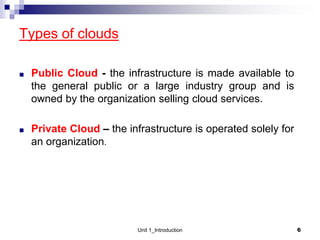
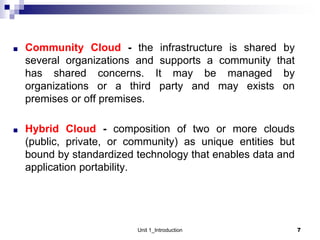
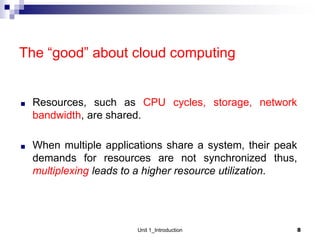
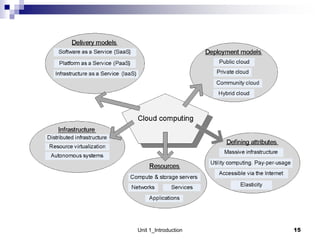
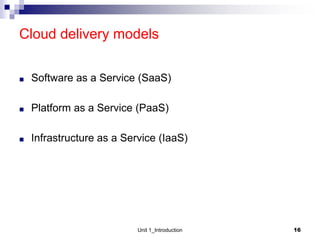
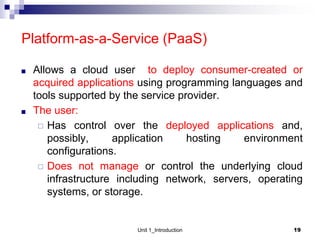
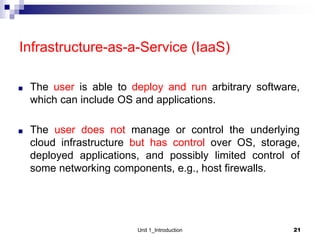
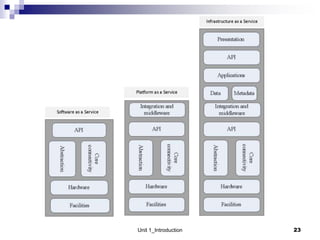
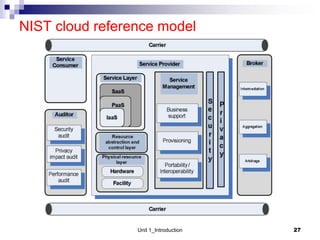
1. Cloud computing provides scalable and elastic resources over the internet that can be dynamically provisioned. There are different cloud delivery models including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
2. Cloud computing faces challenges related to availability of service, vendor lock-in, data security and privacy issues, and performance unpredictability due to resource sharing.
3. Ethical issues in cloud computing include loss of control of data, unauthorized access to data across organizational boundaries, and privacy concerns over personal data being collected by cloud providers.