The document provides an overview of cryptographic algorithms, specifically focusing on DES (Data Encryption Standard) for symmetric key cryptography and RSA (Rivest-Shamir-Adleman) for asymmetric key cryptography. It discusses the necessity of secure communication in light of increasing cyber crime in India, explores various cryptographic techniques, and outlines the strengths and weaknesses of each cryptography type. The document concludes with real-life applications and the importance of cryptography in ensuring secure data transactions.


![Needs for Security in India
• Computer Applications has been
developed to handle financial and
personal data.
• India has bypassed Japan to become
the world’s third largest Internet user
after China and the United States.
• This encourages a group of people to
indulge in cyber crime activities.
• India ranked 11th in the cyber crime
activities in the world [1].
Alice (Sender)
Bob (Receiver)
Medium
Eve
(Unauthorized
Person)](https://image.slidesharecdn.com/cryptographicalgorithmsss-150427111019-conversion-gate02/85/Cryptographic-Algorithms-DES-and-RSA-3-320.jpg)
![Needs for Security in India
Figure: Number of cyber crime complaints registered in India [2]](https://image.slidesharecdn.com/cryptographicalgorithmsss-150427111019-conversion-gate02/85/Cryptographic-Algorithms-DES-and-RSA-4-320.jpg)

![Basic Terms
• Plain Text: Message before encryption.
• Cipher Text: Message after encryption.
• Cipher: Encryption algorithm
• Encryption: the process of converting Plain text to Ciphertext
• Decryption: the process of converting ciphertext back to the original plaintext.
• Key: Sequence that controls the operation and behavior of the cryptographic
algorithm.
Figure: General working principle of Cryptography [3]](https://image.slidesharecdn.com/cryptographicalgorithmsss-150427111019-conversion-gate02/85/Cryptographic-Algorithms-DES-and-RSA-7-320.jpg)


![Types of Cryptography
1. Symmetric Key Cryptography:
• Symmetric key cryptography involves the usage of the same key for encryption
encryption and decryption [4].
• Both sender and receiver must know the common key.
• The common key need to be exchanged before hand by some other secure
secure method.
Figure: Working principle of Symmetric Key Cryptography [5]](https://image.slidesharecdn.com/cryptographicalgorithmsss-150427111019-conversion-gate02/85/Cryptographic-Algorithms-DES-and-RSA-10-320.jpg)

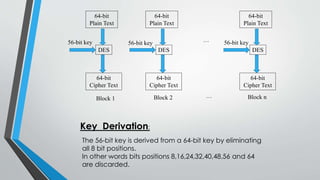
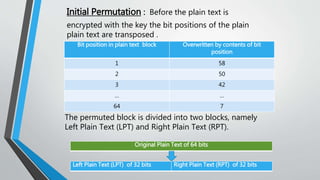
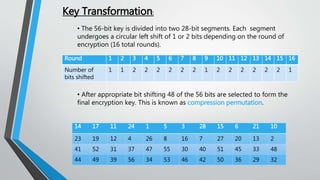
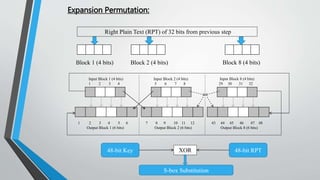
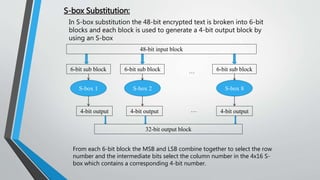
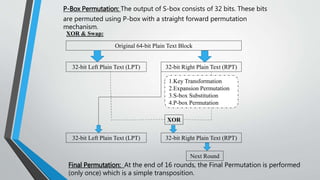


![Types of Cryptography (Contd…)
2. Asymmetric Key Cryptography:
• Two different keys are used to encrypt and decrypt the message.
• Receiver generates a public and private key pair.
• Receiver broadcasts the public key.
• Encryption is done by public key and private key is used for decryption.
Figure: Working principle of Asymmetric Key Cryptography [6]](https://image.slidesharecdn.com/cryptographicalgorithmsss-150427111019-conversion-gate02/85/Cryptographic-Algorithms-DES-and-RSA-20-320.jpg)



![EXAMPLE OF RSA ALGORITHM
C
BOB wants to send a message
(M) to ALICE.
*Public Key KU{ e , N} is available
to
sender(BOB)
*Encrypting M, to create the cipher
text(C).
*Sending C to receiver ALICE
*Decrypting Cipher text (C):
Figure: Explanation Of RSA
[7]](https://image.slidesharecdn.com/cryptographicalgorithmsss-150427111019-conversion-gate02/85/Cryptographic-Algorithms-DES-and-RSA-24-320.jpg)
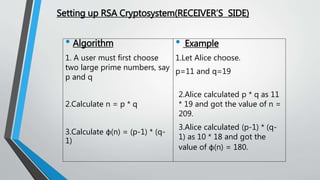
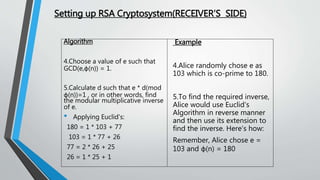

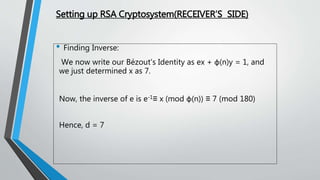
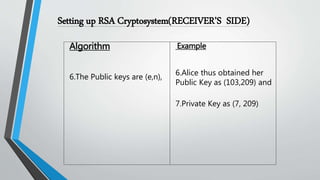
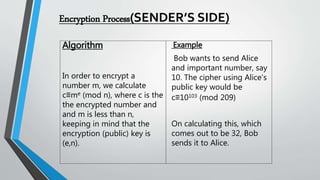



![Real Life Application Of Cryptography[8]
• Authentication and Digital Signatures
• Time stamping
• Electronic Cash transaction
• Disk encryption](https://image.slidesharecdn.com/cryptographicalgorithmsss-150427111019-conversion-gate02/85/Cryptographic-Algorithms-DES-and-RSA-34-320.jpg)

![References
• [1]: http://www.dnaindia.com/india/report-indore-industries-lose-rs-18k-
cryr-to-cyber-crimes-1930610
• [2]: http://www.medianama.com
• [3]: http://www.slideshare.net/priyavinkal/cryptography-10858819(slide
number: 7)
• [4]: Cryptography and Network Security By Atul Kahate (ISBN: 0-07-
049483-5)
• [5]: http://www.slideshare.net/priyavinkal/cryptography-108588(slide
number: 11)
• [6]: http://www.slideshare.net/priyavinkal/cryptography-108588(slide
number: 14)
• [7]: www.youtube.com
• [8]: www.laits.utexas.edu/../life.html](https://image.slidesharecdn.com/cryptographicalgorithmsss-150427111019-conversion-gate02/85/Cryptographic-Algorithms-DES-and-RSA-36-320.jpg)
