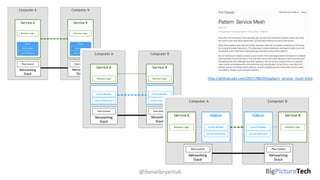
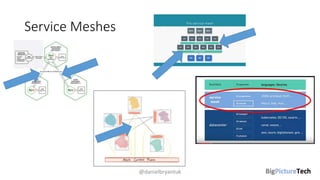
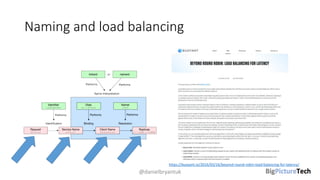
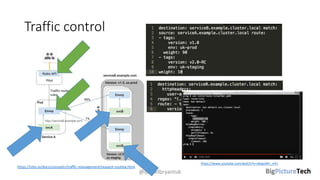
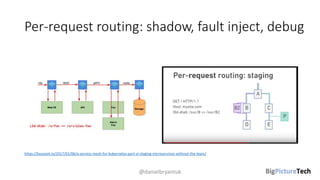
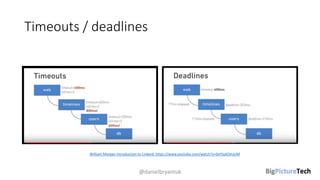
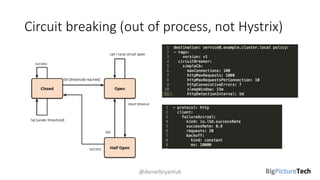
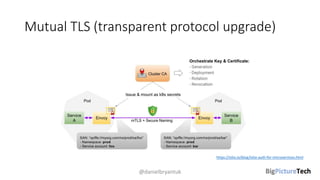
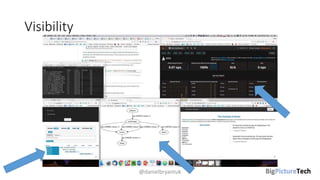
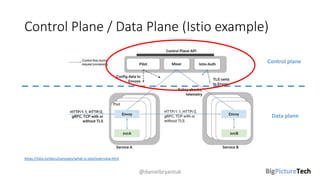
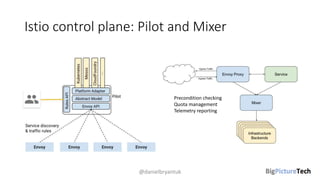
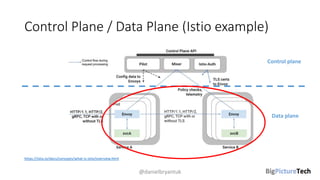
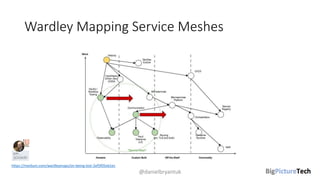
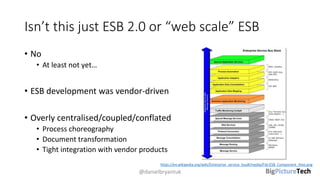
A service mesh is an infrastructure layer designed to facilitate safe, reliable, and observable communication between microservices in cloud-native applications. It provides features like traffic shaping, load balancing, security, and observability, which are crucial as organizations transition from monolithic architectures to complex microservices. However, caution is advised as this technology is emerging and can introduce complexities that must be understood and managed effectively.