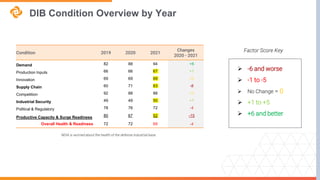
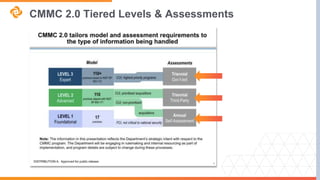
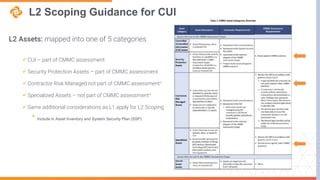
The document explains CMMC 2.0 and its implications for small and midsize businesses, focusing on compliance requirements and the assessment process. It highlights the health of the defense industrial base and the challenges it faces, including supply chain issues and declines in innovation. Additionally, the document outlines the structure of CMMC 2.0, including levels of assessment for Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).