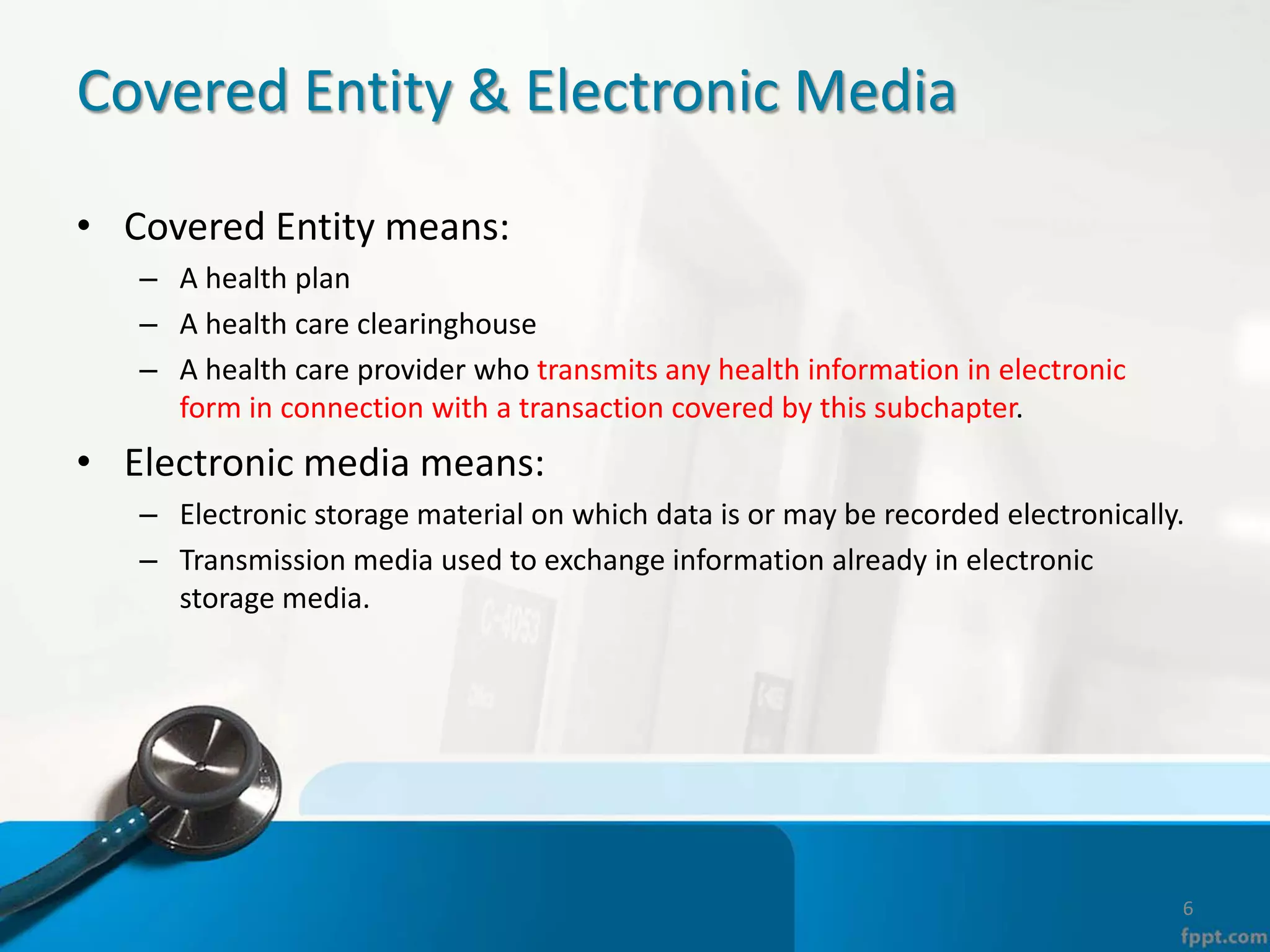
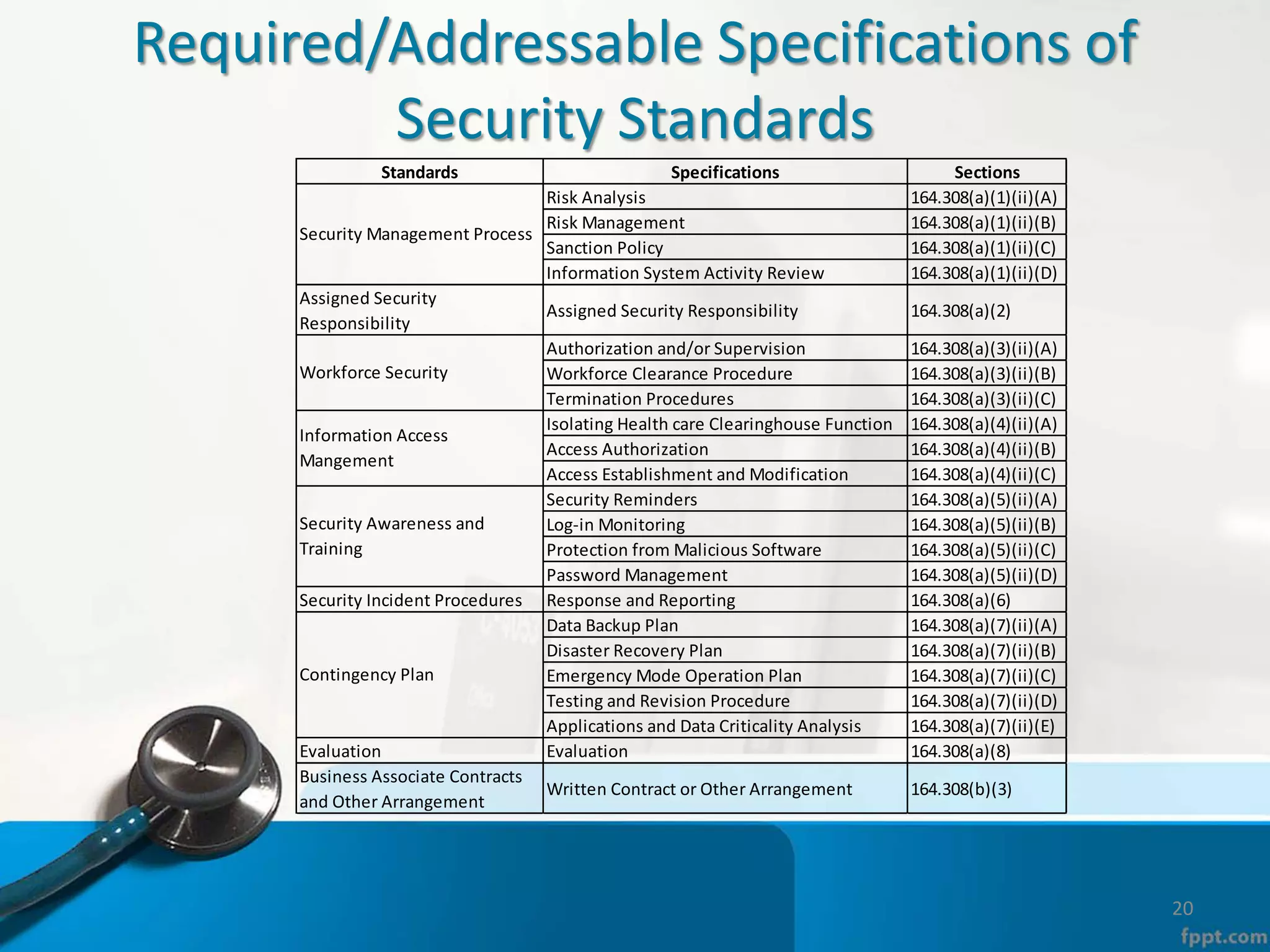
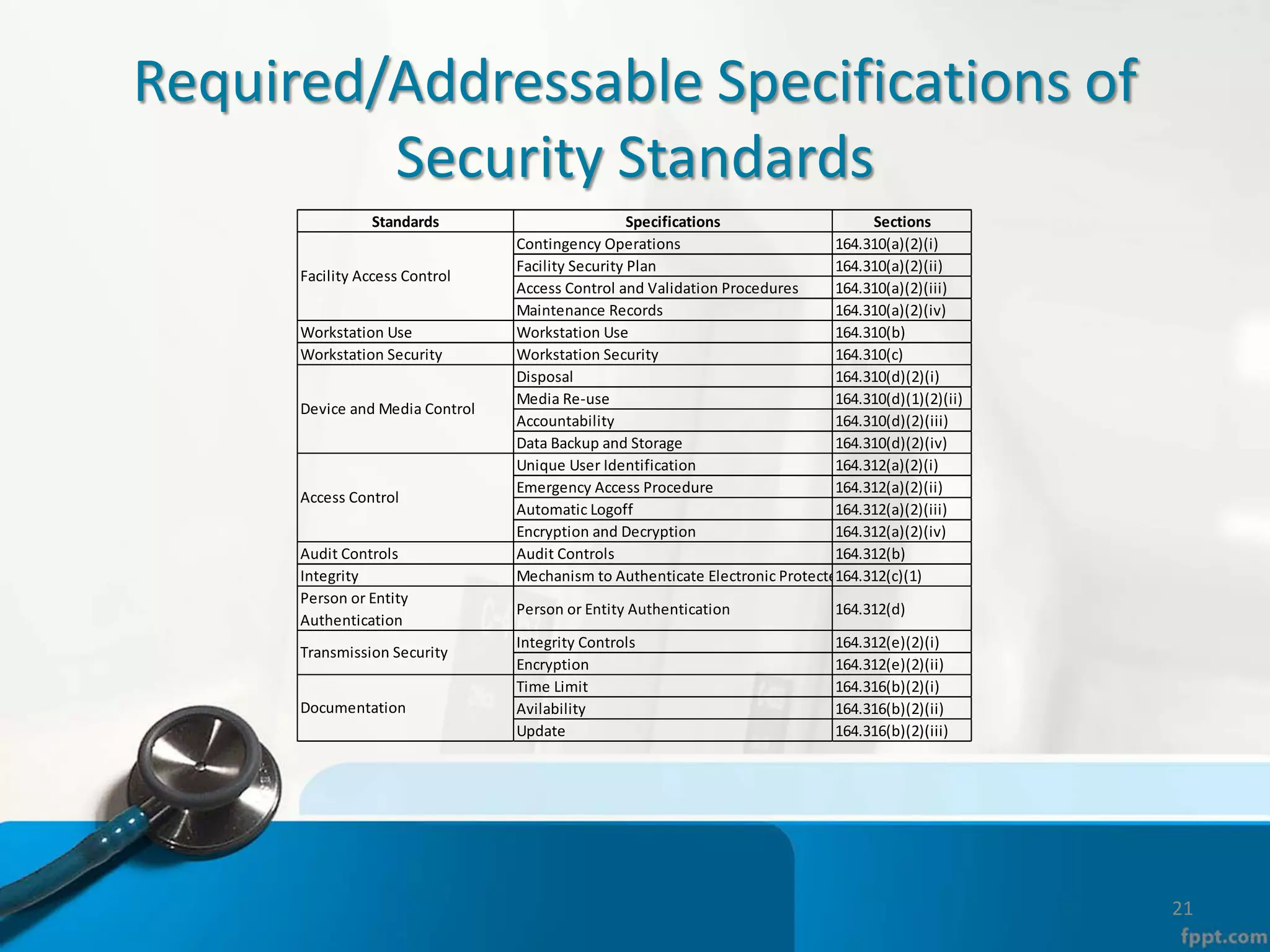
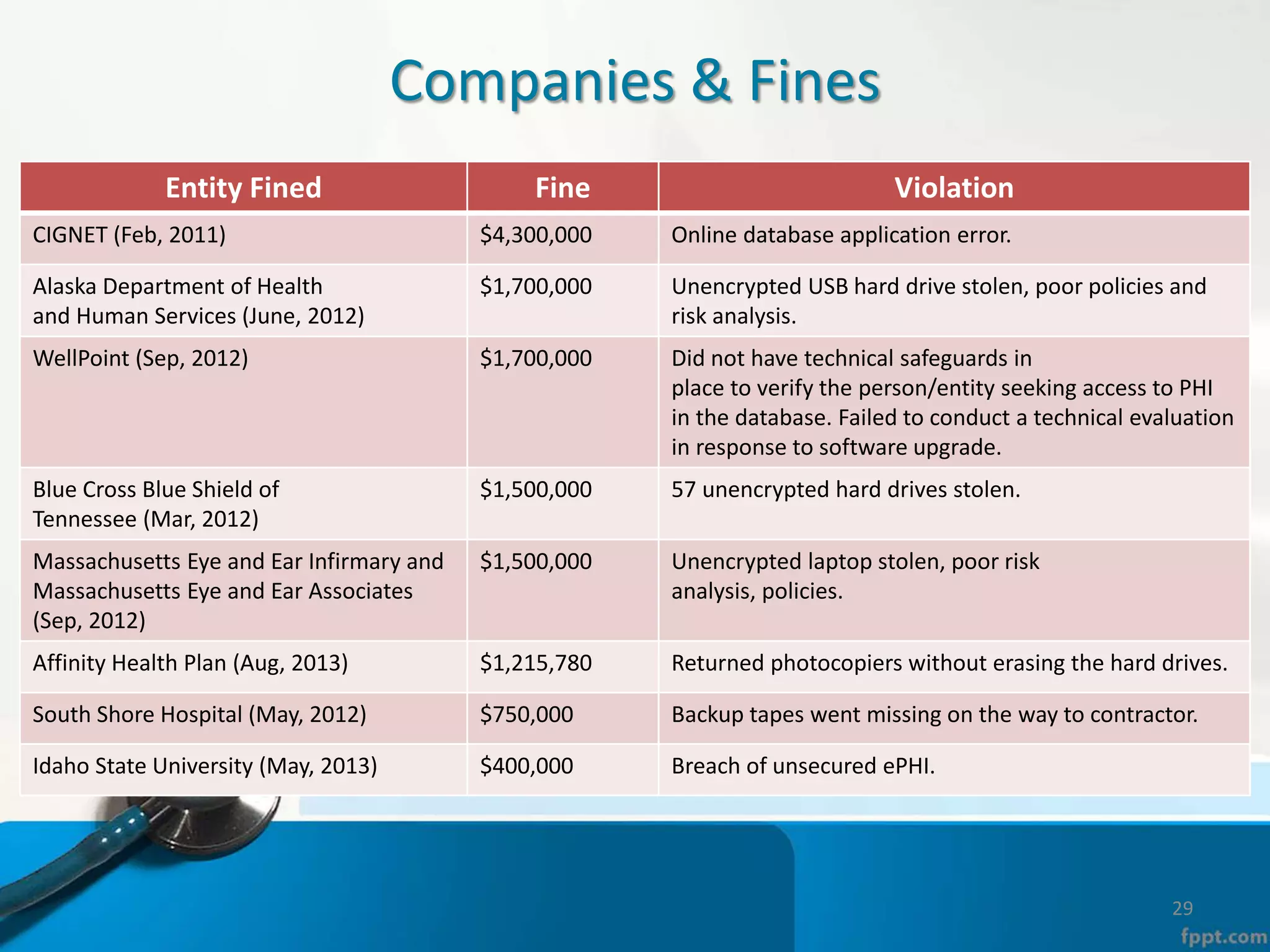
The document provides an overview of the Health Insurance Portability and Accountability Act (HIPAA) Privacy and Security Rules. It defines key terms like protected health information (PHI), covered entities, and business associates. It describes HIPAA regulations around the privacy of PHI, including the minimum necessary rule, authorizations required for disclosure, and the notice of privacy practices. It also outlines HIPAA security rules, including administrative, physical, and technical safeguards covered entities must implement to secure electronic PHI (ePHI). Breaches of PHI are also discussed, along with examples of companies that have faced fines for HIPAA violations.