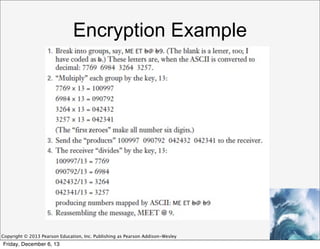
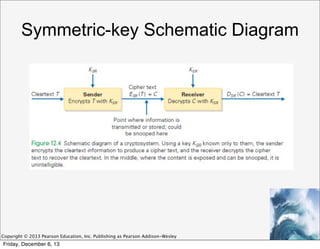
This document discusses privacy and digital security. It covers information privacy standards like the OECD Fair Information Practices, which outline principles for handling personal data. The document also discusses methods of encryption, including symmetric key encryption where both parties share a private key, and public key encryption where individuals have separate public and private keys. The use of cookies and tracking online is also examined from a privacy perspective.