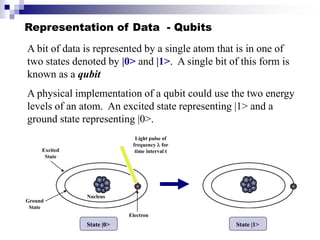
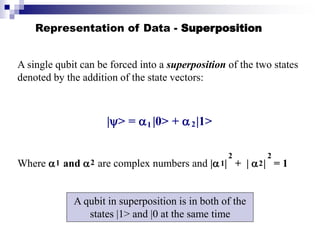
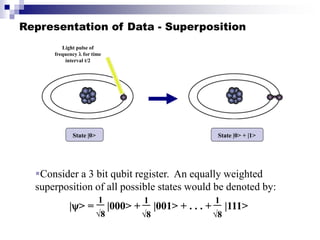
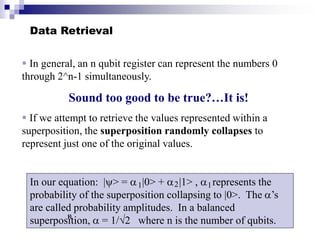
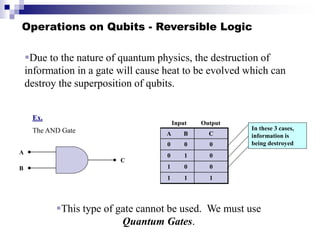
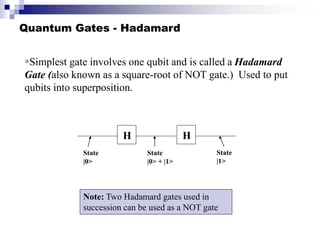
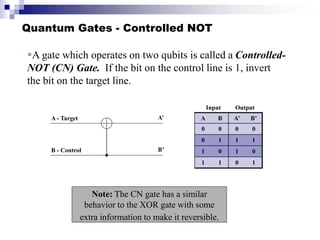
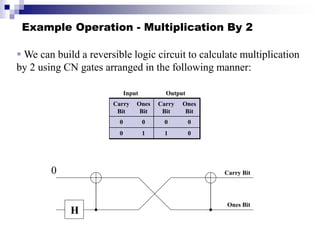
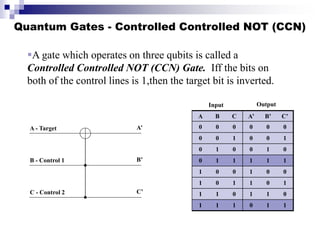
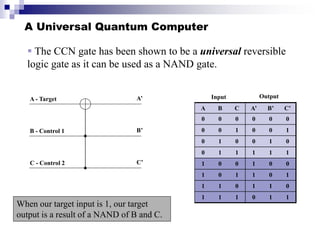
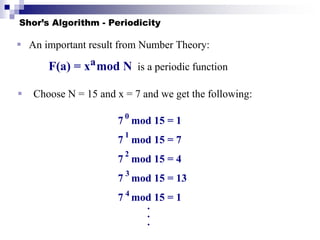
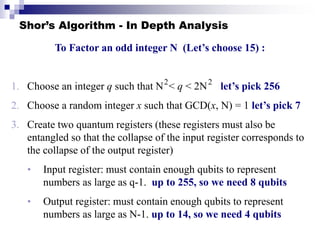
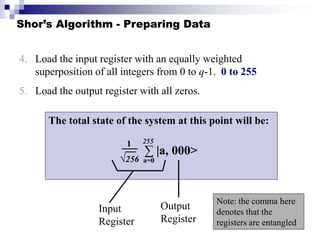
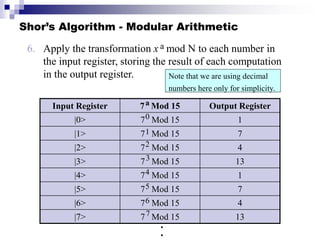
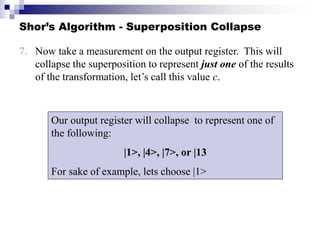
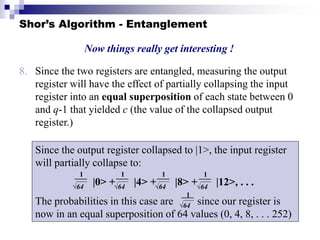
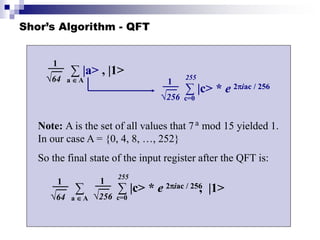
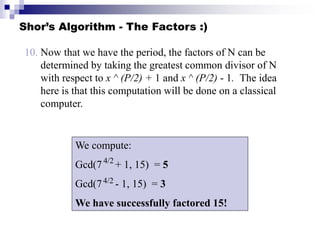
Quantum computing uses quantum mechanics principles to perform calculations. A qubit can represent a 1, 0, or superposition of both simultaneously. Operations are performed by reversible logic gates like CNOT. Shor's algorithm shows quantum computers can factor large numbers faster by using quantum Fourier transforms to find the period of a function, revealing the factors. While progress is being made, challenges remain in building larger quantum computers and developing new algorithms to solve other hard problems.