Embed presentation
Download to read offline


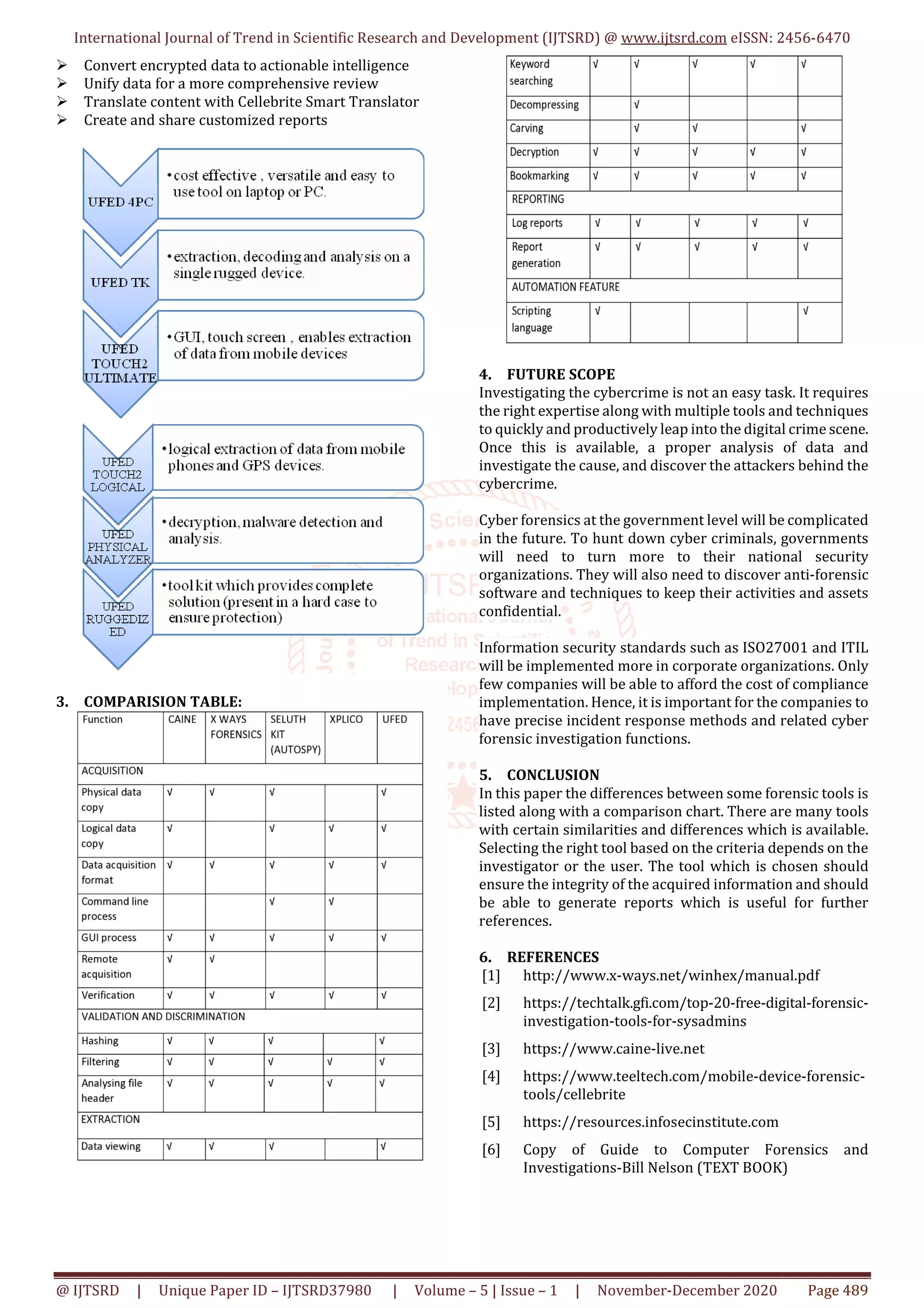
The document presents a comparative analysis of various digital forensic extraction tools used in investigations to collect and examine digital evidence. It details the methodologies of computer forensic analysis, various tools available, their features, and a comparison chart for selection based on investigation needs. Additionally, it discusses future challenges in cyber forensics and the importance of choosing the right tools to ensure data integrity and effective reporting.


