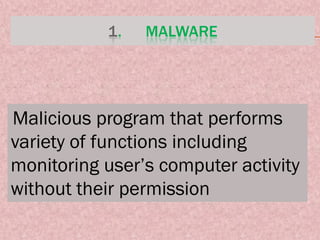
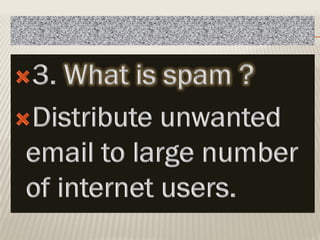
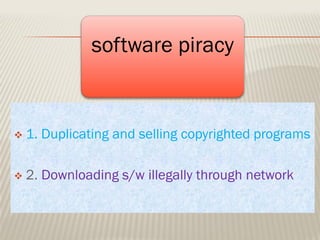
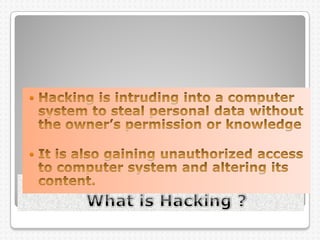
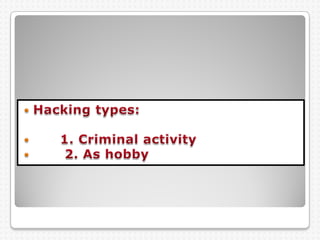
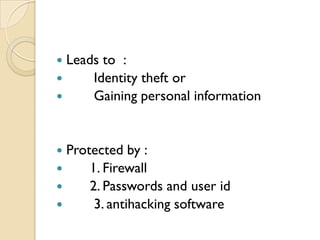
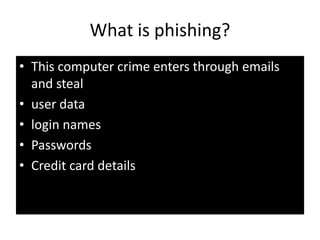
Computer crimes and ethics involve threats to businesses from hacking, malware, and theft of passwords or sensitive information. The document outlines that computer users should be honest, respect others' privacy, and obey cyber laws. It defines various computer crimes like malware, spam, and software piracy. Malware can monitor users without permission while spam spreads unsolicited messages. Piracy involves illegally duplicating or downloading copyrighted software. The document also discusses worms, spyware, ransomware, phishing, cookies, firewalls, proxy servers, encryption, decryption, and cyber laws in India to prevent computer crimes.