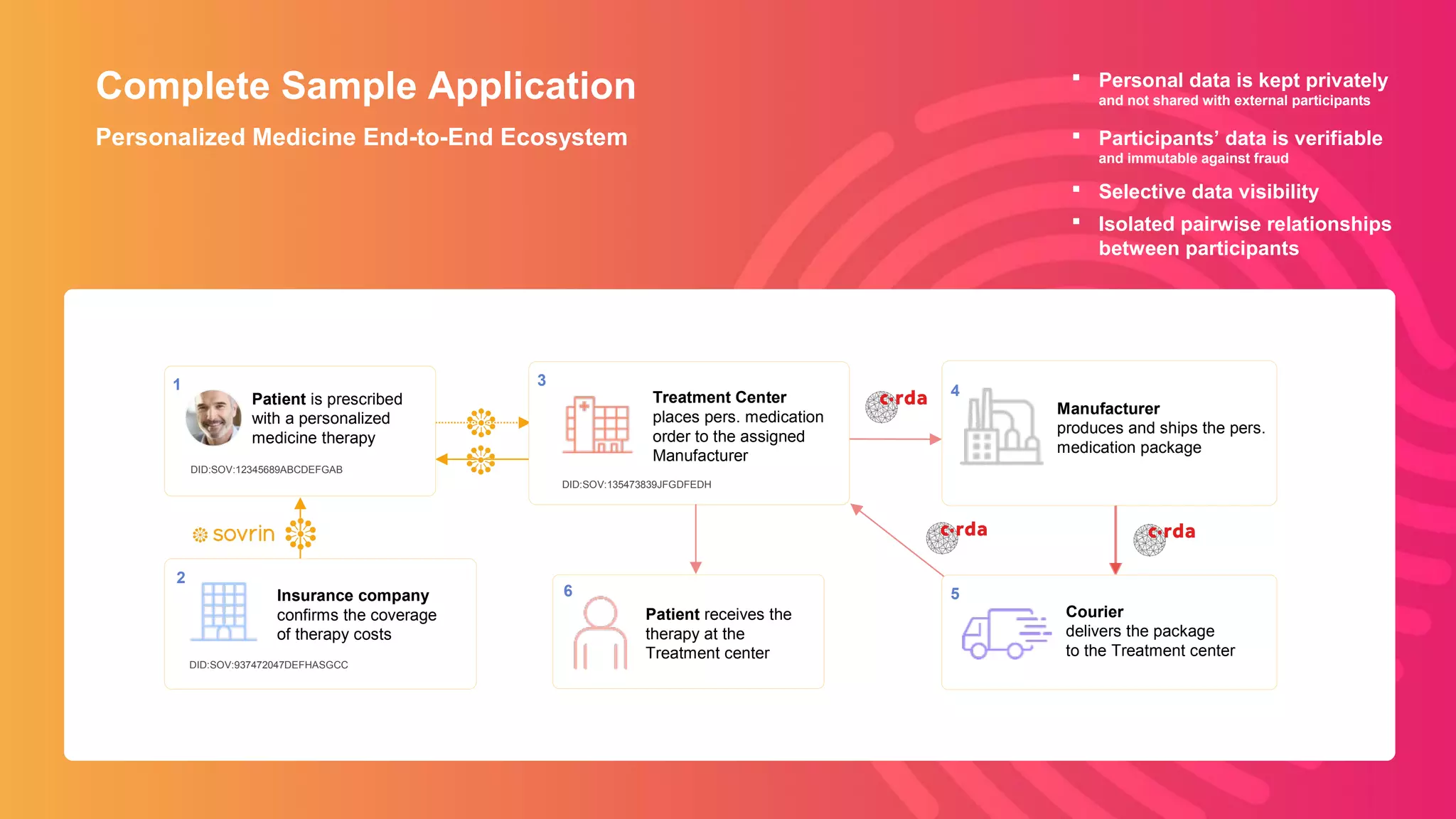
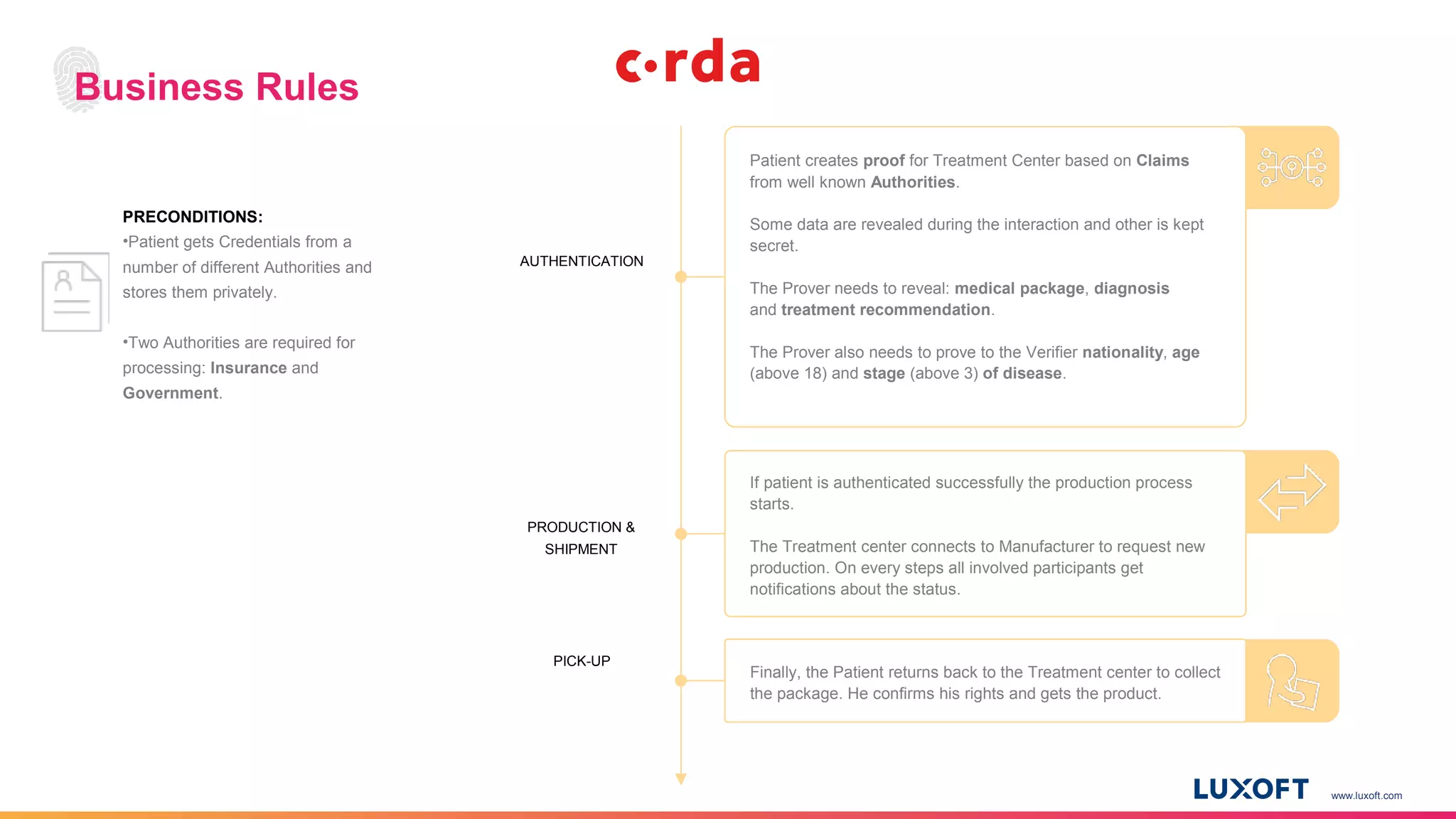
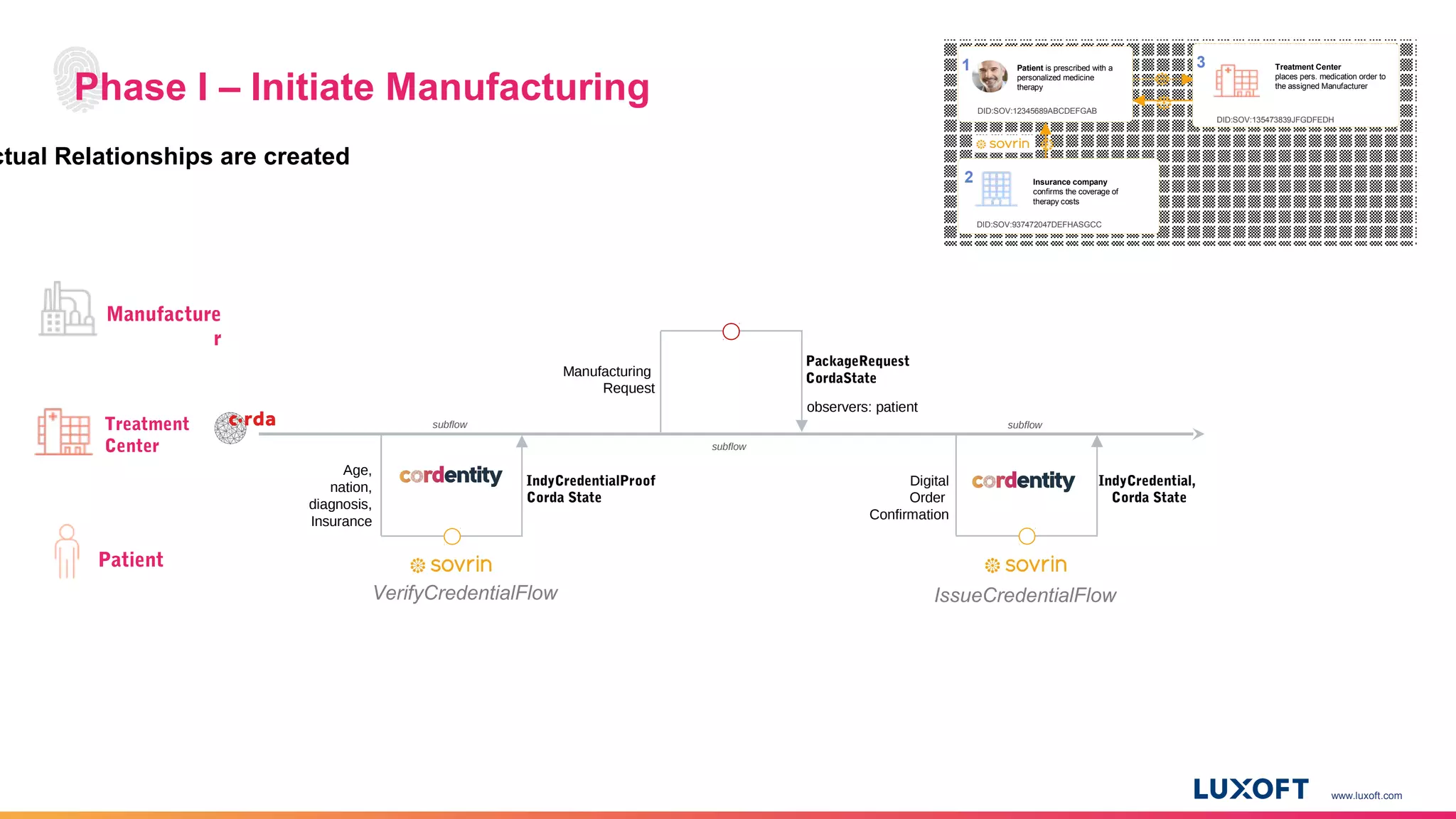
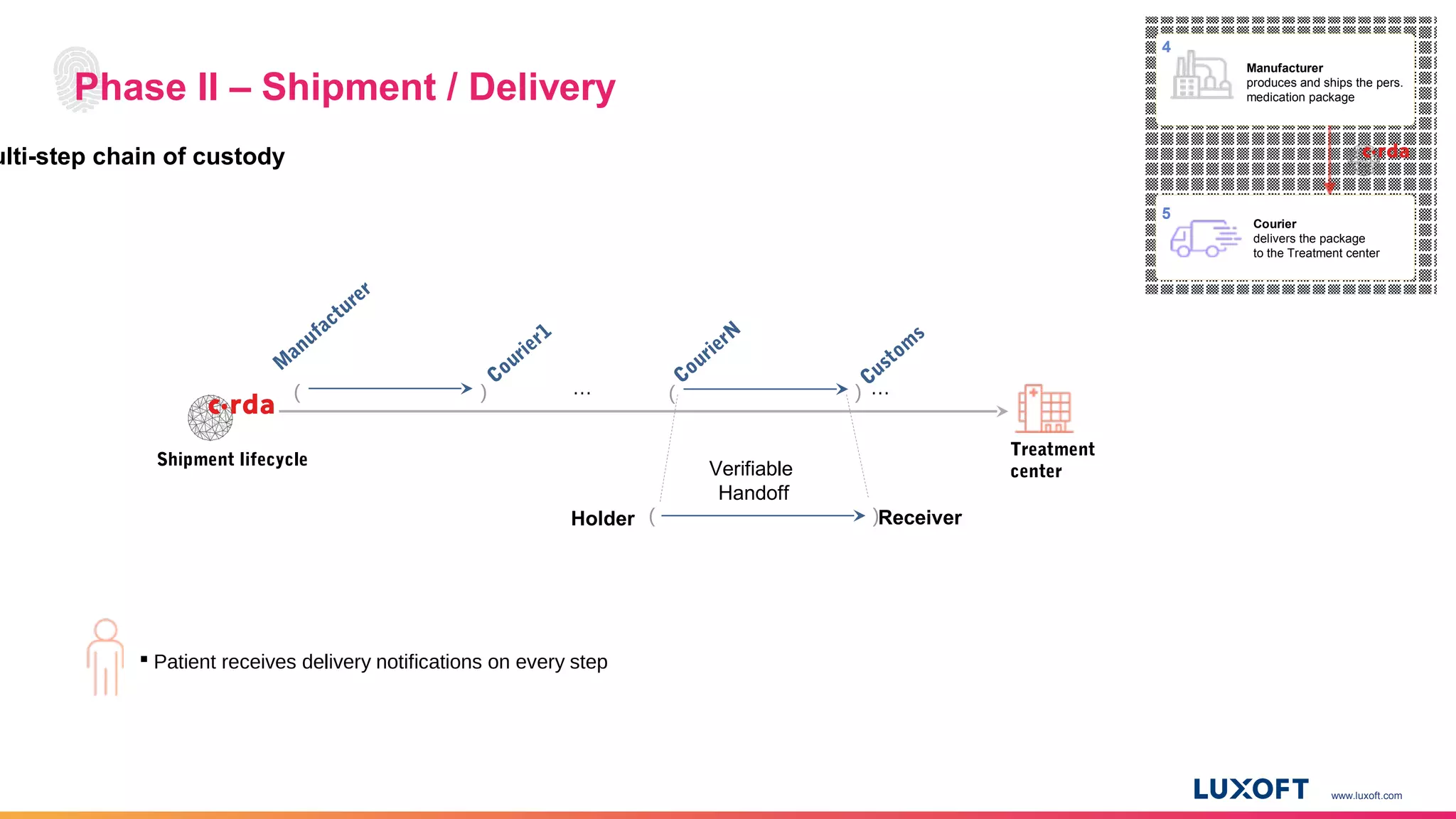
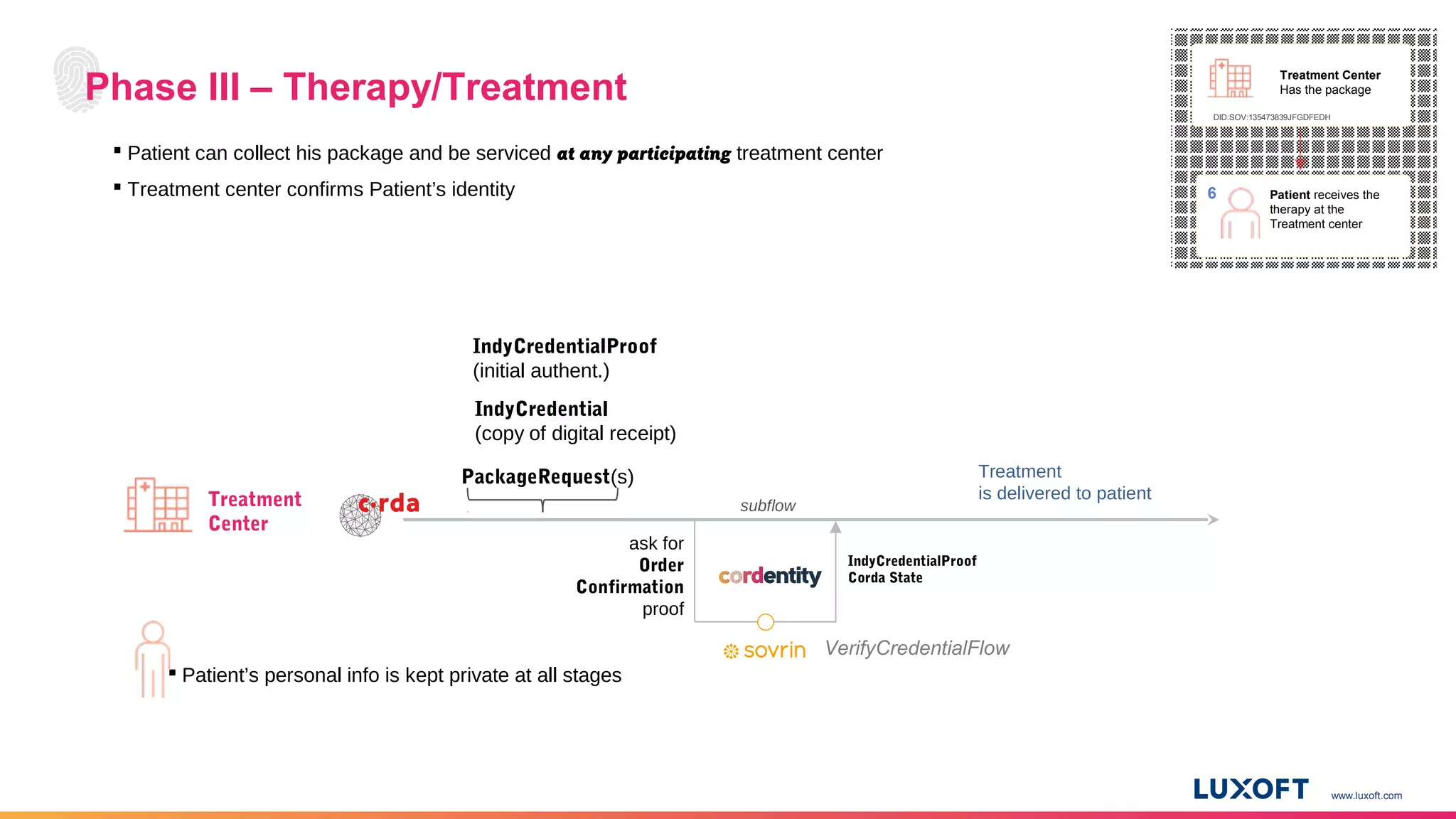
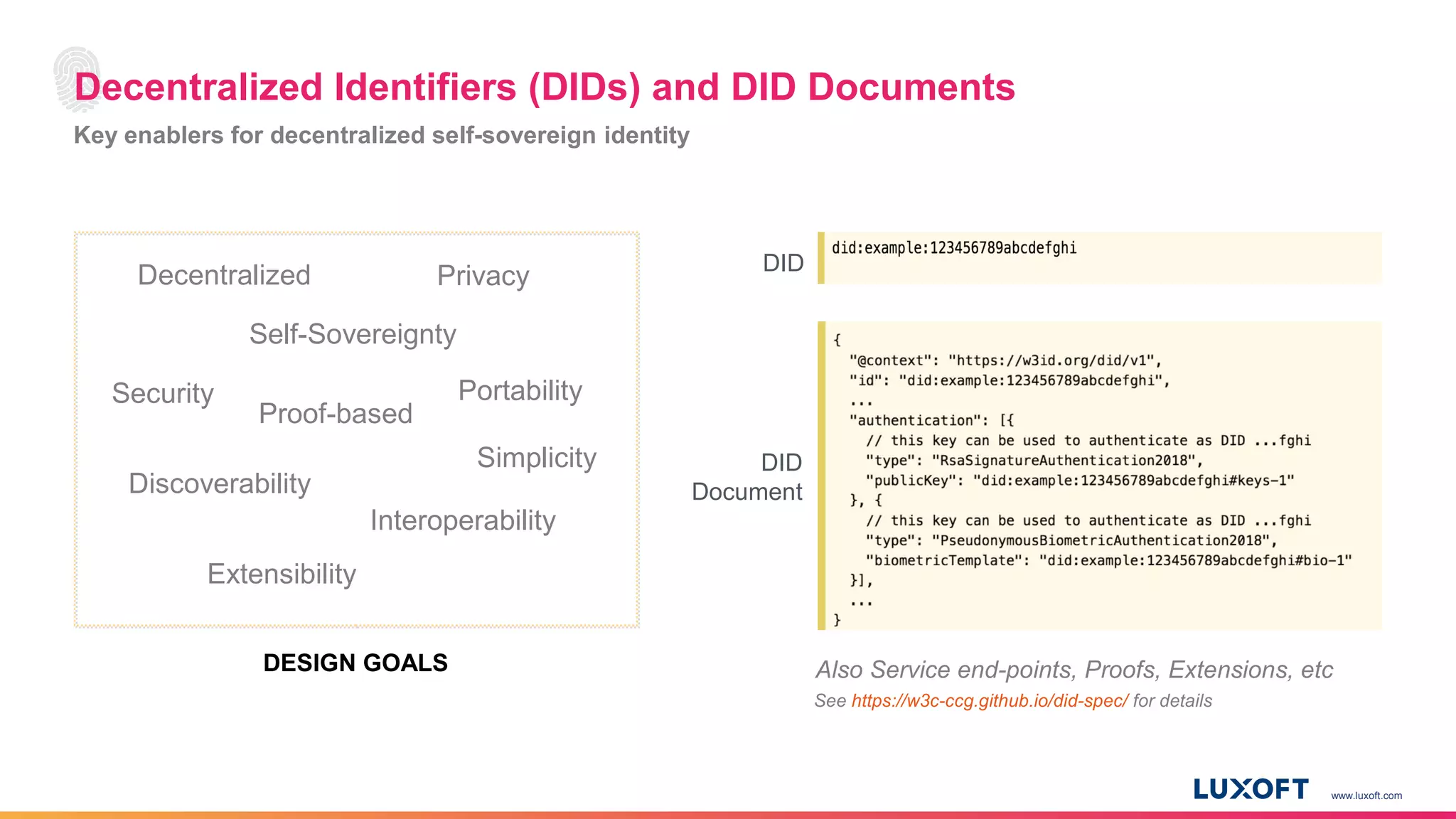
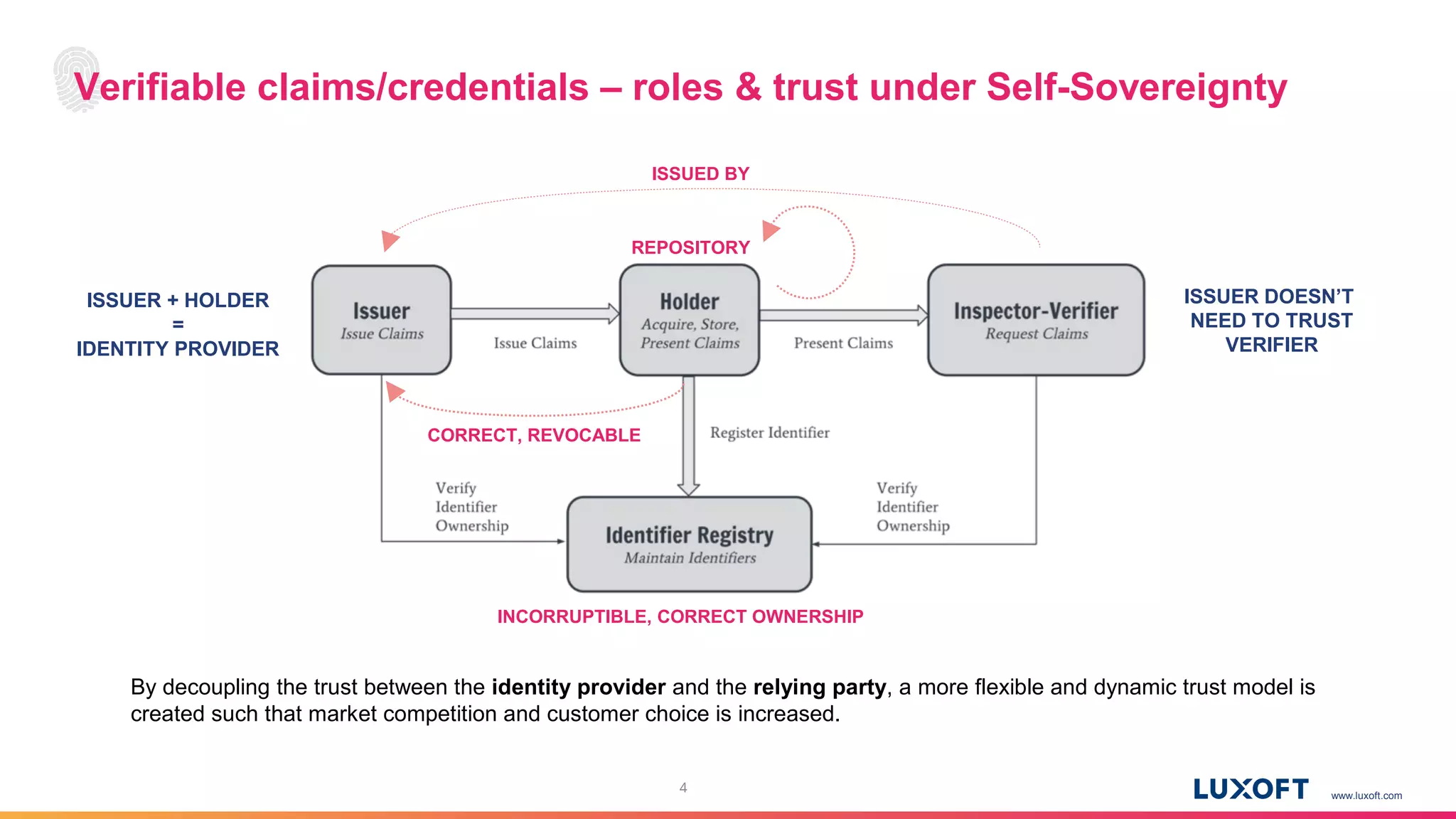
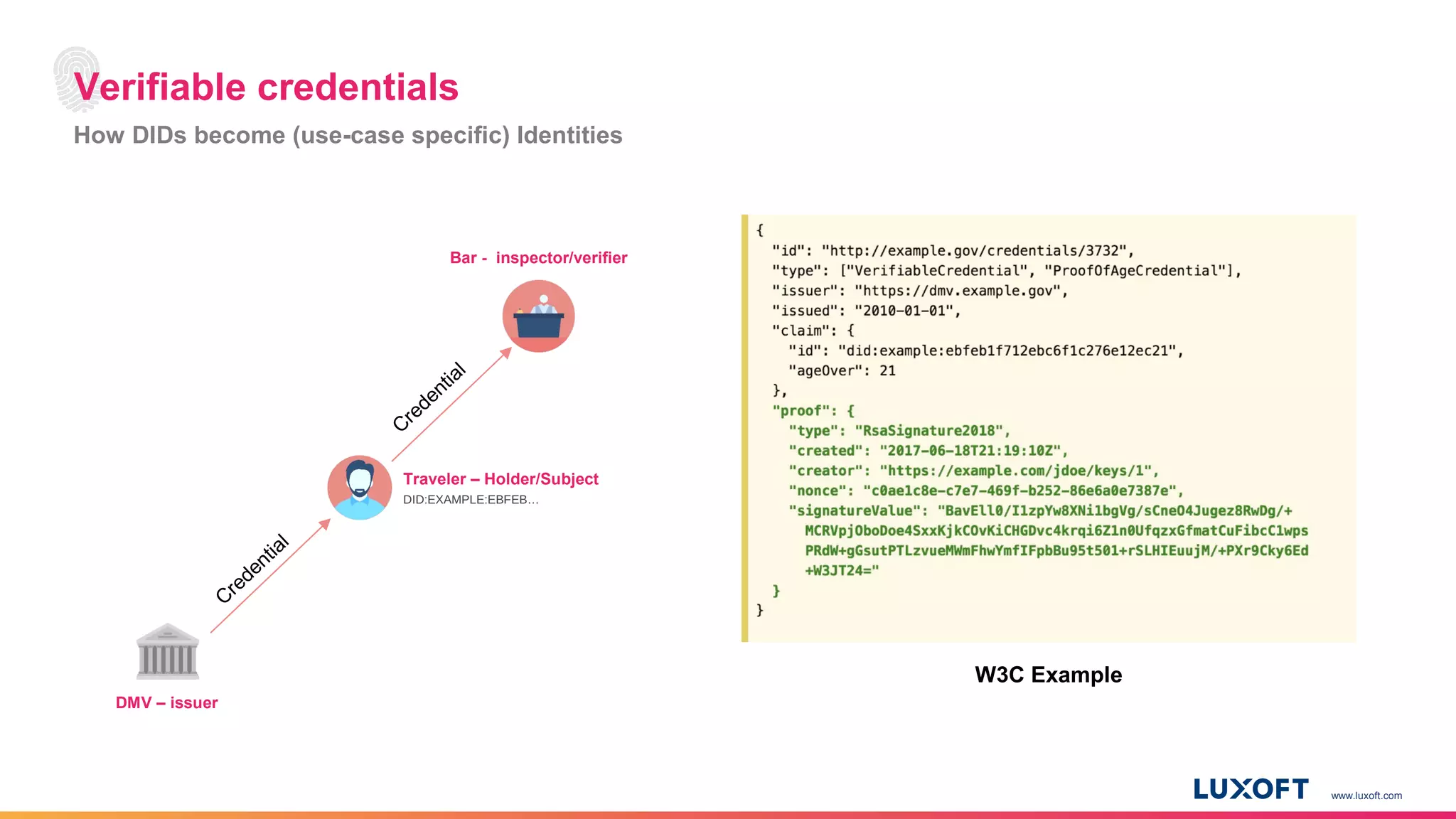
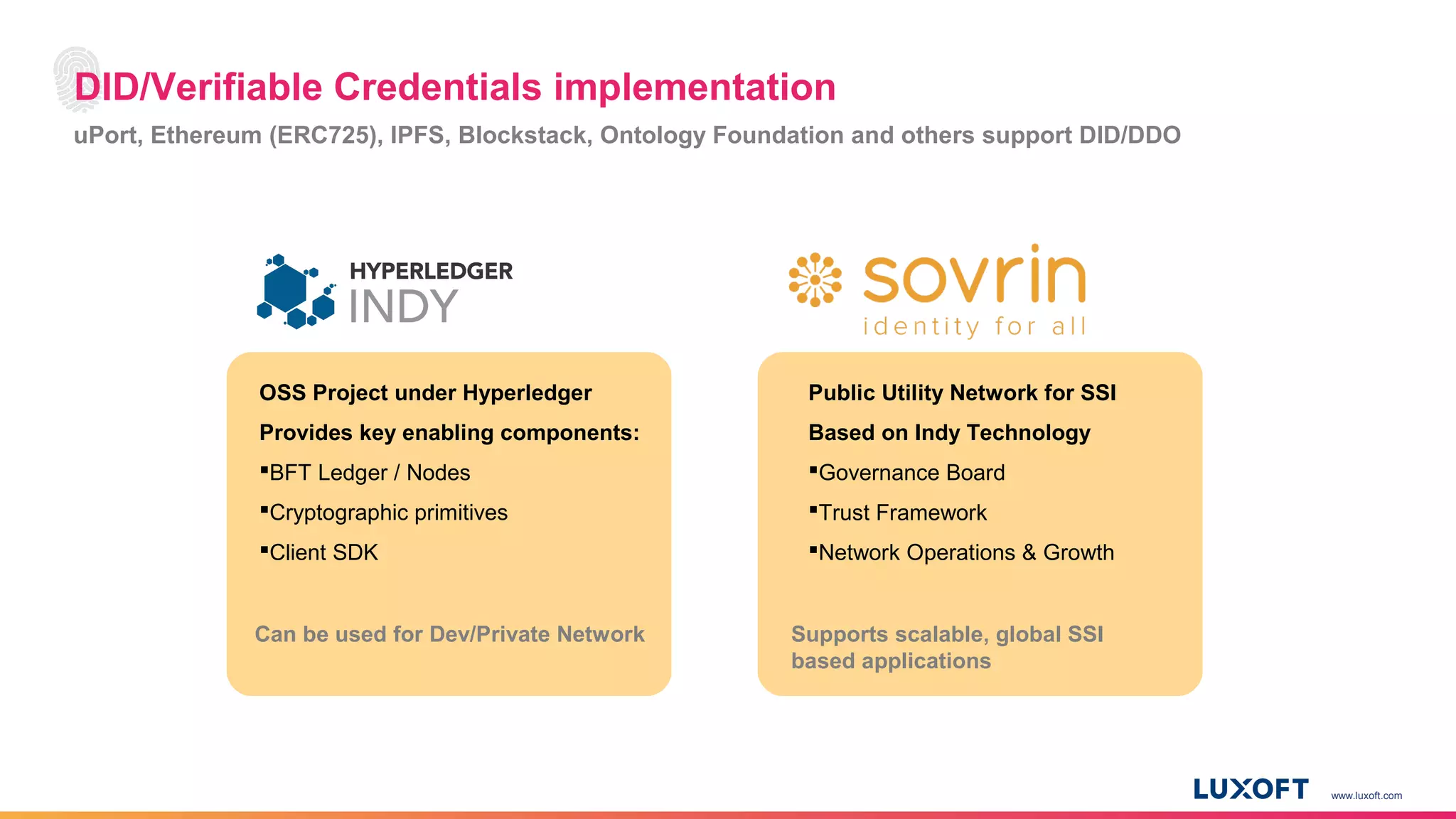
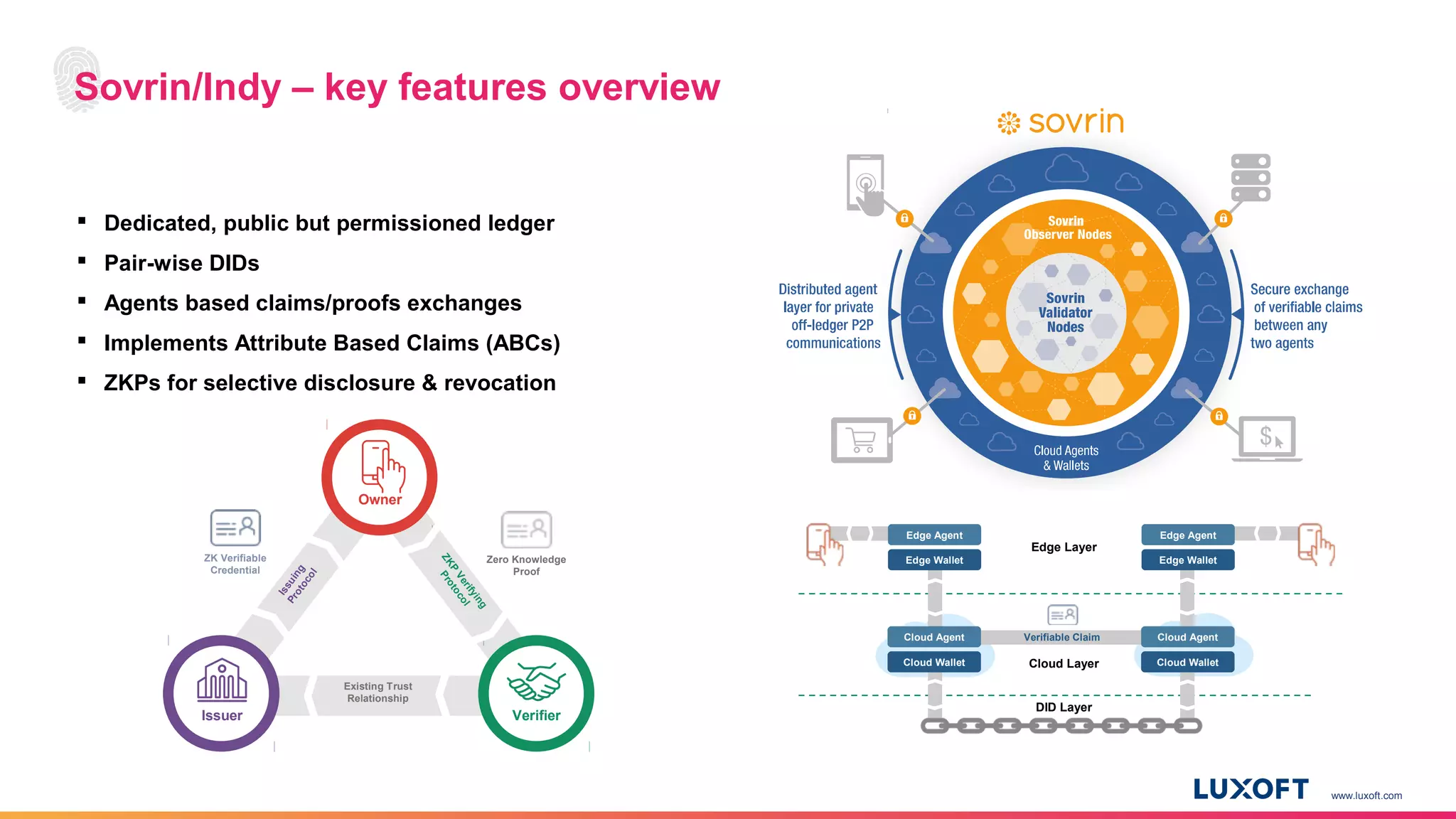
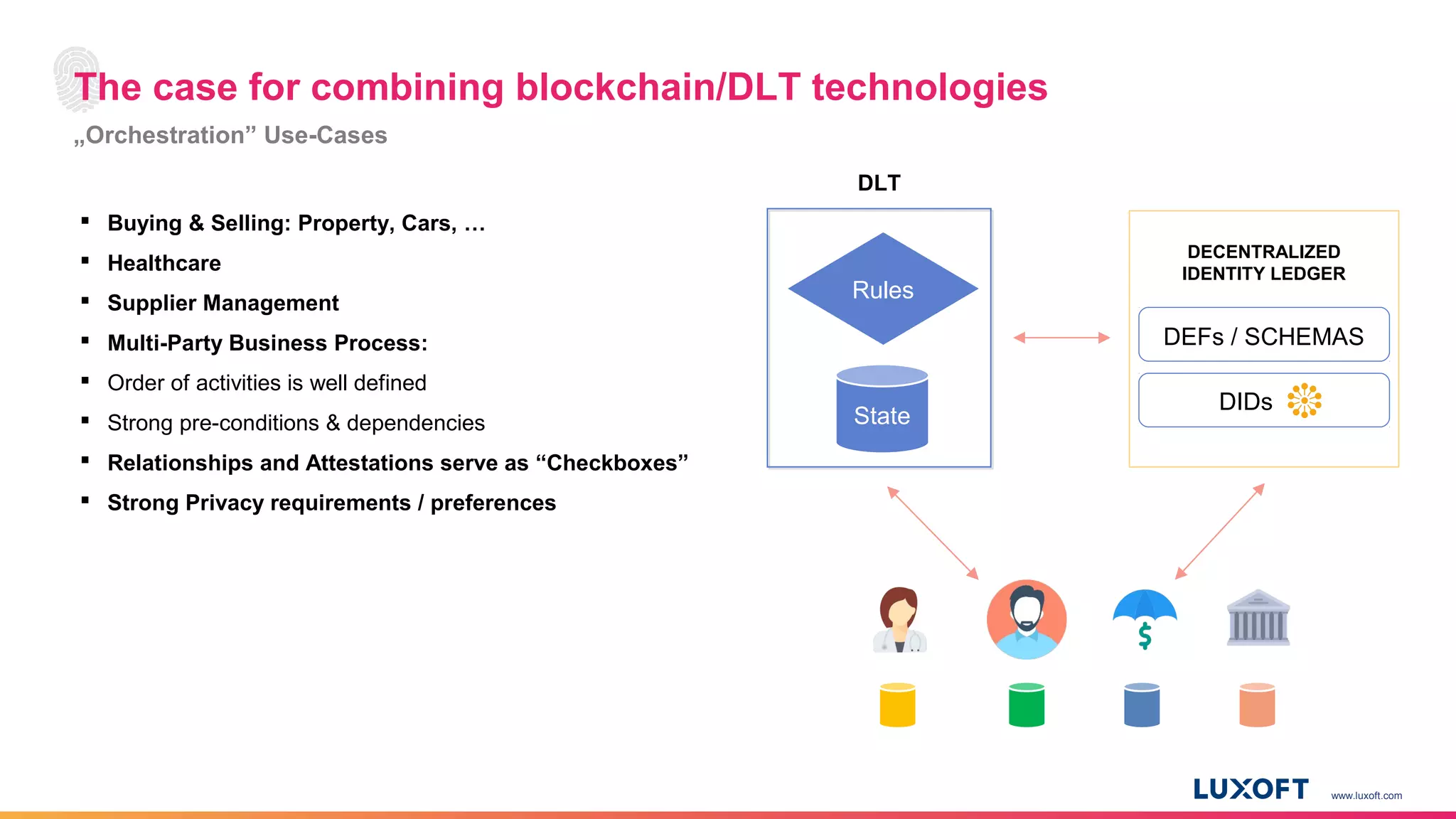
The document discusses the integration of self-sovereign identity (SSI) into decentralized applications using blockchain technology, primarily focusing on Hyperledger Indy and Corda. It highlights the framework for decentralized identifiers (DIDs), verifiable credentials, and their roles in creating a dynamic trust model that enhances privacy and security. Various use cases, such as personalized medicine and supply chain management, exemplify the practical applications of these technologies in developing scalable, secure, and efficient identity solutions.

![www.luxoft.com
Indy/Sovrin under the hood - 1/3
credential definition: {
"ver":"1.0",
"id":"V4SGRU86Z58d6TV7PBUe6f:3:CL:12:TAG_1",
"schemaId":"12",
"type":"CL",
"tag":"TAG_1",
"value":{
"primary": {
"n":"104273...84493",
"s":"824420…08151",
"rms":"52810…7940757153551267",
"r":{
"attr2":"73…809361",
"attr1":"88653…3706"
},
"rctxt":"6775...3821855822433",
"z":"418407...5877279897334588"
}
}
}
schema: {
"ver":"1.0",
"id": "V4SGRU86Z58d6TV7PBUe6f:2:schema_name:1.0",
"name":"schema_name",
"version":"1.0",
"attrNames":["attr1","attr2"],
"seqNo":12
}
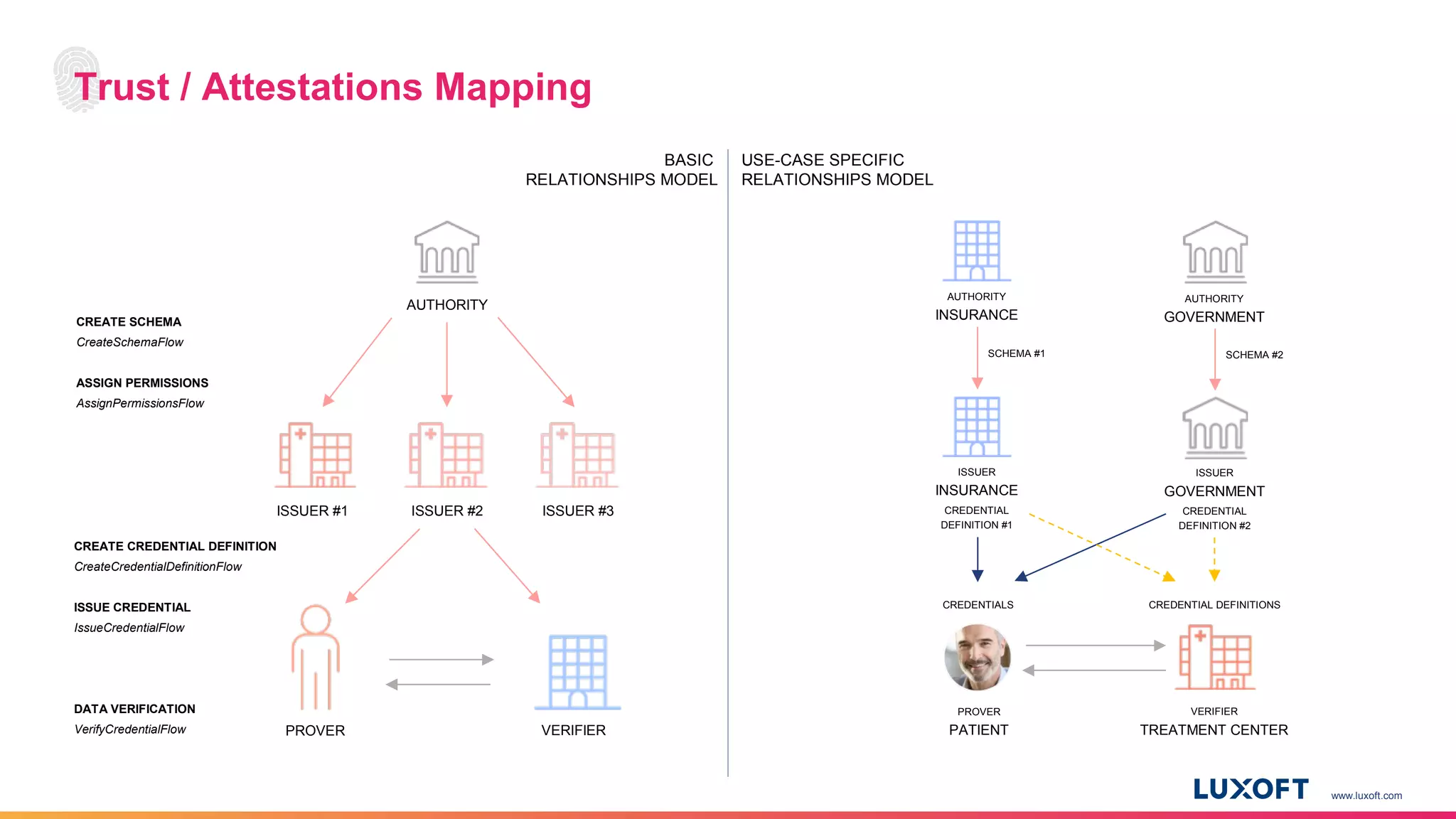
new schema
by authority
schema
from authority
new definition
by issuer #1
new definition
by issuer #2
new definition
by issuer #3
What’s in the blocks?
Schema
A structure that defines future credential
format or credential specification.
Credential
A digital assertion about identity attributes made
by a Ledger Entity about itself or another Ledger
Entity.
A Credential may be Public Data or Private
Data.
Credential Definition
A machine-readable definition of the semantic
structure of a Credential. (i.e. Public Key)
Proof
Cryptographic verification of a Credential.
PlenumLedger
Who interacts with the Ledger?
Authority
Creates Schemas
Issuer
Creates Credential Definitions
Prover
A Prover receives Credentials from the
Issuers. Both Prover and Issuer interact to
agree on some facts.
Verifier
Requests Proofs](https://image.slidesharecdn.com/cordacon2018-cordentityv1-180913163911/75/Cordacon-2018-Cordentity-Hyperledger-Indy-Corda-9-2048.jpg)