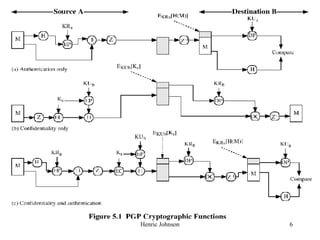
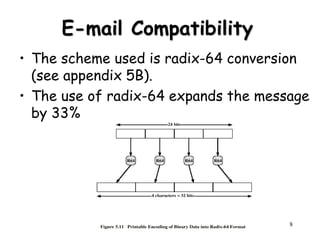
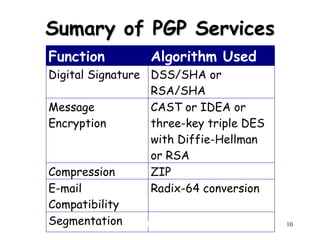
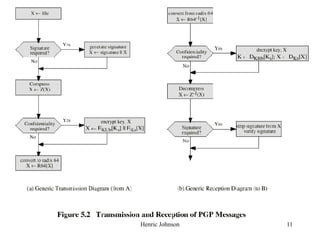
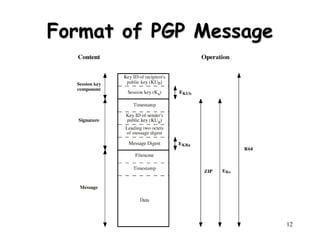
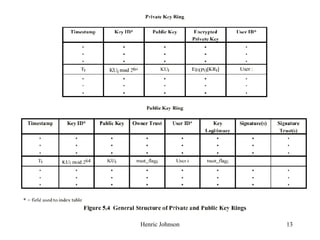
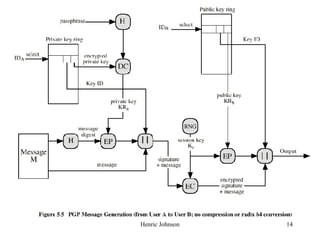
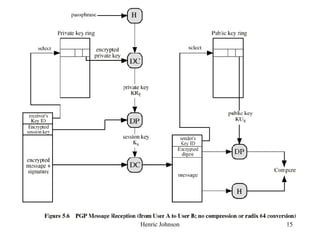
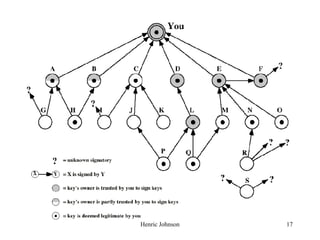
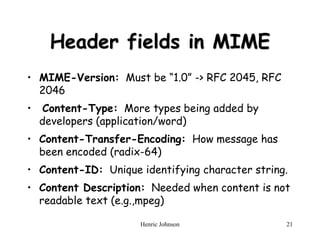
This document discusses electronic mail security and summarizes Pretty Good Privacy (PGP) and S/MIME. PGP provides confidentiality, authentication, compression and other services for email and files. It uses algorithms like DSS/SHA and CAST for signing and encrypting messages. S/MIME will likely become the industry standard, using X.509 certificates and algorithms like SHA-1, DSS, and Triple-DES. The document also provides details on how keys are managed and messages are formatted with each method.