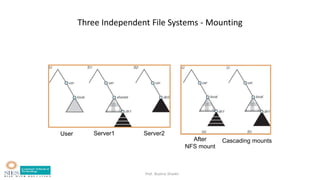
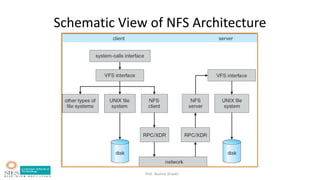
This document summarizes a lecture on file system implementation. It discusses:
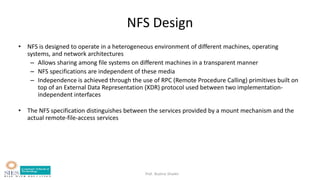
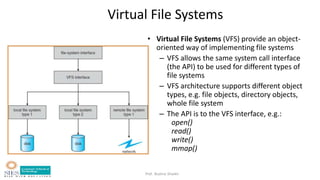
- File system structure including logical file system, file organization module, basic file system, and device drivers.
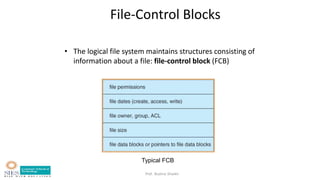
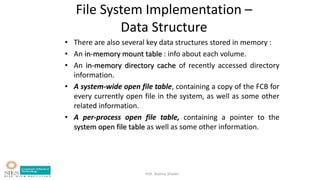
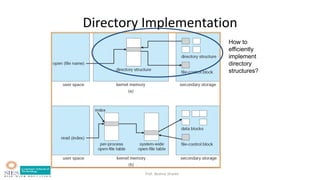
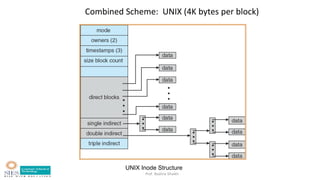
- Key data structures including file control blocks, mount table, directory cache, open file tables.
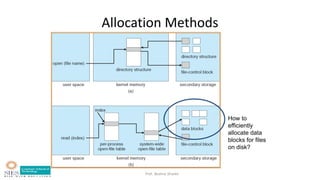
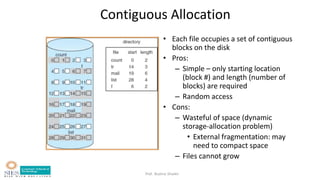
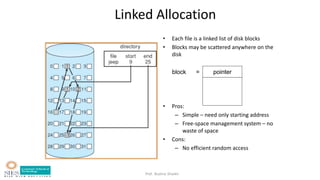
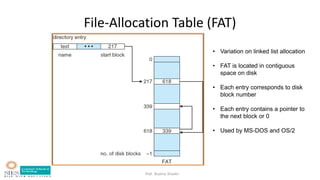
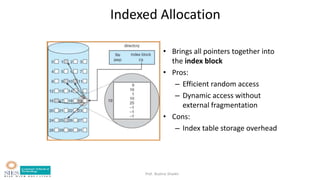
- Allocation methods like contiguous, linked, and indexed allocation.
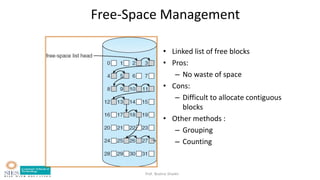
- Free space management techniques like bit vectors, linked lists, and grouping.
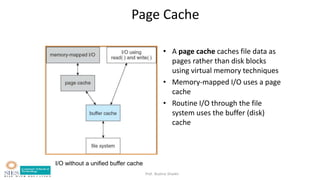
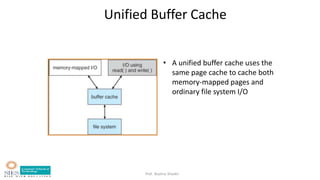
- Caching strategies to improve performance like disk caching, read-ahead, and memory mapping.


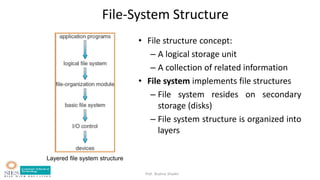
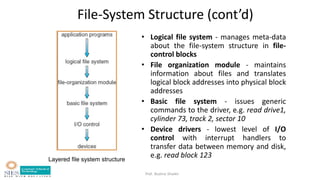







![Prof. Bushra Shaikh
…
0 1 2 n-1
bit[i] =
0 block[i] free
1 block[i] occupied
Block number calculation:
(number of bits per word) x (number of 0-value words) + offset of first 1 bit
We scan the bitmap sequentially for the first non-zero word.
The first group of 8 bits (00001110) constitute a non-zero word since all bits are not 0.
After the non-0 word is found, we look for the first 1 bit. This is the 4th bit of the non-zero word.
So, offset = 4.Therefore, the first free block number = 8*0+4 = 4.
Free-Space Management - Bit Vector
• Bit vector (for n blocks)](https://image.slidesharecdn.com/chapter5-filesystemimplementation-230330144335-34402085/85/chapter5-file-system-implementation-ppt-22-320.jpg)