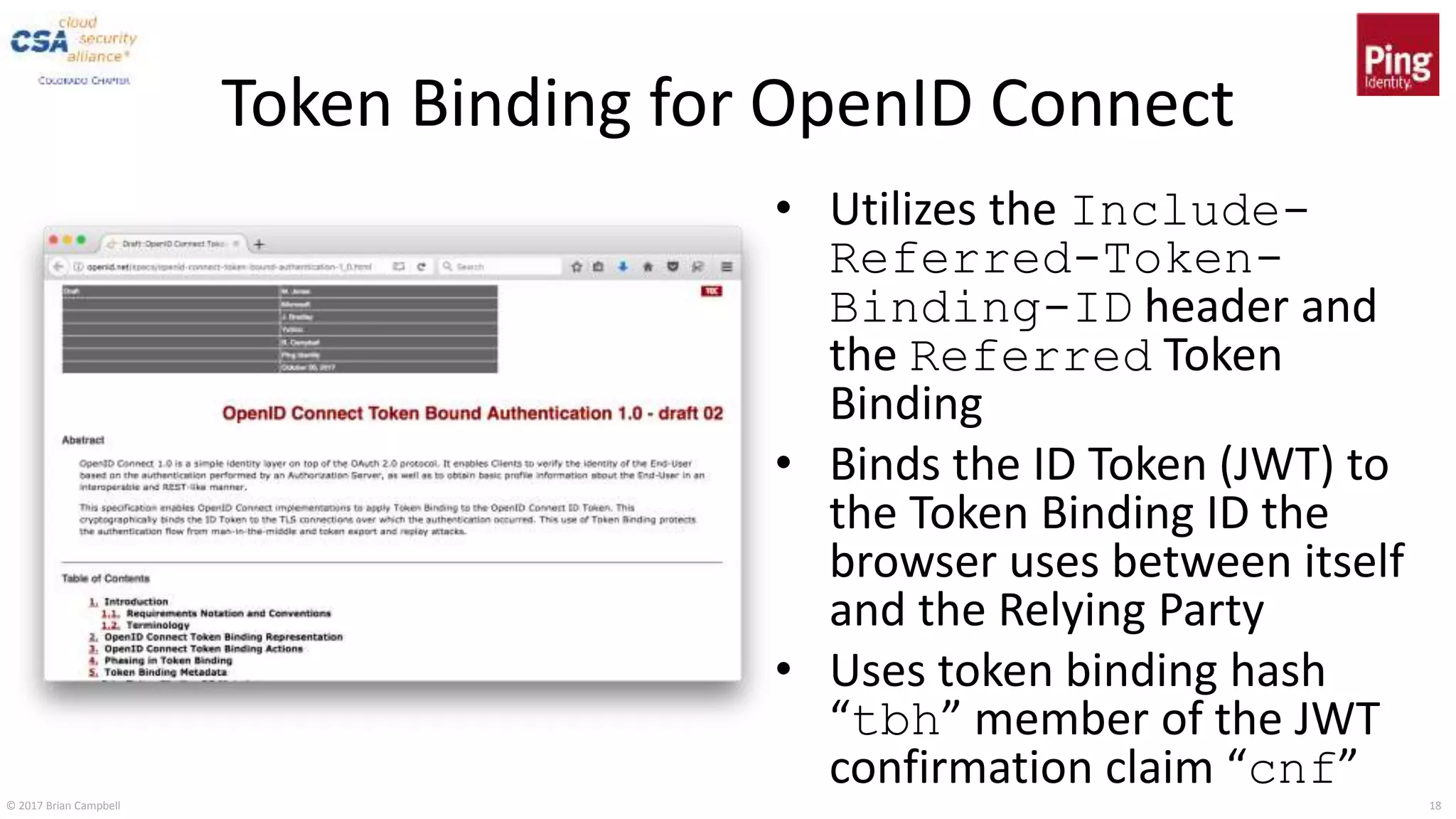
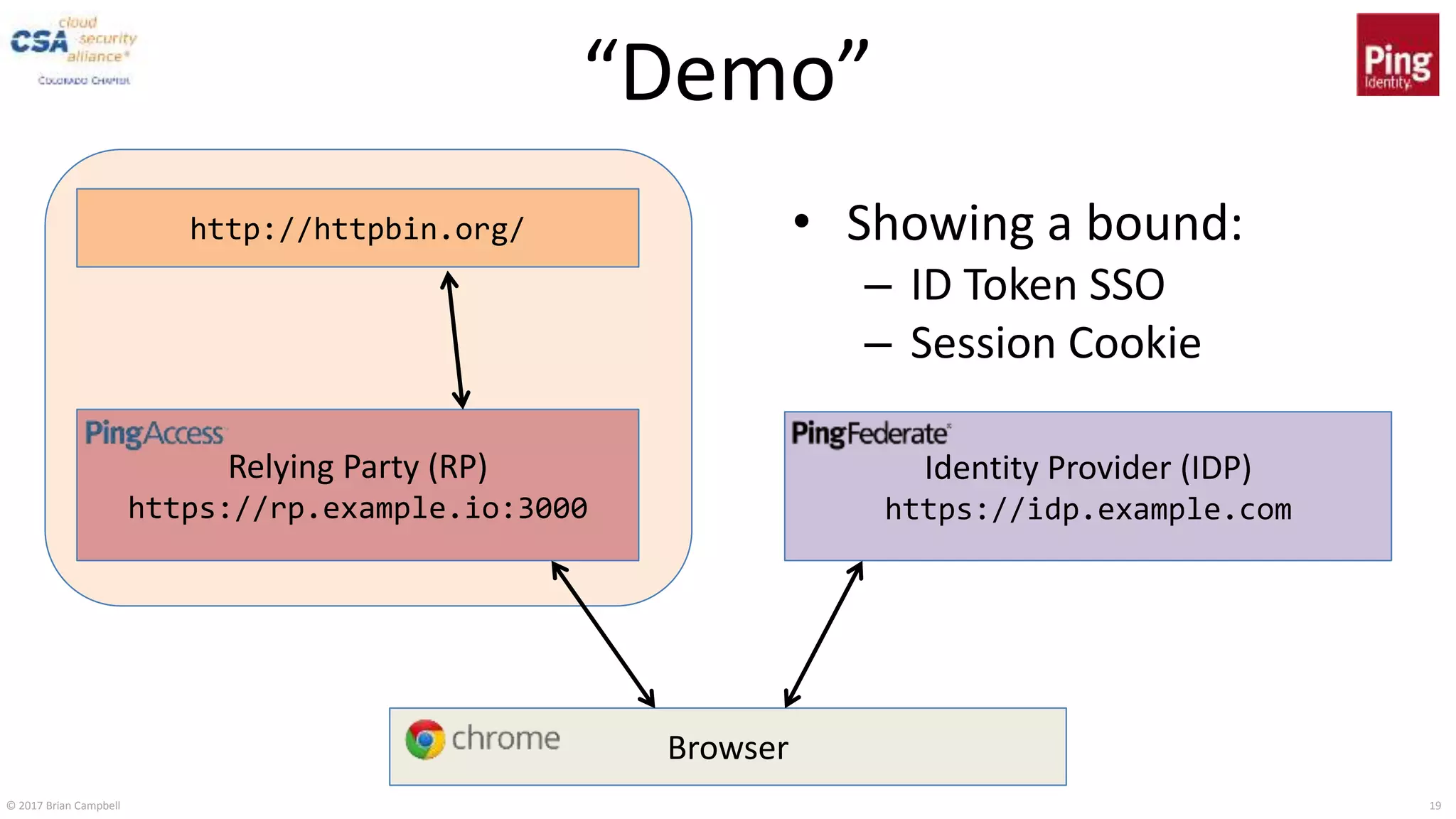
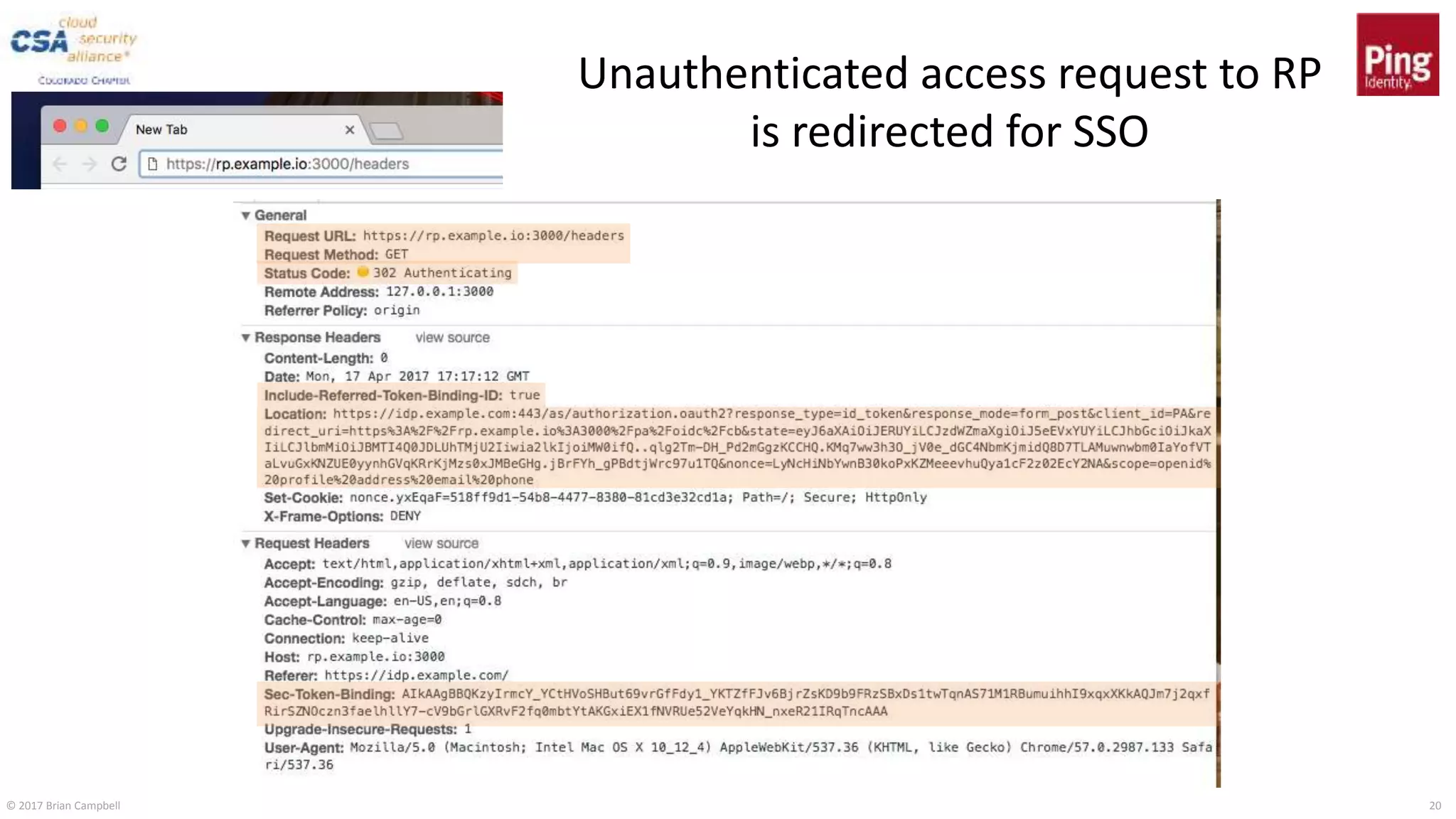
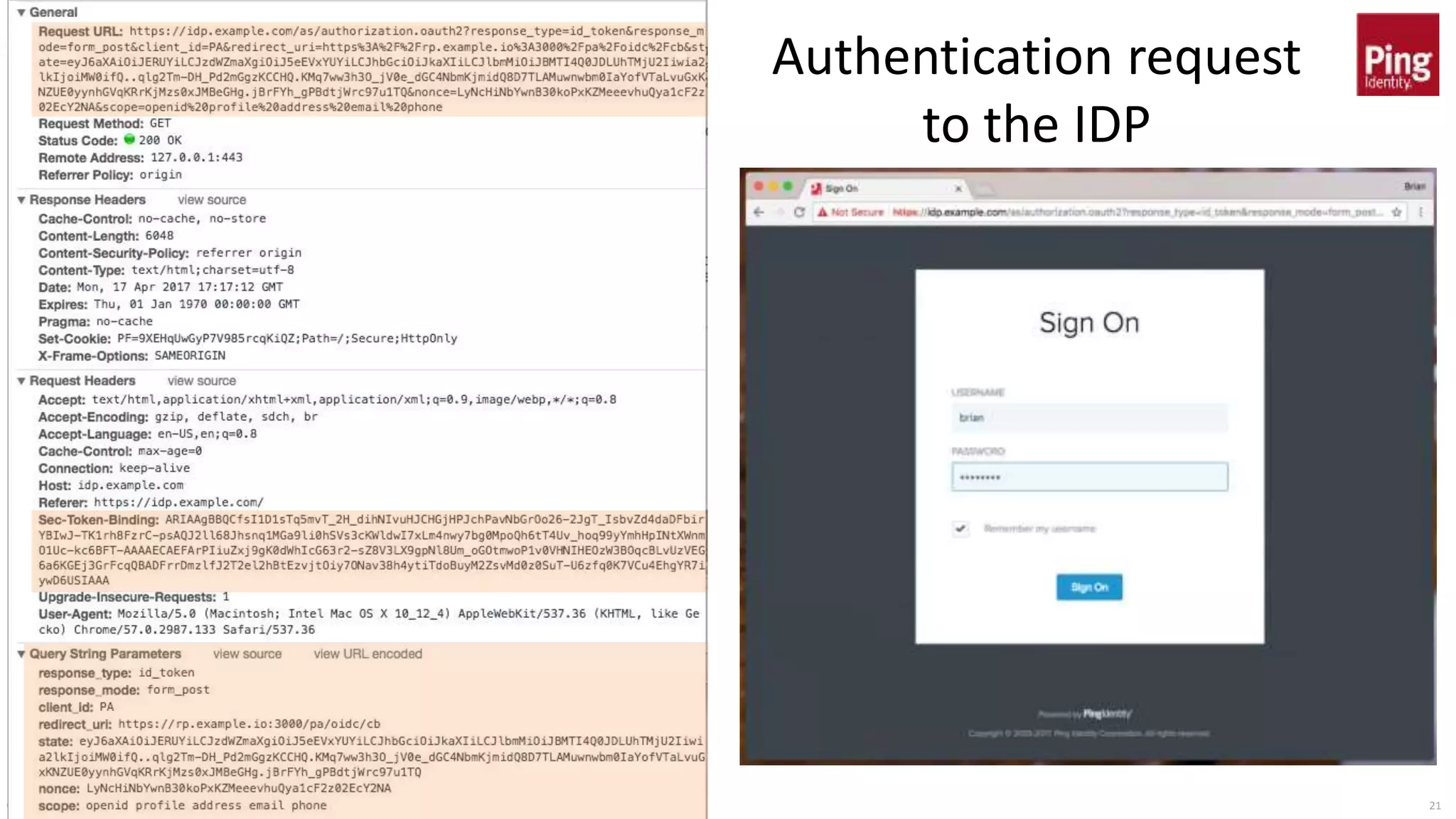
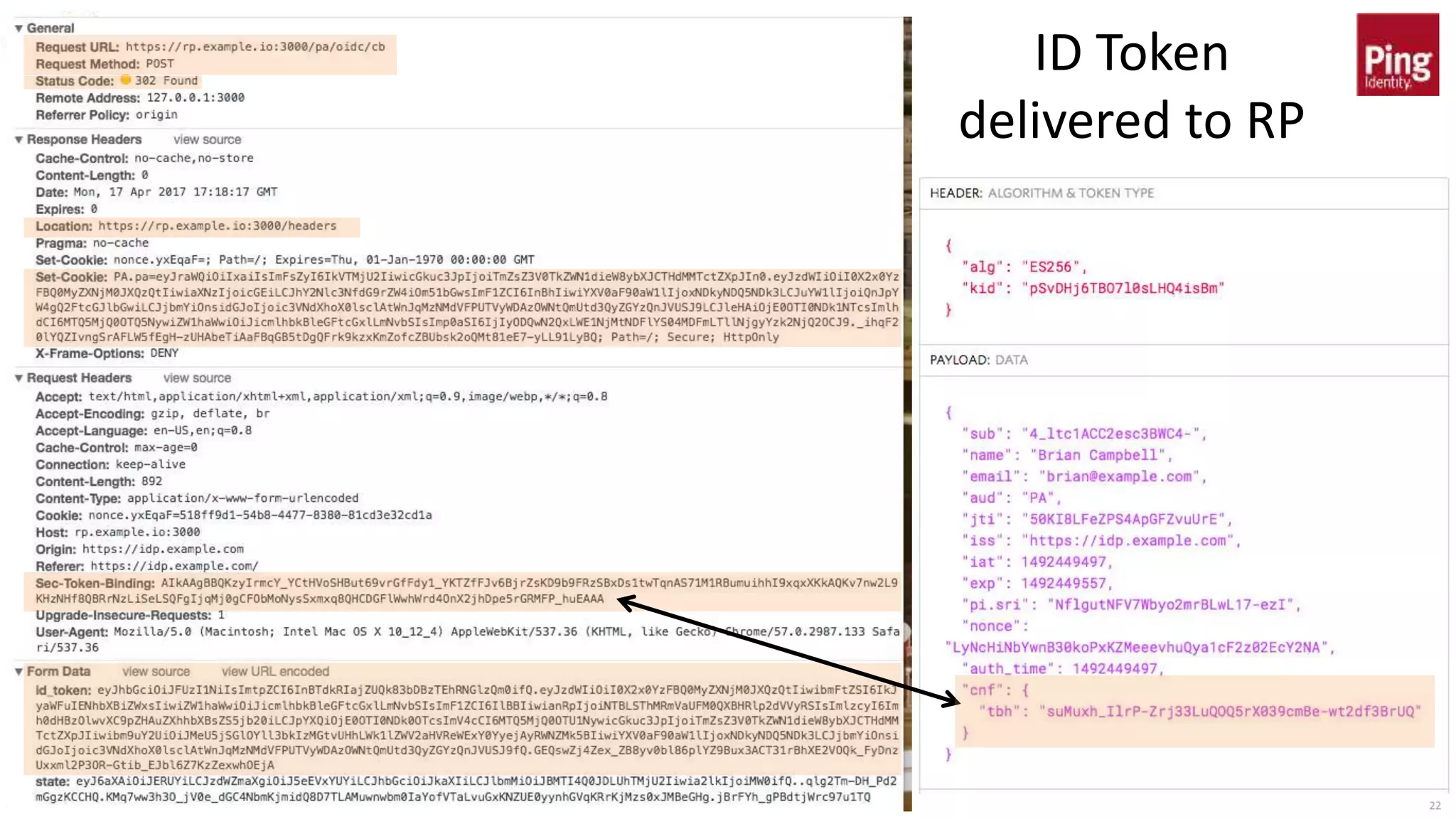
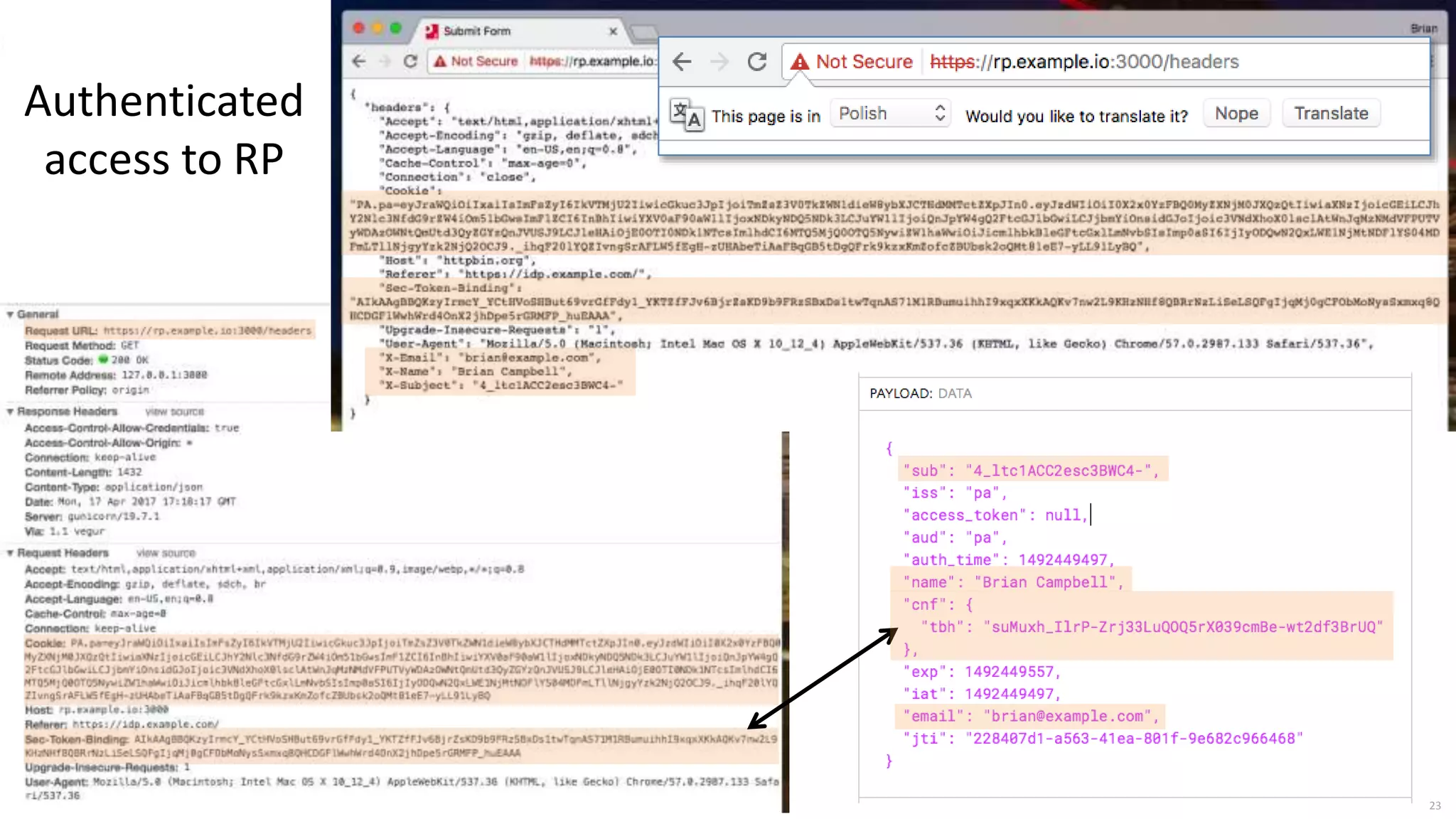
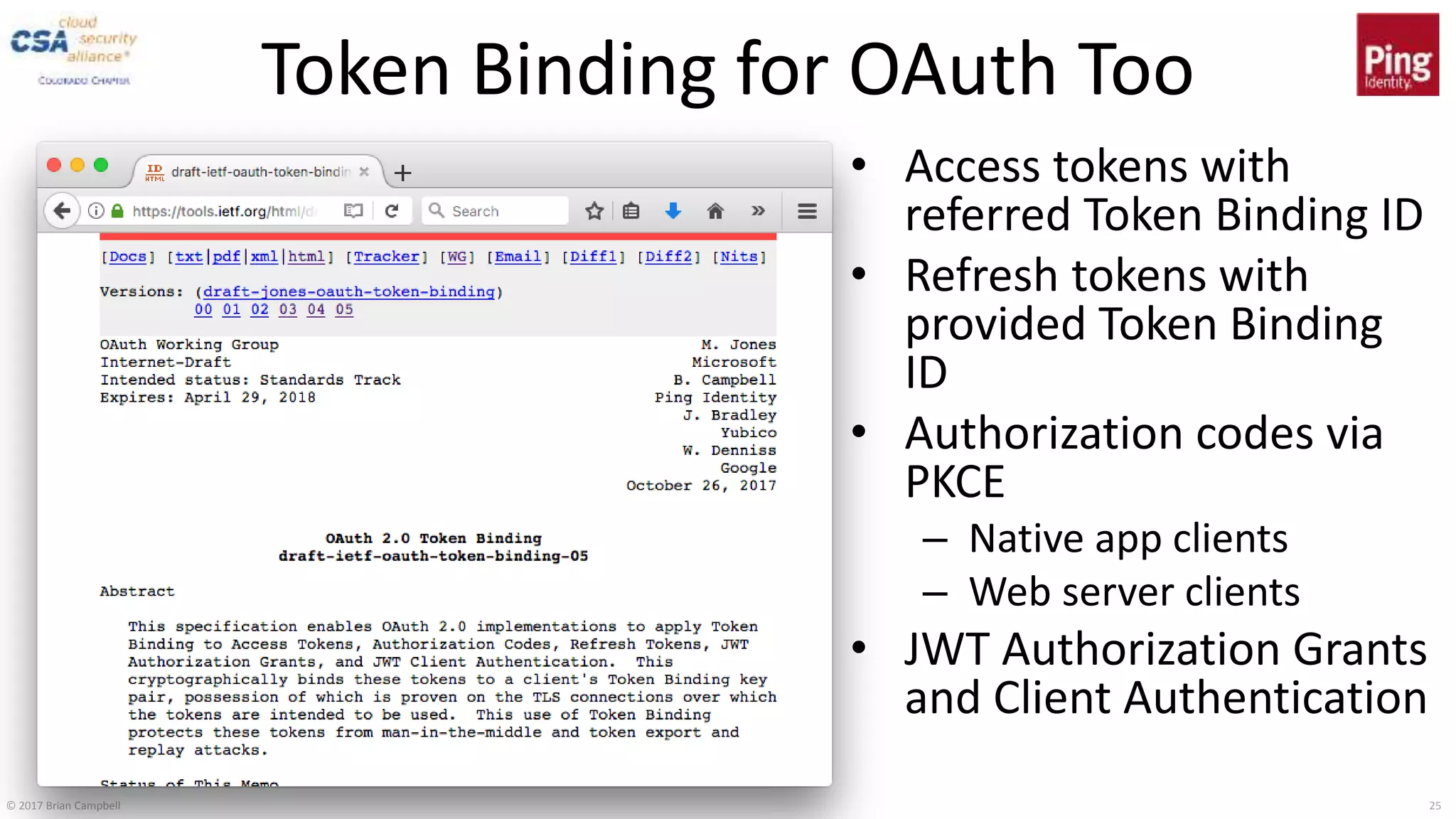
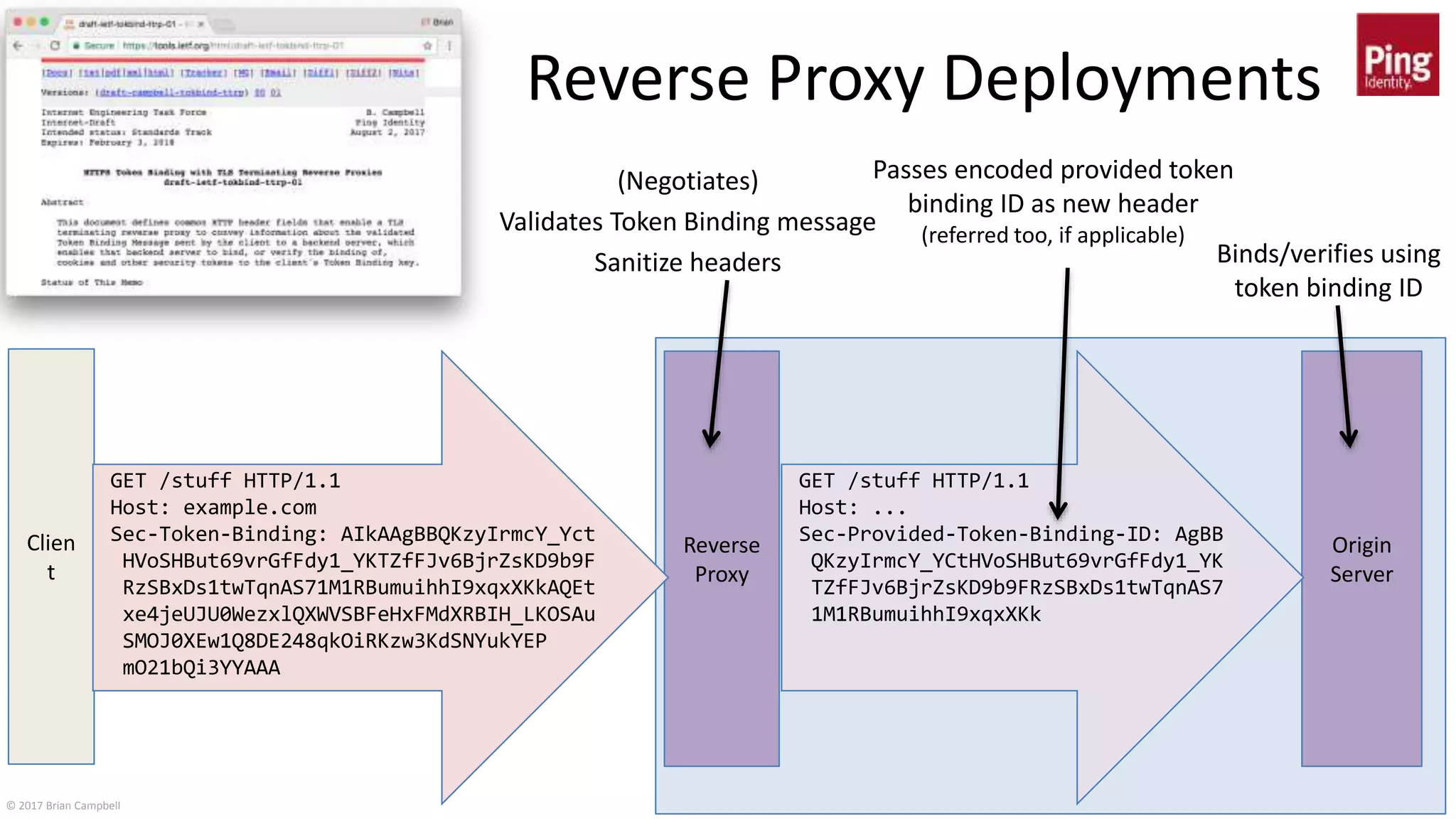
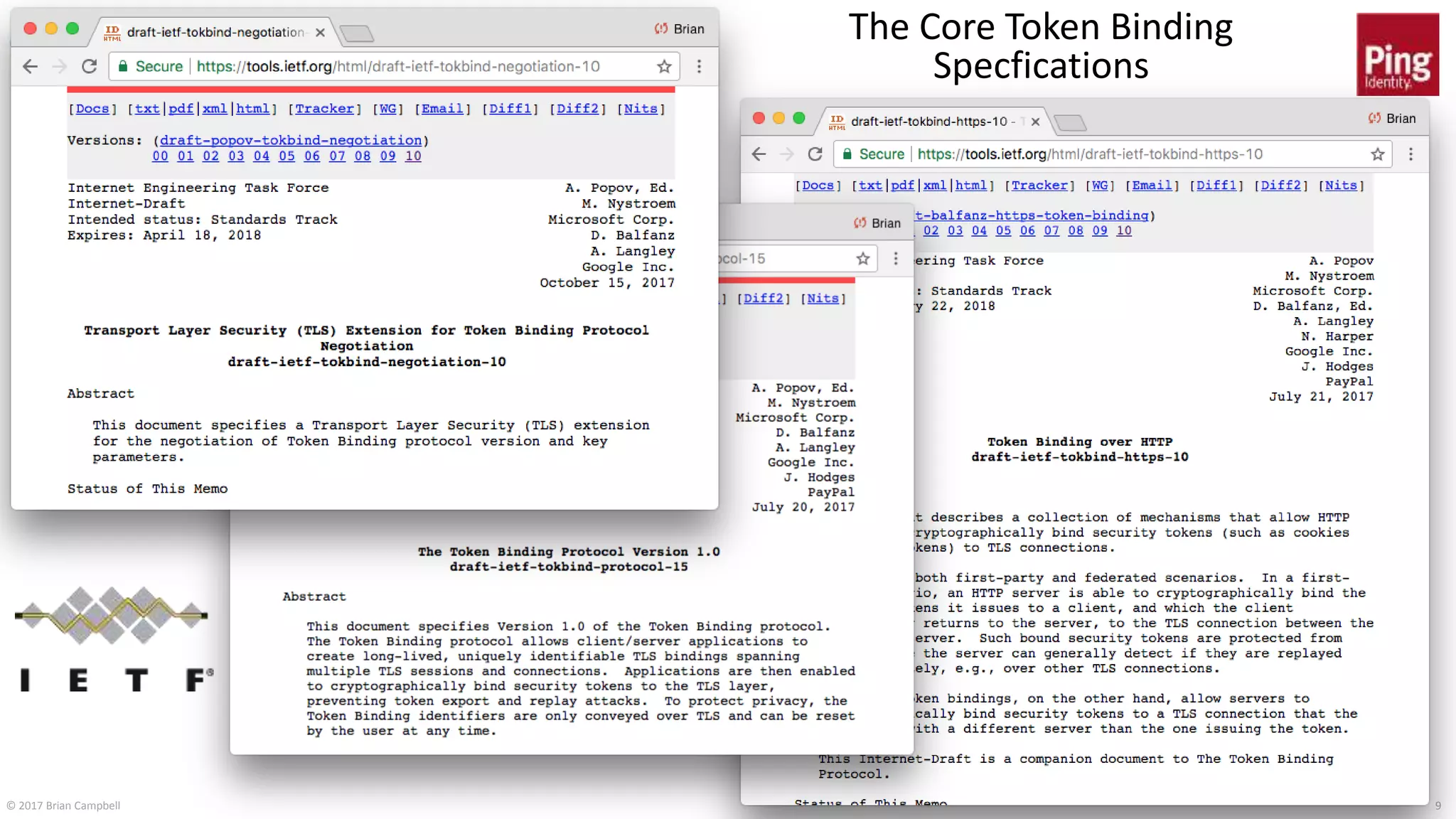
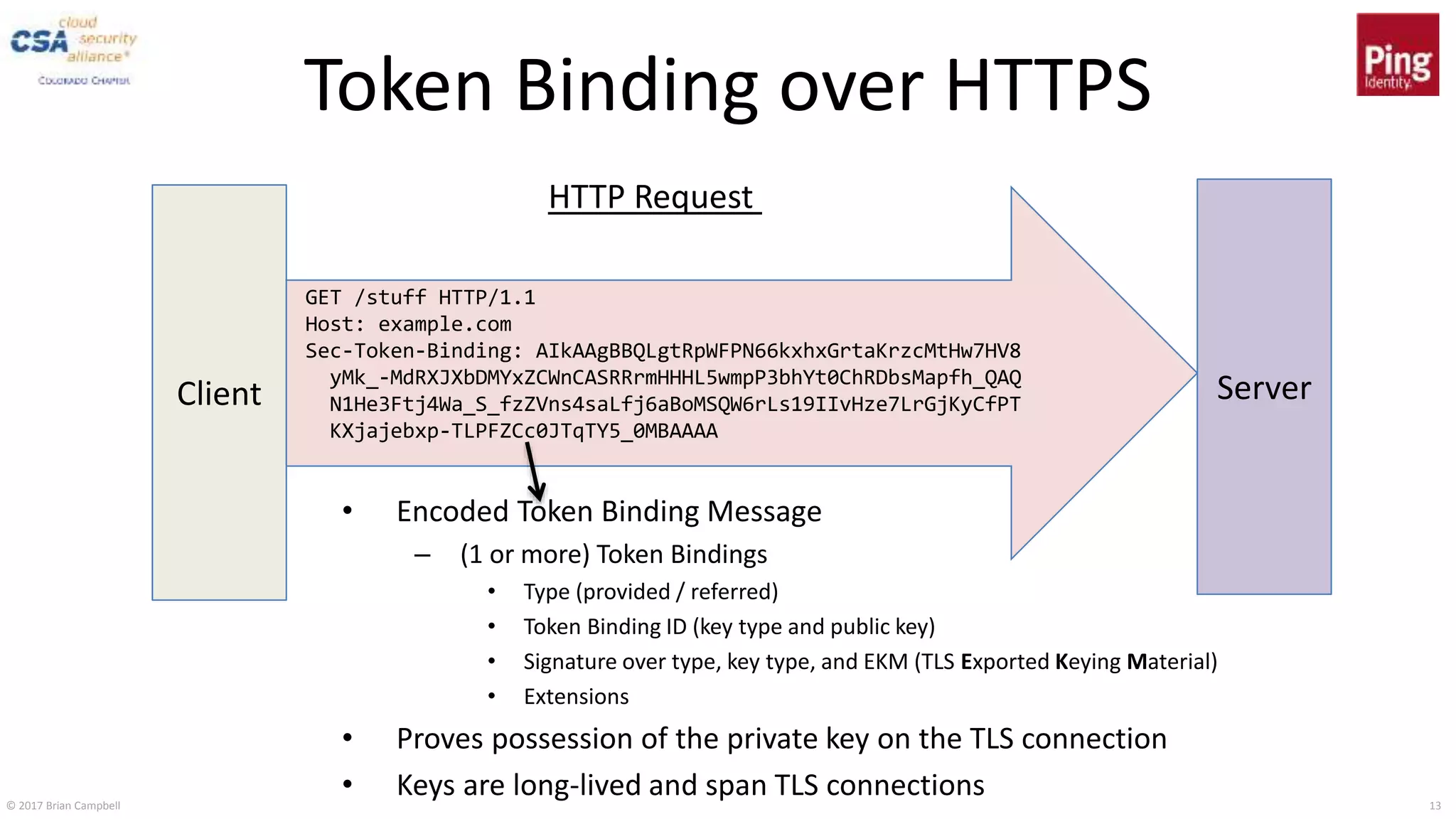
This document discusses token binding as a way to more securely bind security tokens like cookies to client devices. It summarizes the core token binding specifications from the IETF, how token binding can be applied to single sign-on with OpenID Connect and OAuth, and the current landscape of implementations. Token binding allows binding of tokens to a client-generated public-private key pair to prove possession of the private key over TLS. This can help mitigate risks from cross-site scripting and other attacks. Specifications are being developed for token binding in areas like OpenID Connect and OAuth, and implementations exist in browsers, servers, and libraries.








![© 2017 Brian Campbell 12
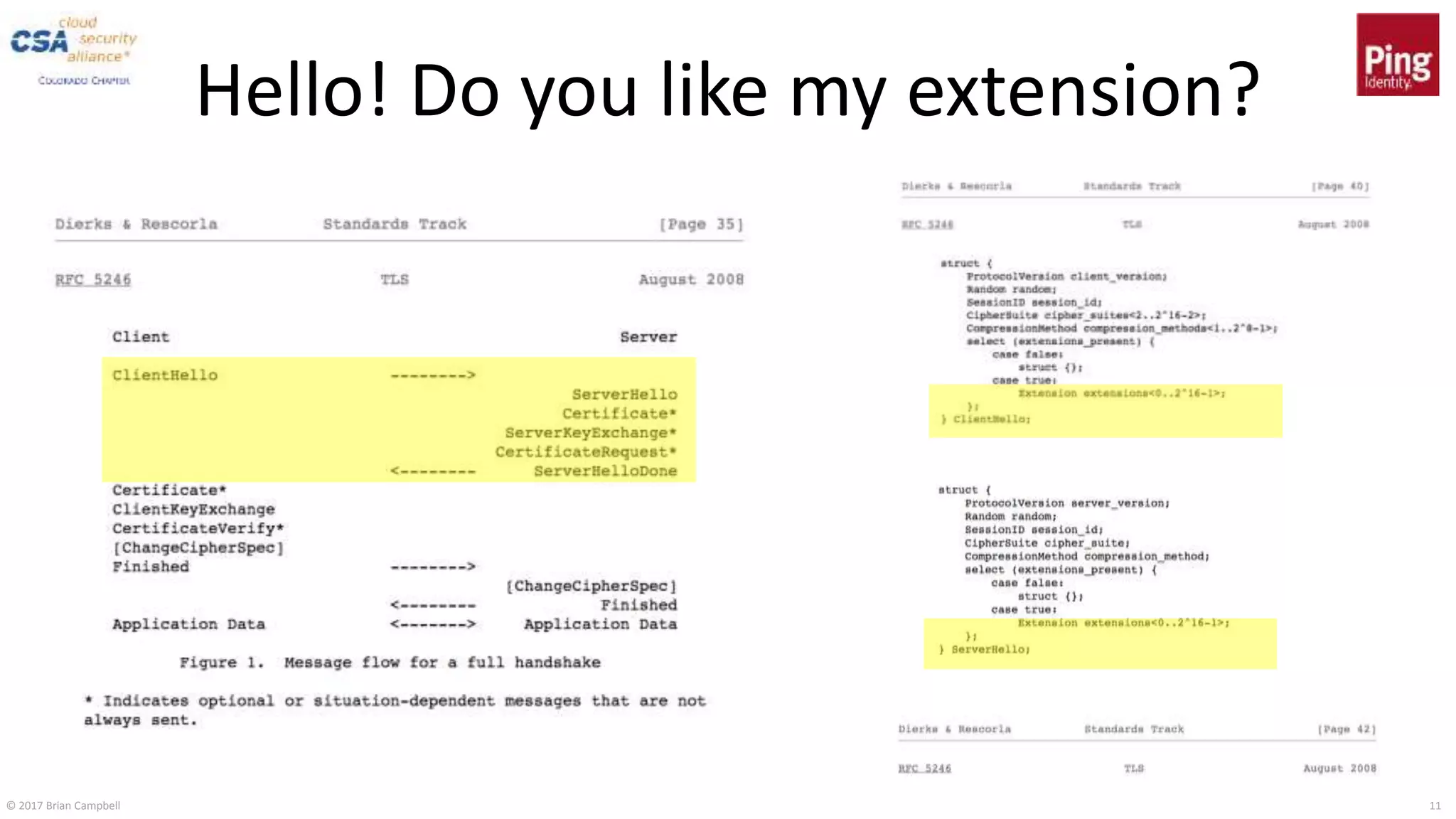
Do you even bind tokens, bro?
Client Server
ClientHello
...
token_binding [24]
token_binding_version [1,0]
key_parameters_list [2,0]
ServerHello
...
token_binding [24]
token_binding_version [1,0]
key_parameters_list [2]
Key Parameters:
(0) rsa2048_pkcs1.5
(1) rsa2048_pss
(2) ecdsap256
Also need extenstions:
Extended Master Secret
Renegotiation Indication
TLS Handshake](https://image.slidesharecdn.com/csa-co-2017-campbell-tokenbinding-171116165806/75/Token-Binding-as-the-Foundation-for-a-More-Secure-Web-12-2048.jpg)


![© 2017 Brian Campbell 17
Interlude: ‘jot’ or not?
A JWT
eyJraWQiOiJrMSIsImFsZyI6IkVTMjU2In0.eyJpc3MiOiJodHRwczovL2lzcy5leGFtcGxlLmNvbSIsImF1Z
CI6Imh0dHBzOi8vcnAuZXhhbXBsZS5vcmciLCJleHAiOjE1MDkzOTM3NTgsIm5iZiI6MTUwOTM5MzAzOCwic3
ViIjoiYnJpYW4iLCJlbWFpbCI6ImJyaWFuLmNhbXBiZWxsQGV4YW1wbGUuY29tIiwiZ3JvdXBzIjpbImdvb2Q
iLCJiYWQiLCJ1Z2x5Il19.hh8DBF1GfhXrf1L2jKJiJzjIESvBYzPc6NKjCZAXaztFQDiFIP2-
wfPw_JWBMulQsPJmVKKl-XA1OQWXQKgKiQ
The Header
{"kid":"k1","alg":"ES256"}
The Payload
{"iss":"https://iss.example.com",
"aud":"https://rp.example.org",
"exp":1509393758,
"nbf":1509393038,
"sub":"brian",
"email":"brian.campbell@example.com",
"groups":["good","bad","ugly"]}
The Signature
A quick refresher/introduction to JWT](https://image.slidesharecdn.com/csa-co-2017-campbell-tokenbinding-171116165806/75/Token-Binding-as-the-Foundation-for-a-More-Secure-Web-17-2048.jpg)