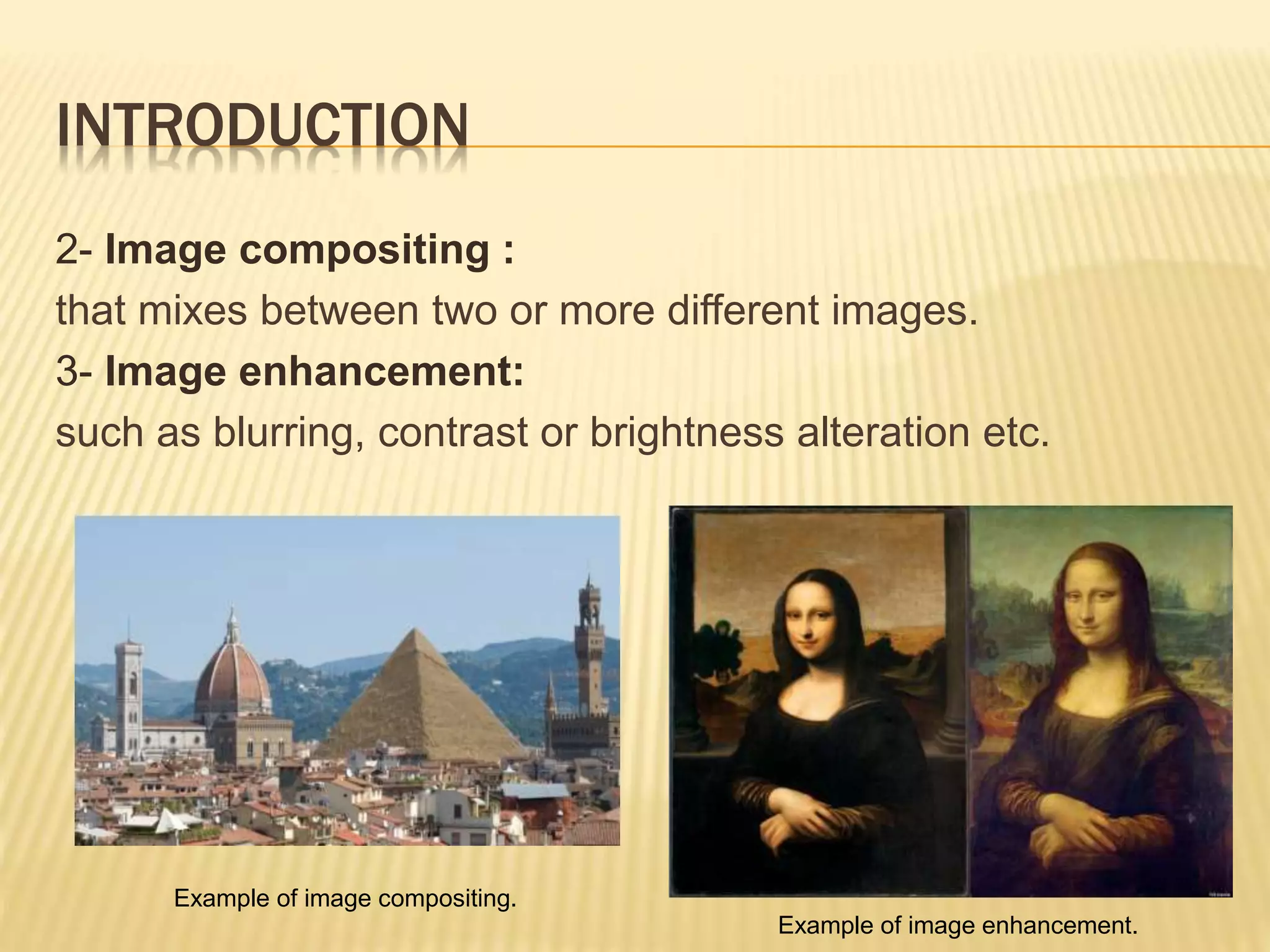
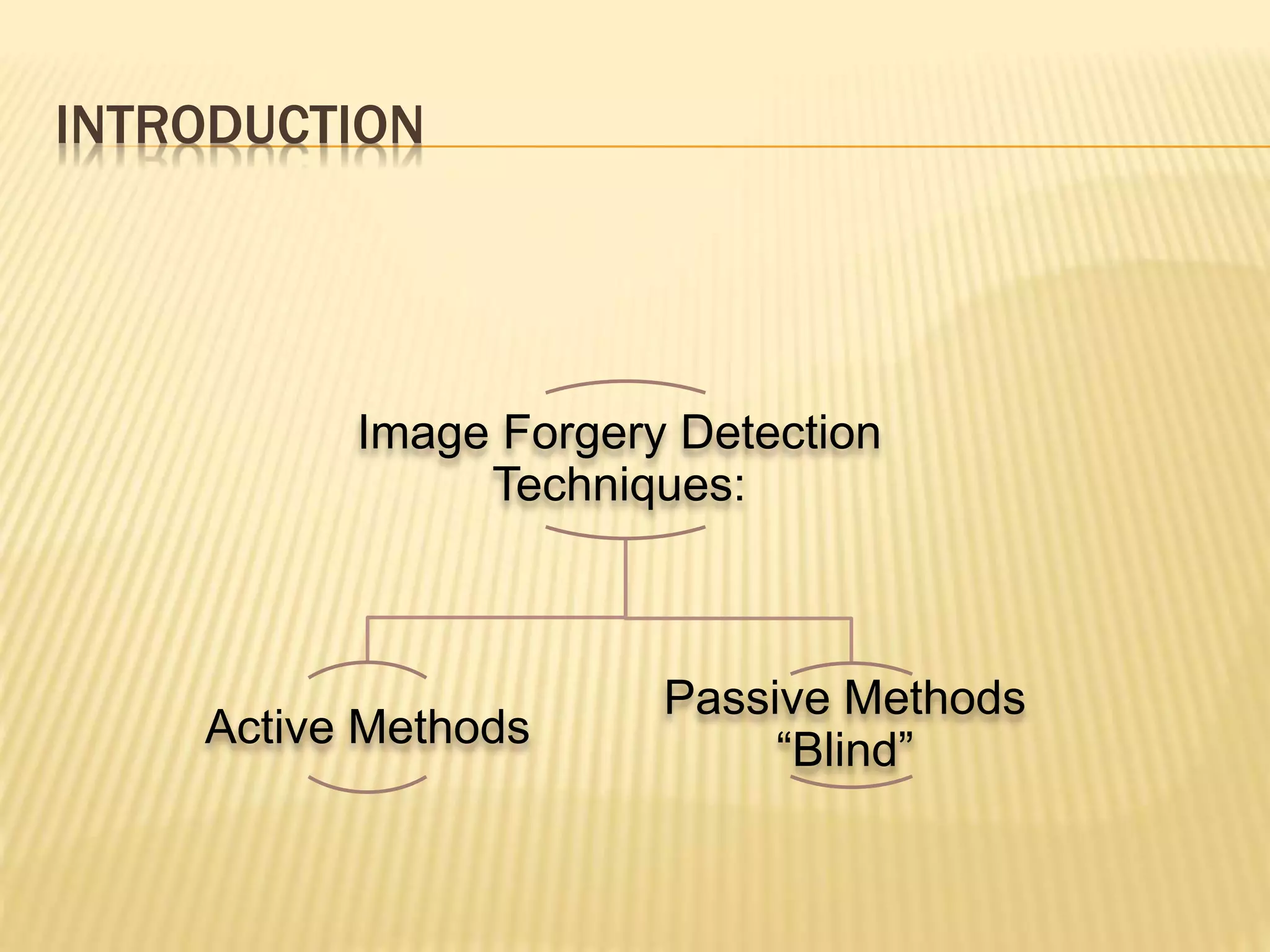
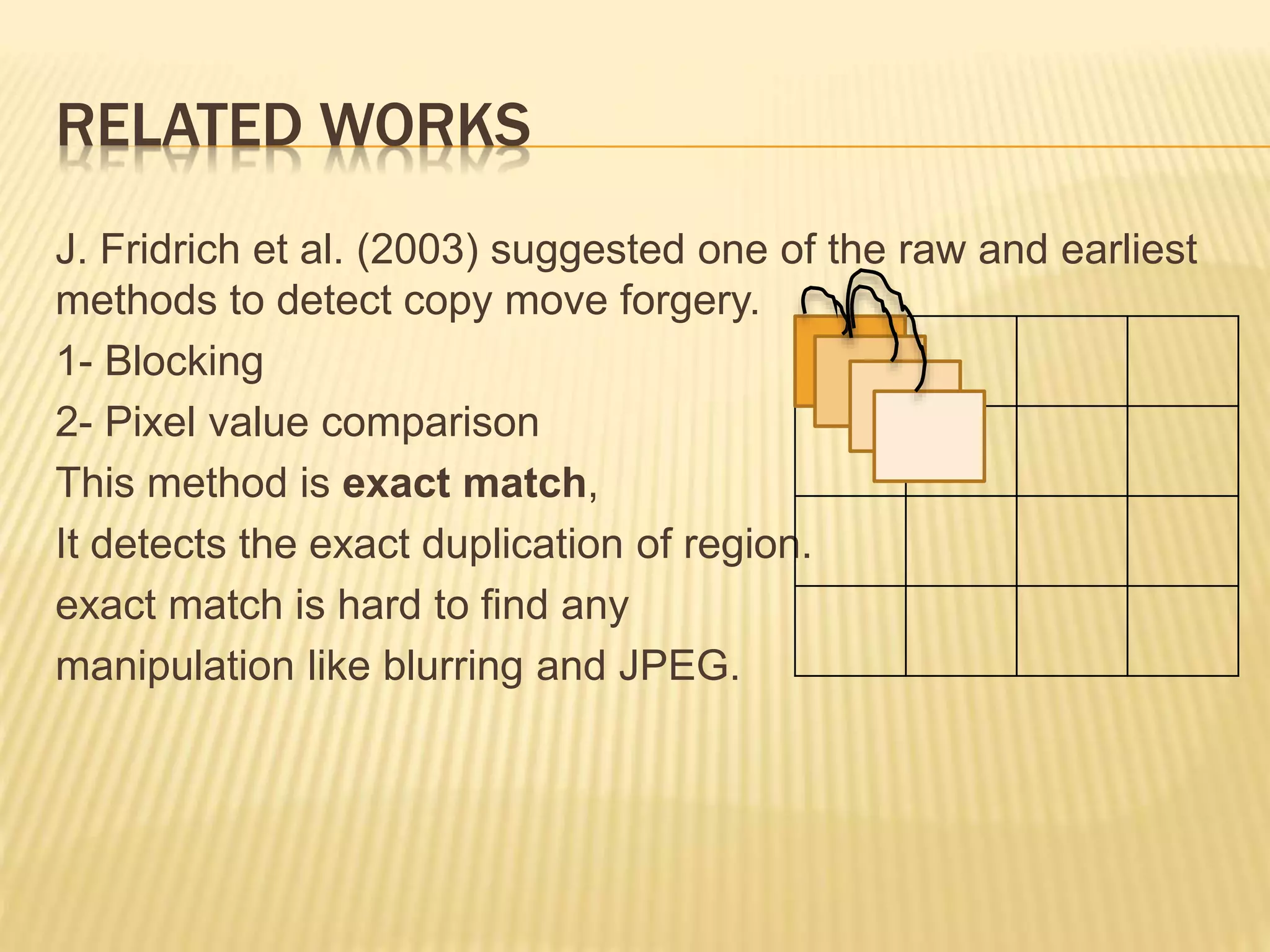
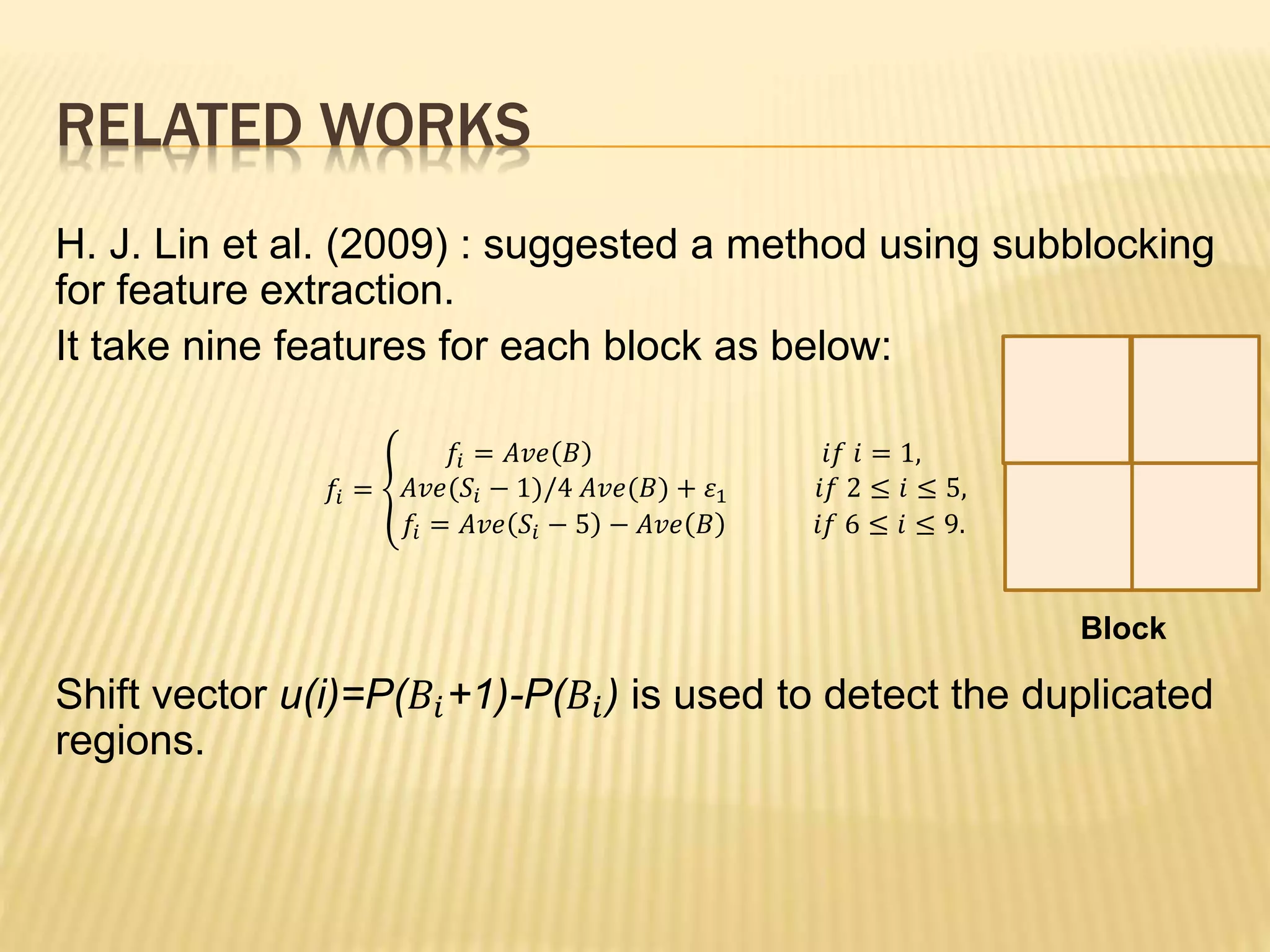
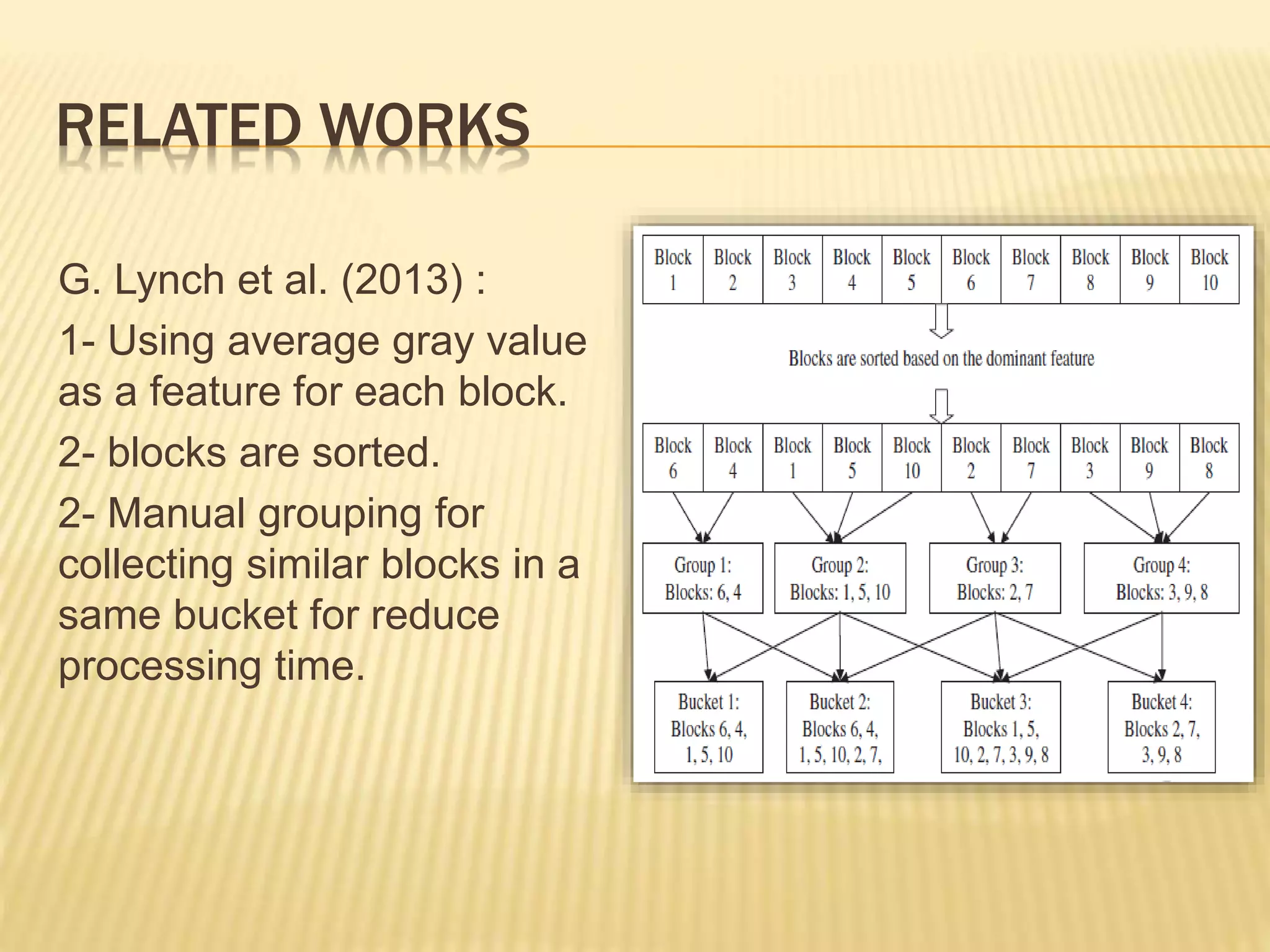
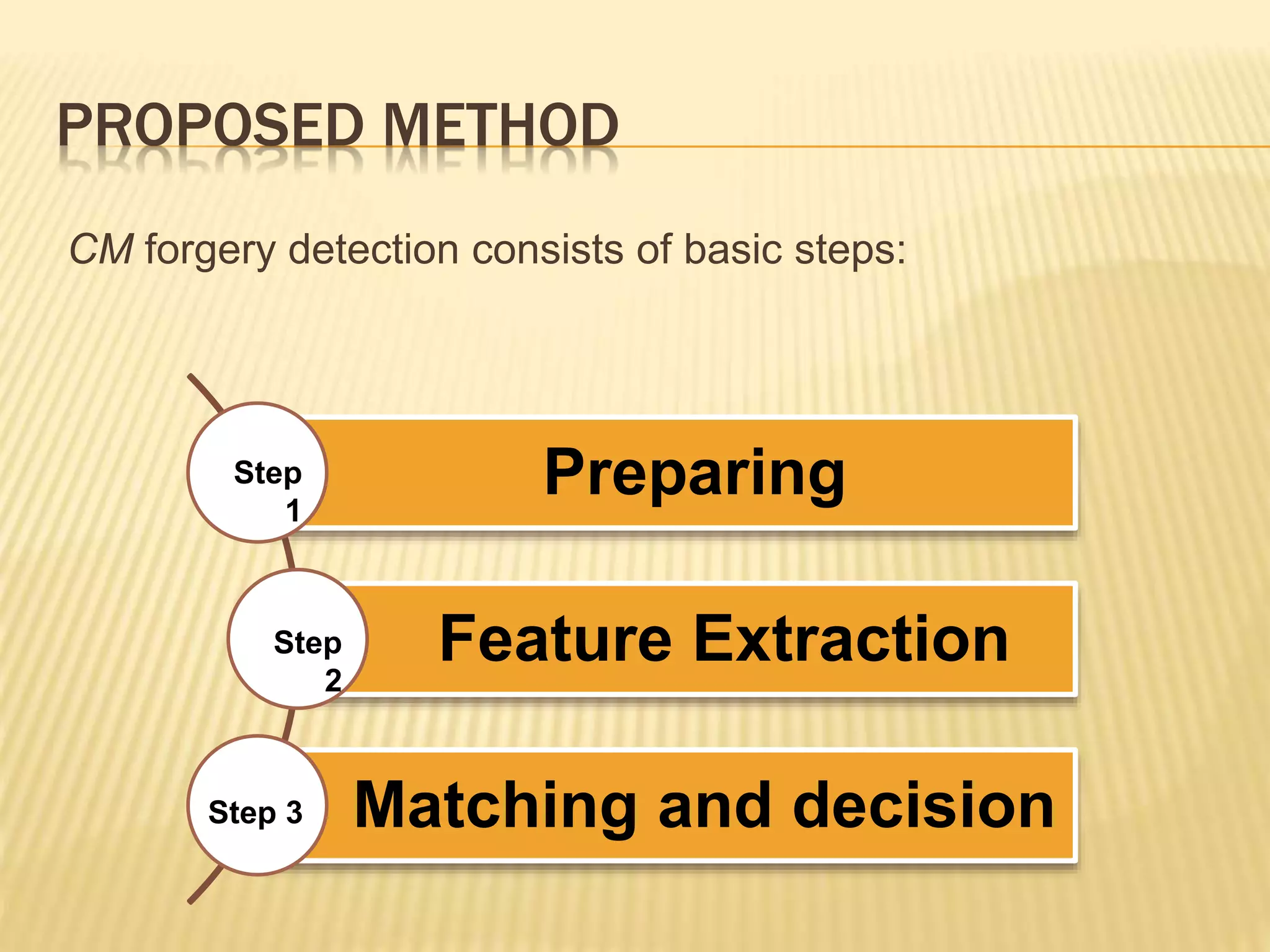
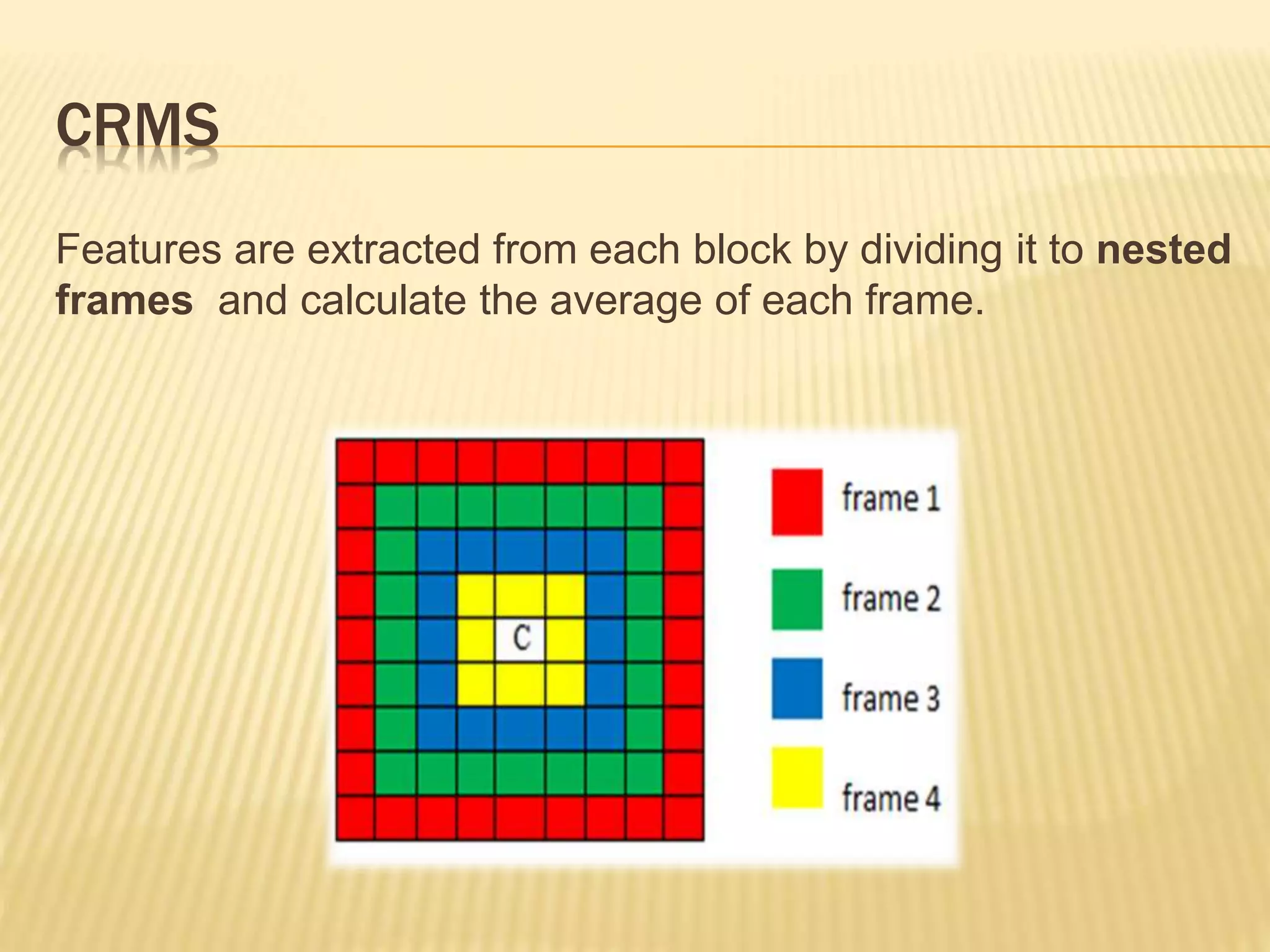
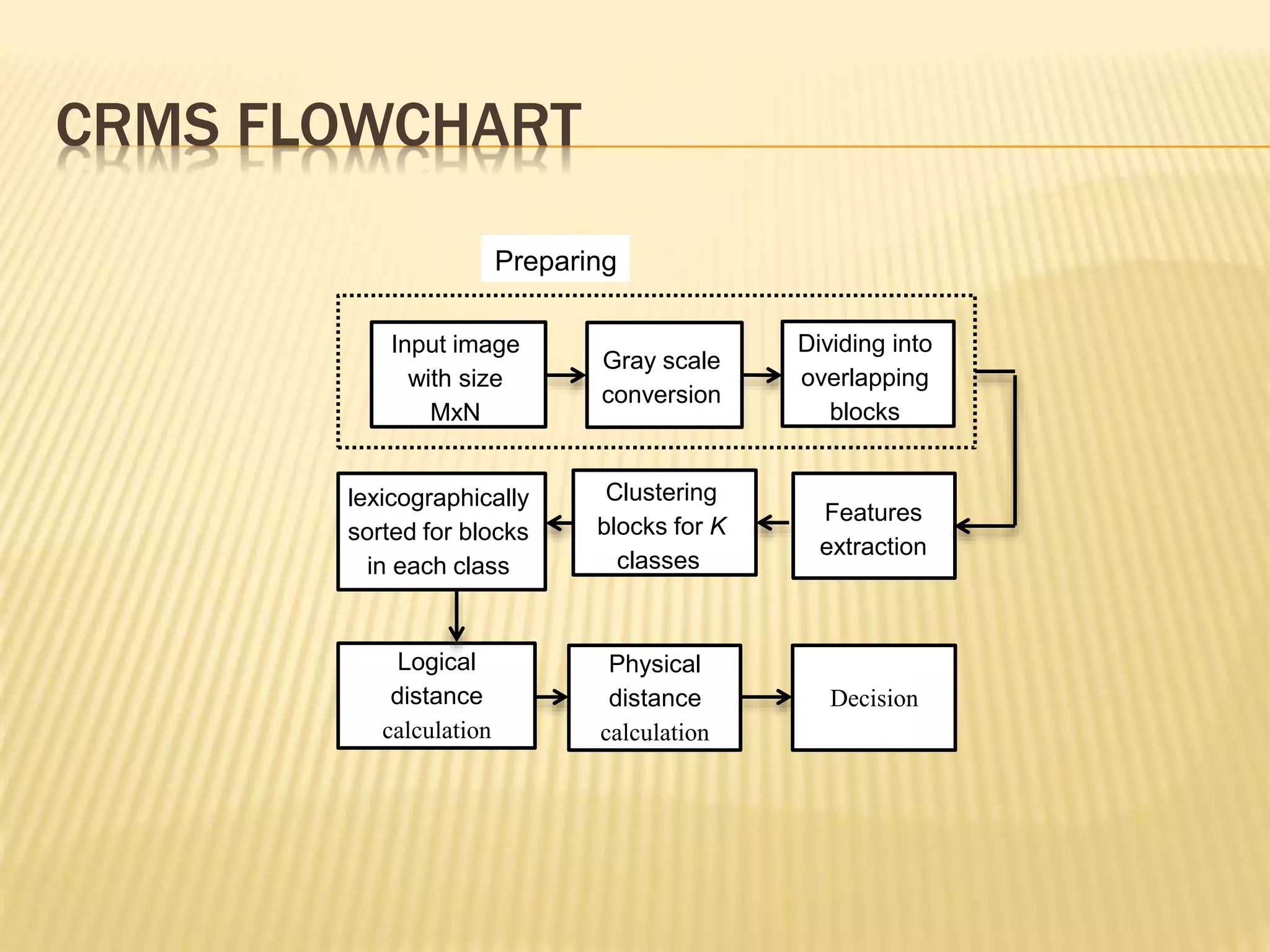
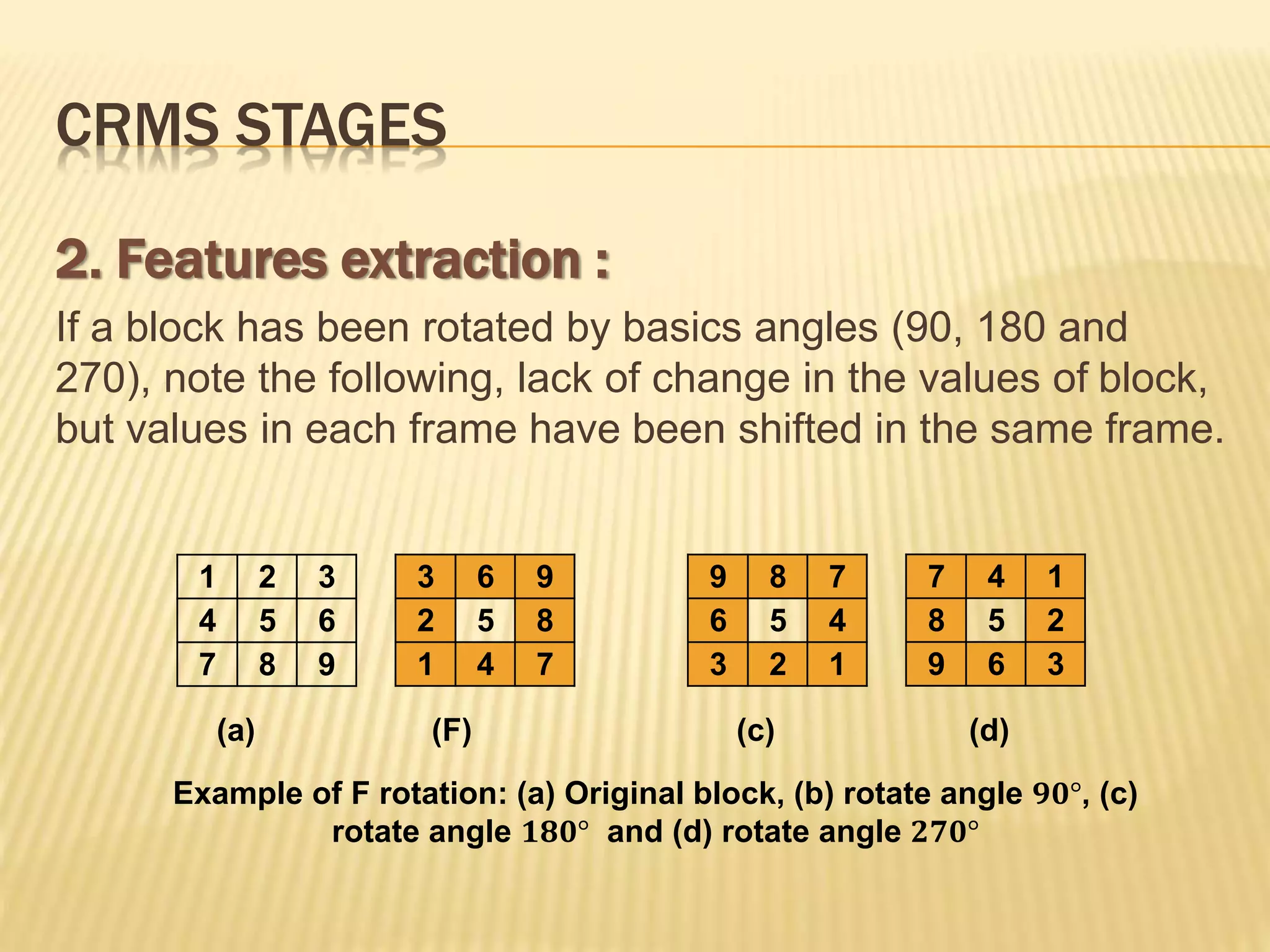
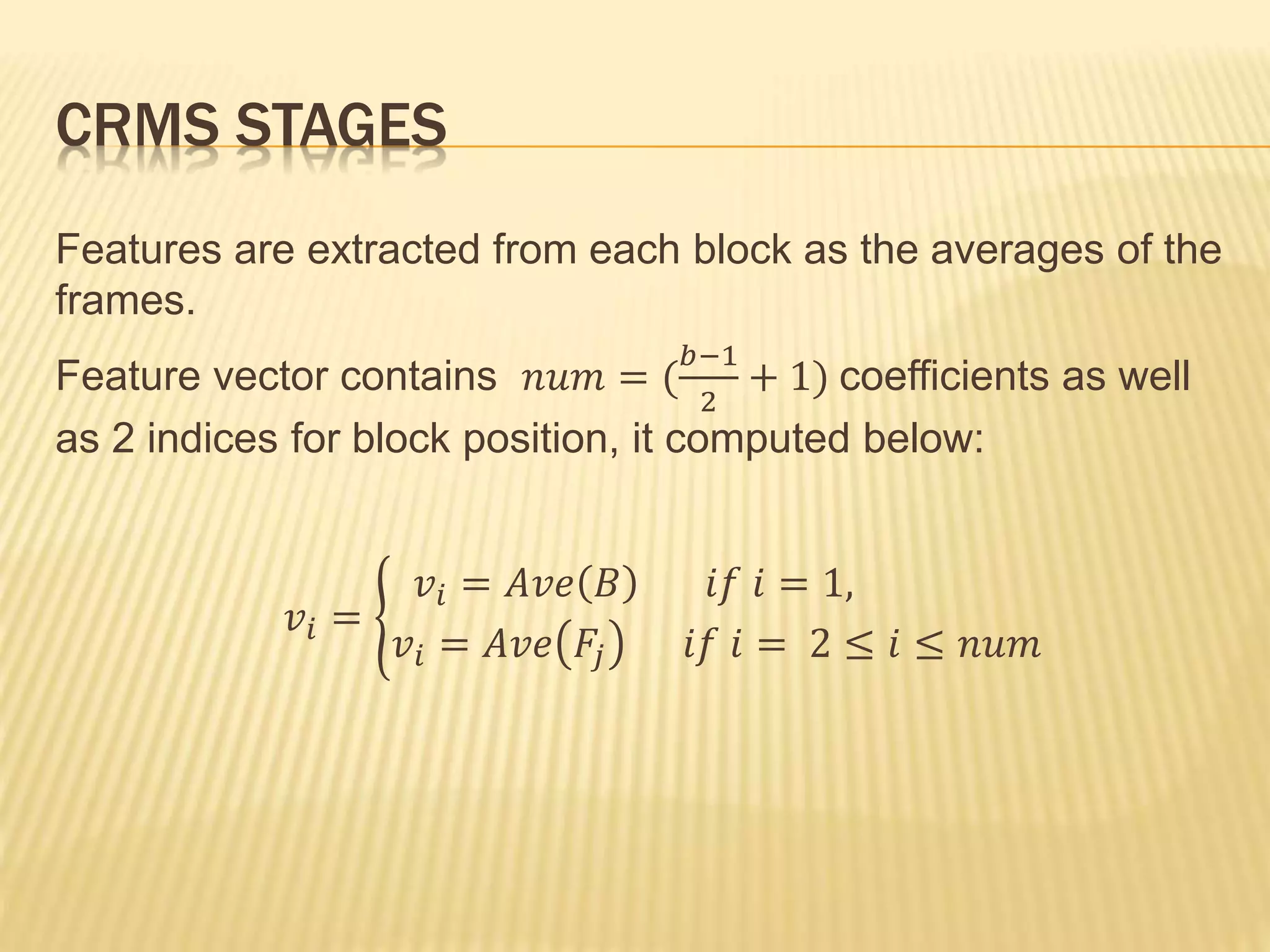
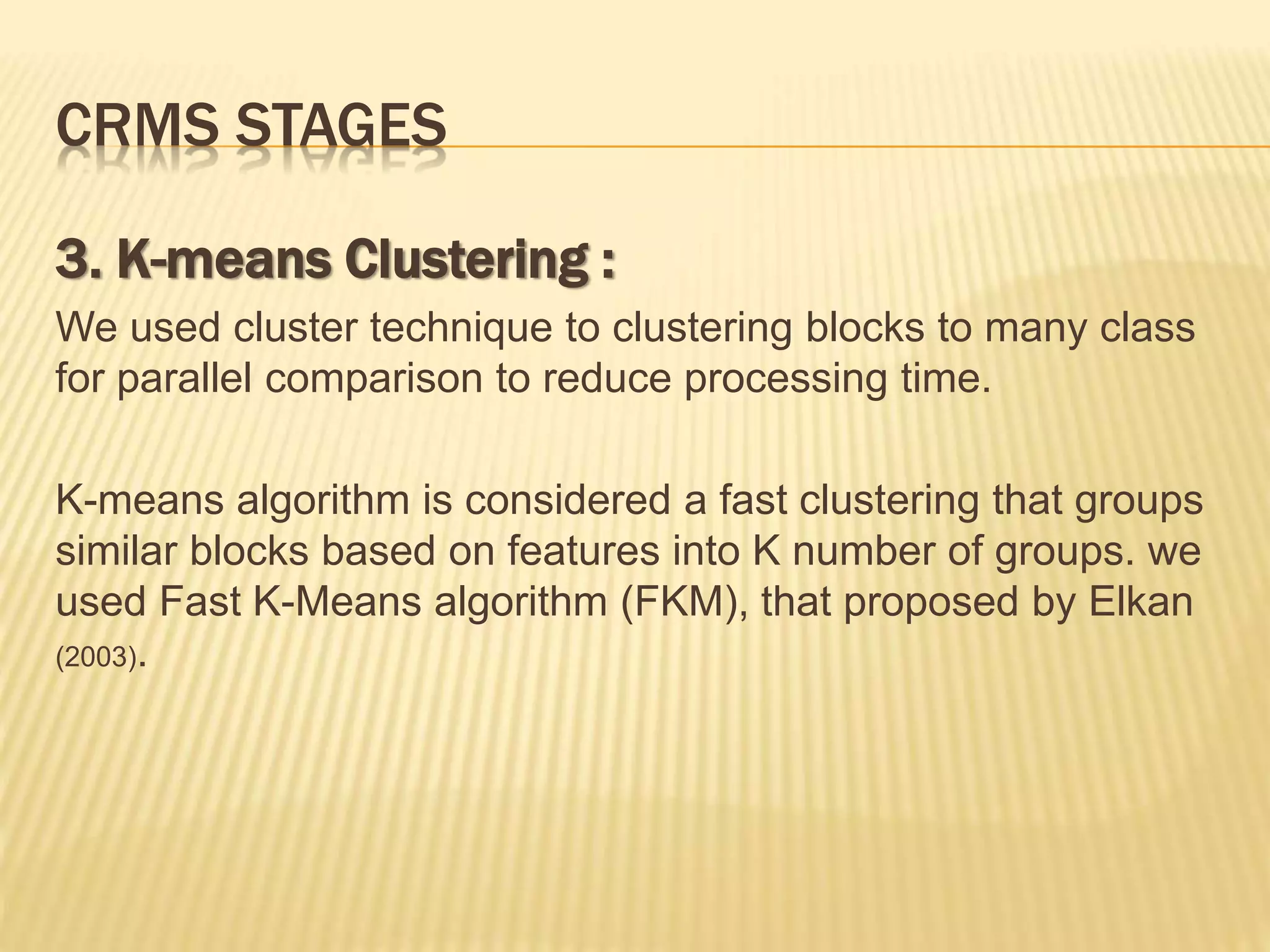
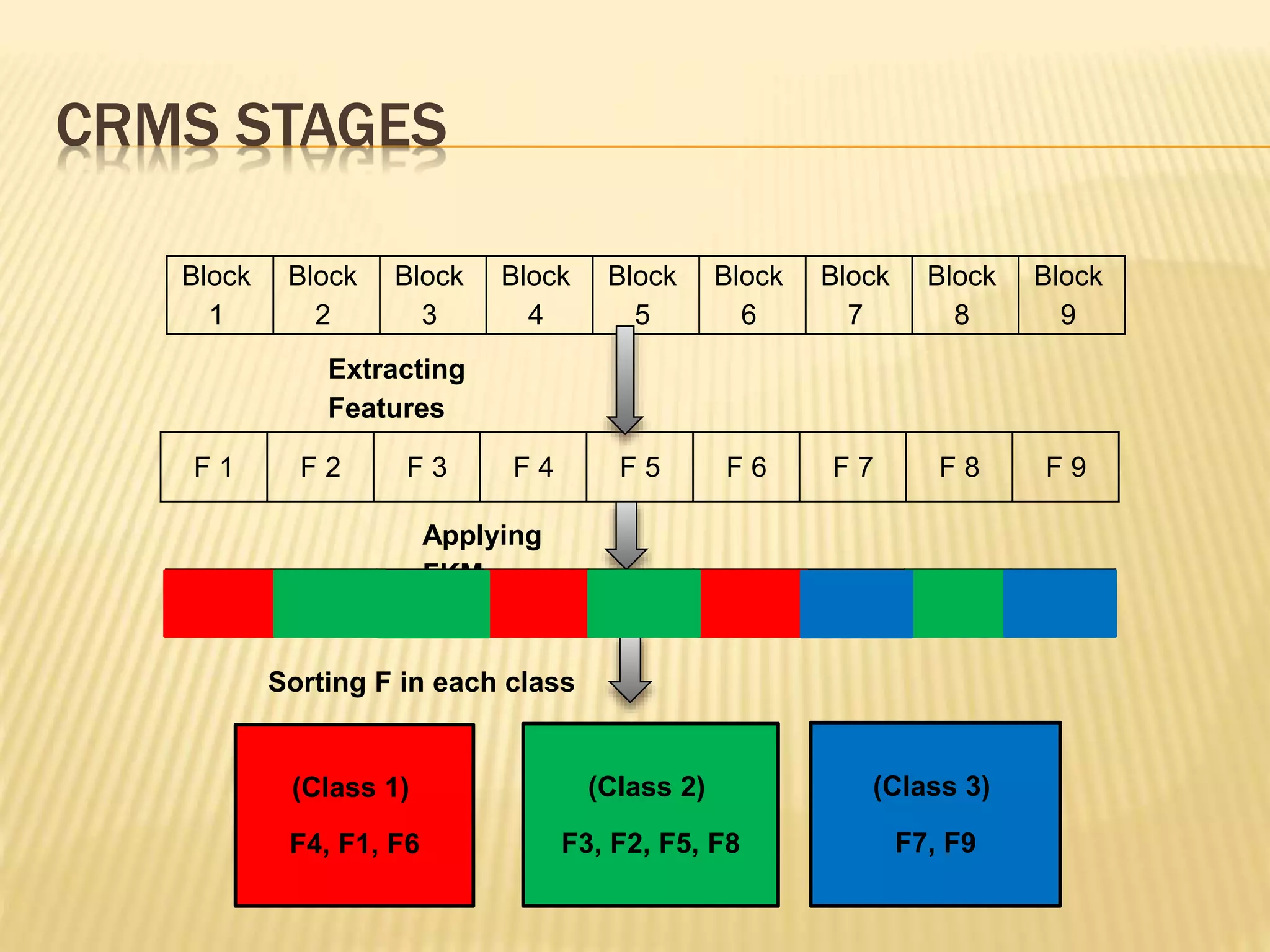
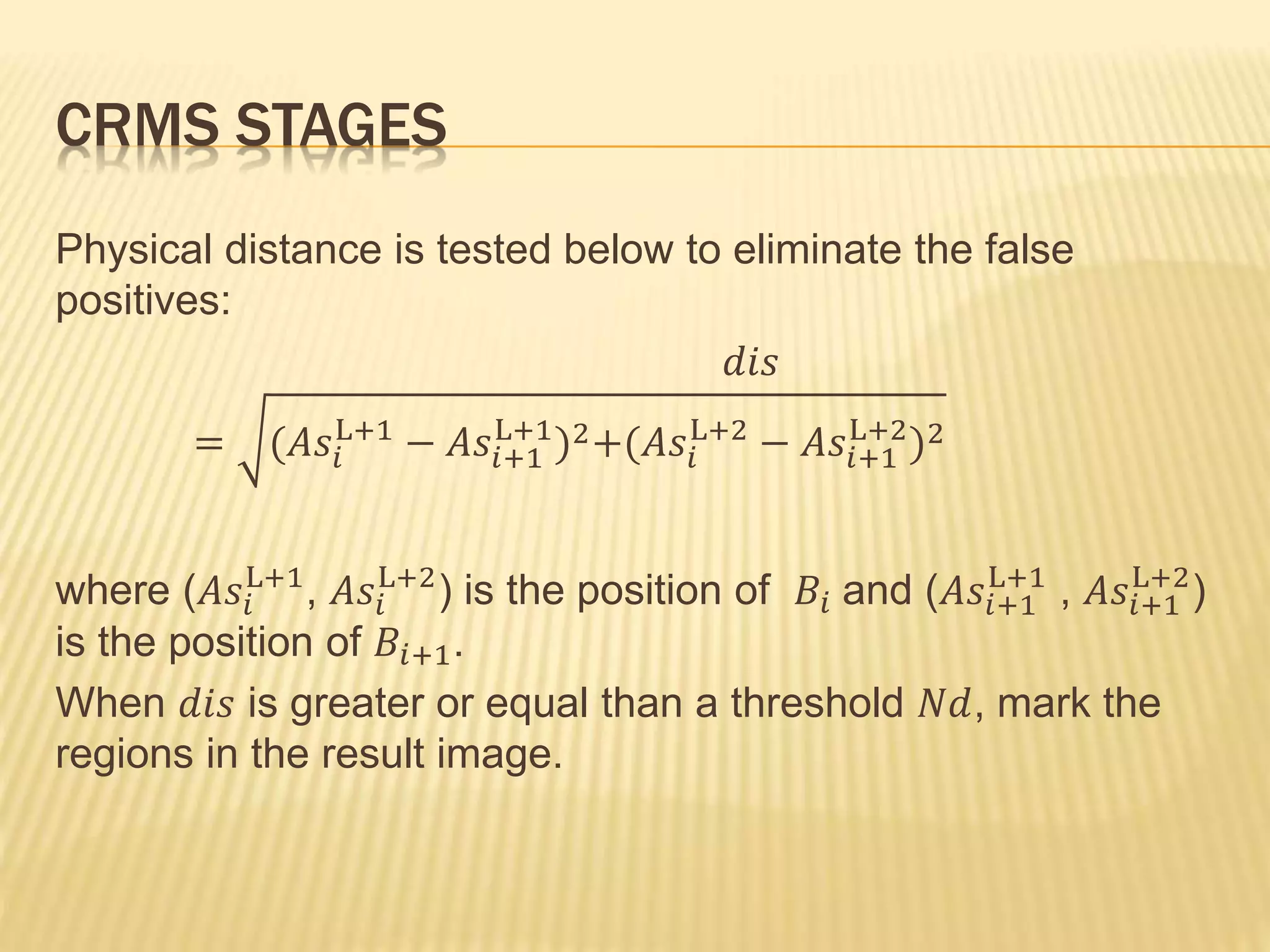
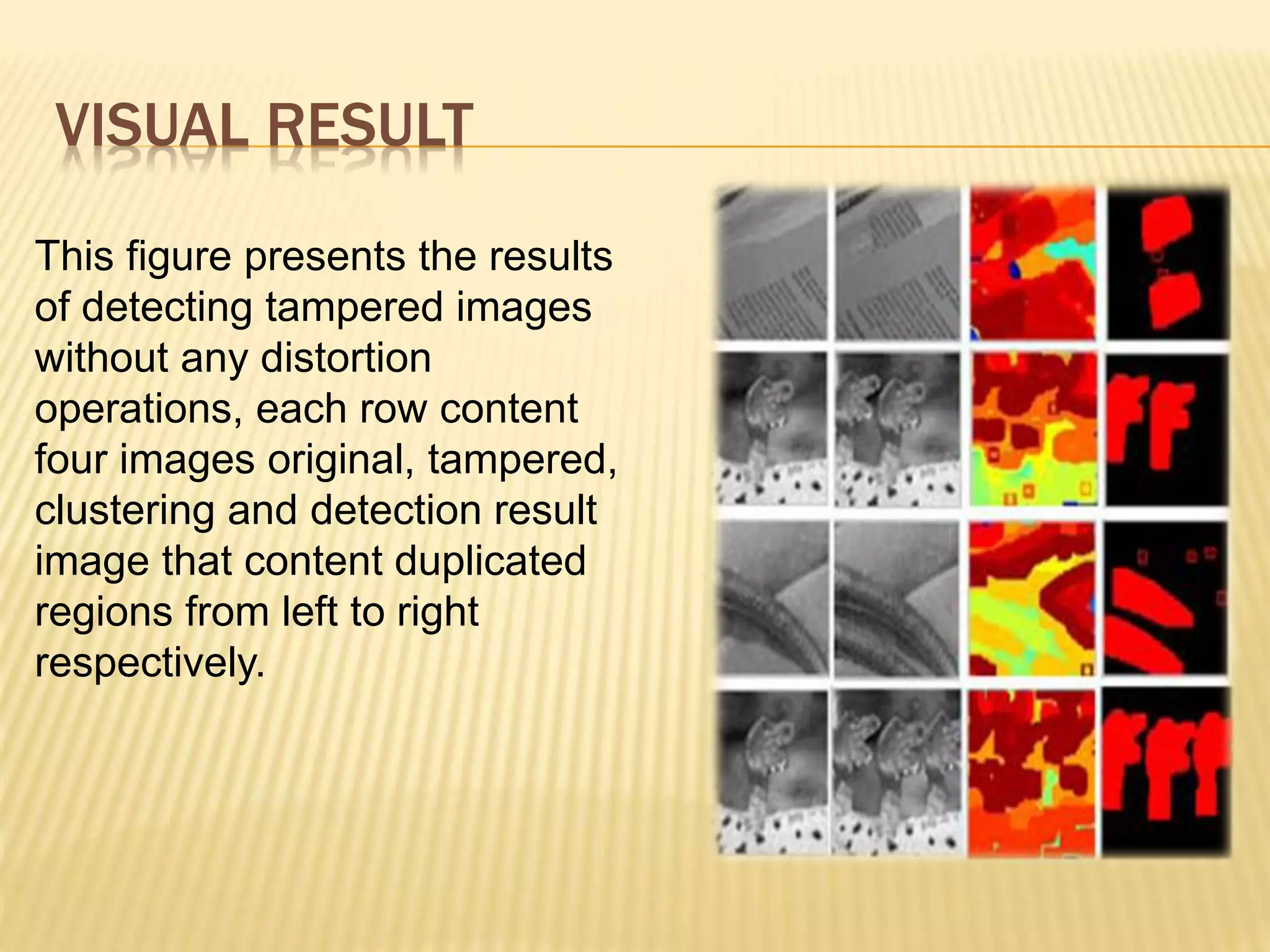
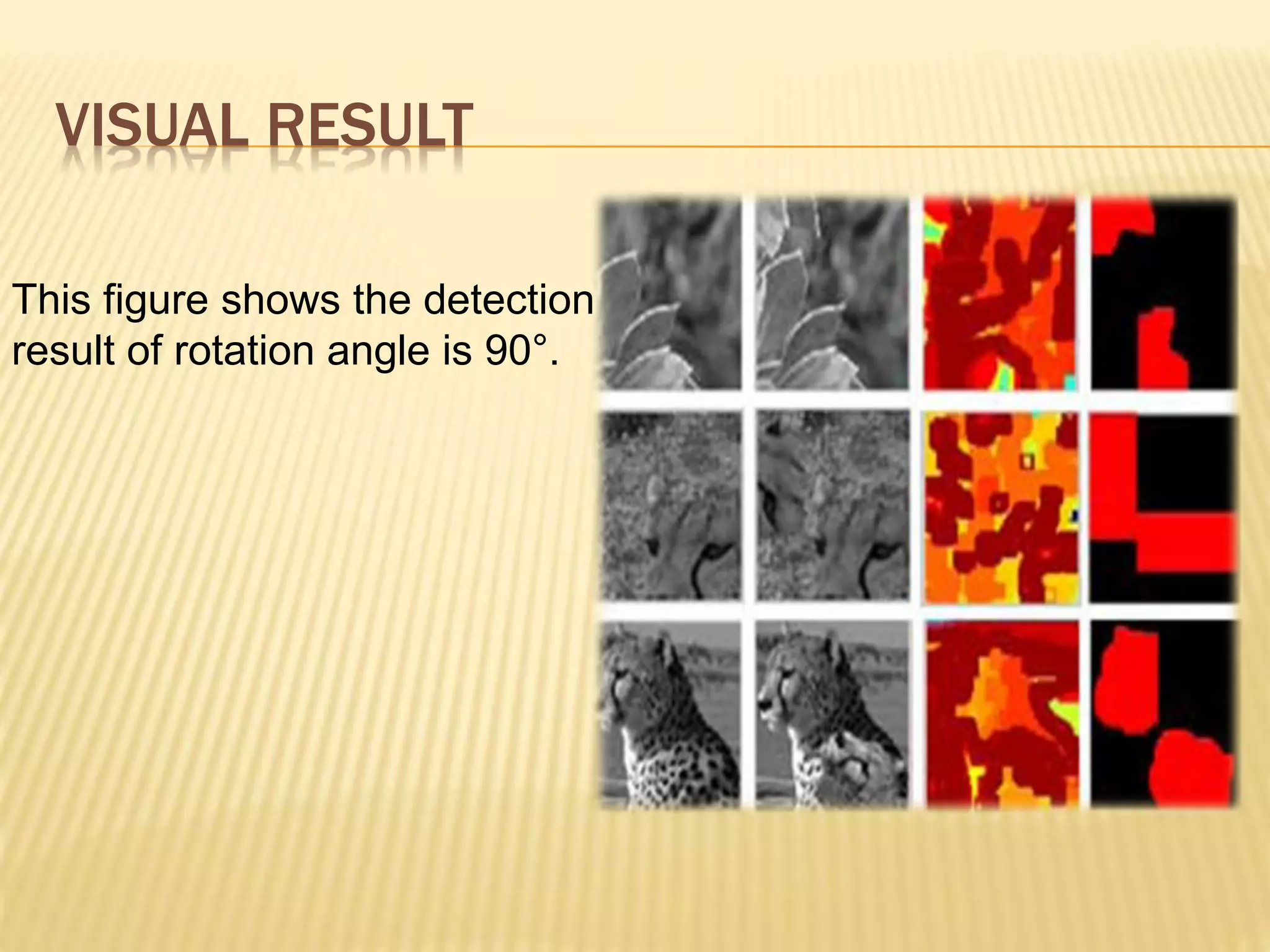
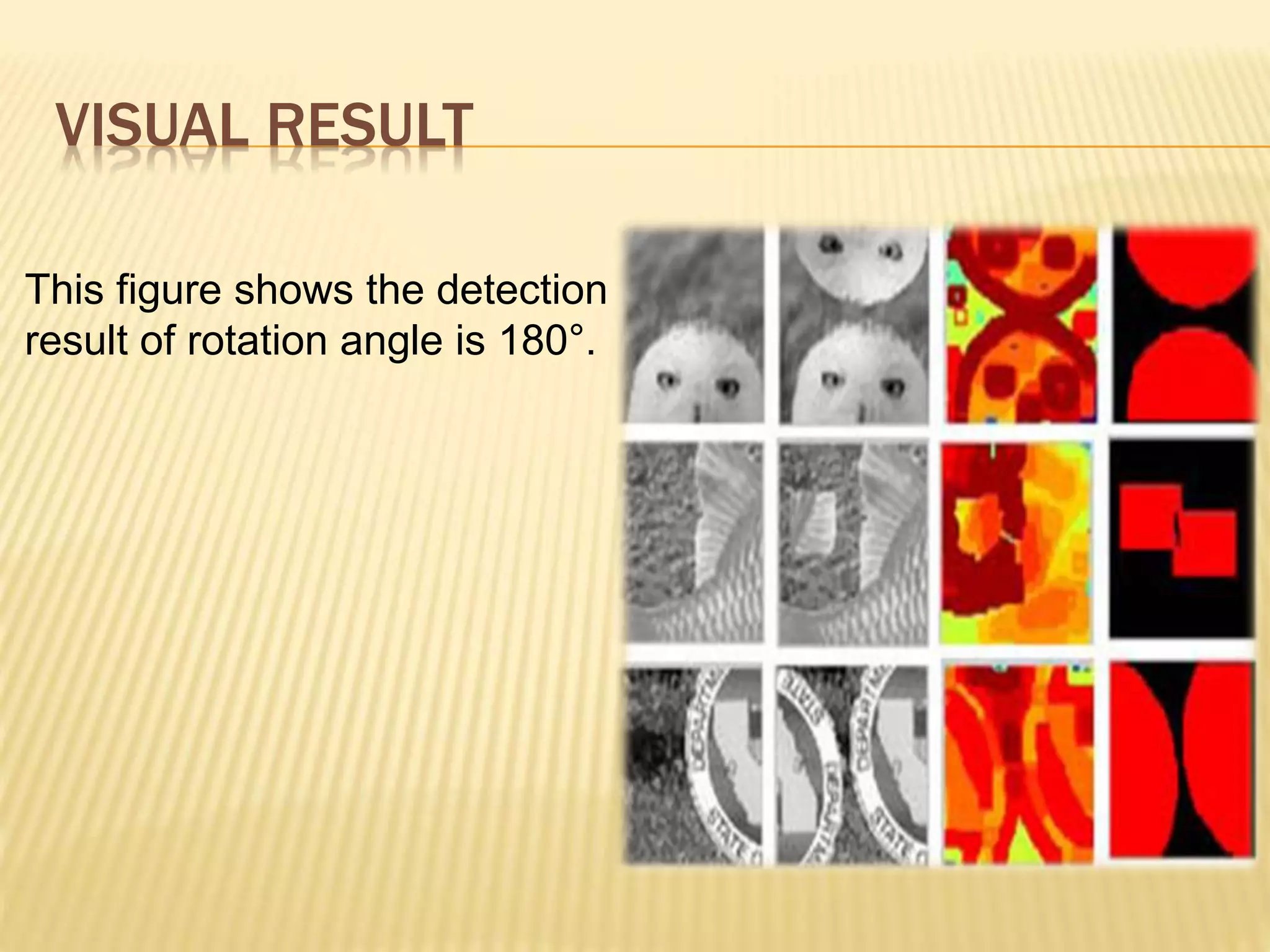
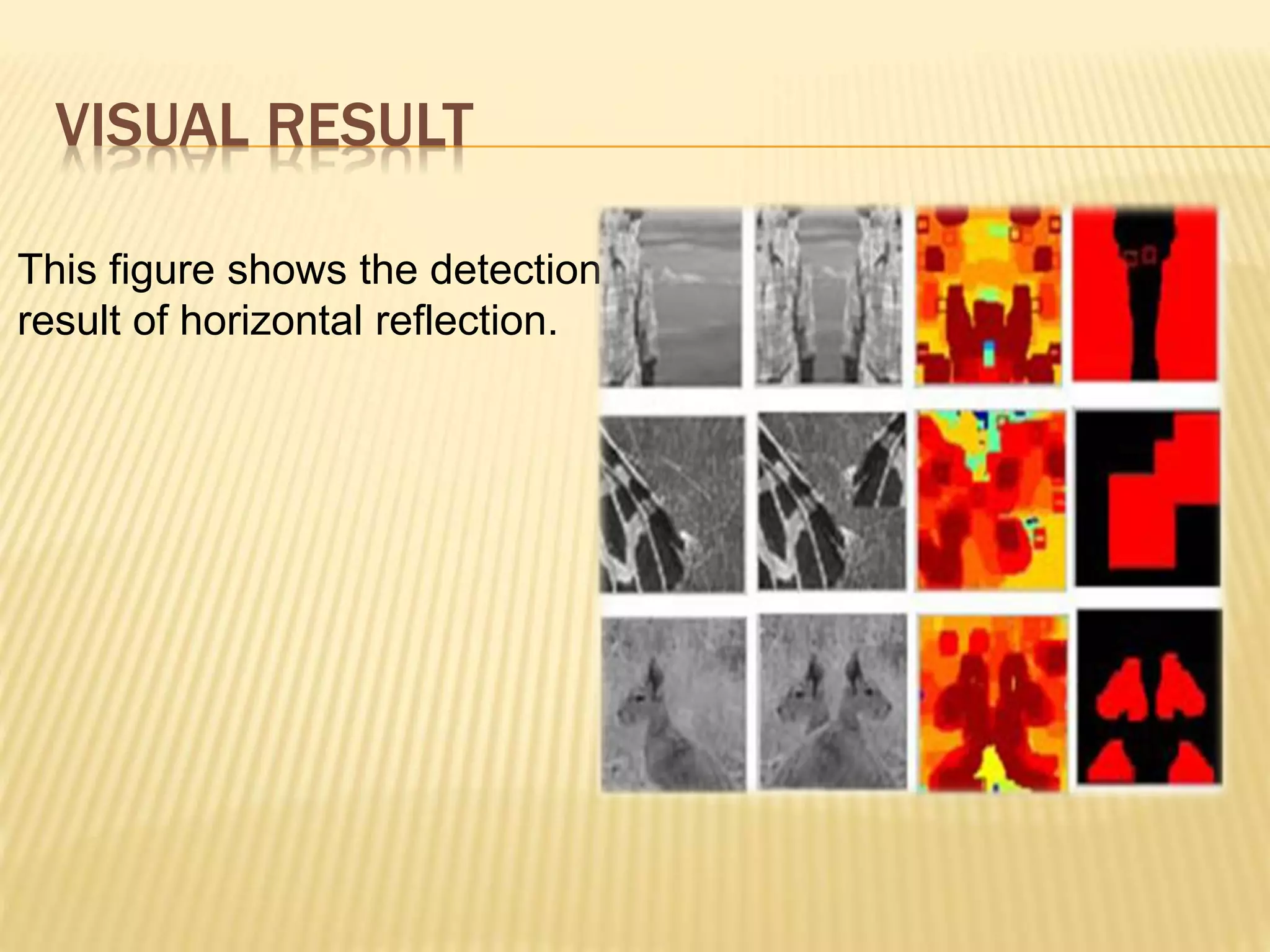
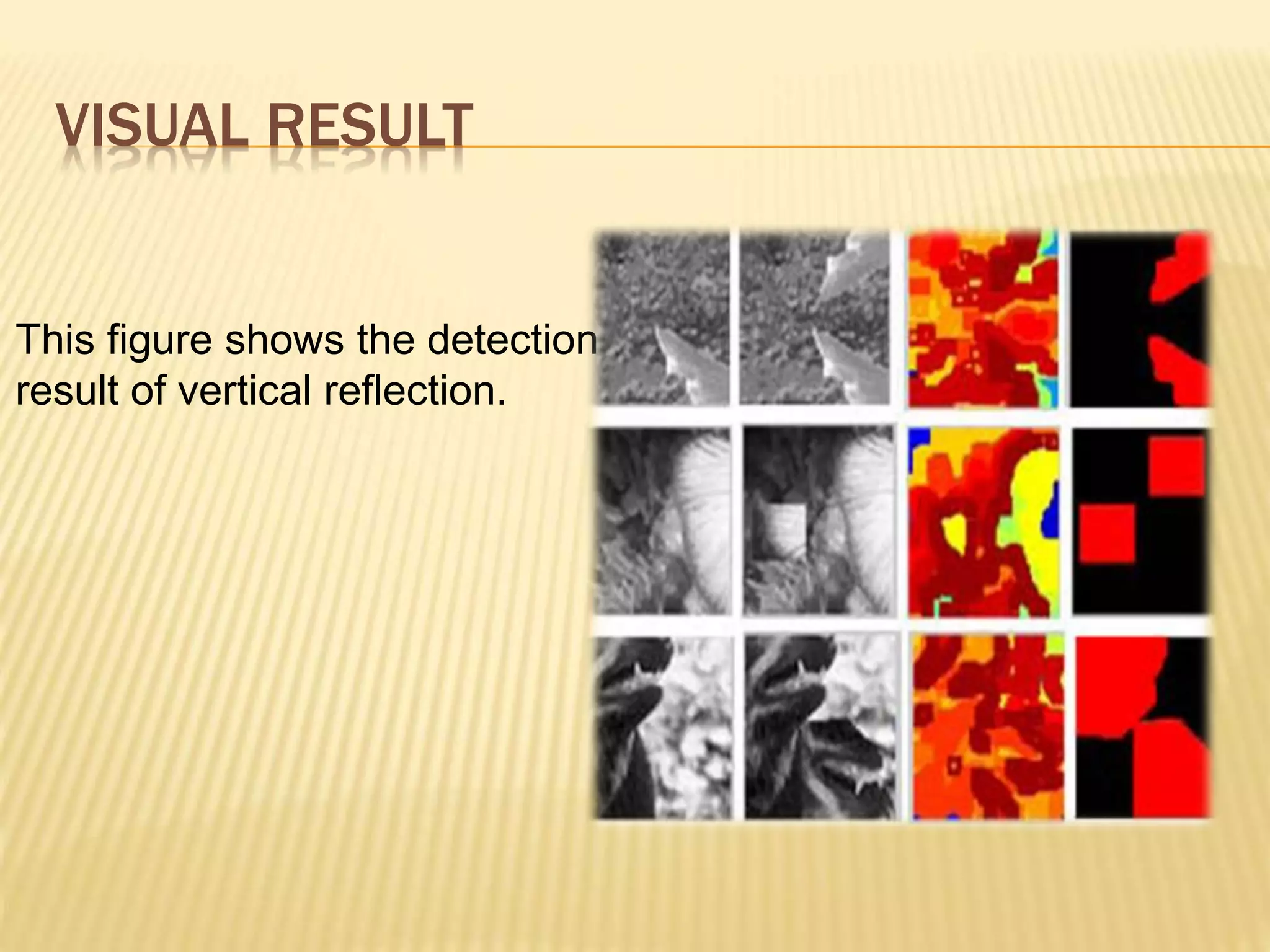
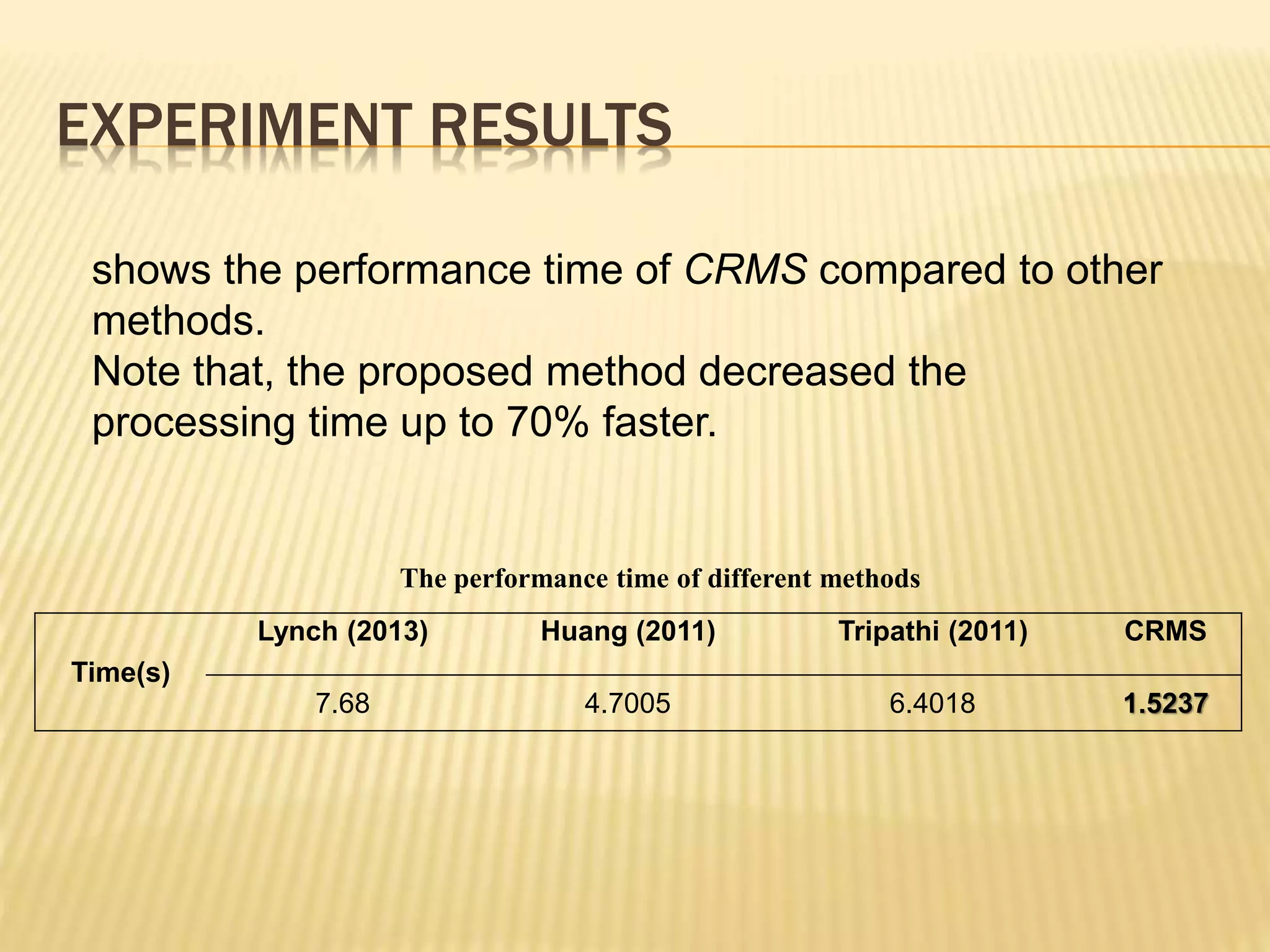
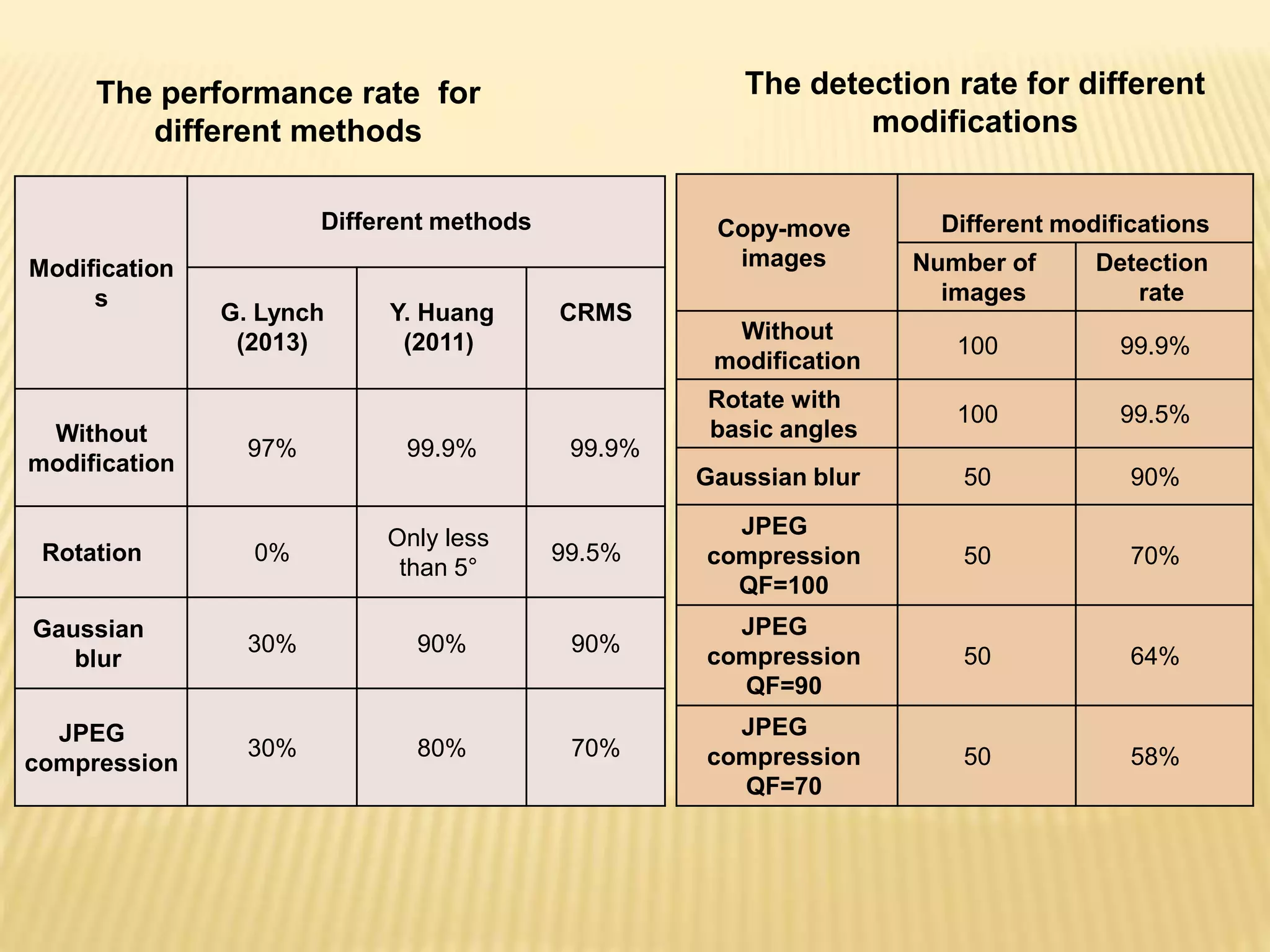
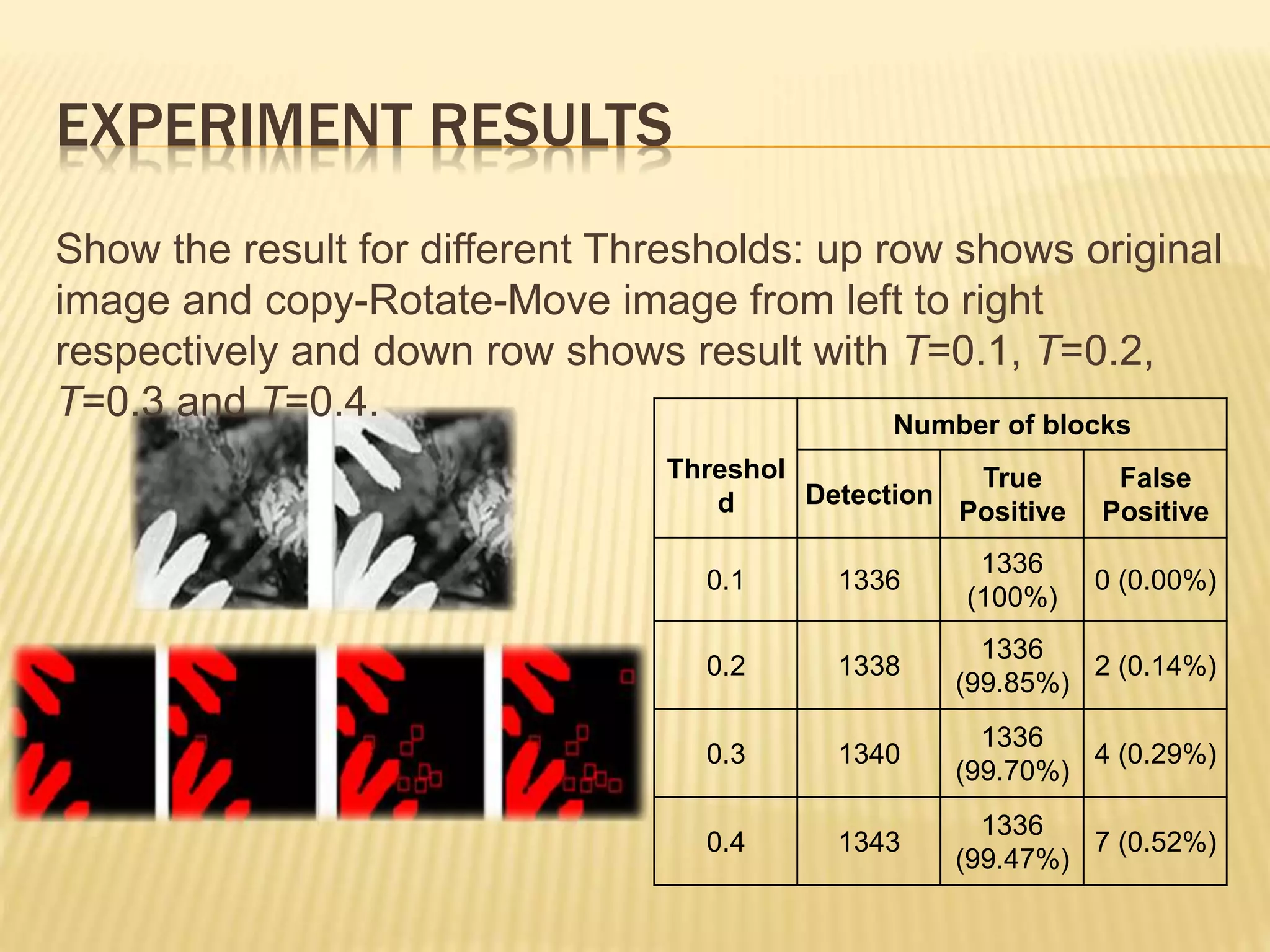
The document presents a method for detecting copy-move forgery in digital images, focusing on a technique called 'copy-rotate-move forgery detection based on spatial domain' (CRMS). The proposed method efficiently identifies duplicated regions in images, even if they have undergone rotation, by using block matching and feature extraction, achieving up to 70% faster processing time compared to existing methods. Experimental results indicate high detection accuracy across various image modifications, demonstrating the method's effectiveness in forgery detection.