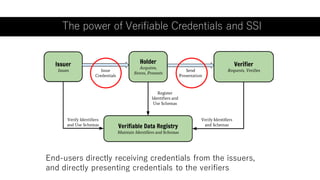
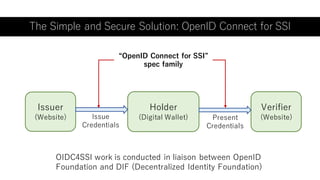
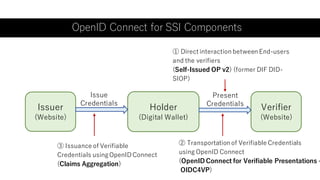
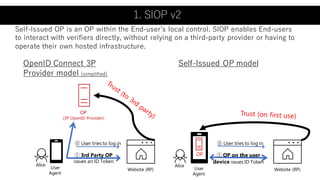
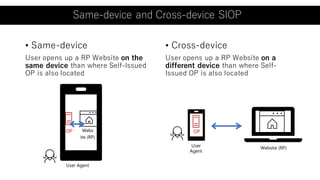
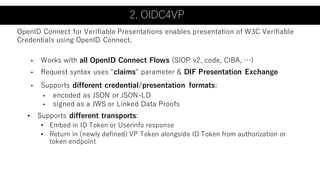
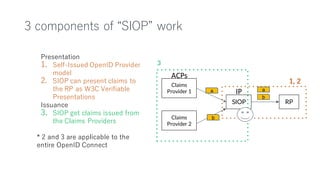
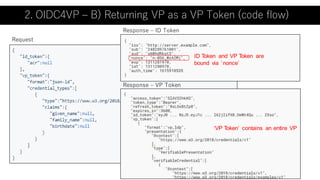
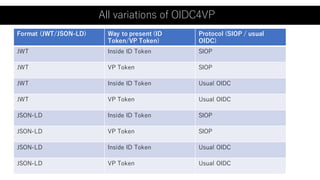
The document outlines a framework using OpenID Connect for Self-Sovereign Identity (SSI) by facilitating direct interactions between end-users and verifiers via verifiable credentials. It discusses several specifications, including Self-Issued OpenID Provider (SIOP) V2 and OpenID Connect for Verifiable Presentations (OIDC4VP), which allow holders to directly manage and present their credentials from wallets. Additionally, it highlights practical implementations, future developments, and the importance of integrating security and usability in SSI applications.