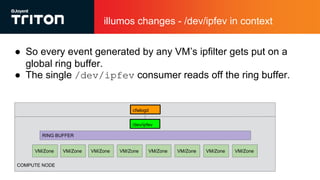
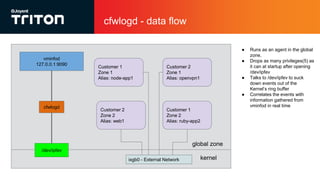
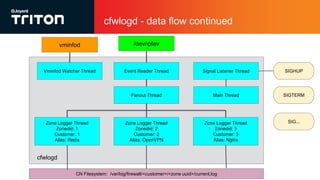
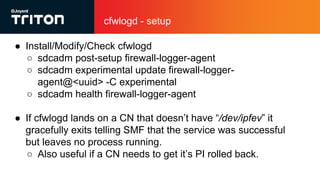
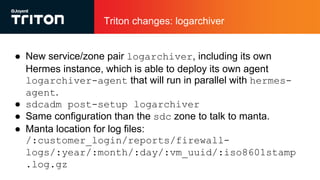
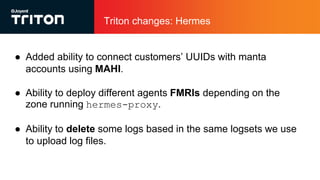
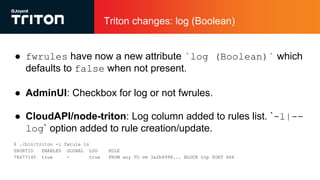
The document outlines the enhancements to Cloud Firewall (CFW) logging for Triton deployments, which now include detailed event logging of dropped packets and connections in compliance with Korean law. It describes various system changes, including the introduction of a new device (/dev/ipfev) for event generation and the implementation of a daemon (cfwlogd) for processing and logging these events in JSON format. Additionally, it discusses future developments and integration with Triton services for better log management and accessibility.