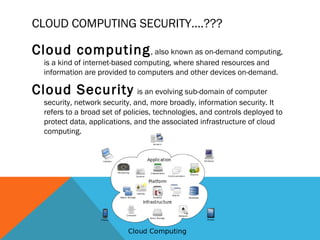
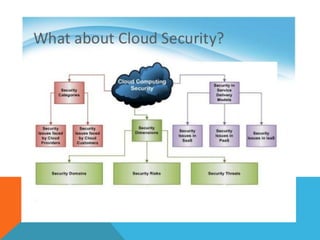
Cloud computing allows for shared resources and data to be provided over the internet. Cloud security aims to protect this data and infrastructure through policies, technologies, and controls. There are security concerns both for cloud providers in maintaining infrastructure integrity and user data safety, and for users in ensuring strong authentication. Nine notable security threats are identified: data breaches, data loss, account hijacking, insecure interfaces, denial of service attacks, malicious insiders, abuse of cloud services, insufficient due diligence, and shared technology vulnerabilities. The document outlines preventative measures for each threat and discusses related privacy and data protection laws in India.