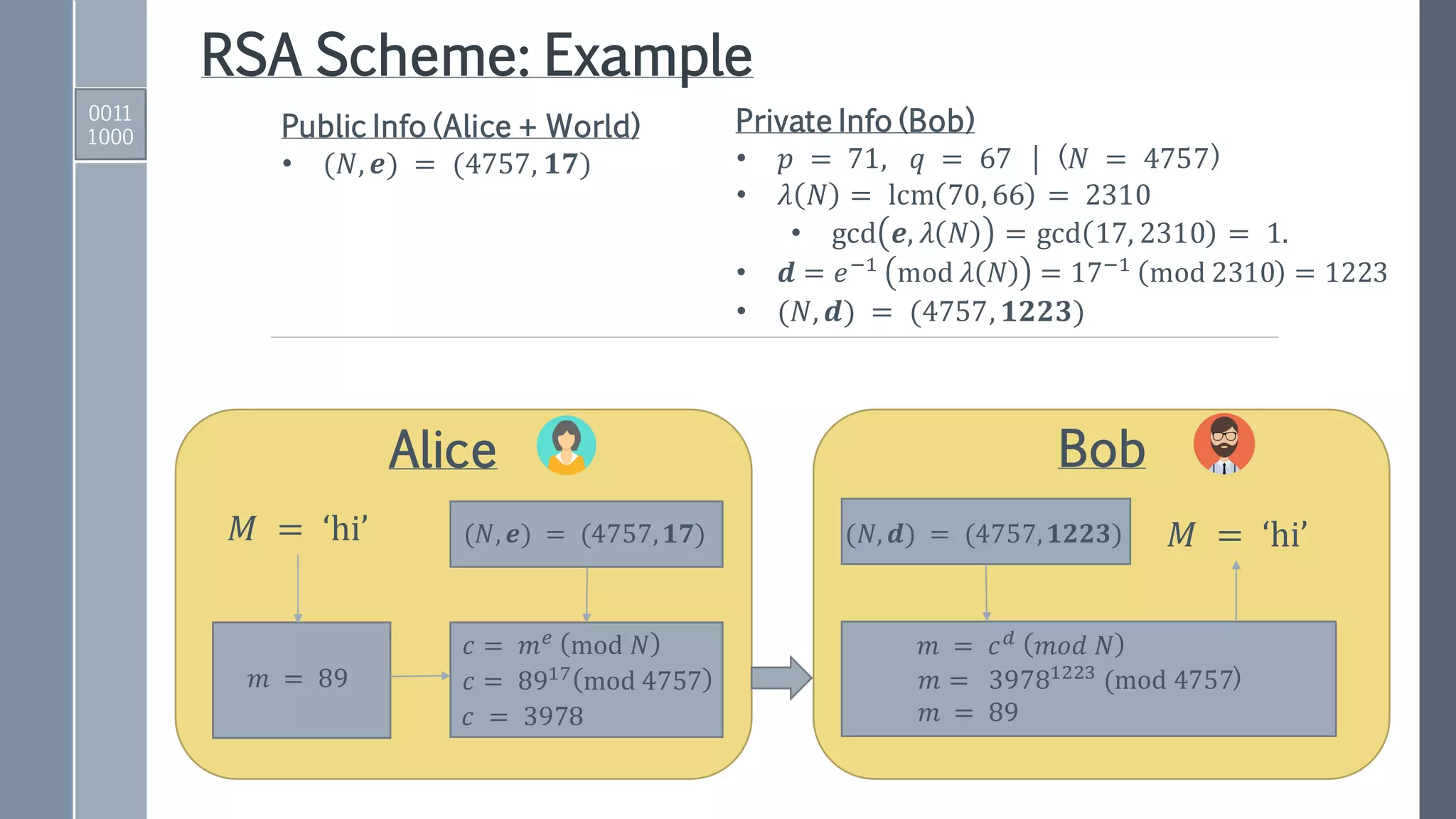
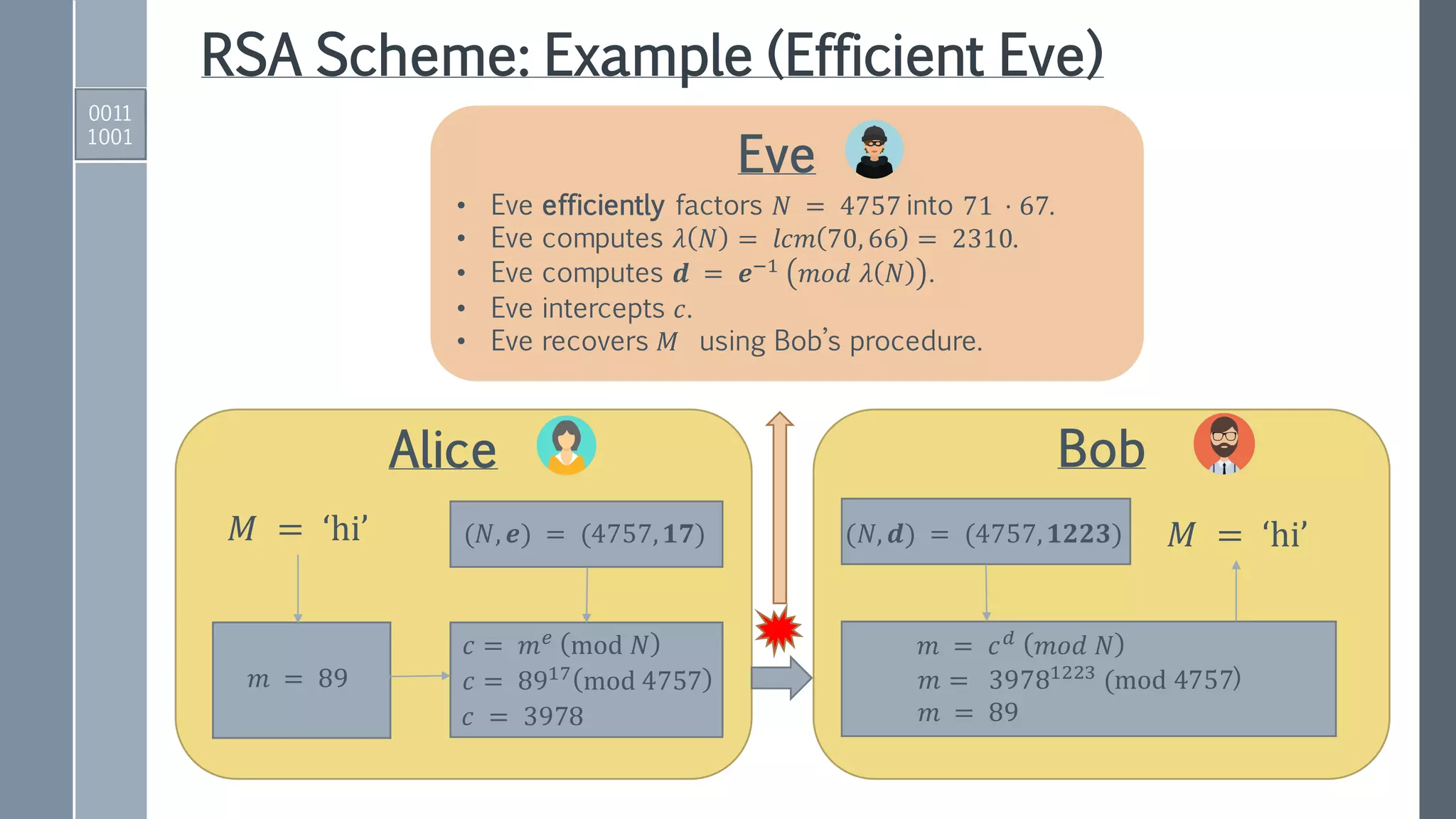
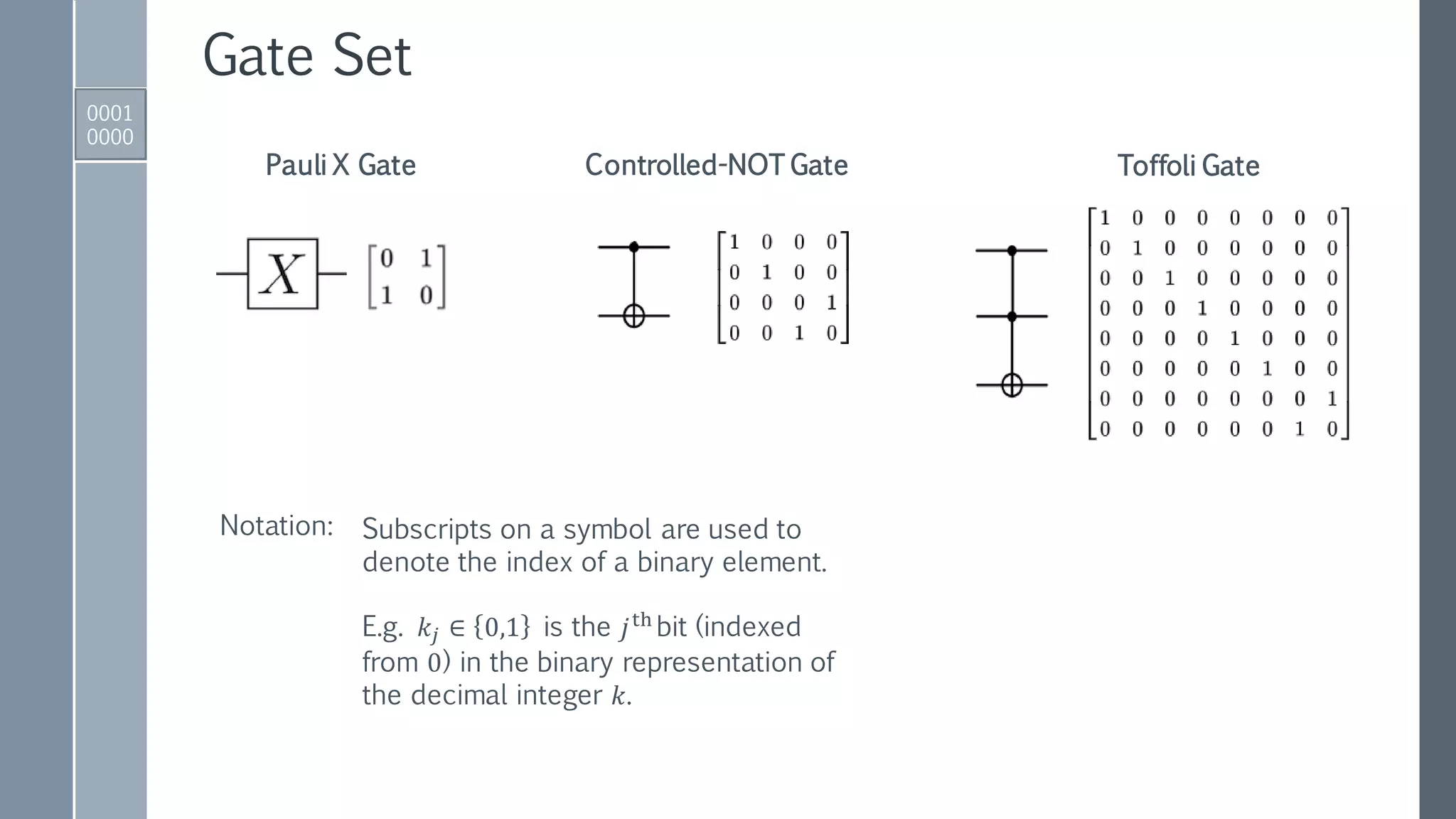
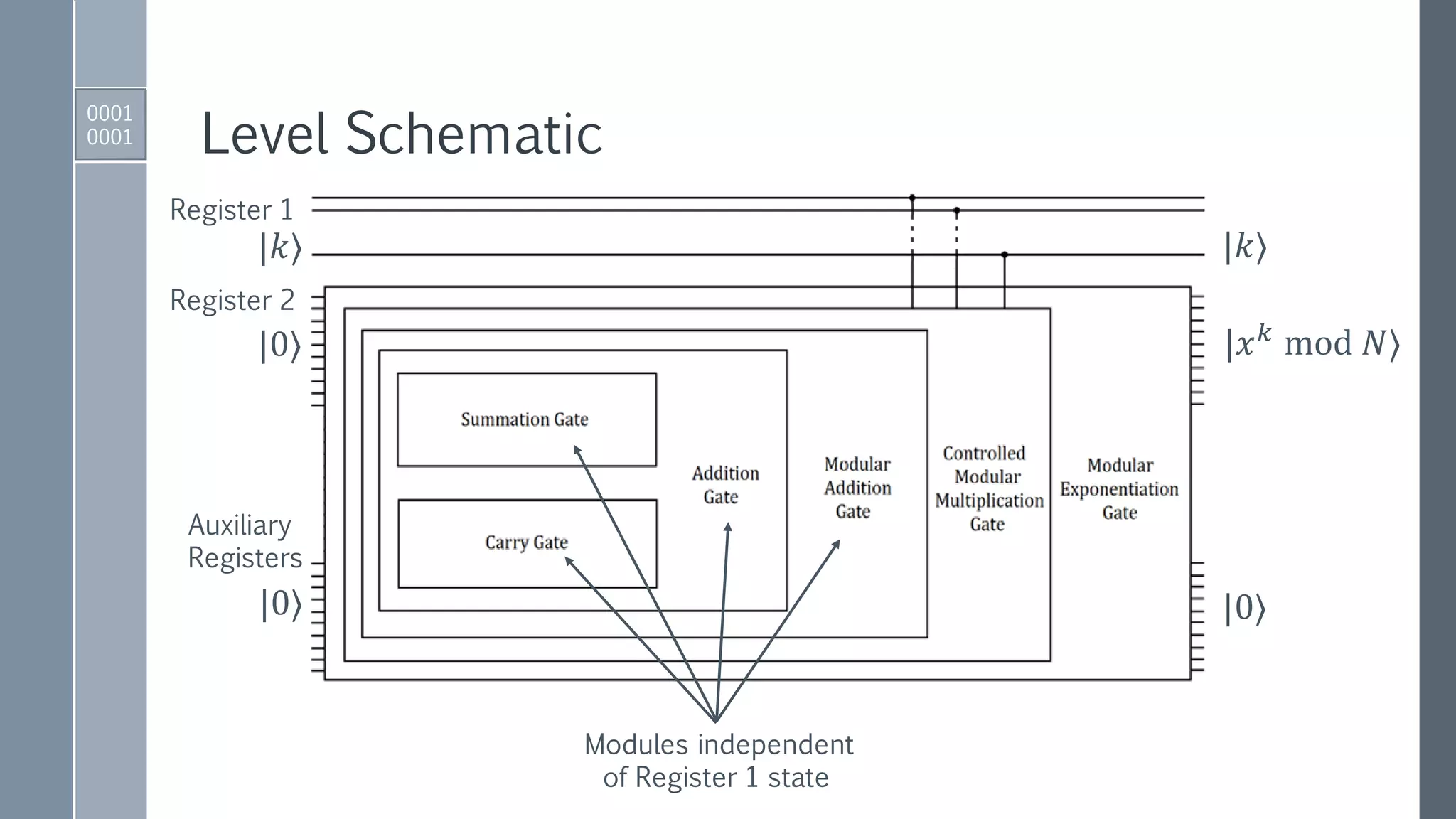
This document provides an exposition on Shor's algorithm and its implementation using quantum circuits and various quantum programming tools including Rigetti's Pyquil, Microsoft's Q#/C#, and IBM's Qiskit. It covers quantum arithmetic circuits, detailed descriptions of Shor's algorithm, and classical examples for understanding the quantum period finding process. Additionally, it discusses the architecture and qubit requirements for successfully factoring large numbers using quantum computing techniques.




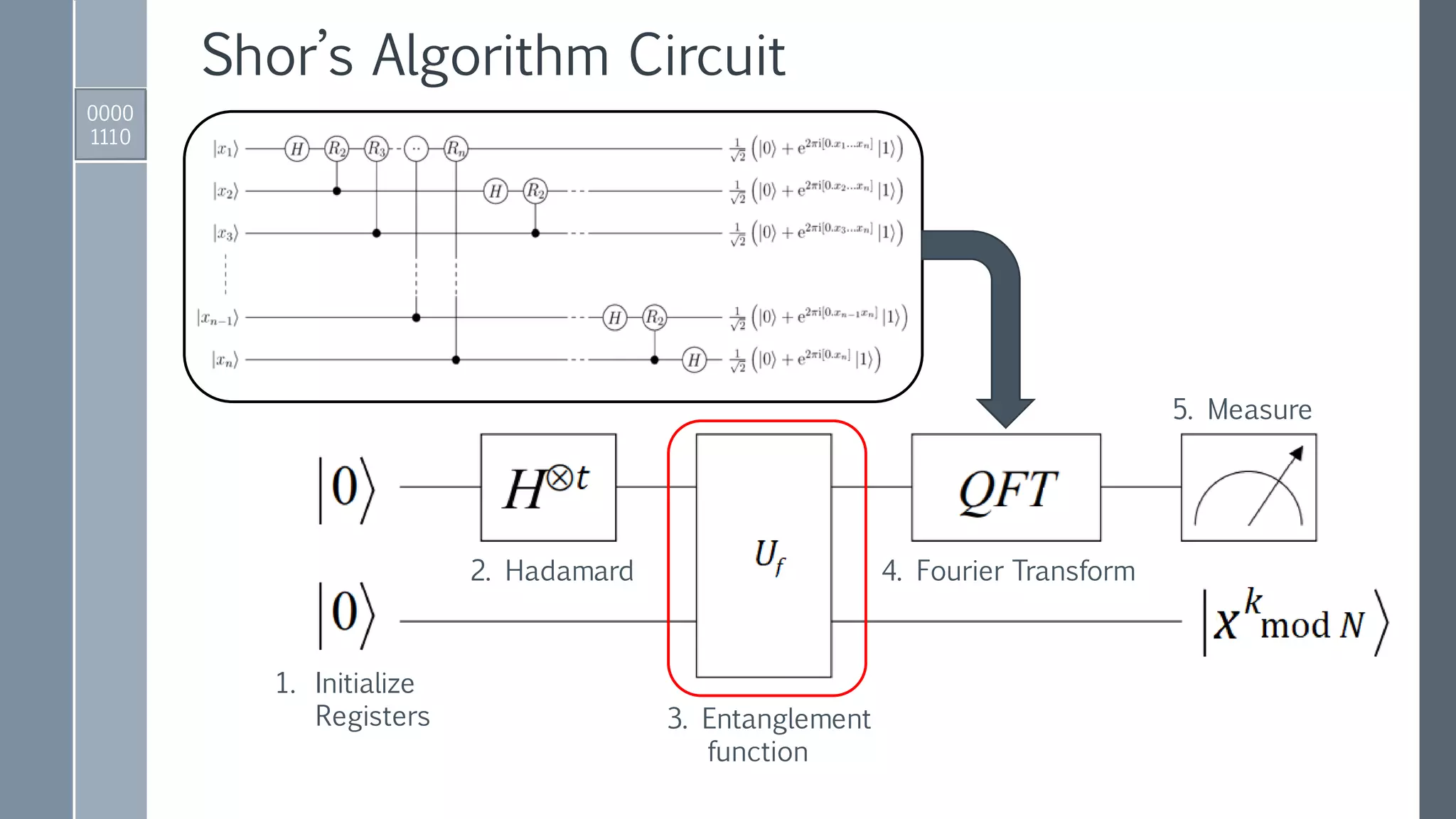
![Quantum Period Finding
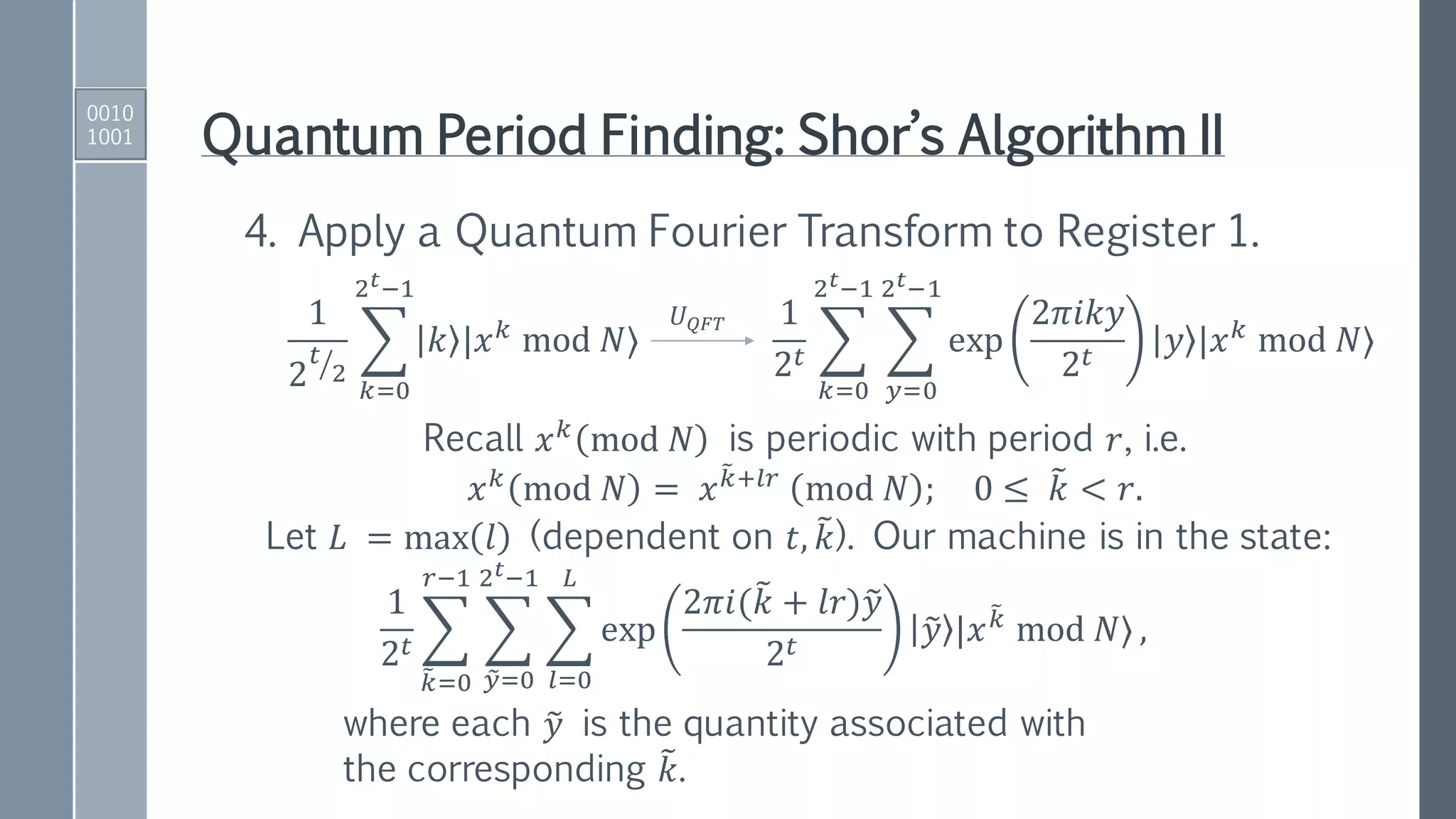
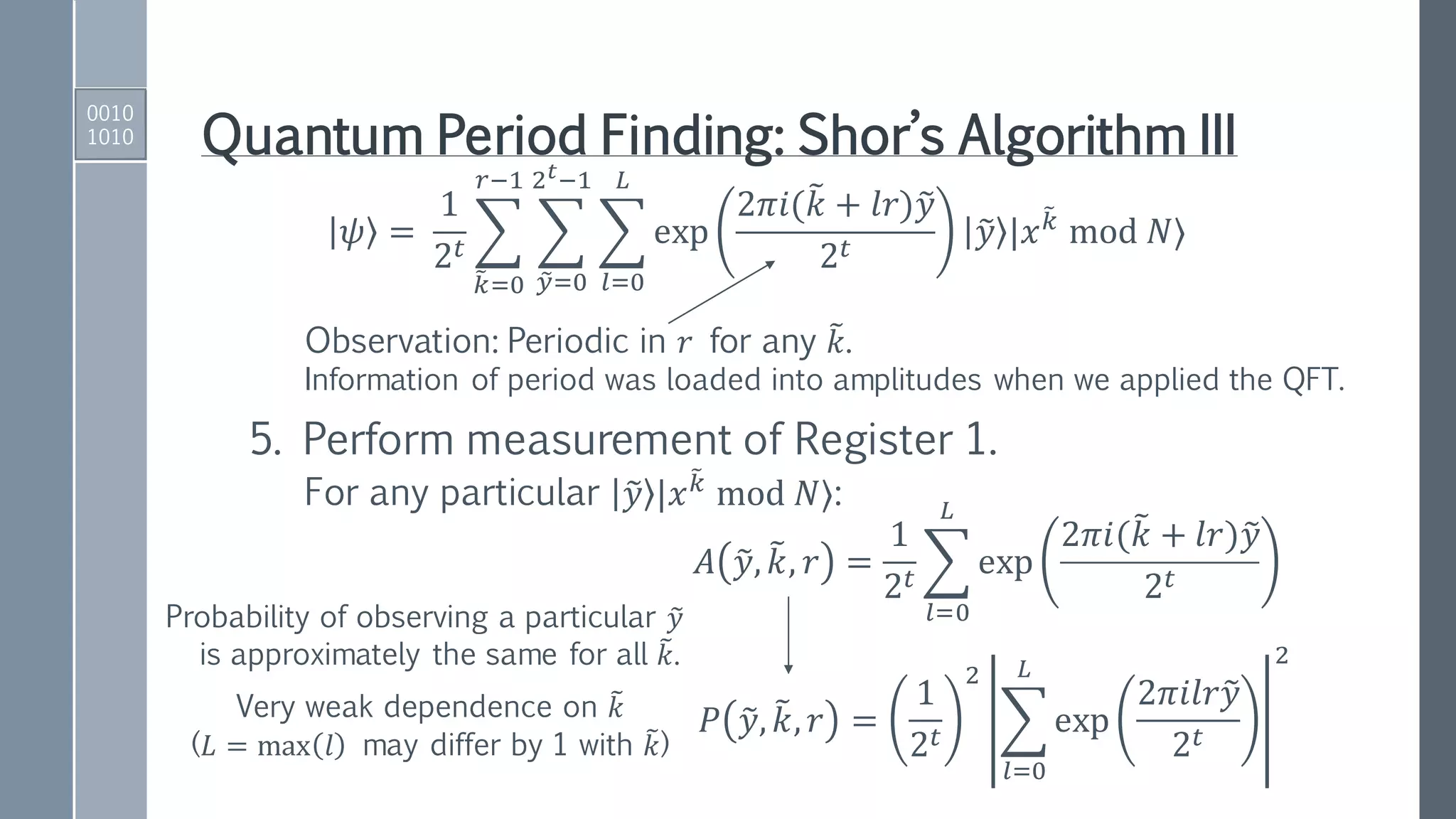
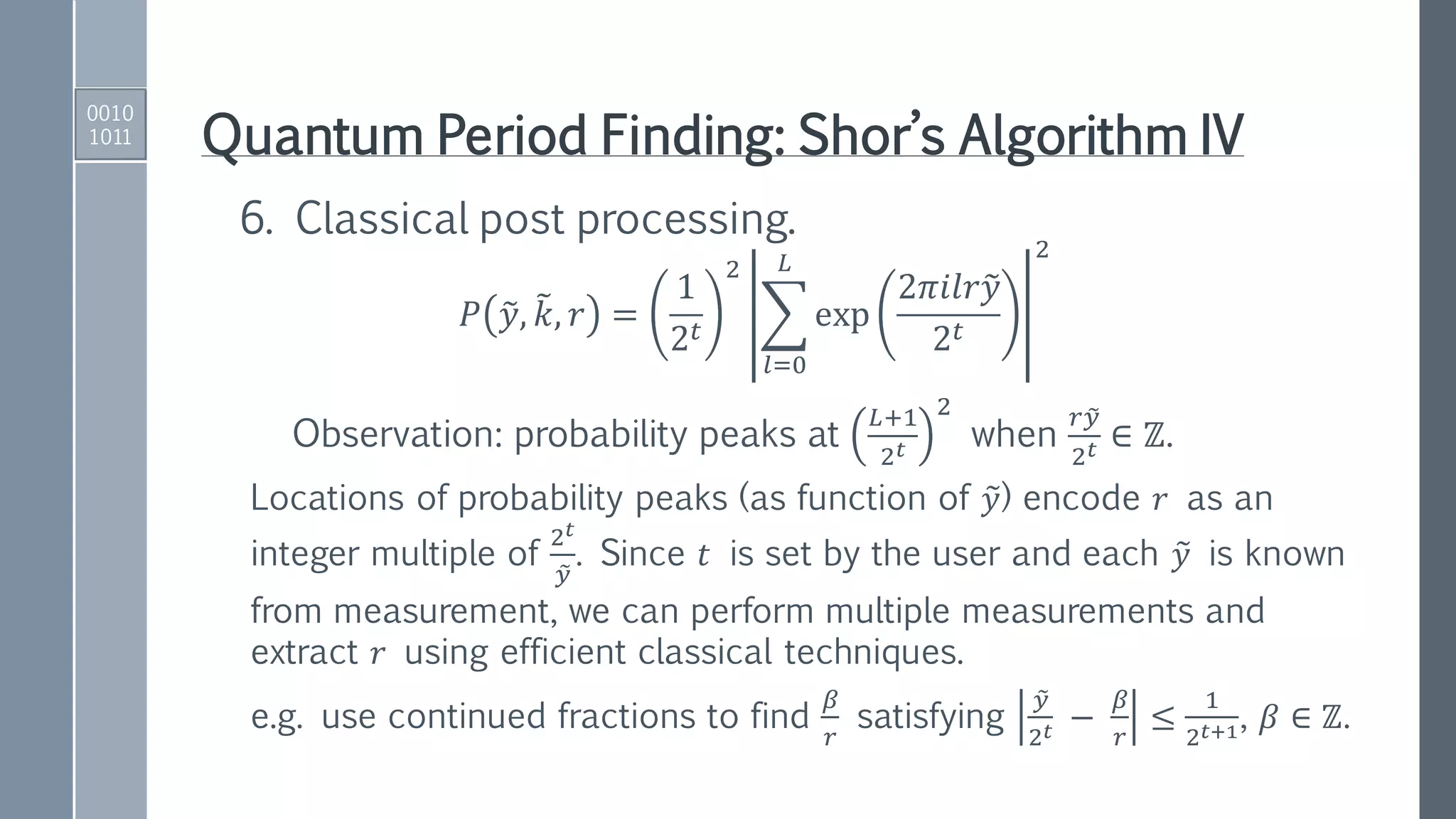
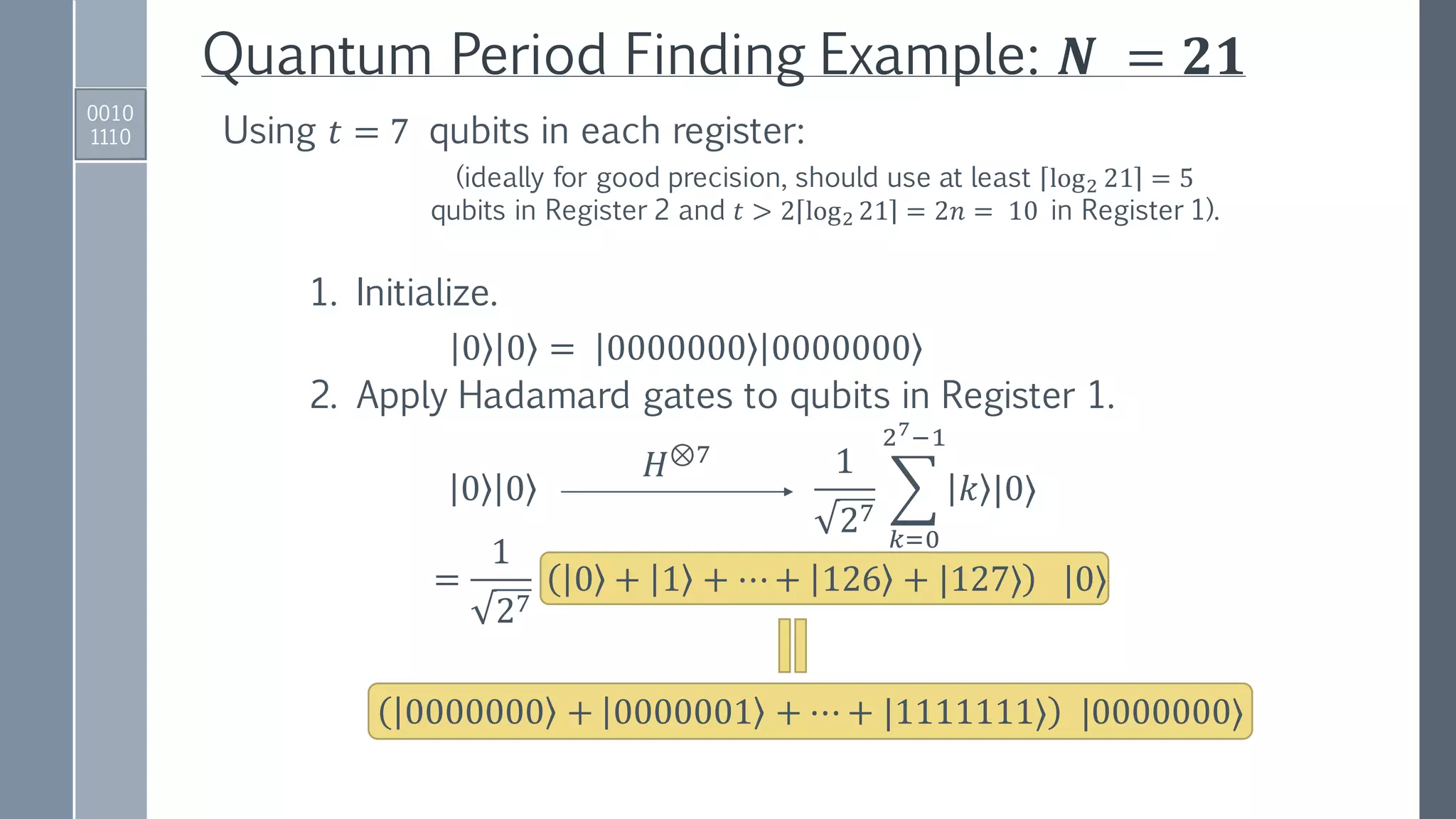
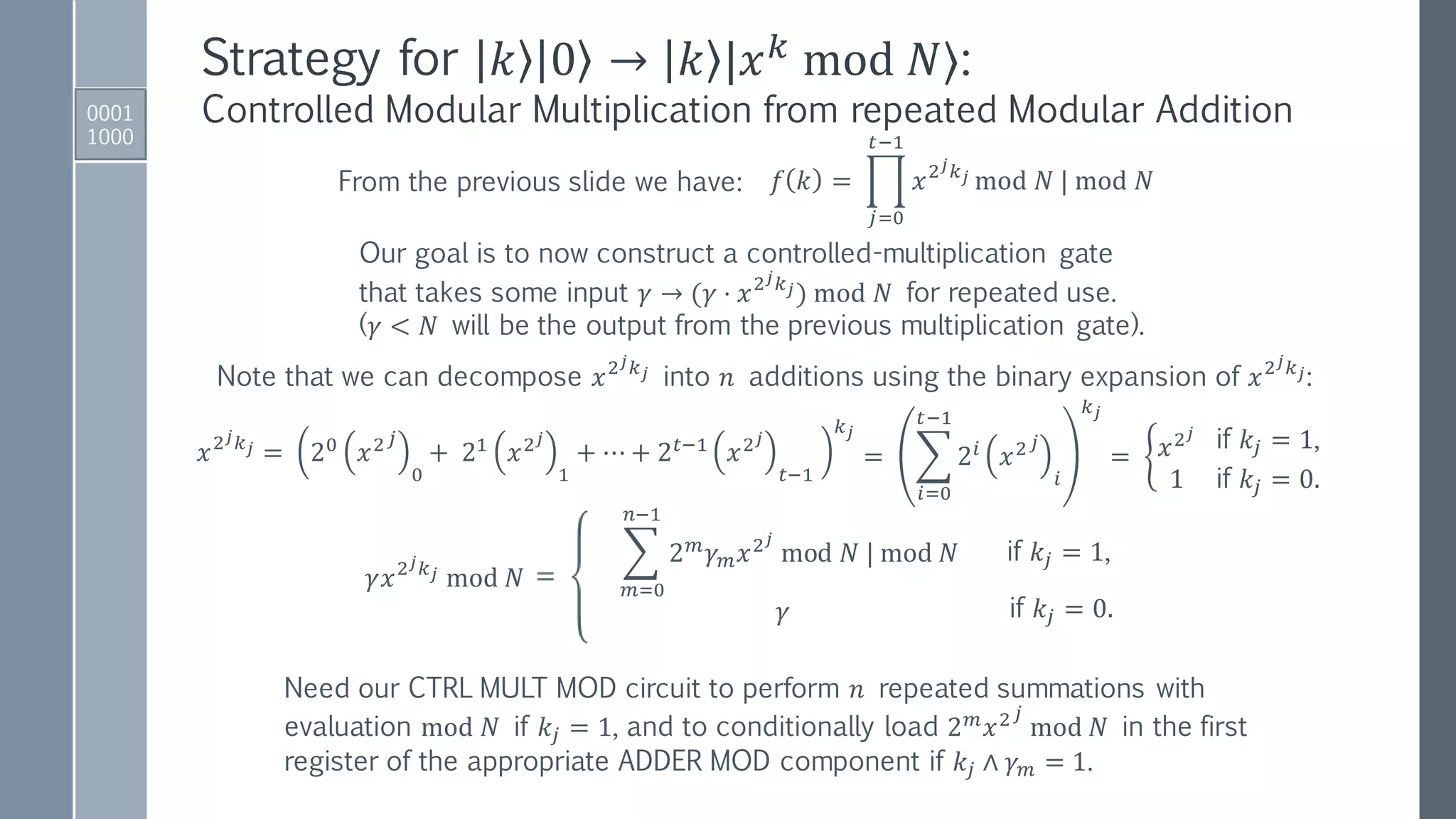
1. Initialize registers to zero-position.
00 … 00 00 …00 = 0 |0⟩
|Register 1⟩ |Register 2⟩
2. Apply Hadamard gates to the 𝑡 qubits in Register 1.
𝑡 qubits in Register 1 to encode
integers [0, …, 2 𝑡
− 1] in binary;
𝑡 larger than 2𝑛 = 2 log2 𝑁 .
0 0
1
2 ൗ𝑡
2
𝑘=0
2 𝑡−1
𝑘 |0⟩
𝐻⊗𝑡
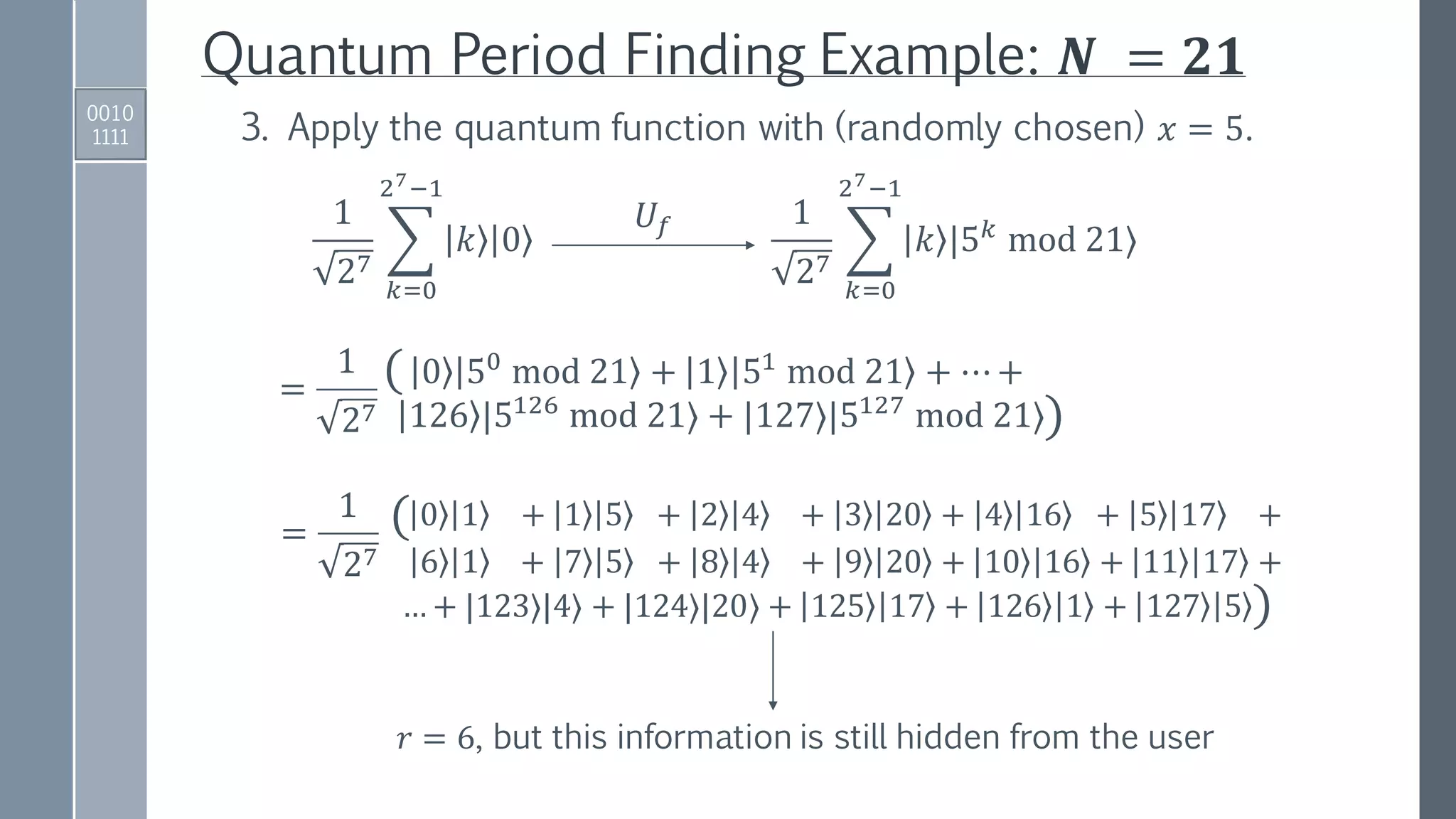
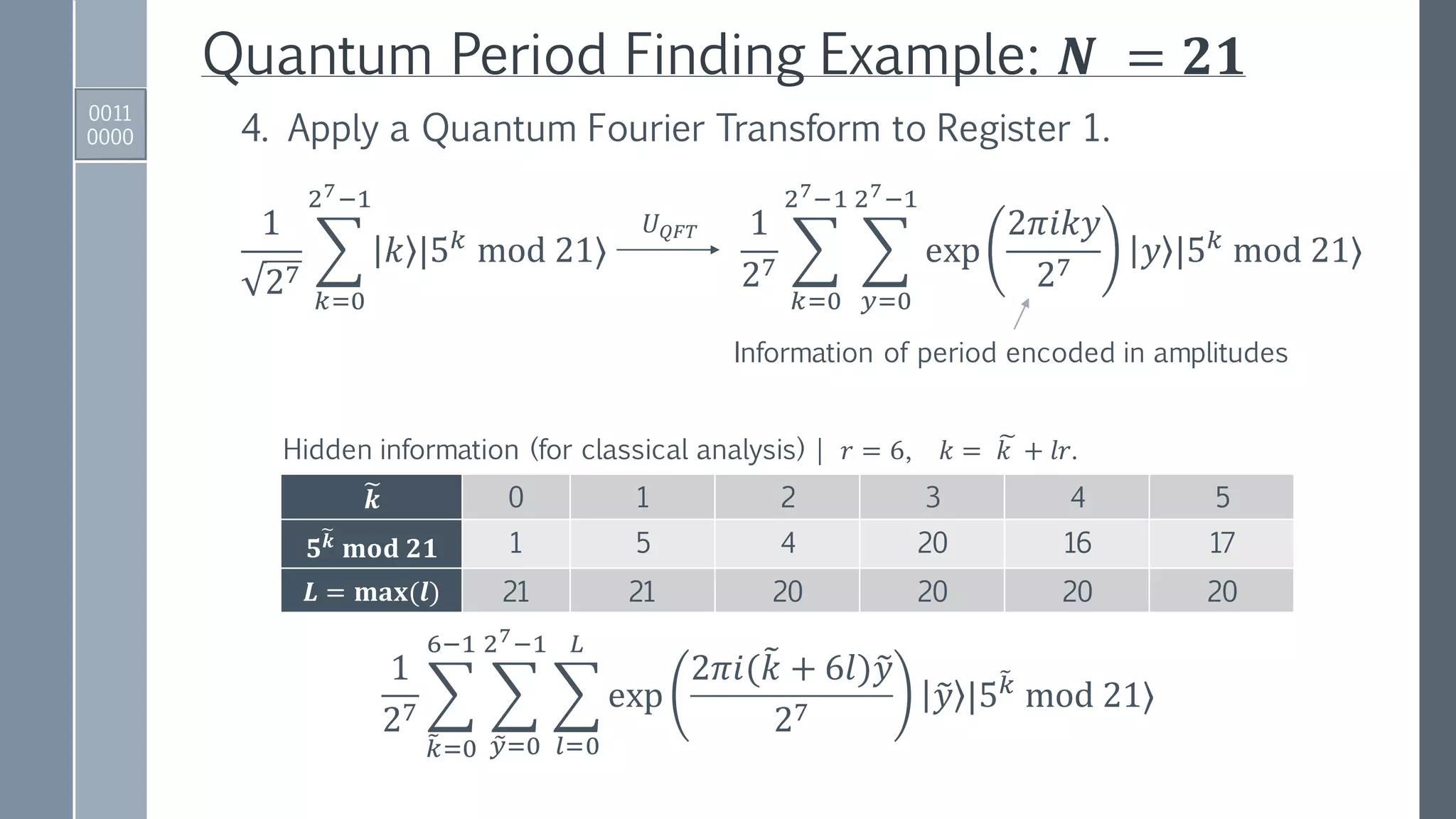
3. Apply a quantum function that performs the map:
𝑈𝑓1
2 ൗ𝑡
2
𝑘=0
2 𝑡−1
𝑘 0
1
2 ൗ𝑡
2
𝑘=0
2 𝑡−1
𝑘 |𝑥 𝑘
mod 𝑁⟩
0000
1100](https://image.slidesharecdn.com/shorsalgorithm-180821211208/75/Cryptanalysis-with-a-Quantum-Computer-An-Exposition-on-Shor-s-Factoring-Algorithm-12-2048.jpg)

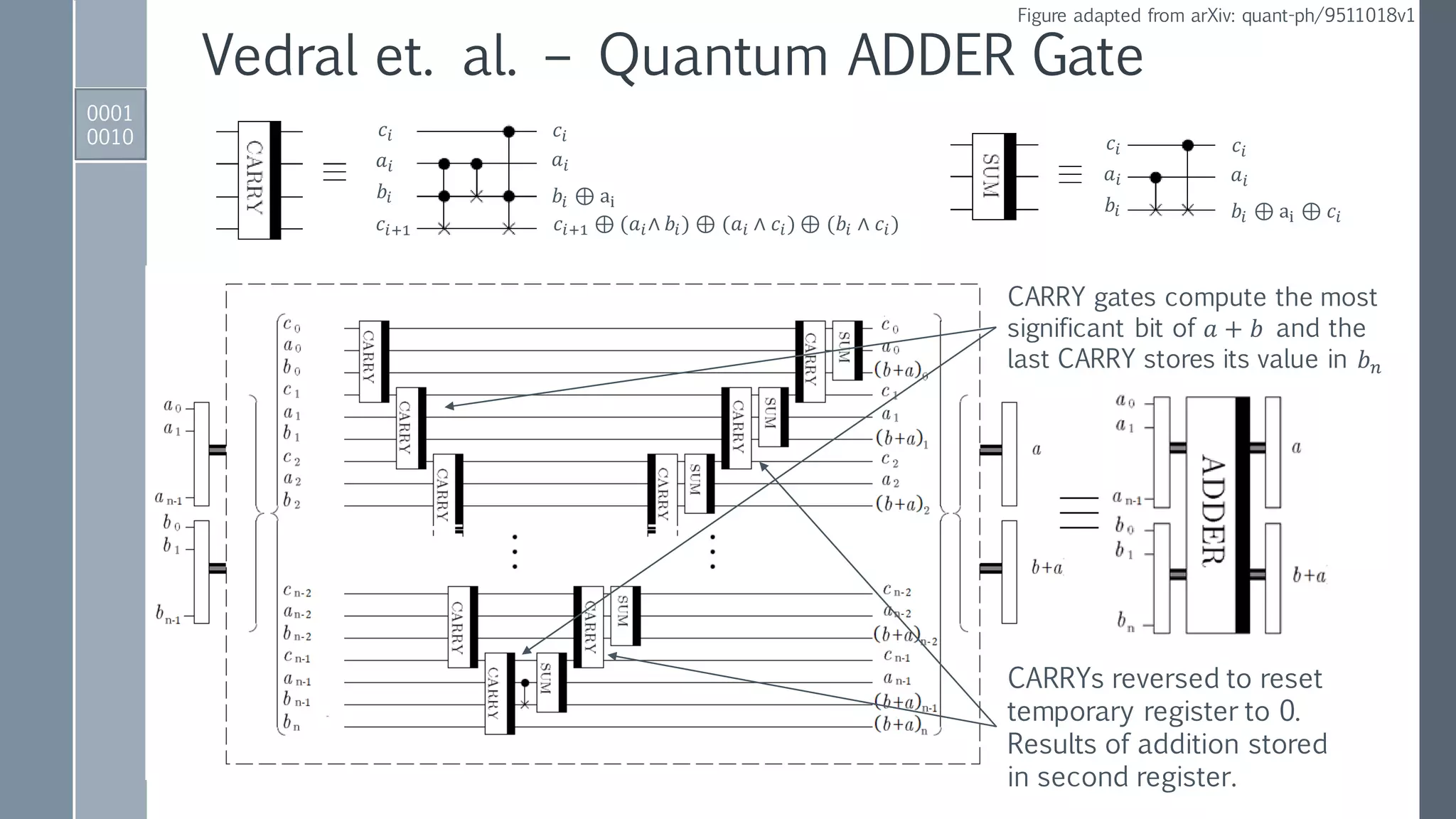
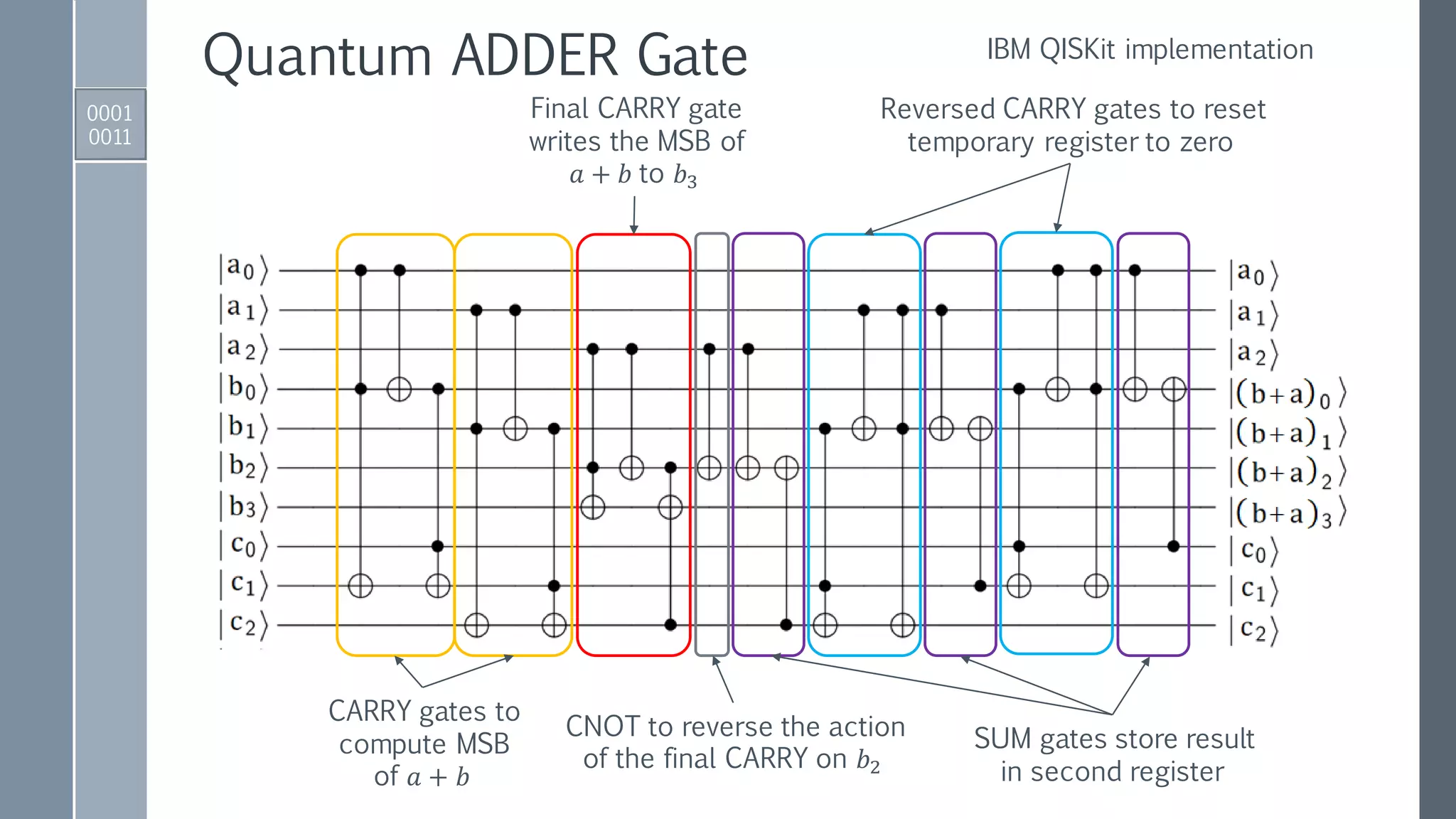
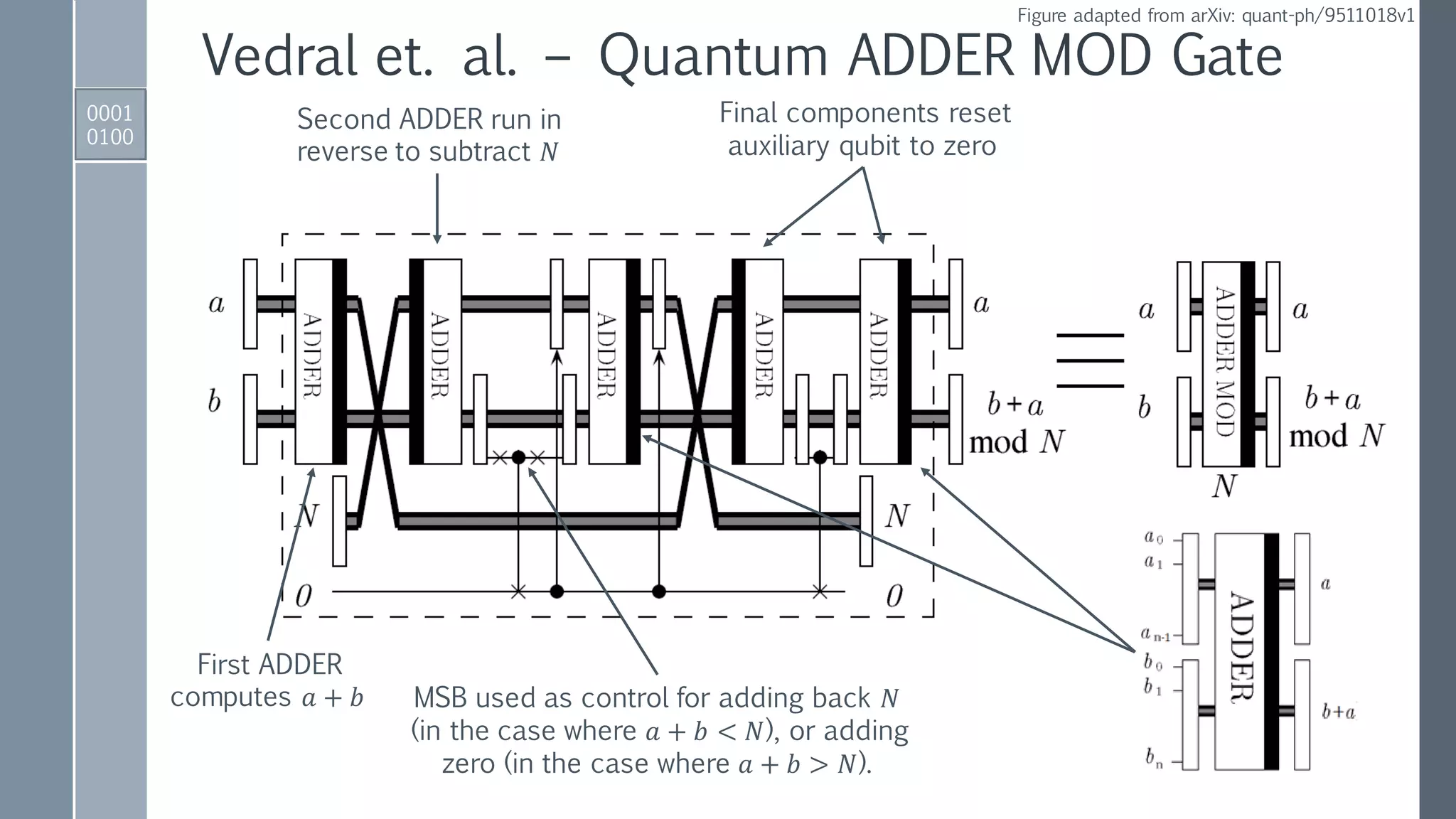
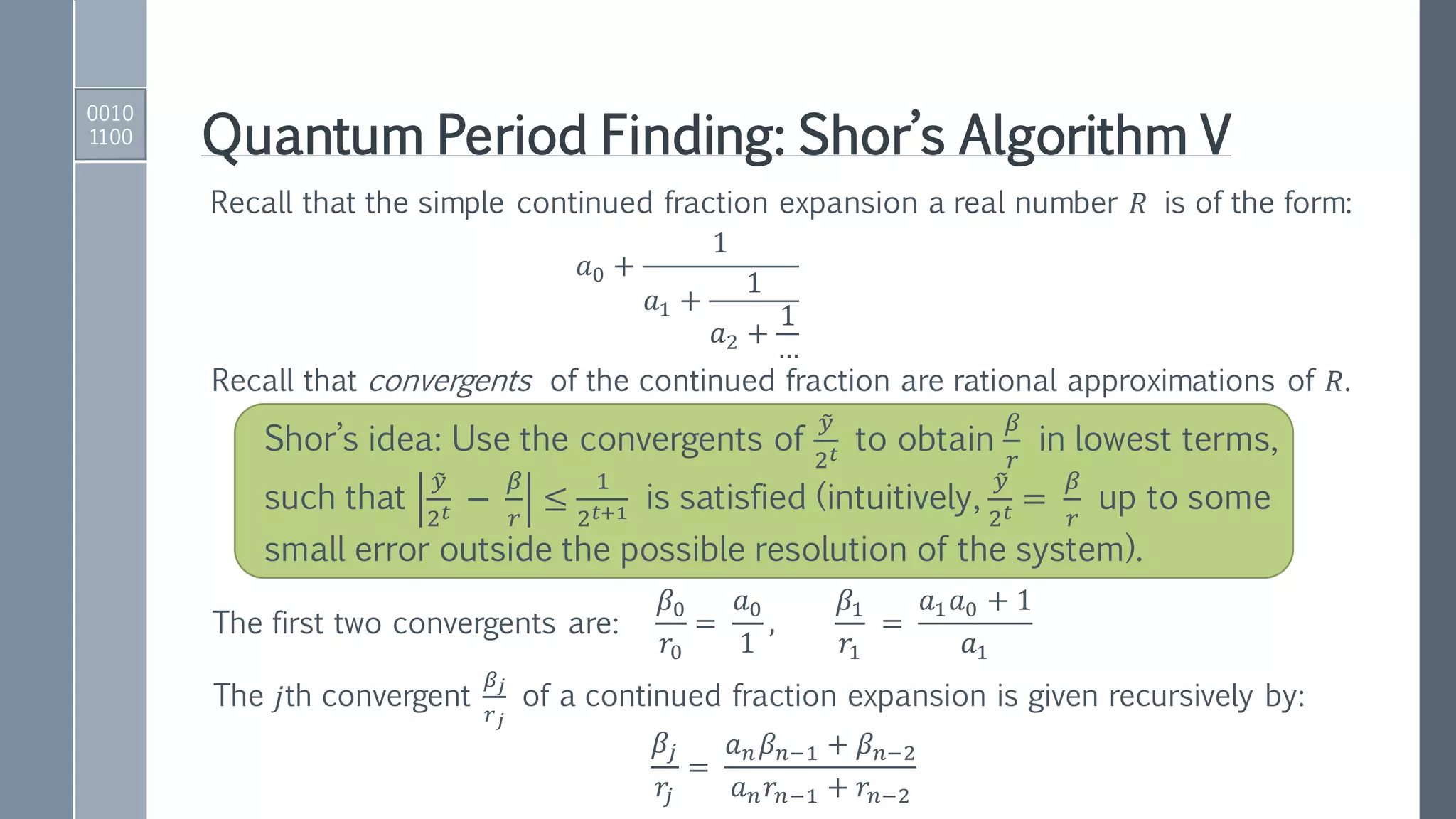
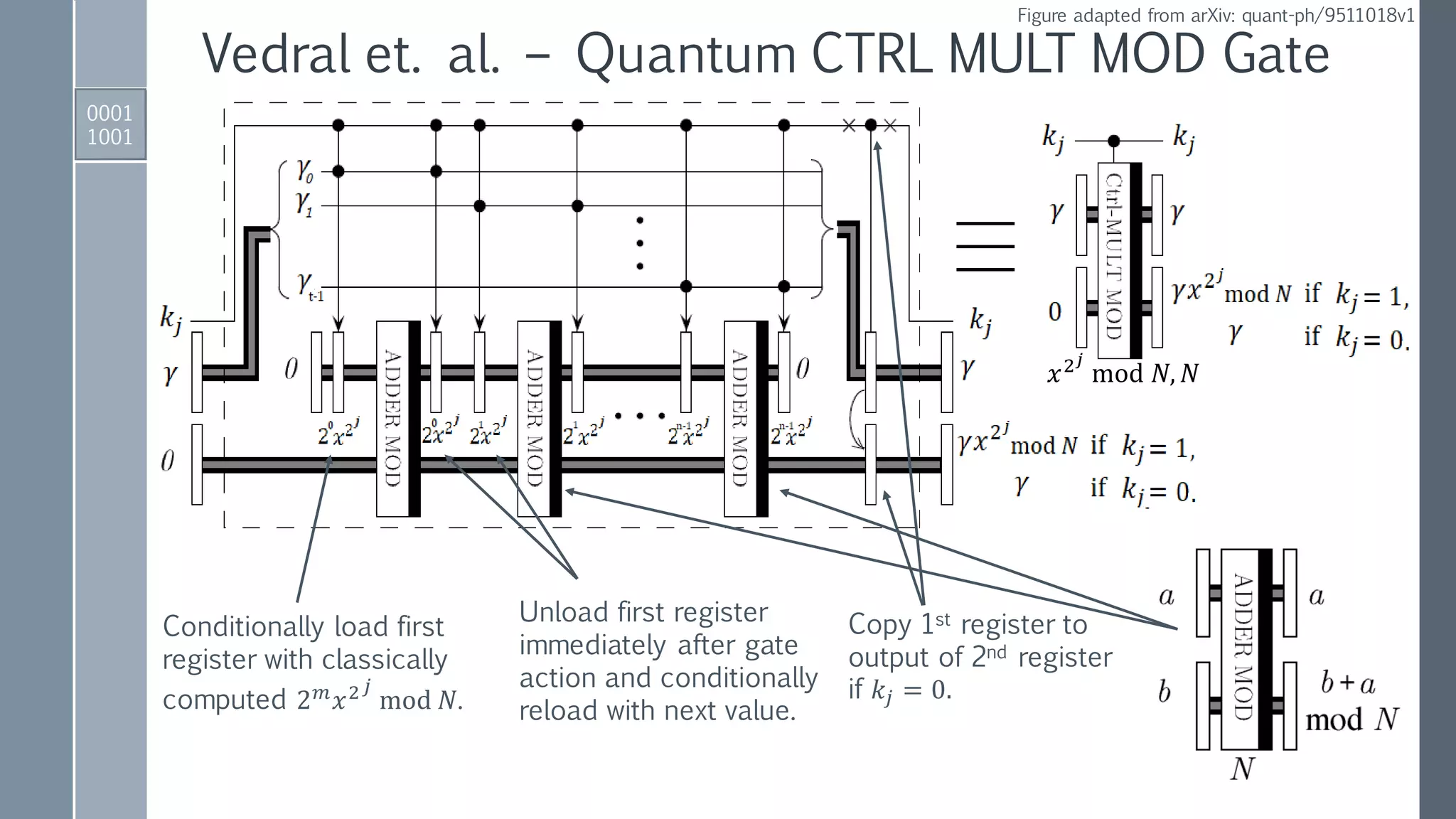
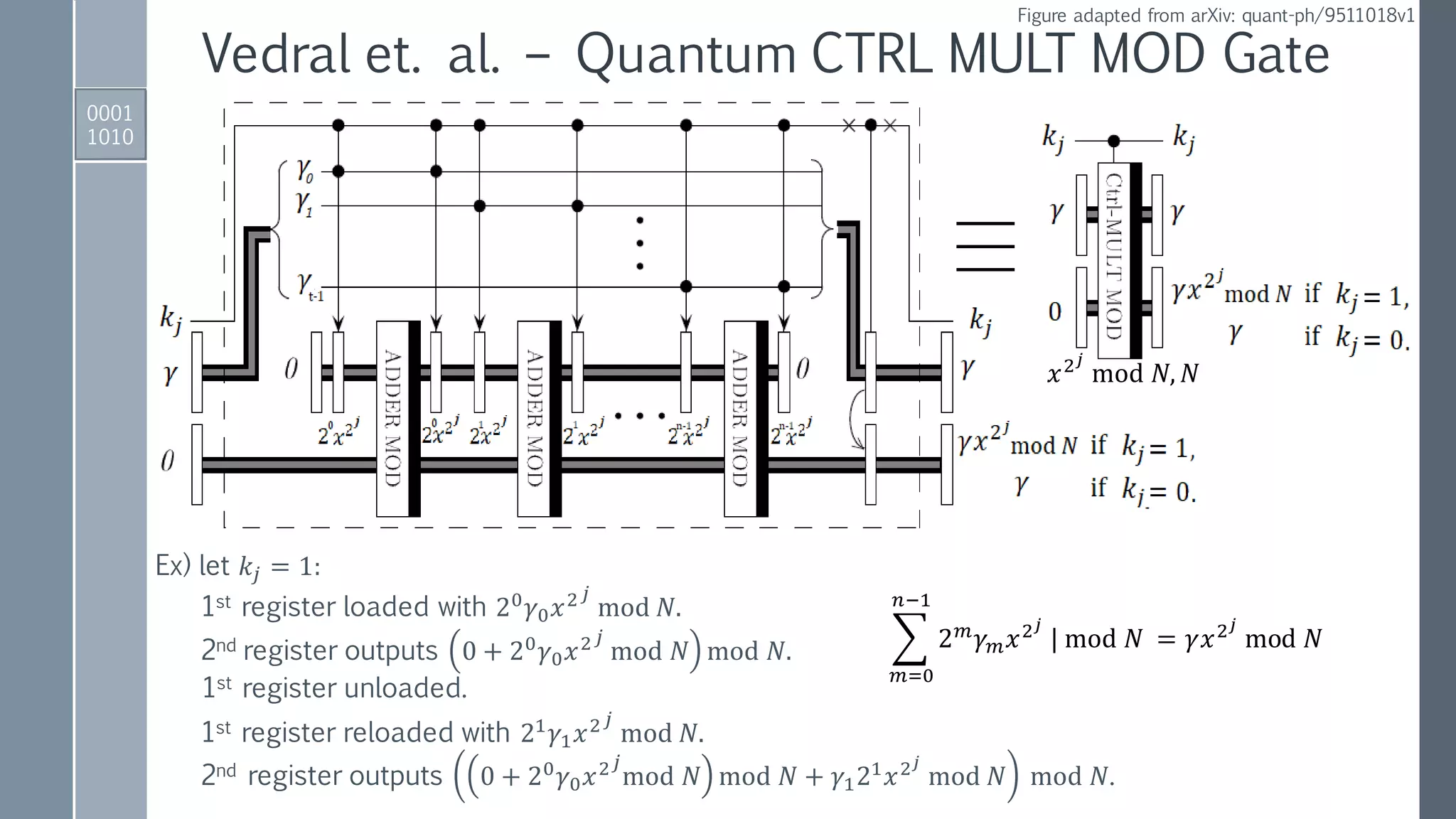
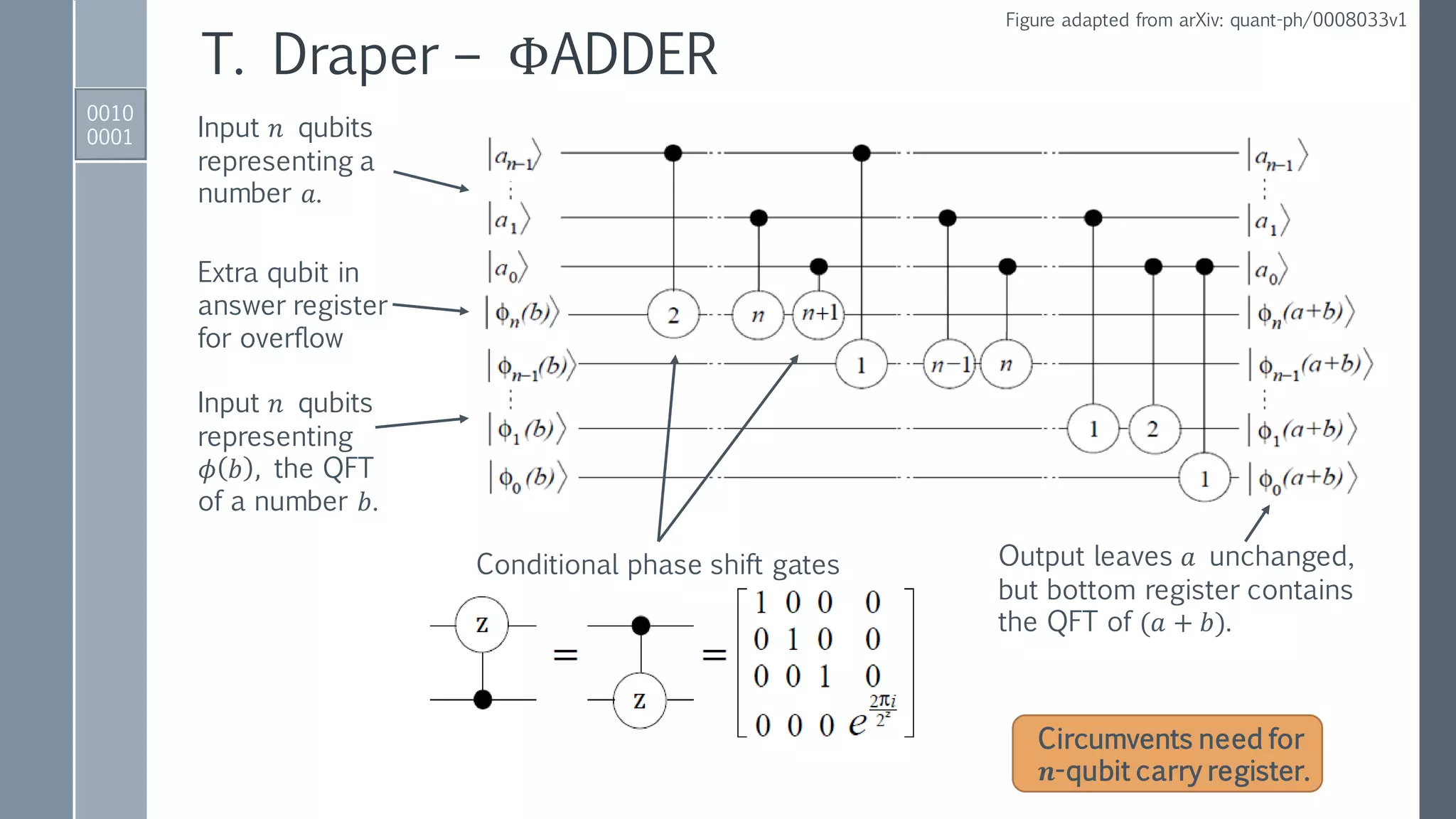
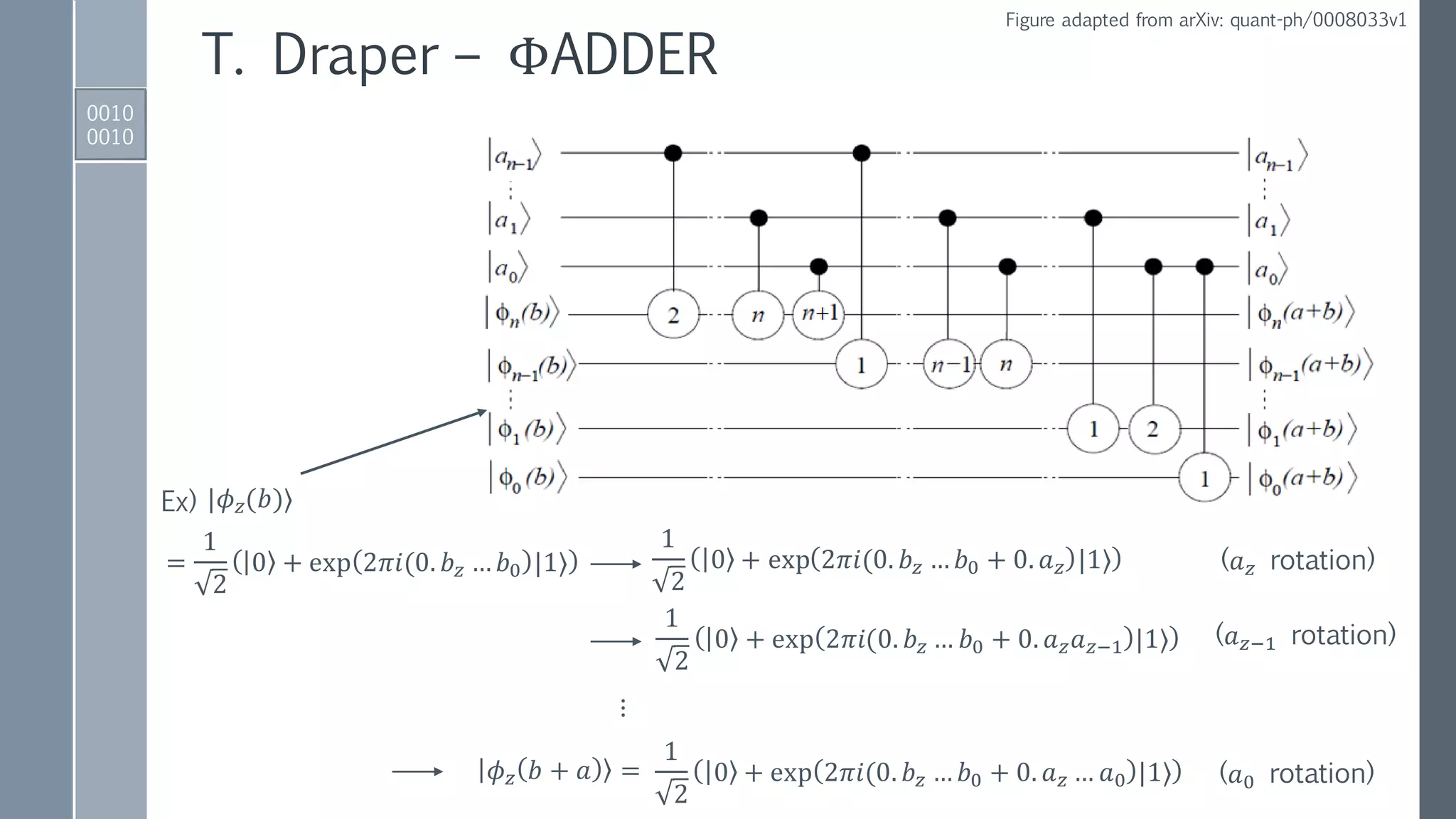
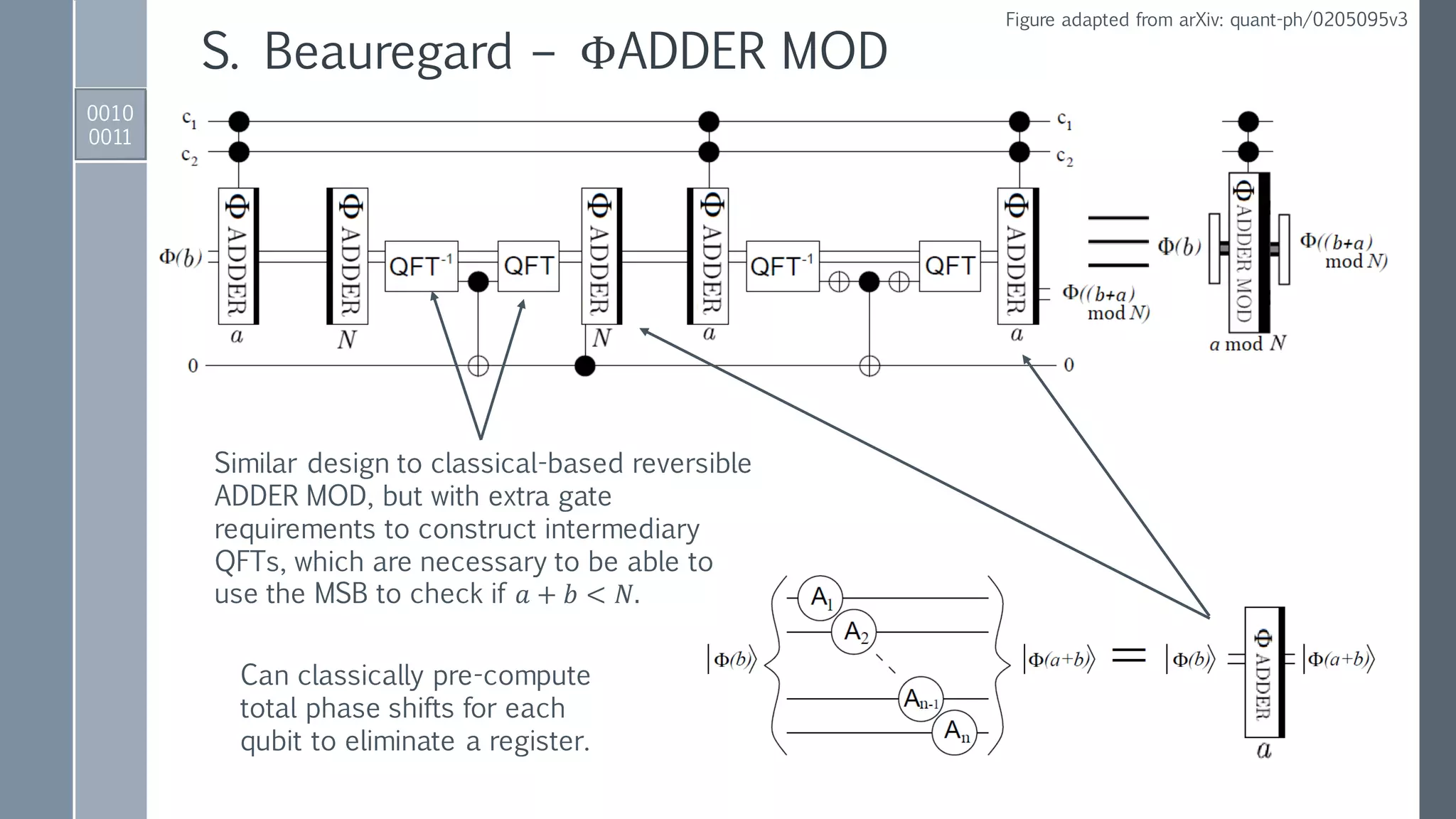
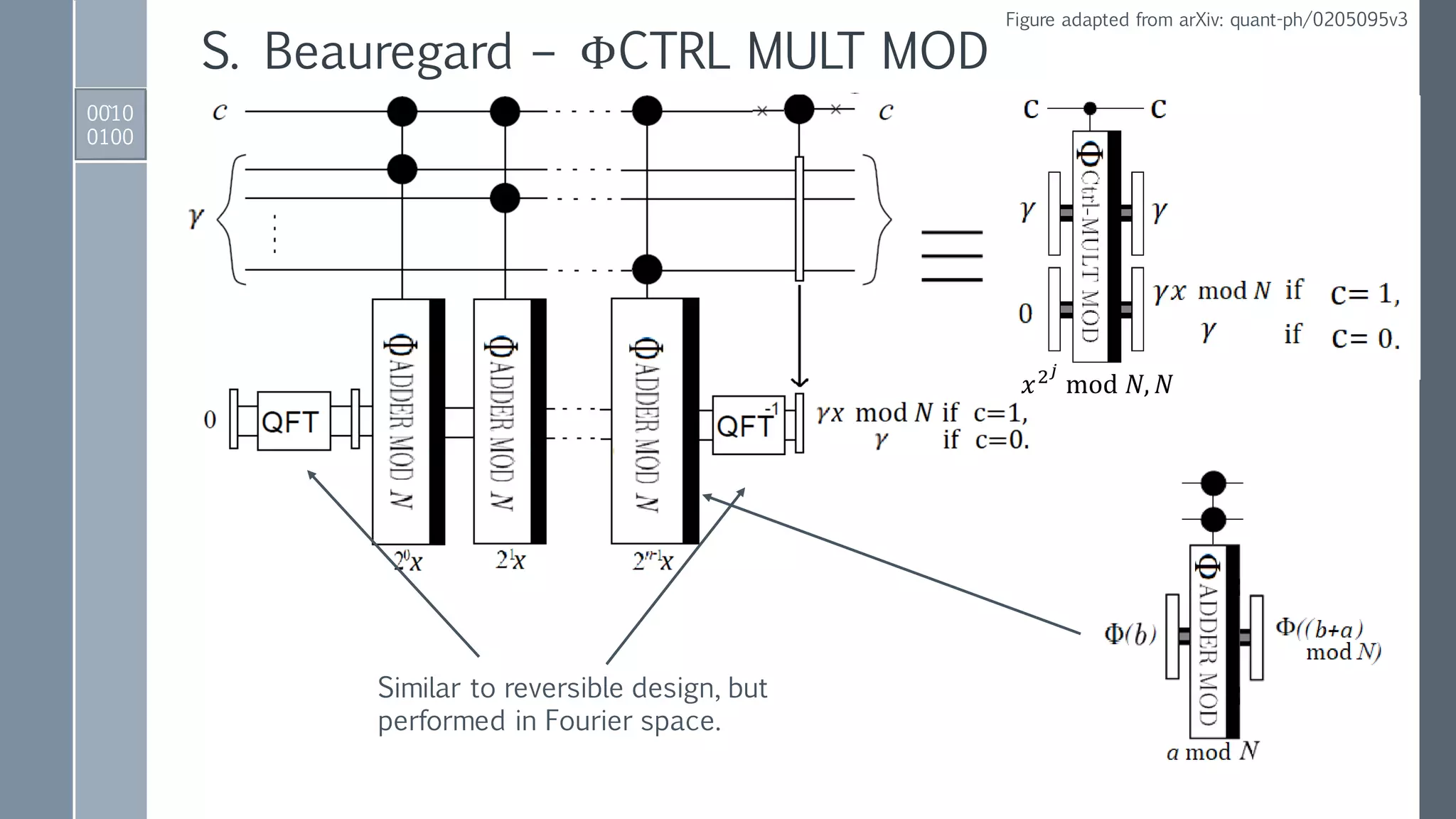
![Quantum ADDER MOD Gate
0001
0101
IBM QISKit implementation
ADDER gate to perform
𝑎, 𝑏 → |𝑎, 𝑎 + 𝑏⟩.
Reversed ADDER gate to perform:
𝑁, (𝑎 + 𝑏) → |𝑁,(𝑎 + 𝑏) − 𝑁⟩ if 𝑁 < 𝑎 + 𝑏,
𝑁, (𝑎 + 𝑏) → |𝑁, 2 𝑛+1−[𝑁 − 𝑎 + 𝑏 ]⟩ if 𝑁 > 𝑎 + 𝑏.
Conditionally set 𝑁-register to zero
if 𝑁 < 𝑎 + 𝑏 using MSB as control.
Conditionally add
either 0 or 𝑁 to
second register.
Conditionally
restore 𝑁-register.
Reversed
modules to
reset auxiliary.](https://image.slidesharecdn.com/shorsalgorithm-180821211208/75/Cryptanalysis-with-a-Quantum-Computer-An-Exposition-on-Shor-s-Factoring-Algorithm-21-2048.jpg)
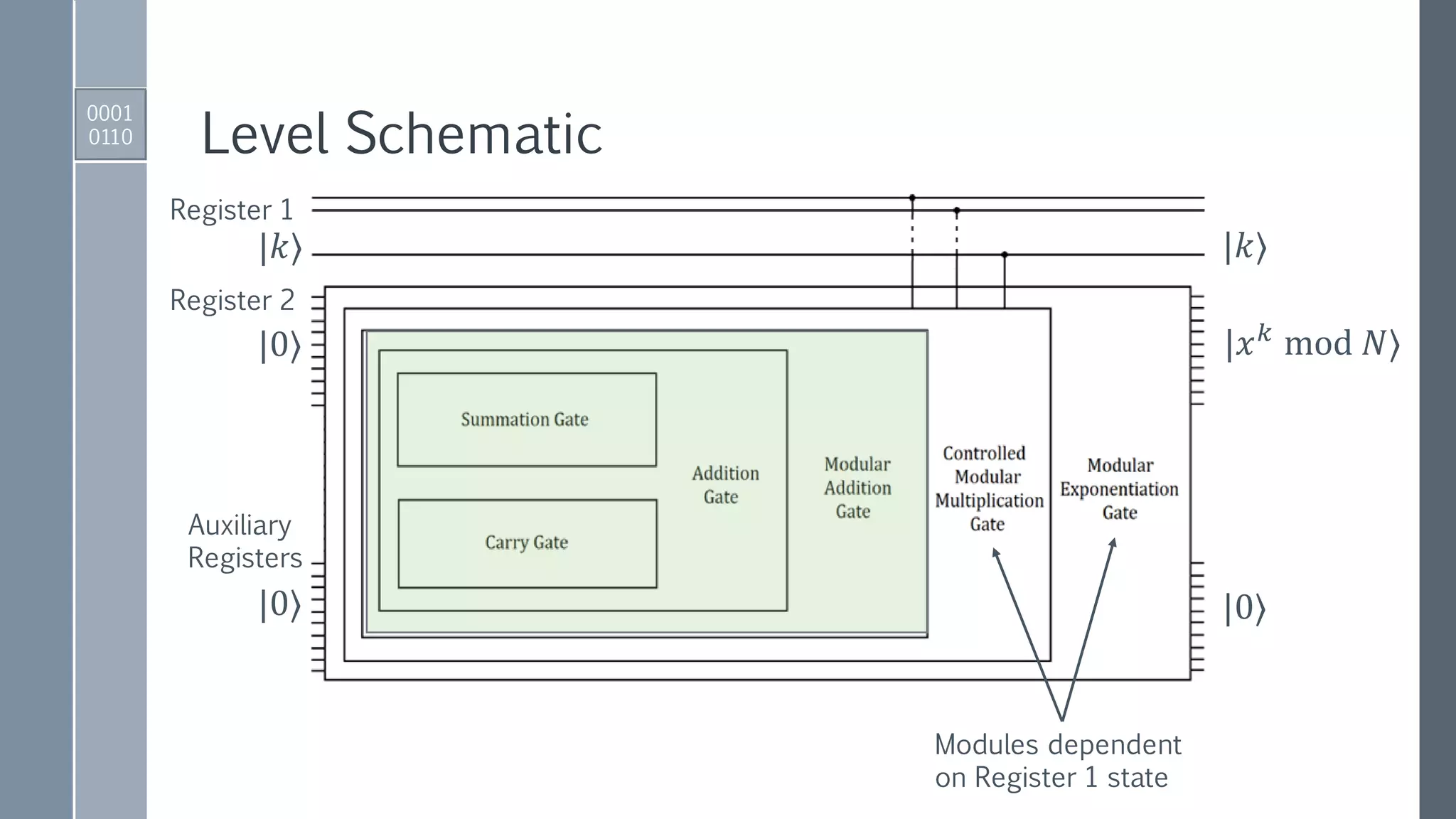
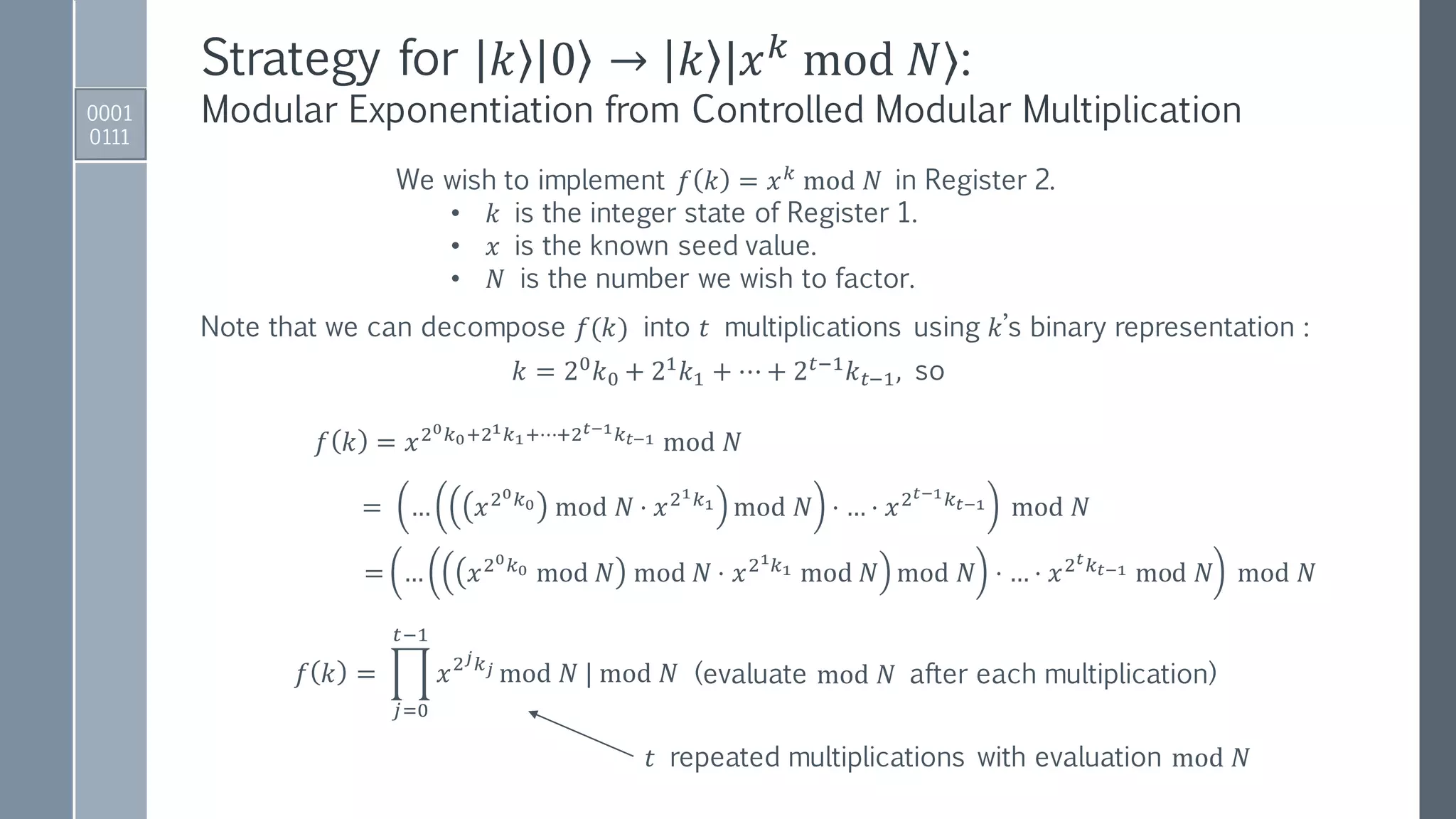
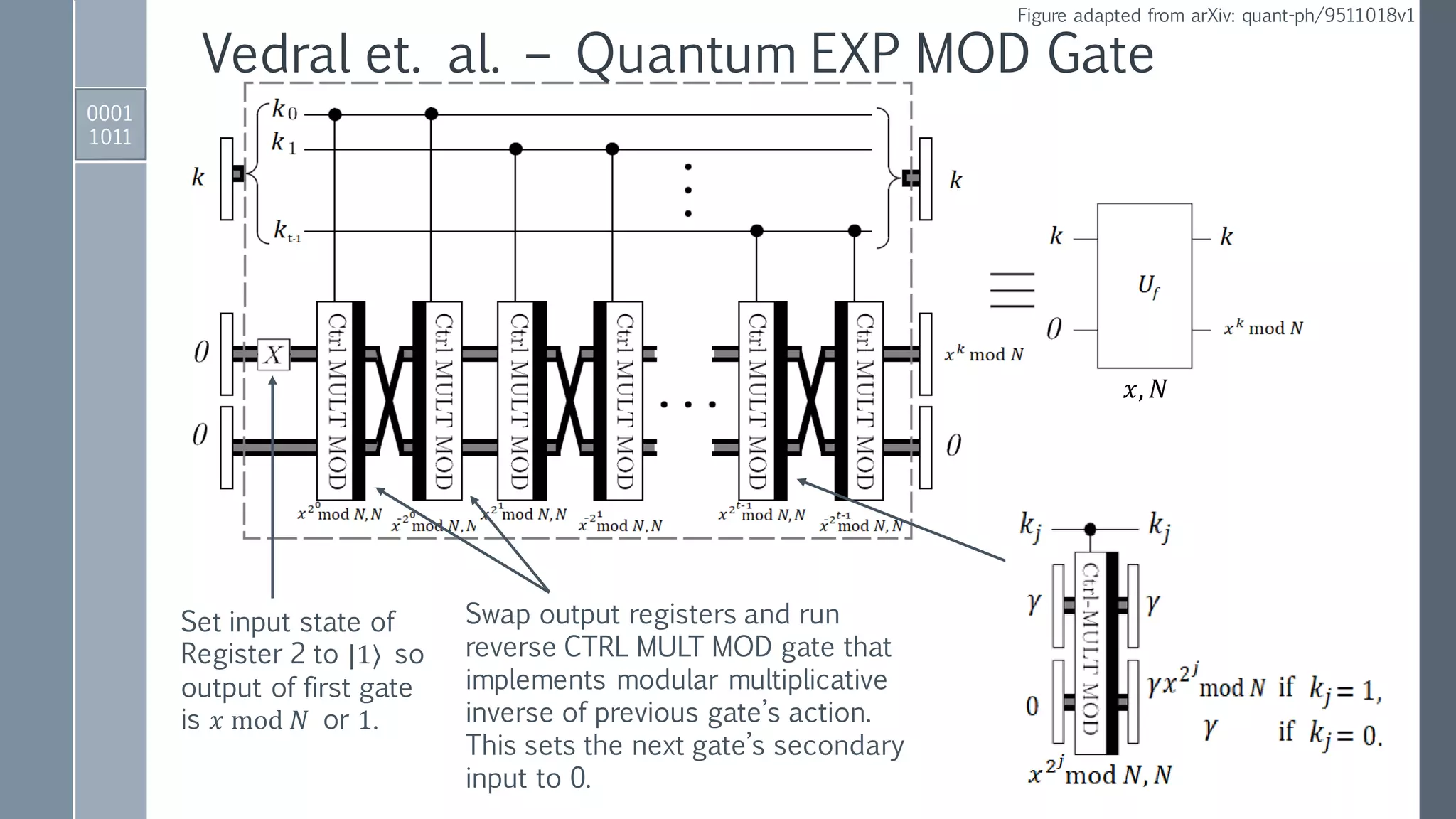

![Quantum Period Finding: Shor’s Algorithm I
1. Initialize registers to zero-position.
00 … 00 00 …00 = 0 |0⟩
|Register 1⟩ |Register 2⟩
2. Apply Hadamard gates to the 𝑡 qubits in Register 1.
0 0
1
2 ൗ𝑡
2
𝑘=0
2 𝑡−1
𝑘 |0⟩
𝐻⊗𝑡
3. Apply a quantum function that performs the map:
𝑈𝑓1
2 ൗ𝑡
2
𝑘=0
2 𝑡−1
𝑘 0
1
2 ൗ𝑡
2
𝑘=0
2 𝑡−1
𝑘 |𝑥 𝑘
mod 𝑁⟩
0010
1000
𝑡 qubits in Register 1 to encode
integers [0, …, 2 𝑡
− 1] in binary;
𝑡 larger than 2𝑛 = 2 log2 𝑁 .](https://image.slidesharecdn.com/shorsalgorithm-180821211208/75/Cryptanalysis-with-a-Quantum-Computer-An-Exposition-on-Shor-s-Factoring-Algorithm-40-2048.jpg)