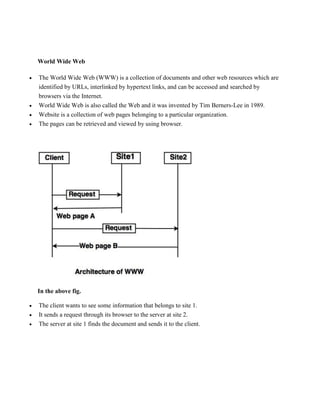
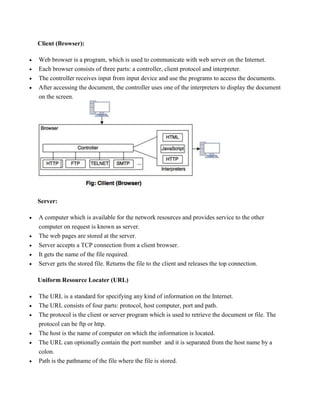
The document discusses several topics related to networking including IP addresses, IP protocols, DNS, remote login, MIME protocol, and the World Wide Web. It provides details on:
- What an IP address is and the different types (IPv4 and IPv6)
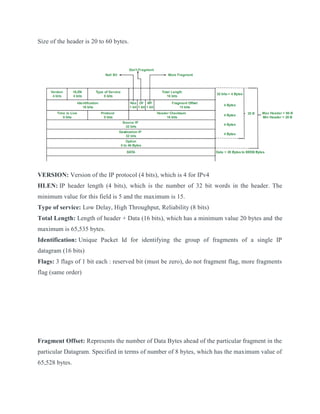
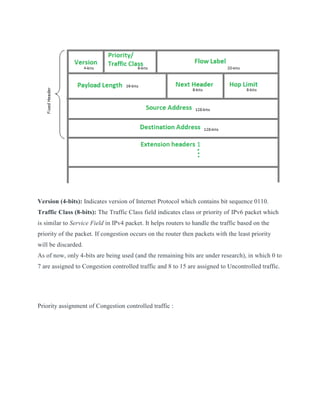
- Components of an IPv4 and IPv6 packet header
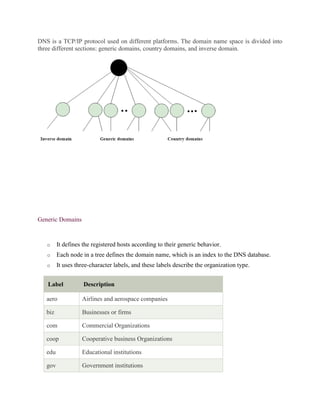
- How DNS works to translate domain names to IP addresses
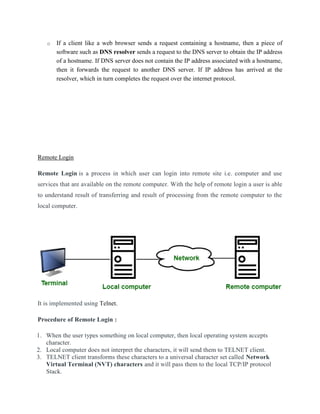
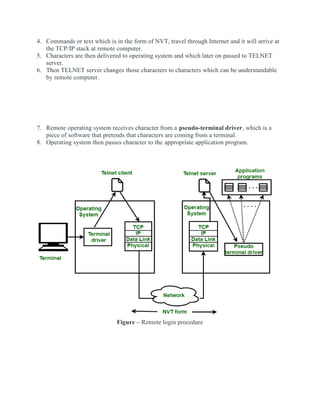
- The process of remote login using Telnet
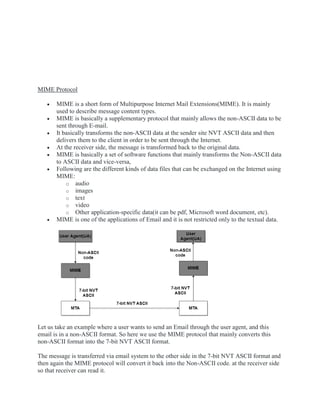
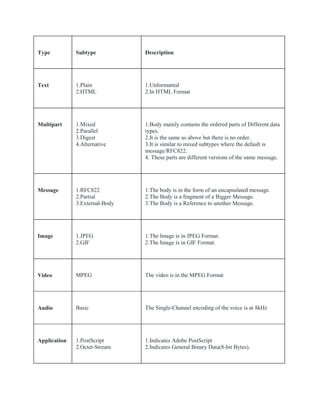
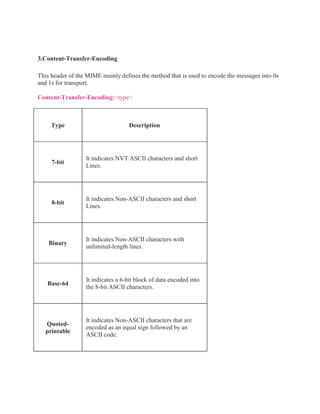
- How MIME allows non-ASCII data to be sent via email by encoding and decoding it
- Key components of the World Wide Web including browsers, servers, and URLs