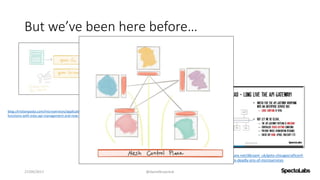
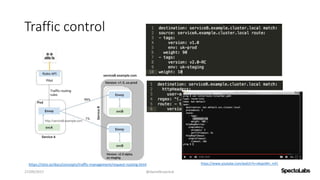
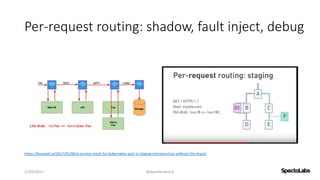
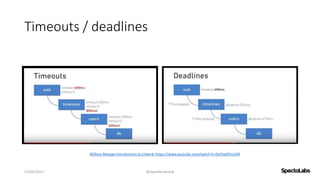
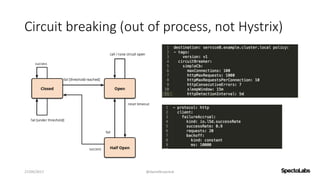
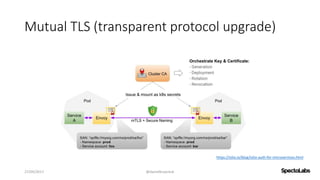
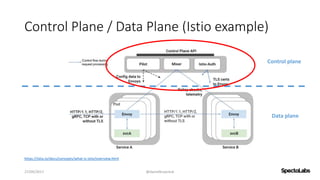
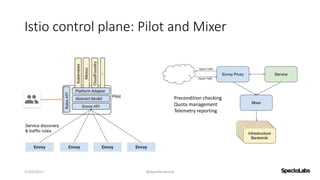
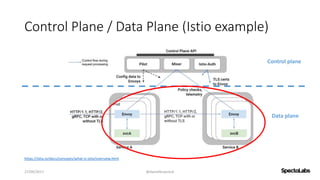
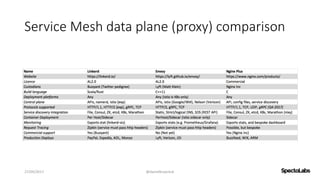
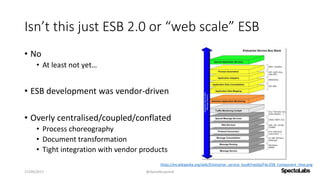
A service mesh is a dedicated infrastructure layer that facilitates secure, fast, and reliable service-to-service communication in cloud-native applications. It consists of a control plane for managing the services and a data plane with service proxies, helping to navigate the complexities of microservices architecture. Service meshes enhance security, observability, and control over communication, making them essential for deploying cloud-native systems effectively.