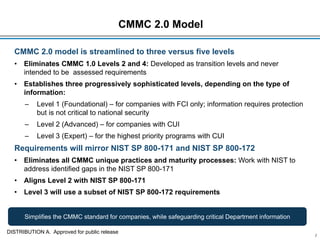
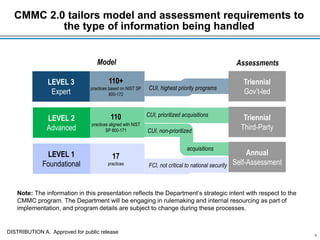
The document outlines the Cybersecurity Maturity Model Certification (CMMC) Version 2.0. It summarizes that CMMC 2.0 streamlines the model to three levels instead of five, aligns the levels with NIST standards, and tailors assessment requirements based on the type of controlled information handled. It also allows limited use of plans of action and milestones and waivers. The changes will be implemented through a rulemaking process that includes public comment and congressional review.