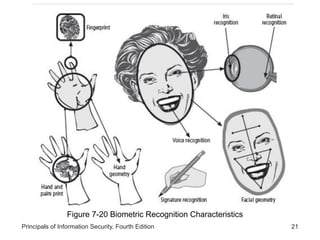
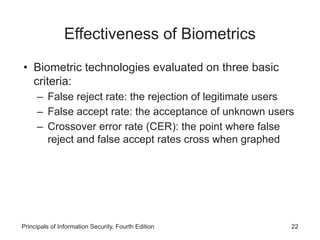
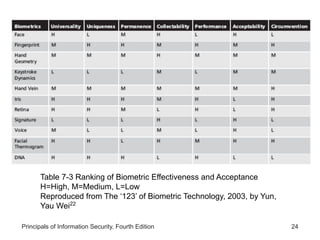
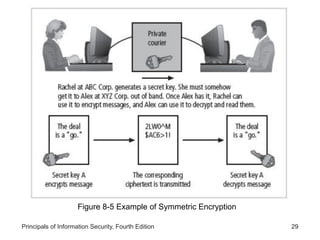
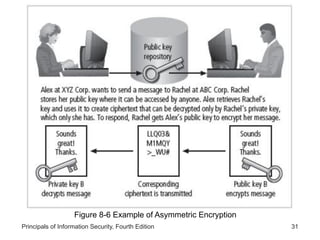
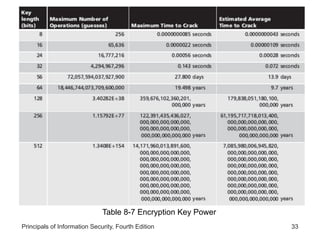
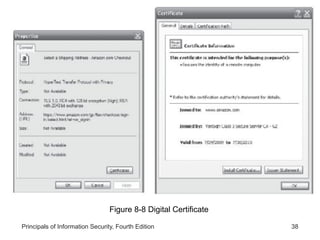
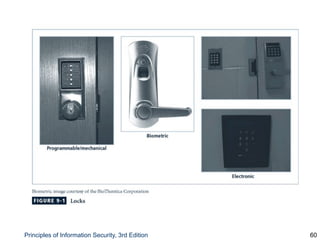
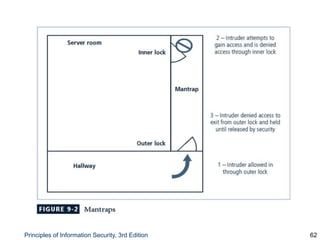
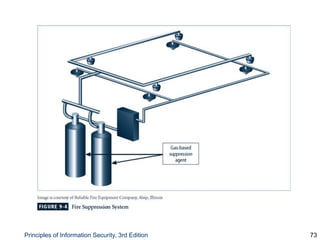
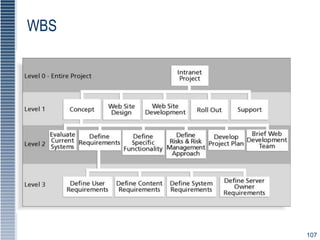
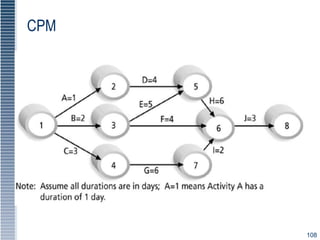
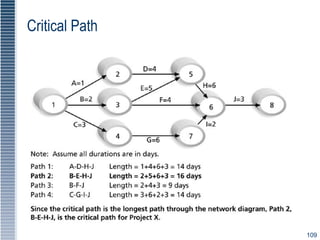
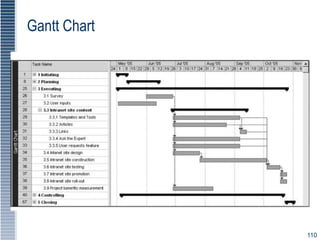
This document provides an overview of security tools and technologies including intrusion detection and prevention systems, honeypots, biometric access control, cryptography, and secure communication protocols. It describes the basic categories and operating principles of intrusion detection and prevention systems. It also discusses honeypots, honeynets, and padded cell systems along with the advantages and disadvantages of these approaches. The document then covers biometric access control methods and issues related to effectiveness and user acceptability. It provides an introduction to cryptography including symmetric and asymmetric encryption algorithms and standards. Finally, it outlines several secure communication protocols and common attacks against cryptosystems such as man-in-the-middle and timing attacks.