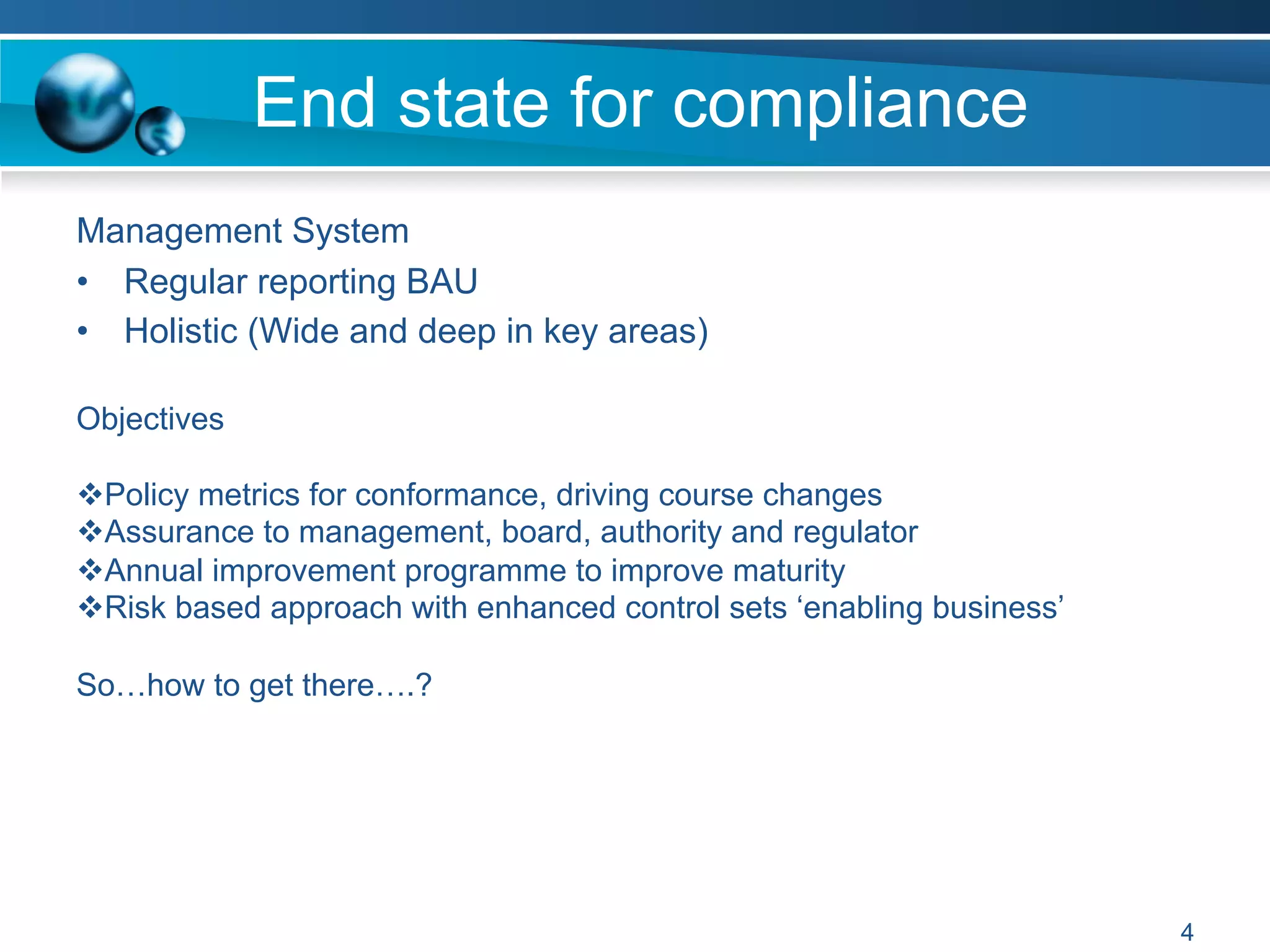
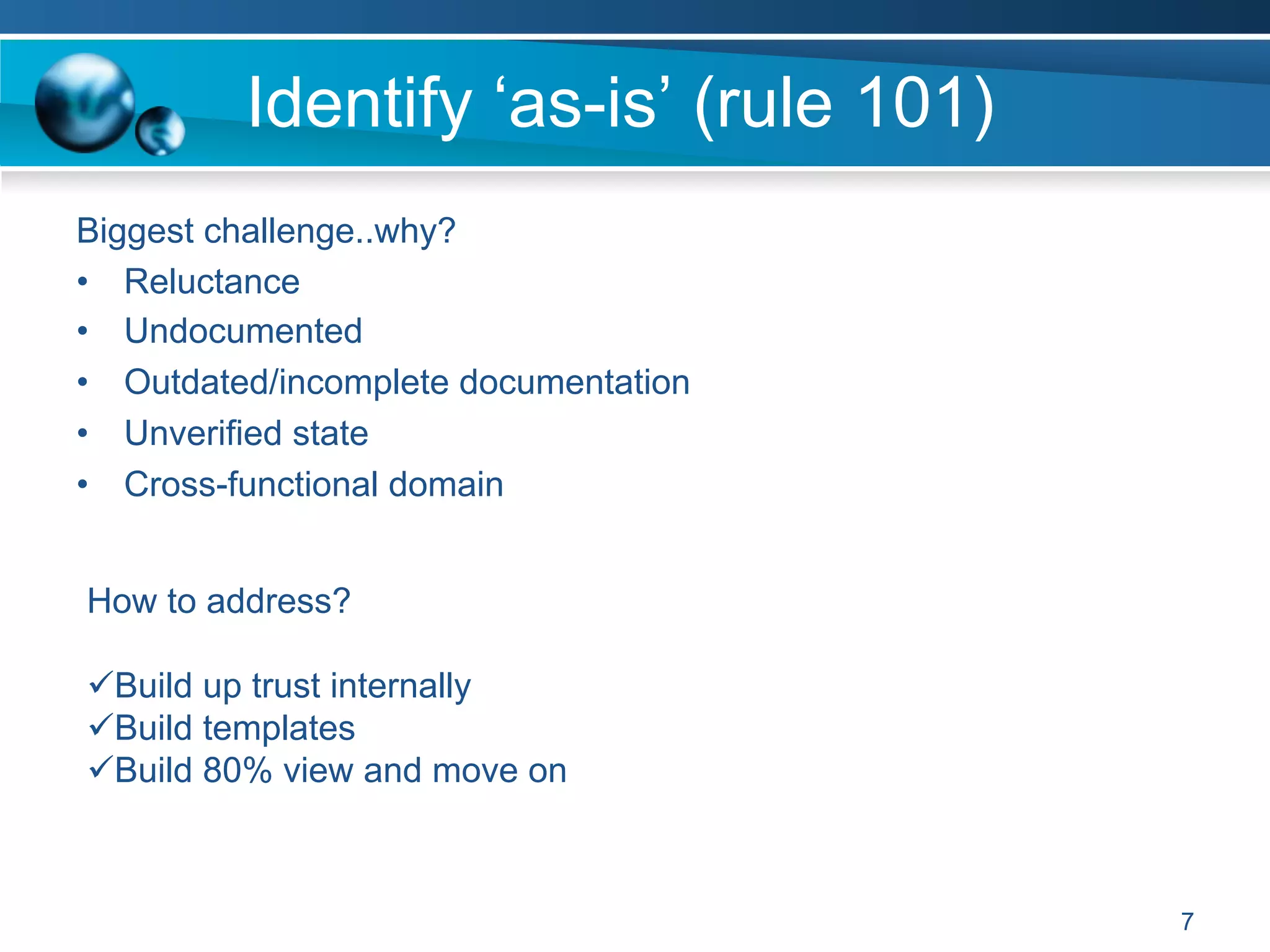
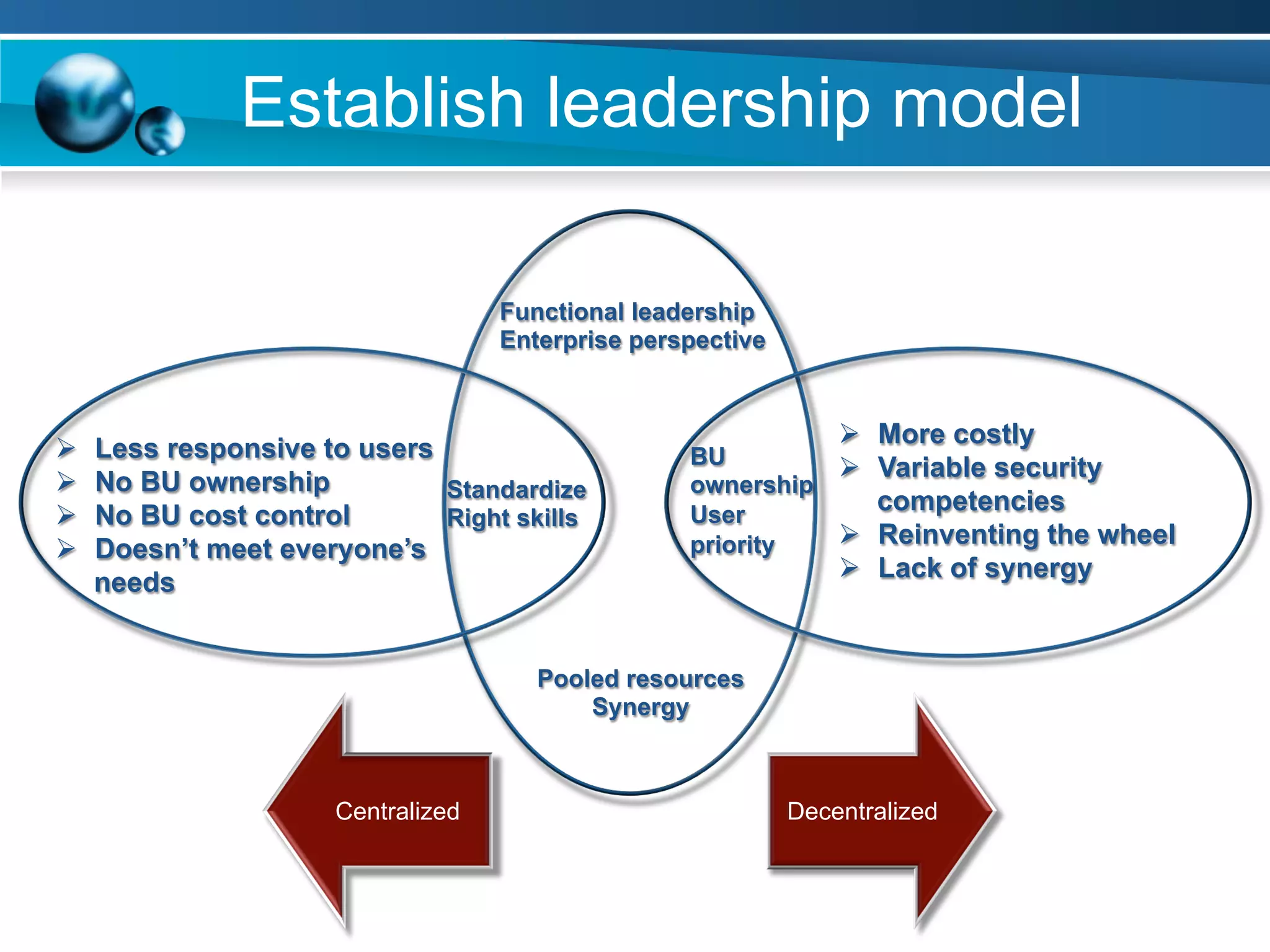
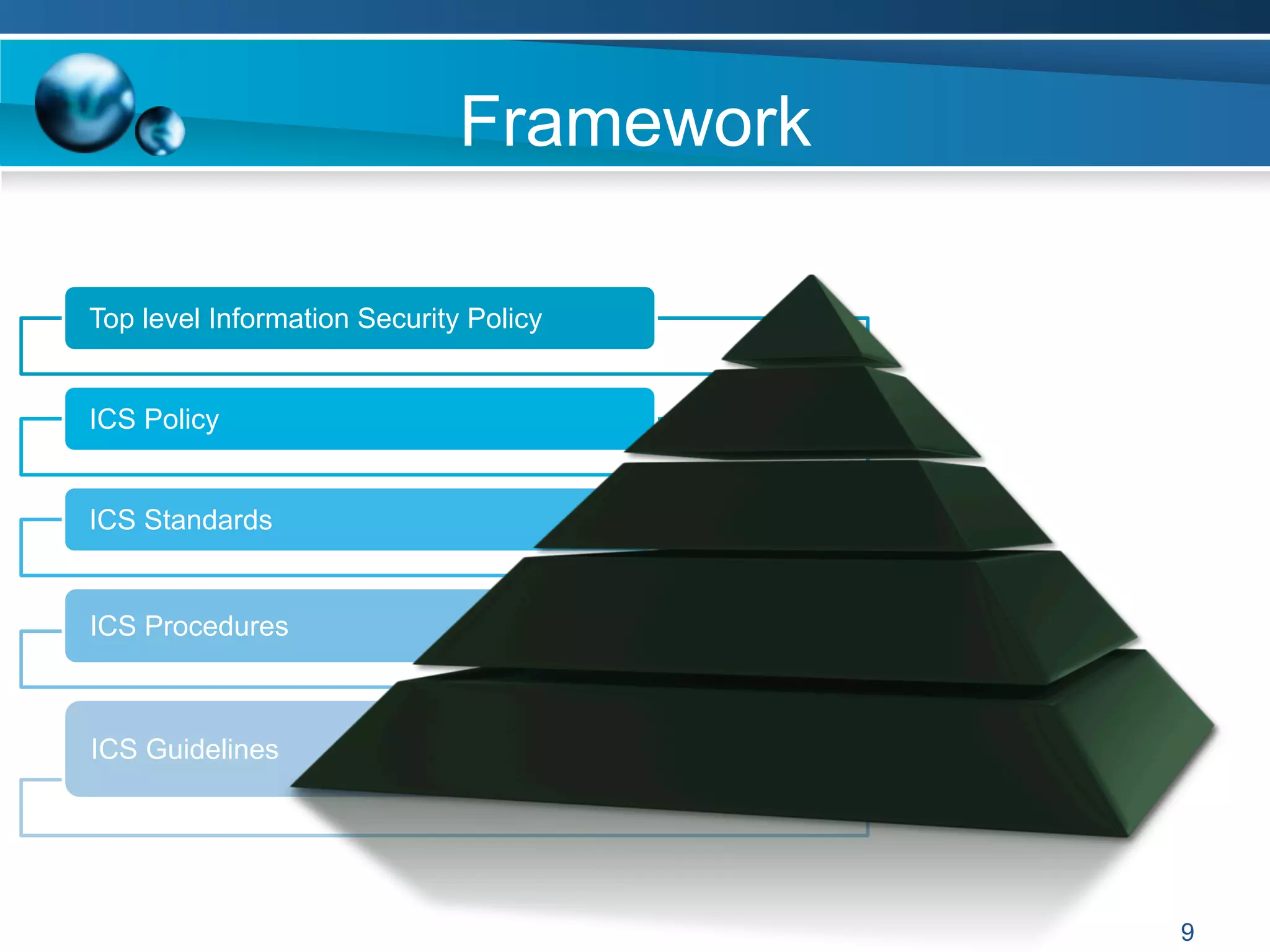
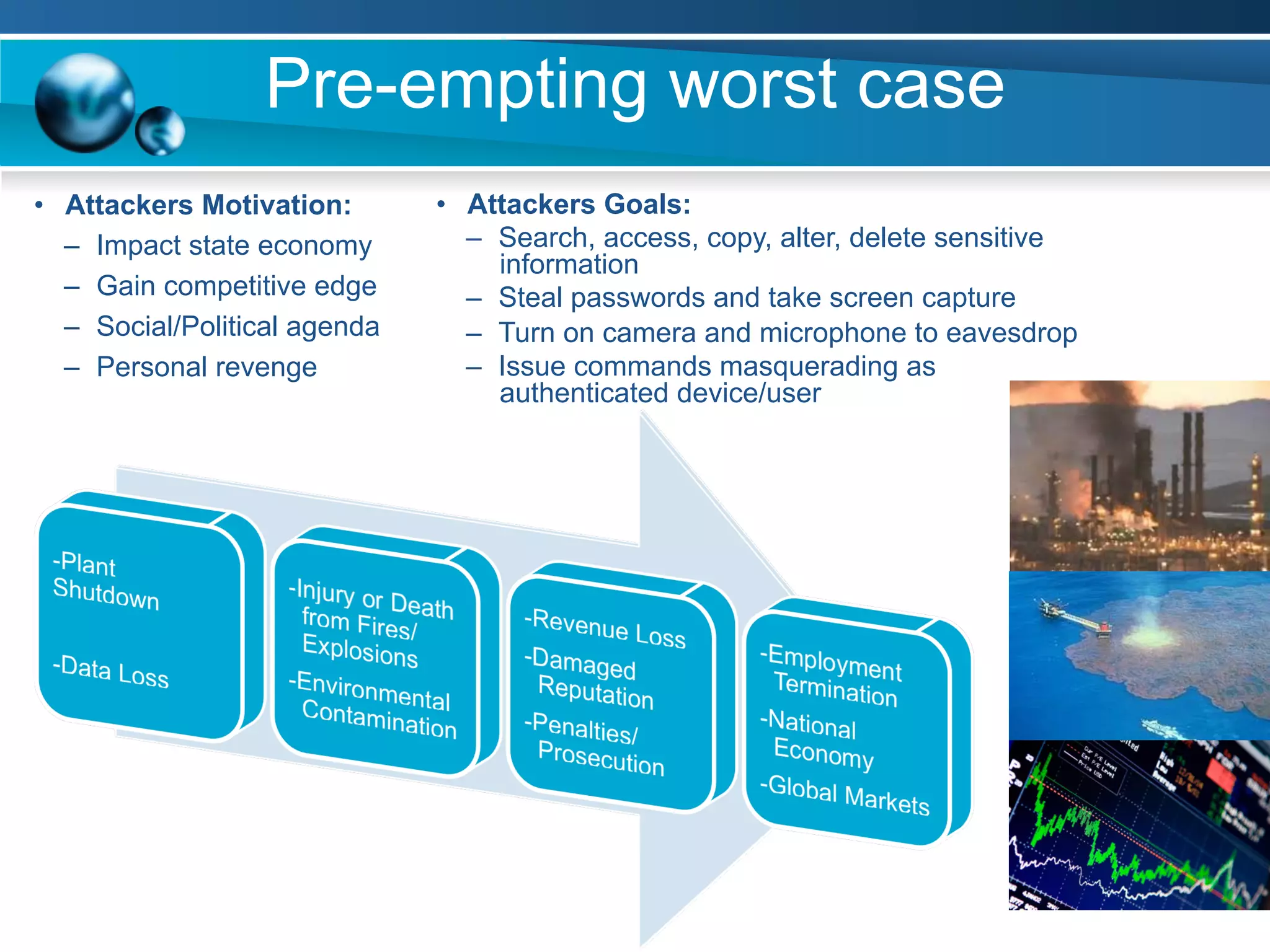
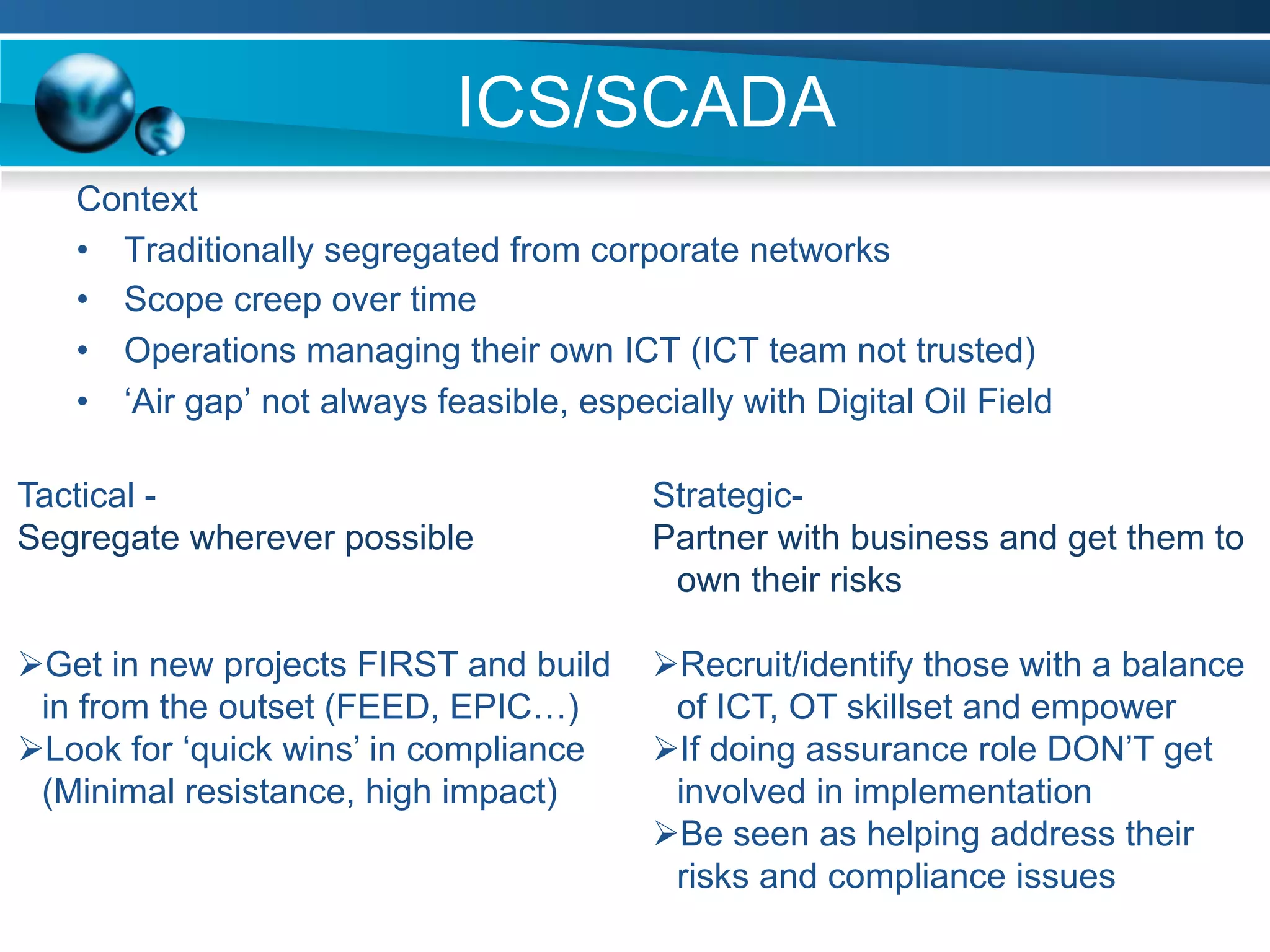
The document discusses achieving information and cyber security (ICS/SC) compliance through a risk-based approach. It begins by outlining the end state of having a holistic management system for regular compliance reporting and improvement. It then addresses identifying the current "as-is" security state, establishing a leadership model, and using compliance and risk assessments to prioritize controls. The document emphasizes that compliance is just the beginning and that risk management should inform decision making to balance security, compliance, and business needs. It concludes that compliance alone is not sufficient and a phased, governance-based approach is needed to deal with complex environments.