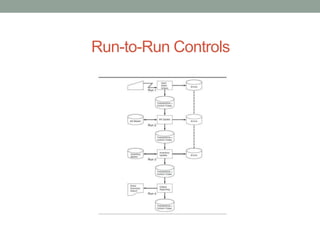
The document discusses computer-assisted audit tools and techniques, focusing on transaction input controls, processing controls, and output controls in accounting applications. It highlights various methods for ensuring data integrity and error management, including validation procedures, run-to-run controls, and output verification. The document also covers audit techniques such as test data method, integrated test facility, and parallel simulation for effective control testing.