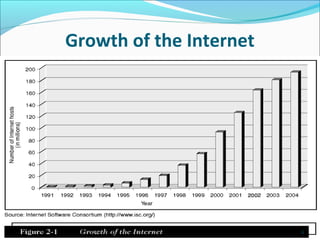
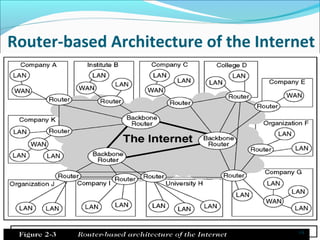
The document discusses the history and technical aspects of the Internet and World Wide Web. It covers the origins of the ARPANET network in the 1960s, the development of protocols like TCP/IP and HTML, and different connection methods including DSL, cable, and wireless. It also examines intranets, extranets, Internet2, and the goals of the Semantic Web to add meaning to words on webpages through XML tagging.