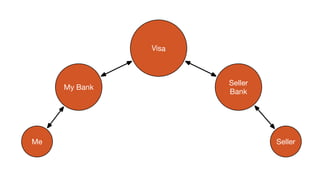
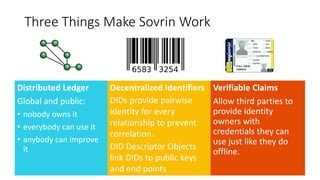
The document discusses self-sovereign identity (SSI) as an alternative to traditional trust models, emphasizing its ability to simplify workflows and integrations by allowing instant trust in claims made by individuals. It outlines how decentralized identifiers (DIDs) and verifiable claims facilitate pairwise identities and credentials, fostering a globally accessible and publicly improved identity system. The framework promotes universal trust and individual sovereignty through its innovative design.