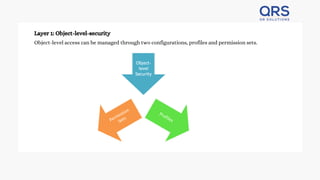
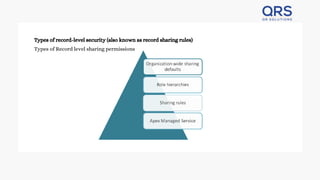
Salesforce utilizes a robust security model encompassing object-level, field-level, and record-level security to protect data stored in objects, fields, and records. Access is managed through profiles and permission sets, allowing customization for users' needs, including individual fields and records. The model provides multiple ways to share records, ensuring that only authorized users can view or modify the data, making Salesforce a secure CRM solution.