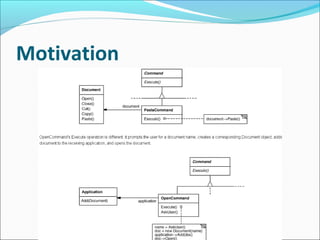
The Command pattern encapsulates requests as objects, allowing clients to parameterize other objects with different requests, queue or log requests, and support undoable operations. It decouples the object that invokes the operation from the one that knows how to perform it. ConcreteCommand classes define a binding between a receiver object and an action, implementing Execute to invoke operations on the receiver. The pattern makes it easy to add new commands without changing existing classes.