This document discusses client/server computing. It defines client/server computing as a model based on distributing functions between server and client processes. A client is a process that requests services, while a server provides requested services. Clients and servers can reside on the same or different networked computers. Different types of servers are discussed, including file servers, print servers, application servers, mail servers, and fax servers, each providing a specific type of service to client processes over a network.
























































































































![Introduction to Client/Server Computing
108
machine, tell it to display to the user’s machine (e.g., export DISPLAY=[user’s machine]:0
on a remote machine running bash), then start the client. The client will then connect to
the local server and the remote application will display to the local screen and accept input
from the local input devices. Alternately, the local machine may run a small helper program
to connect to a remote machine and start the desired client application there. Practical
examples of remote clients include:
• administering a remote machine graphically.
• running a computationally-intensive simulation on a remote Unix machine and
displaying the results on a local Windows desktop machine.
• running graphical software on several machines at once, controlled by a single
display, keyboard and mouse.
Keyboard Mouse Screen
User Workstations
Remote Machine
X-Server
X-Client
(Browser)
X-Client
(X-Terminal)
Network
X-Client
Fig. 6.1: X-Client-Server Model
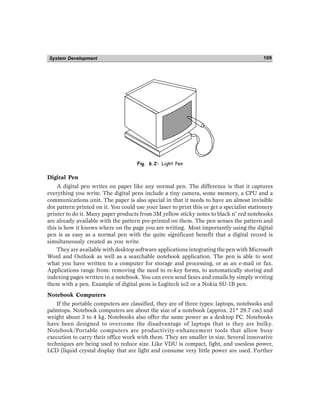
Light Pen
Light Pen is an input device that utilizes a light-sensitive detector to select objects on a
display screen. It is similar to a mouse, except that with a light pen you can move the
pointer and select objects on the display screen by directly pointing to the objects with the
pen. A light pen is pointing device that can be used to select an option by simply pointing
at it, drawing figures directly on the screen. It has a photo-detector at its tip. This detector
can detect changes in brightness of the screen. When the pen is pointed at a particular spot
on the screen, it records change in brightness instantly and inform the computer about
this. The computer can find out the exact spot with this information. Thus, the computer
can identify where you are pointing on the screen.
Light pen is useful for menu-based applications. Instead of moving the mouse around
or using a keyboard, the user can select an option by pointing at it. A light pen is also
useful for drawing graphics in CAD.](https://image.slidesharecdn.com/client-server-computing-220607124616-49e178be/85/client-server-computing-pdf-121-320.jpg)