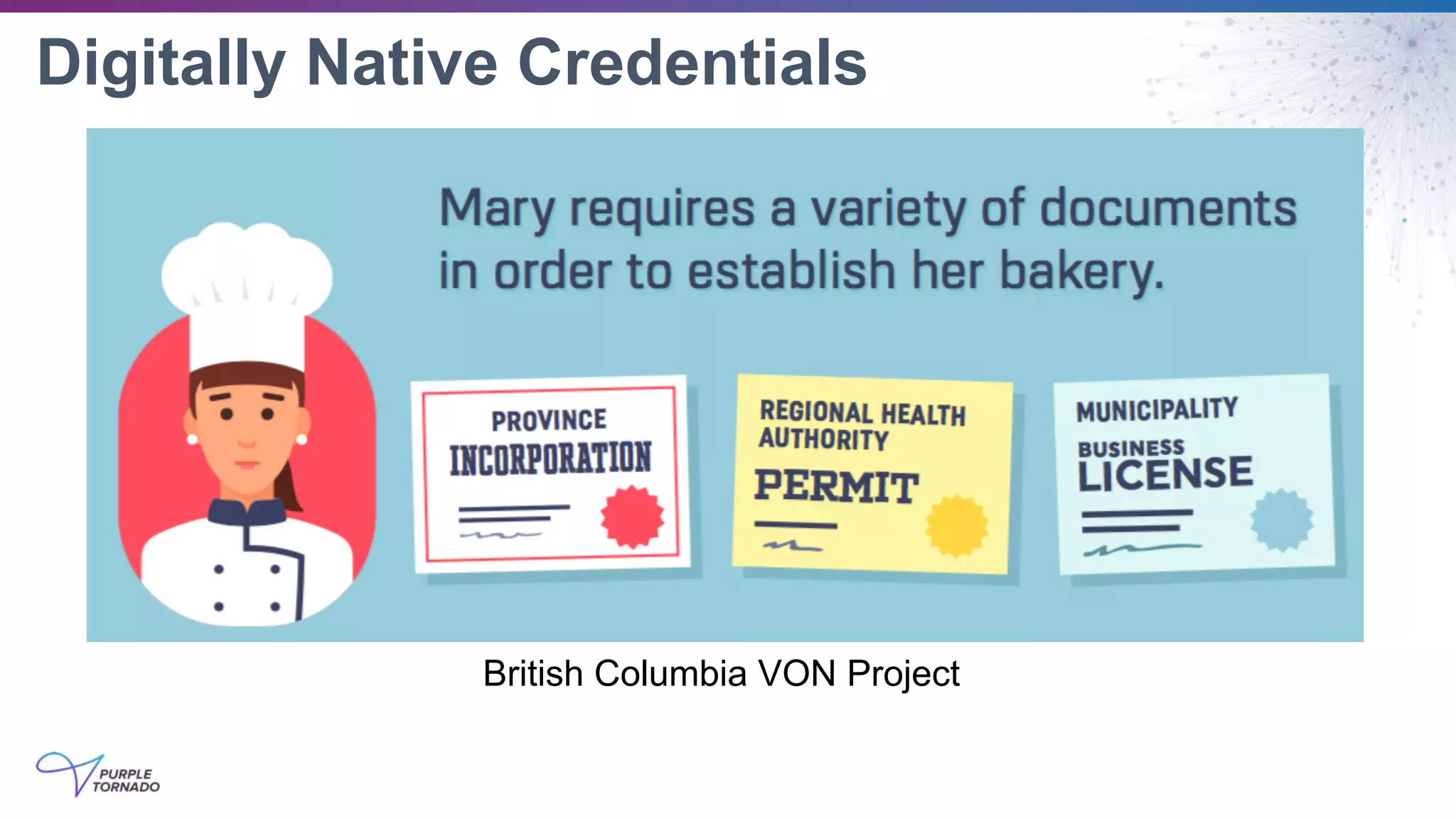
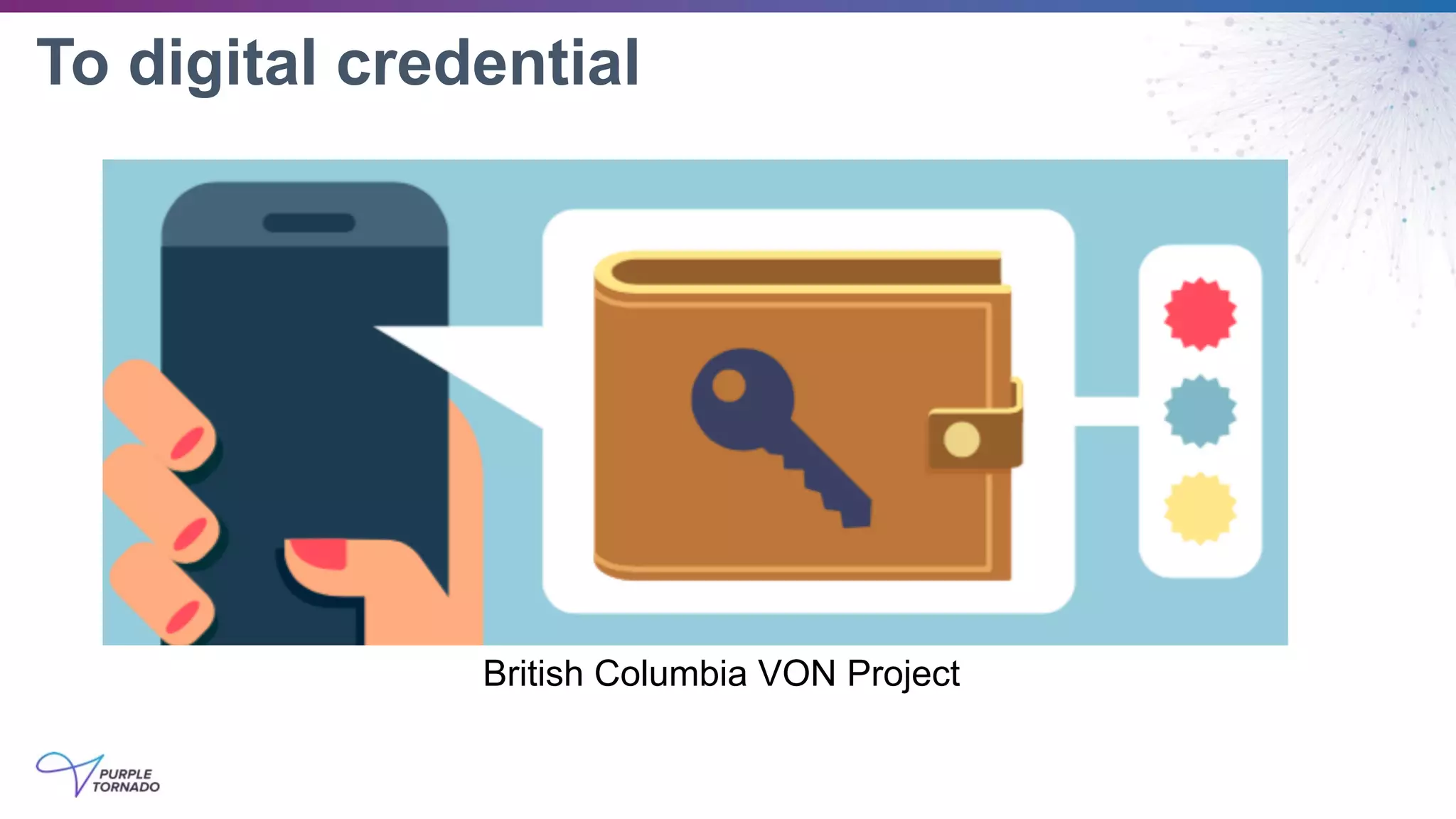
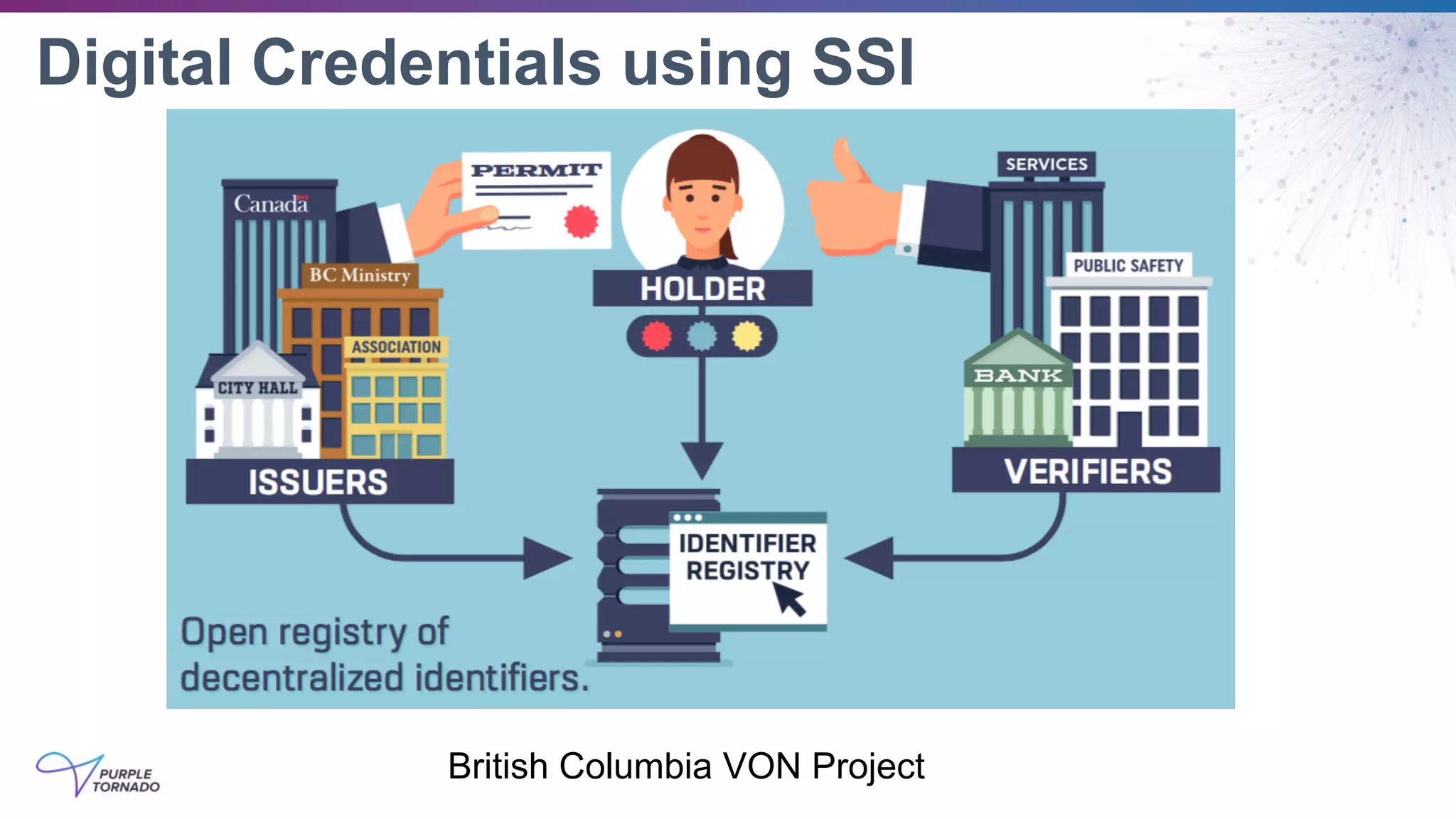
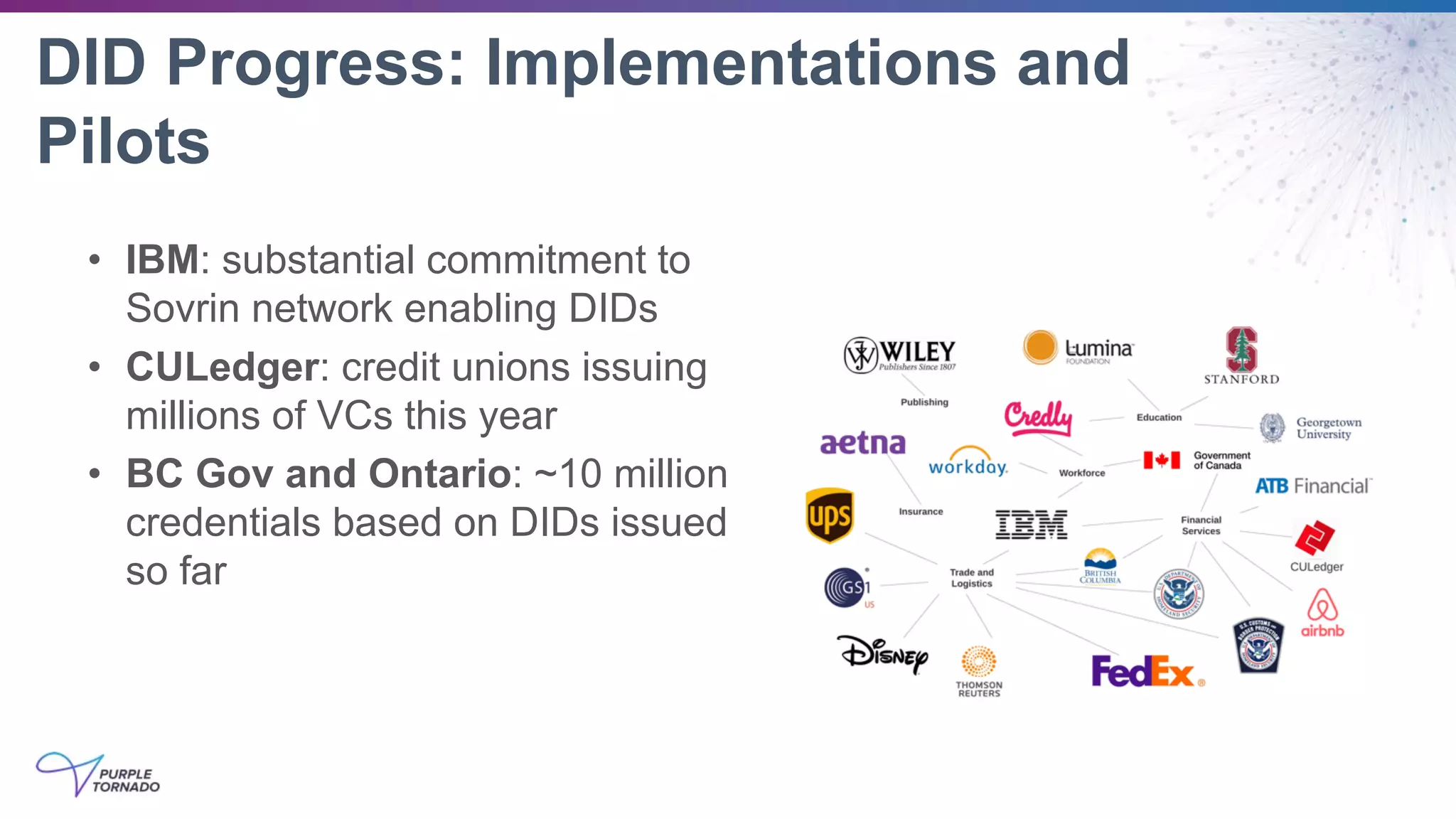
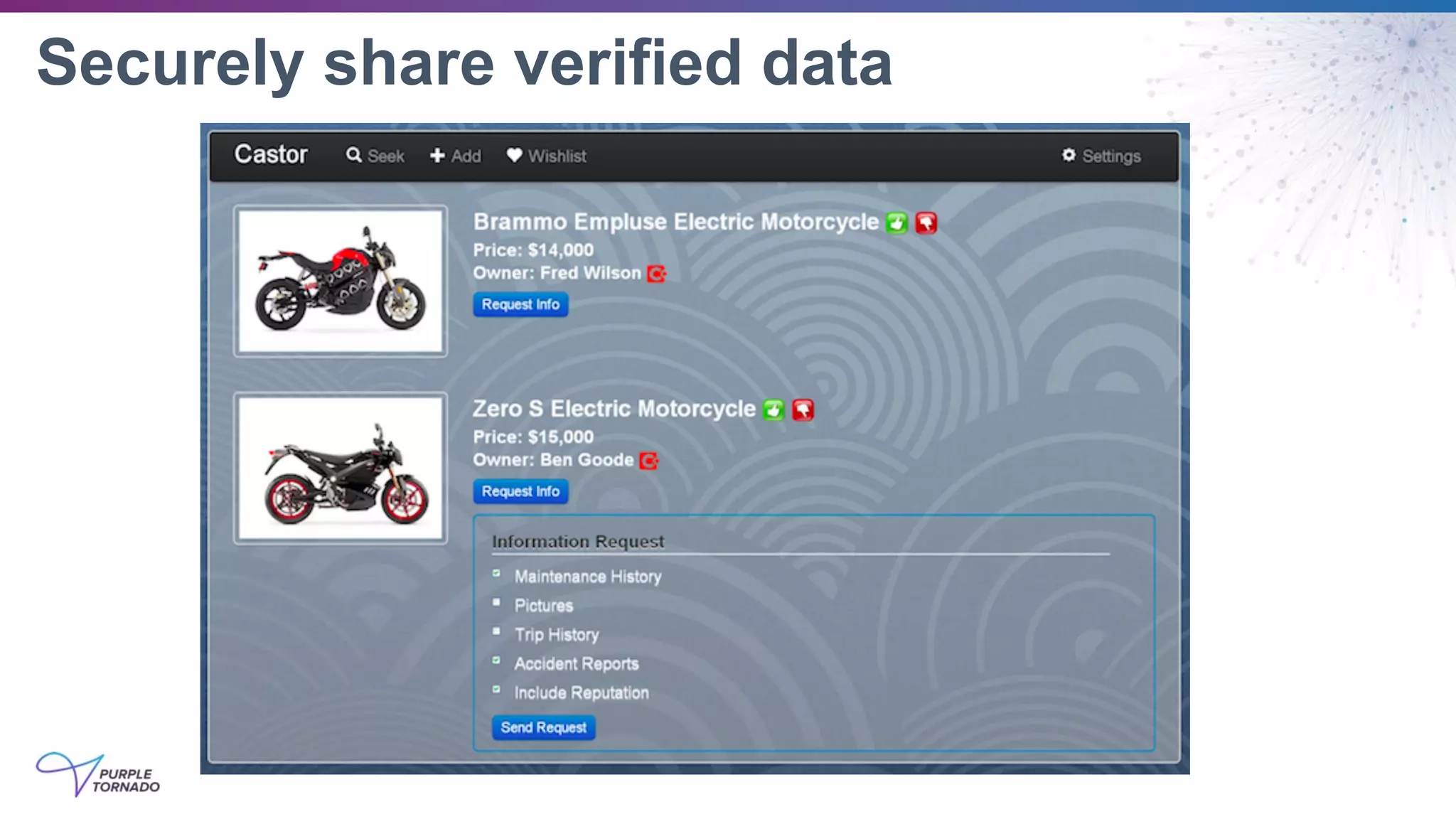
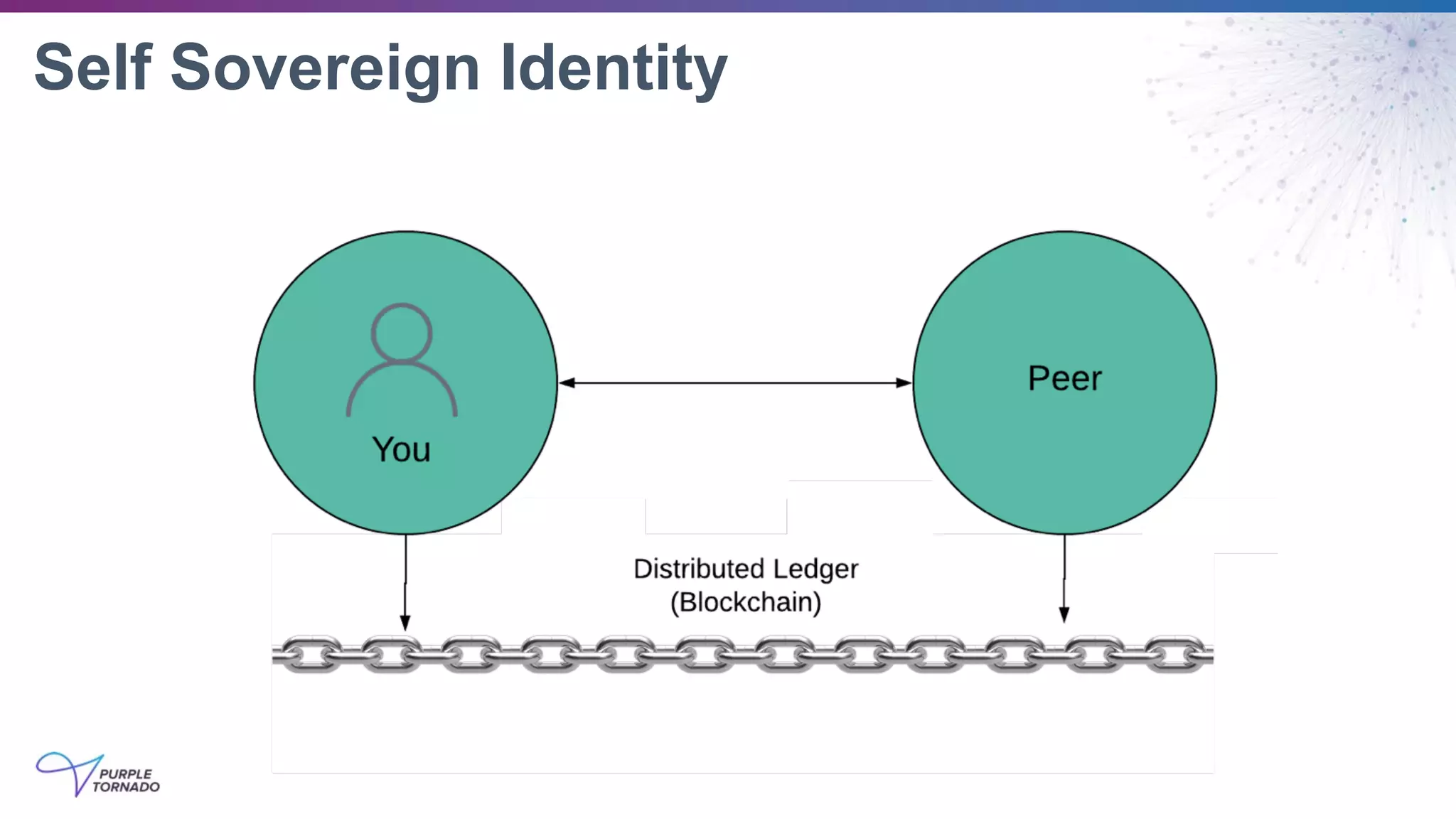
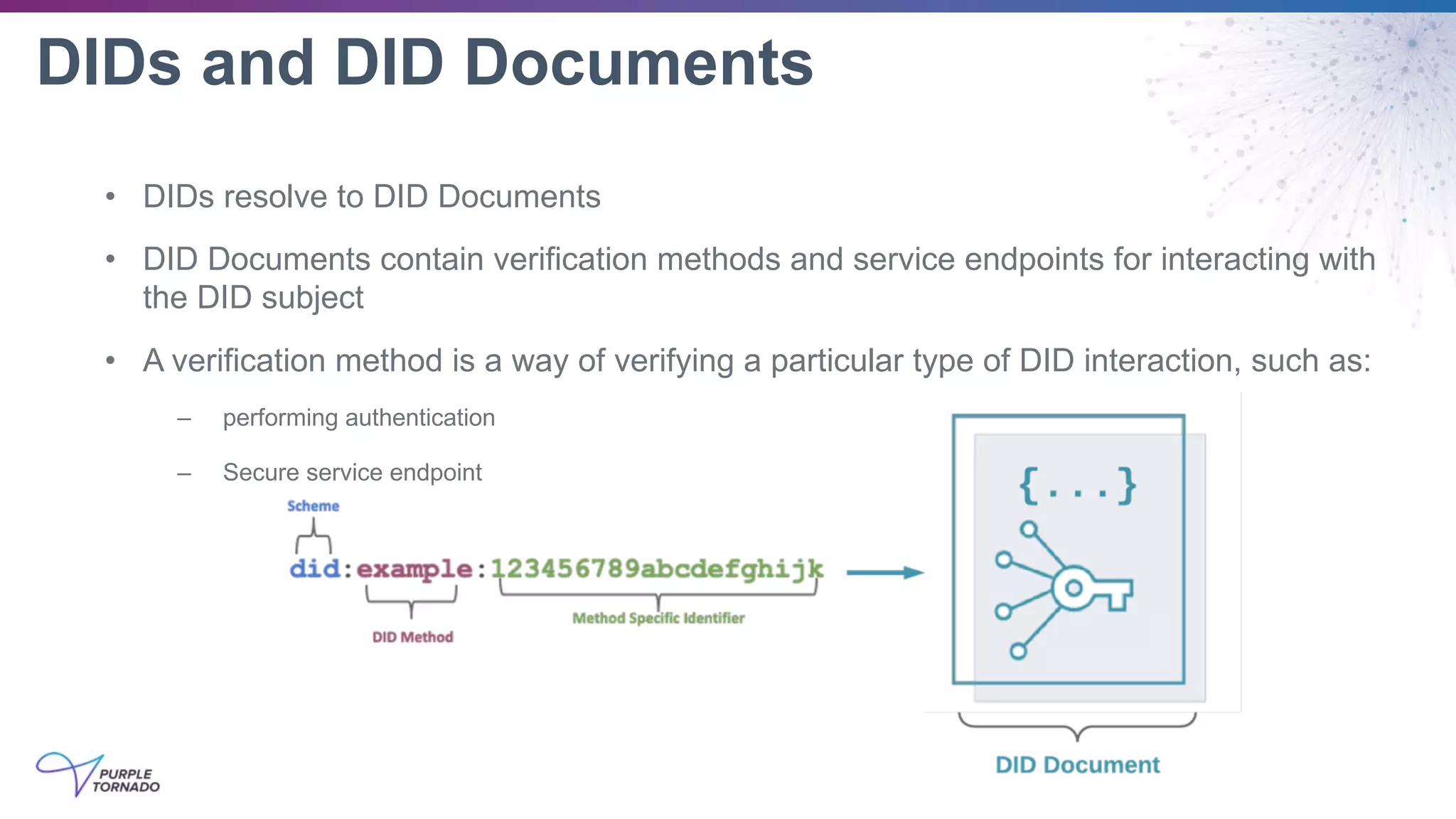
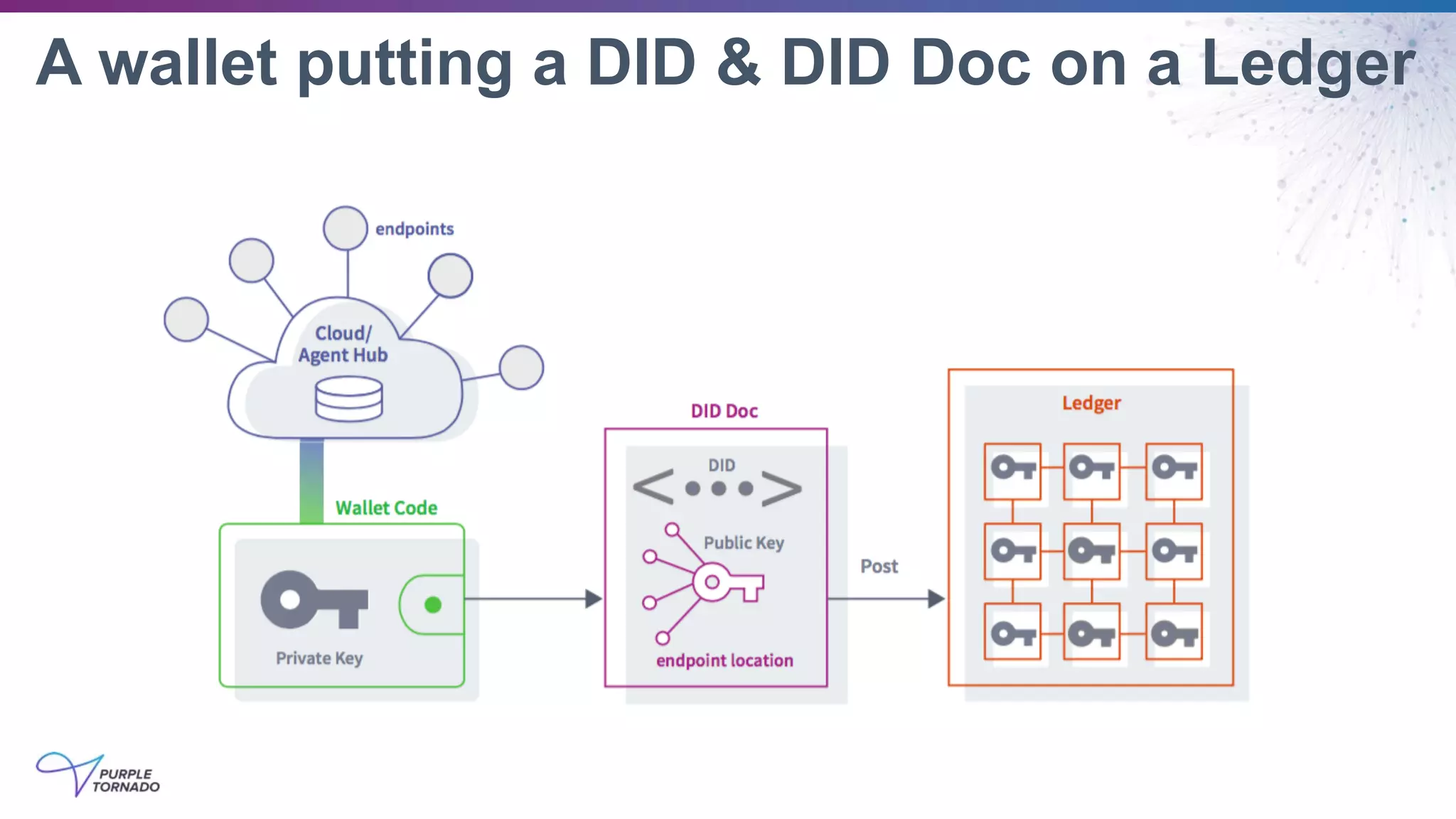
The document discusses self-sovereign identity (SSI) and decentralized identifiers (DIDs) as solutions to the long-standing problem of digital identity on the internet. It highlights the importance of giving individuals control over their personal data and the role of emerging standards and technologies in facilitating this transition. Key topics include the architecture of SSI systems, the standards being developed, and the foundational structures of DIDs.









![DID Document{
"@context": "https://w3id.org/did/v1",
"id": "did:example:123456789abcdefghi",
"publicKey": [{
"id": "did:example:123456789abcdefghi#keys-1",
"type": "RsaSigningKey2018",
"owner": "did:example:123456789abcdefghi",
"publicKeyPem": "-----BEGIN PUBLIC KEY...END PUBLIC KEY-----rn"
}],
"authentication": [{
"type": "RsaSignatureAuthentication2018",
"publicKey": "did:example:123456789abcdefghi#keys-1"
}],
"service": [{
"type": "ExampleService",
"serviceEndpoint": "https://example.com/endpoint/8377464"
}],
"created": "2002-10-10T17:00:00Z",
"updated": "2016-10-17T02:41:00Z",
”proof": {
"type": "RsaSignature2018",
"created": "2016-02-08T16:02:20Z",
"creator": "did:sov:8uQhQMGzWxR8vw5P3UWH1j#key/1",
”proofValue": "IOmA4R7TfhkYTYW87z640O3GYFldw0
yqie9Wl1kZ5OBYNAKOwG5uOsPRK8/2C4STOWF+83cMcbZ3CBMq2/
gi25s=”
}
}](https://image.slidesharecdn.com/ssi-iiw-duffyvescent4-190506145828/75/Introduction-to-Self-Sovereign-Identity-20-2048.jpg)
![DID Document – DID{
"@context": "https://w3id.org/did/v1",
"id": "did:example:123456789abcdefghi",
"publicKey": [{
"id": "did:example:123456789abcdefghi#keys-1",
"type": "RsaSigningKey2018",
"owner": "did:example:123456789abcdefghi",
"publicKeyPem": "-----BEGIN PUBLIC KEY...END PUBLIC KEY-----rn"
}],
"authentication": [{
"type": "RsaSignatureAuthentication2018",
"publicKey": "did:example:123456789abcdefghi#keys-1"
}],
"service": [{
"type": "ExampleService",
"serviceEndpoint": "https://example.com/endpoint/8377464"
}],
"created": "2002-10-10T17:00:00Z",
"updated": "2016-10-17T02:41:00Z",
”proof": {
"type": "RsaSignature2018",
"created": "2016-02-08T16:02:20Z",
"creator": "did:sov:8uQhQMGzWxR8vw5P3UWH1j#key/1",
”proofValue": "IOmA4R7TfhkYTYW87z640O3GYFldw0
yqie9Wl1kZ5OBYNAKOwG5uOsPRK8/2C4STOWF+83cMcbZ3CBMq2/
gi25s=”
}
}](https://image.slidesharecdn.com/ssi-iiw-duffyvescent4-190506145828/75/Introduction-to-Self-Sovereign-Identity-21-2048.jpg)
![DID Document – public key{
"@context": "https://w3id.org/did/v1",
"id": "did:example:123456789abcdefghi",
"publicKey": [{
"id": "did:example:123456789abcdefghi#keys-1",
"type": "RsaSigningKey2018",
"owner": "did:example:123456789abcdefghi",
"publicKeyPem": "-----BEGIN PUBLIC KEY...END PUBLIC KEY-----rn"
}],
"authentication": [{
"type": "RsaSignatureAuthentication2018",
"publicKey": "did:example:123456789abcdefghi#keys-1"
}],
"service": [{
"type": "ExampleService",
"serviceEndpoint": "https://example.com/endpoint/8377464"
}],
"created": "2002-10-10T17:00:00Z",
"updated": "2016-10-17T02:41:00Z",
”proof": {
"type": "RsaSignature2018",
"created": "2016-02-08T16:02:20Z",
"creator": "did:sov:8uQhQMGzWxR8vw5P3UWH1j#key/1",
”proofValue": "IOmA4R7TfhkYTYW87z640O3GYFldw0
yqie9Wl1kZ5OBYNAKOwG5uOsPRK8/2C4STOWF+83cMcbZ3CBMq2/
gi25s=”
}
}](https://image.slidesharecdn.com/ssi-iiw-duffyvescent4-190506145828/75/Introduction-to-Self-Sovereign-Identity-22-2048.jpg)
![DID Document – service endpoint{
"@context": "https://w3id.org/did/v1",
"id": "did:example:123456789abcdefghi",
"publicKey": [{
"id": "did:example:123456789abcdefghi#keys-1",
"type": "RsaSigningKey2018",
"owner": "did:example:123456789abcdefghi",
"publicKeyPem": "-----BEGIN PUBLIC KEY...END PUBLIC KEY-----rn"
}],
"authentication": [{
"type": "RsaSignatureAuthentication2018",
"publicKey": "did:example:123456789abcdefghi#keys-1"
}],
"service": [{
"type": "ExampleService",
"serviceEndpoint": "https://example.com/endpoint/8377464"
}],
"created": "2002-10-10T17:00:00Z",
"updated": "2016-10-17T02:41:00Z",
”proof": {
"type": "RsaSignature2018",
"created": "2016-02-08T16:02:20Z",
"creator": "did:sov:8uQhQMGzWxR8vw5P3UWH1j#key/1",
”proofValue": "IOmA4R7TfhkYTYW87z640O3GYFldw0
yqie9Wl1kZ5OBYNAKOwG5uOsPRK8/2C4STOWF+83cMcbZ3CBMq2/
gi25s=”
}
}](https://image.slidesharecdn.com/ssi-iiw-duffyvescent4-190506145828/75/Introduction-to-Self-Sovereign-Identity-23-2048.jpg)
![DID Document – date{
"@context": "https://w3id.org/did/v1",
"id": "did:example:123456789abcdefghi",
"publicKey": [{
"id": "did:example:123456789abcdefghi#keys-1",
"type": "RsaSigningKey2018",
"owner": "did:example:123456789abcdefghi",
"publicKeyPem": "-----BEGIN PUBLIC KEY...END PUBLIC KEY-----rn"
}],
"authentication": [{
"type": "RsaSignatureAuthentication2018",
"publicKey": "did:example:123456789abcdefghi#keys-1"
}],
"service": [{
"type": "ExampleService",
"serviceEndpoint": "https://example.com/endpoint/8377464"
}],
"created": "2002-10-10T17:00:00Z",
"updated": "2016-10-17T02:41:00Z",
”proof": {
"type": "RsaSignature2018",
"created": "2016-02-08T16:02:20Z",
"creator": "did:sov:8uQhQMGzWxR8vw5P3UWH1j#key/1",
”proofValue": "IOmA4R7TfhkYTYW87z640O3GYFldw0
yqie9Wl1kZ5OBYNAKOwG5uOsPRK8/2C4STOWF+83cMcbZ3CBMq2/
gi25s=”
}
}](https://image.slidesharecdn.com/ssi-iiw-duffyvescent4-190506145828/75/Introduction-to-Self-Sovereign-Identity-24-2048.jpg)
![DID Document – proof{
"@context": "https://w3id.org/did/v1",
"id": "did:example:123456789abcdefghi",
"publicKey": [{
"id": "did:example:123456789abcdefghi#keys-1",
"type": "RsaSigningKey2018",
"owner": "did:example:123456789abcdefghi",
"publicKeyPem": "-----BEGIN PUBLIC KEY...END PUBLIC KEY-----rn"
}],
"authentication": [{
"type": "RsaSignatureAuthentication2018",
"publicKey": "did:example:123456789abcdefghi#keys-1"
}],
"service": [{
"type": "ExampleService",
"serviceEndpoint": "https://example.com/endpoint/8377464"
}],
"created": "2002-10-10T17:00:00Z",
"updated": "2016-10-17T02:41:00Z",
”proof": {
"type": "RsaSignature2018",
"created": "2016-02-08T16:02:20Z",
"creator": "did:sov:8uQhQMGzWxR8vw5P3UWH1j#key/1",
”proofValue": "IOmA4R7TfhkYTYW87z640O3GYFldw0
yqie9Wl1kZ5OBYNAKOwG5uOsPRK8/2C4STOWF+83cMcbZ3CBMq2/
gi25s=”
}
}](https://image.slidesharecdn.com/ssi-iiw-duffyvescent4-190506145828/75/Introduction-to-Self-Sovereign-Identity-25-2048.jpg)




![{
"@context": "https://w3id.org/veres-one/v1",
"id": "did:v1:nym:DwkYwcoyUXHNkpj3whn4DgXB4fcg9gj95vKxYN2apkZD",
"publicKey": [{
"id": "did:v1:test:nym:DwkYwcoyUXHNkpj3whn4DgXB4fcg9gj95vKxYN2apkZD#authn-key-1",
"type": "Ed25519VerificationKey2018",
"publicKeyBase58": "DwkYwcoyUXHNkpj3whn4DgXB4fcg9gj95vKxYN2apkZD"
}],
"authentication": [{
"type": "Ed25519SignatureAuthentication2018",
"publicKey": “did:v1:test:nym:DwkYwcoyUXHNkpj3whn4DgXB4fcg9gj95vKxYN2apkZD#authn-key-1”
}],
"service": [{
"type": "ExampleMessagingService2018",
"serviceEndpoint": ”https://example.com/services/messages”
}],
… more DID-specific information here …
}
2. Authentication
Mechanisms
3. Service Discovery
1. Public Key Material
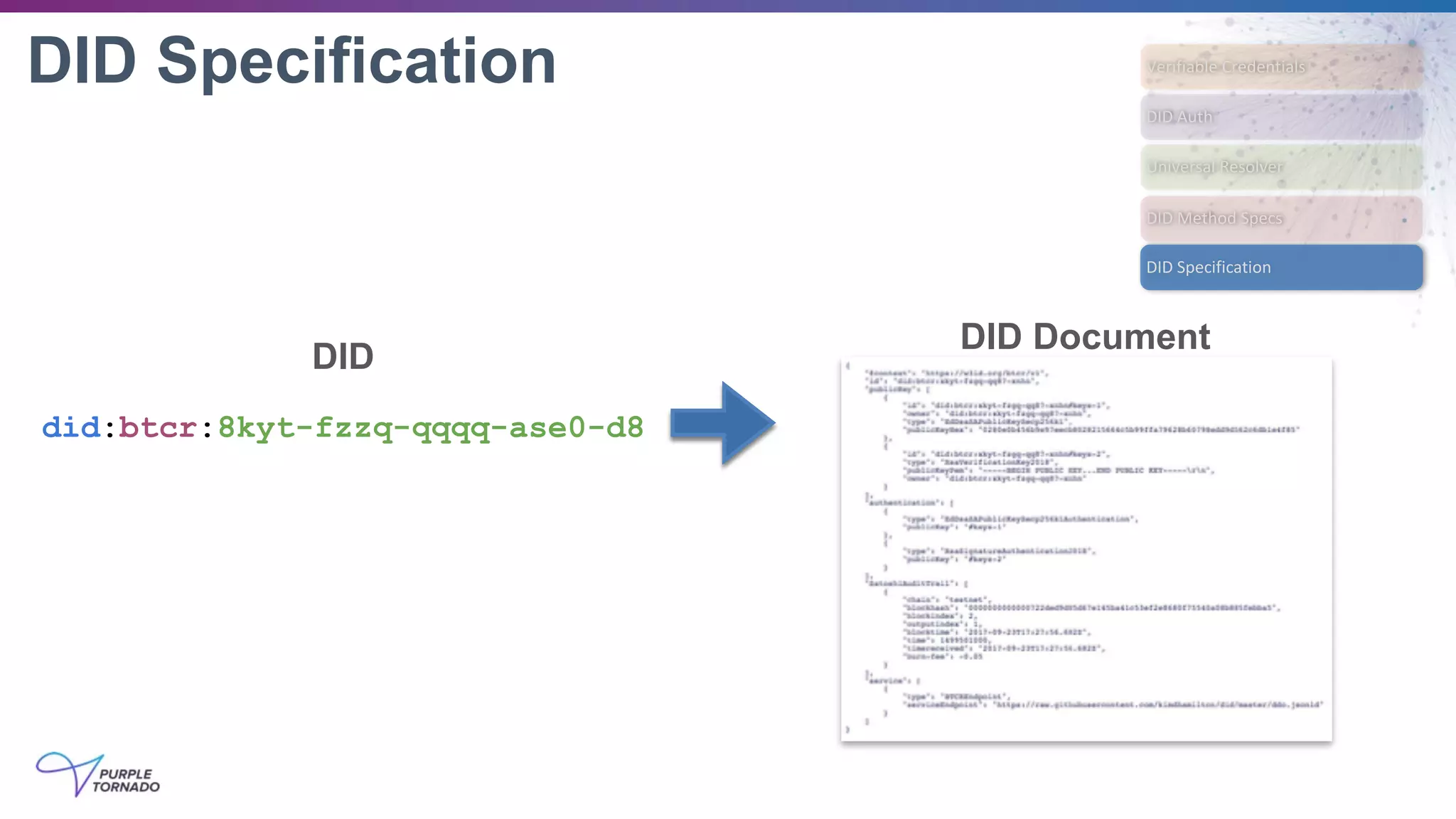
DIDs Resolve to DID Documents
DID Specification
Universal Resolver
DID Auth
Verifiable Credentials
DID Method Specs](https://image.slidesharecdn.com/ssi-iiw-duffyvescent4-190506145828/75/Introduction-to-Self-Sovereign-Identity-33-2048.jpg)
![{
"@context":"https://w3id.org/veres-one/v1”,
"id":"did:v1:test:nym:5YSwjvBZqDbYQkoRG7jD7bCKifVdHBtxHMrATZyTX8xv",
"publicKey":[{
"id":"did:v1:test:nym:5YSwjvBZqDbYQkoRG7jD7bCKifVdHBtxHMrATZyTX8xv#authn-key-1",
"type":"Ed25519VerificationKey2018",
"owner":"did:v1:test:nym:5YSwjvBZqDbYQkoRG7jD7bCKifVdHBtxHMrATZyTX8xv",
"publicKeyBase58":"5YSwjvBZqDbYQkoRG7jD7bCKifVdHBtxHMrATZyTX8xv"
}, {
"id":"did:v1:test:nym:5YSwjvBZqDbYQkoRG7jD7bCKifVdHBtxHMrATZyTX8xv#ocap-grant-key-1",
...
}, {
"id":"did:v1:test:nym:5YSwjvBZqDbYQkoRG7jD7bCKifVdHBtxHMrATZyTX8xv#ocap-invoke-key-1",
}],
"authentication":[{
"type":"Ed25519SignatureAuthentication2018",
"publicKey": "did:v1:test:nym:5YSwjvBZqDbYQkoRG7jD7bCKifVdHBtxHMrATZyTX8xv#authn-key-1”
}],
"grantCapability":[{
"type":"Ed25519SignatureCapabilityAuthorization2018",
"publicKey": "did:v1:test:nym:5YSwjvBZqDbYQkoRG7jD7bCKifVdHBtxHMrATZyTX8xv#ocap-grant-key-1”
}],
"invokeCapability":[{
"type":"Ed25519SignatureCapabilityAuthorization2018",
"publicKey": "did:v1:test:nym:5YSwjvBZqDbYQkoRG7jD7bCKifVdHBtxHMrATZyTX8xv#ocap-invoke-key-1”
}]
DID Specification
Universal Resolver
DID Auth
Verifiable Credentials
DID Method SpecsDID Method Specs
DID Method Spec
{
"@context": "https://w3id.org/did/v1",
"id": "did:ethr:0xb9c5714089478a327f09197987f16f9e5d936e8a",
"publicKey": [{
"id": "did:ethr:0xb9c5714089478a327f09197987f16f9e5d936e8a#owner",
"type": "Secp256k1VerificationKey2018",
"owner": "did:ethr:0xb9c5714089478a327f09197987f16f9e5d936e8a",
"ethereumAddress": "0xb9c5714089478a327f09197987f16f9e5d936e8a"
}],
"authentication" : [{
type: "Secp256k1SignatureAuthentication2018",
publicKey: "did:ethr:0xb9c5714089478a327f09197987f16f9e5d936e8a#owner"
}],
"service" : [{
type: "HubService",
serviceEndpoint: "https://hubs.uport.me"
}]
}
Veres One
ETHR](https://image.slidesharecdn.com/ssi-iiw-duffyvescent4-190506145828/75/Introduction-to-Self-Sovereign-Identity-34-2048.jpg)








![Verifiable Credentials and DIDs
{
"type": ["VerifiableCredential", "UniversityDegreeCredential"],
"issuer": "did:example:2ec211f712ebc6e1ebfeb6f1c27",
"credentialSubject": {
"id": "did:example:ebfeb1f712ebc6f1c276e12ec21",
"degree": {
"type": "BachelorDegree",
"name": "Bachelor of Science in Mechanical Engineering"
}
},
"proof": {
"type": "RsaSignature2018",
"created": "2017-06-18T21:19:10Z",
"creator": "did:example:2ec211f712ebc6e1ebfeb6f1c27#keys-1",
"nonce": "c0ae1c8e-c7e7-469f-b252-86e6a0e7387e",
"signatureValue": "BavEll0/I1zpYw8XNi1bgVg/sCneO4Jugez8RwDg/+
MCRVpjOboDoe4SxxKjkCOvKiCHGDvc4krqi6Z1n0UfqzxGfmatCuFibcC1wps
PRdW+gGsutPTLzvueMWmFhwYmfIFpbBu95t501+rSLHIEuujM/+PXr9Cky6Ed
+W3JT24="
}
}
Recipient DID
Issuer DID](https://image.slidesharecdn.com/ssi-iiw-duffyvescent4-190506145828/75/Introduction-to-Self-Sovereign-Identity-46-2048.jpg)