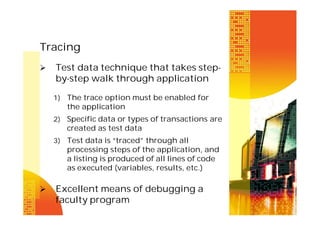
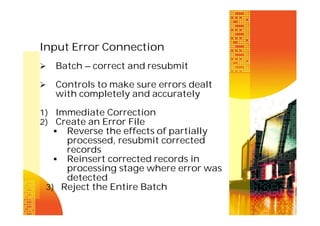
The document discusses various types of input controls, process controls, and output controls that can be used for computerized accounting information systems. It describes in detail classes of input controls like source document controls, data coding controls, batch controls, validation controls, input error correction, and generalized data input systems. It also discusses techniques for testing computer application controls like black box testing, white box testing, test data method, base case system evaluation, tracing, integrated test facility, and generalized audit software.














![Audit Trail Controls
Every transaction becomes
traceable from input to output
Each processing step is documented
Preservation is key to auditability of
AIS
Transaction logs
Log of automatic transactions
Listing of automatic transactions
Unique transaction identifiers [s/n]
Error listing](https://image.slidesharecdn.com/caats-140205215914-phpapp01/85/Caa-ts-19-320.jpg)












![Computer Aided Audit Tools and
Controls (CAATTs)
1)
2)
3)
4)
5)
6)
Test data method
Base case system evaluation
Tracing
Integrated Test Facility [ITF]
Parallel simulation
GAS](https://image.slidesharecdn.com/caats-140205215914-phpapp01/85/Caa-ts-32-320.jpg)