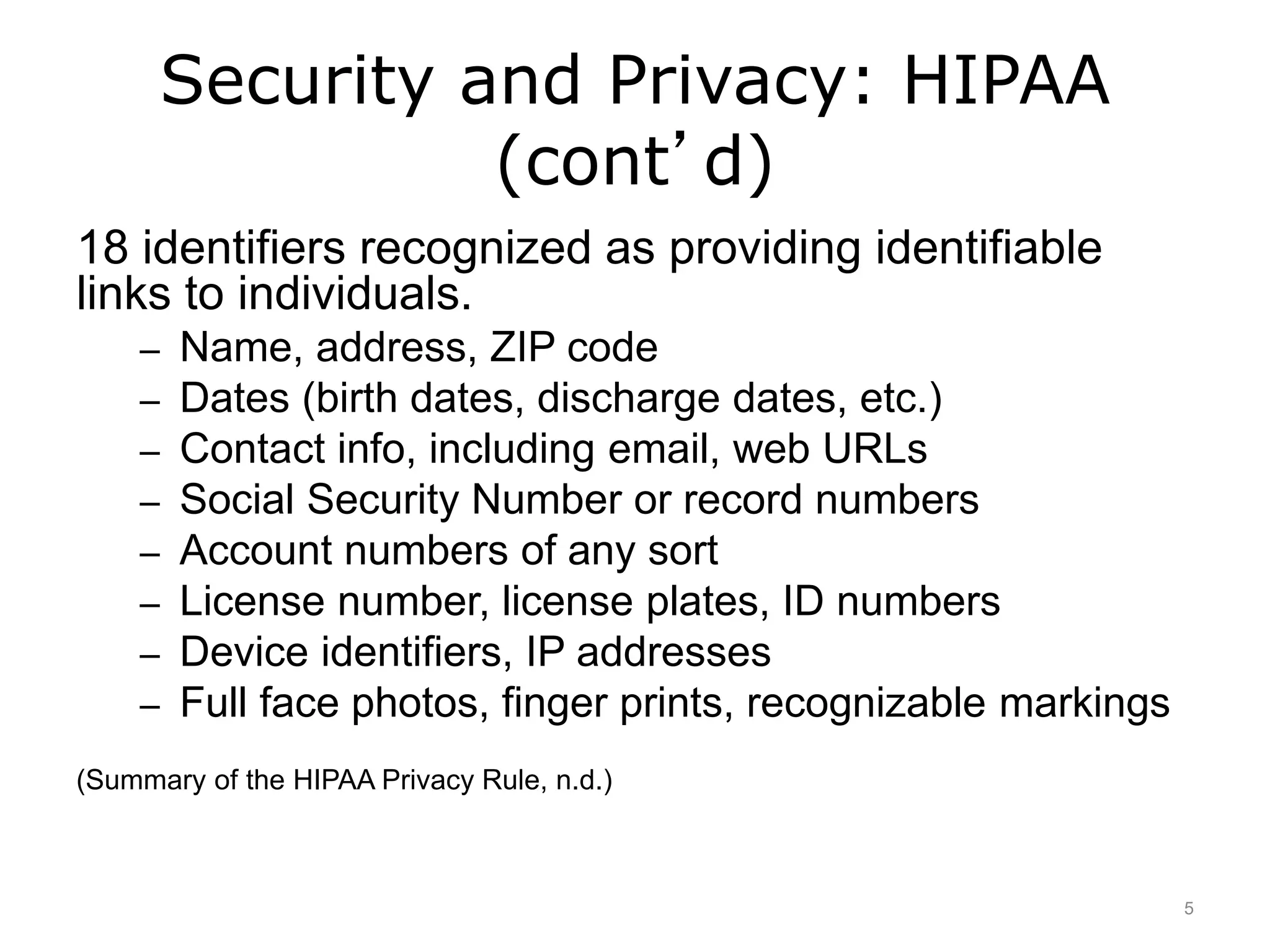
This lecture discusses system security procedures and standards for health IT systems, as required by HIPAA. It covers protected health information (PHI) and the administrative, physical, and technical safeguards required to protect ePHI, including access policies, training, and device security. PHI must be strictly regulated and protected using a layered approach with numerous safeguards. Training is also needed to ensure user awareness of security policies and procedures.