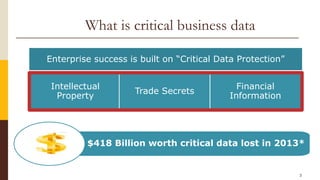
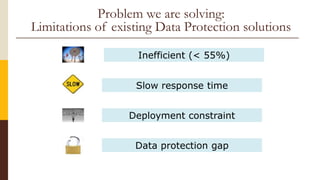
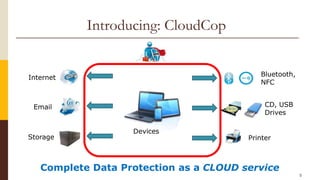
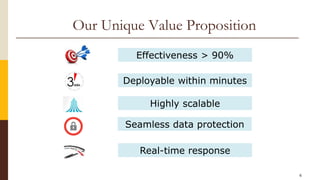
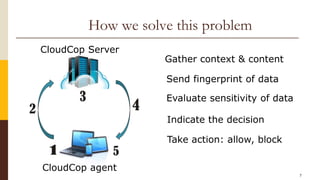
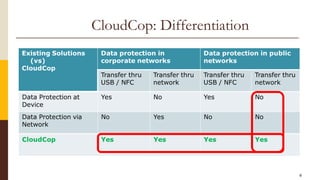
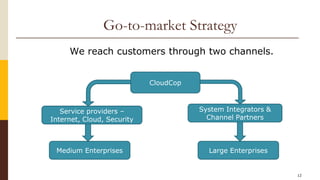
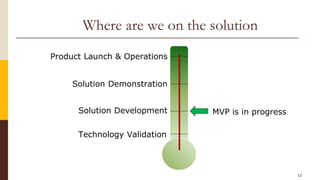
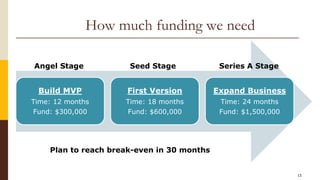
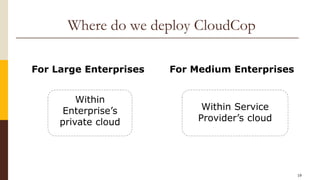
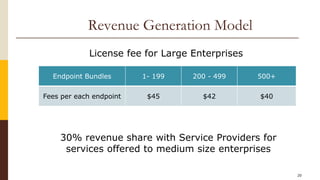
CloudCop is a data protection service aimed at addressing inefficiencies in existing solutions, with a unique cloud-based approach that allows for over 90% effectiveness and rapid deployment. The company seeks to fund its MVP and first product version, projecting a total funding need of $2.4 million over 30 months with plans for a potential exit through merger or acquisition. Target markets include financial services, retail, healthcare, and technology, with a revenue model based primarily on licensing fees for large enterprises.