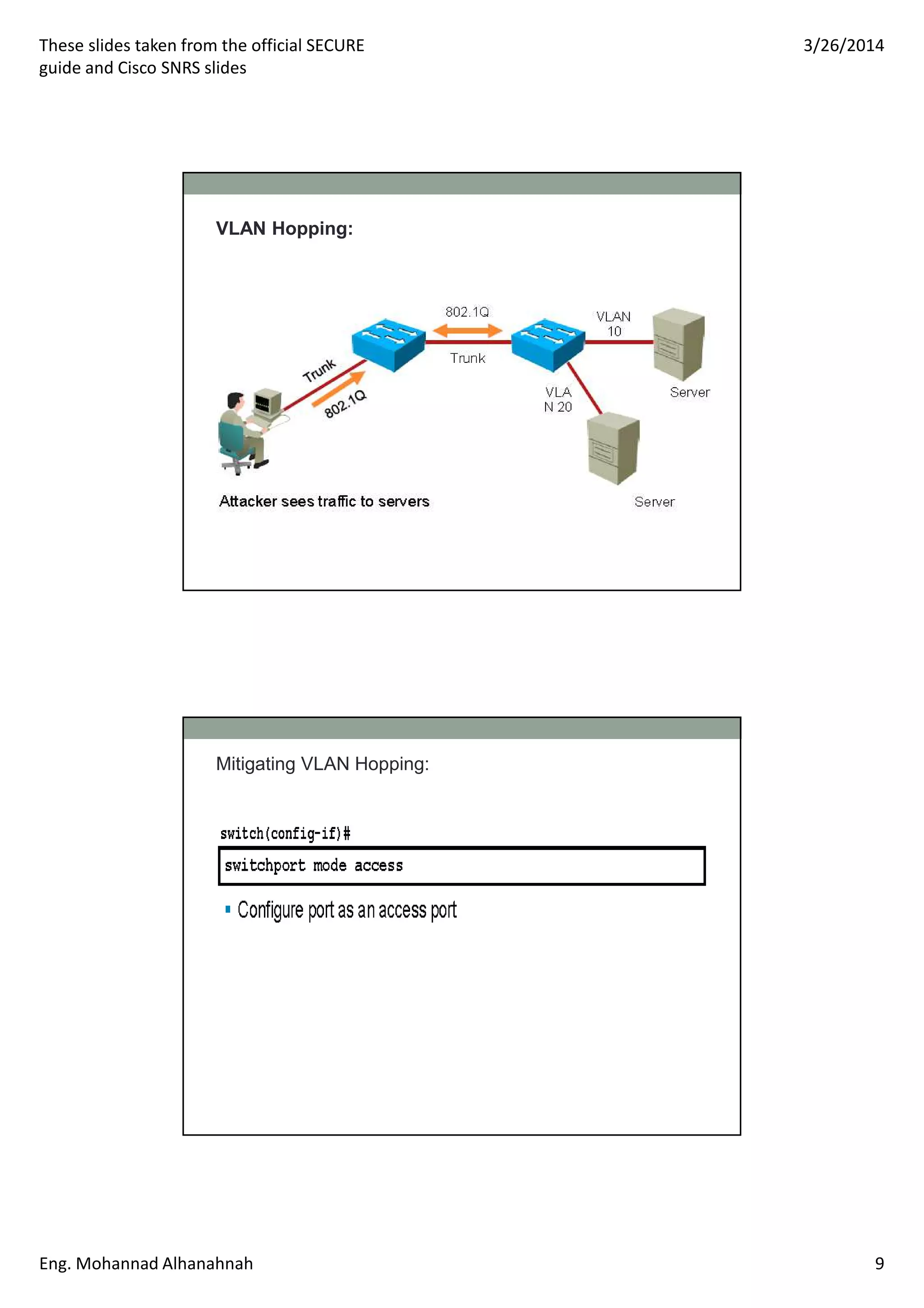
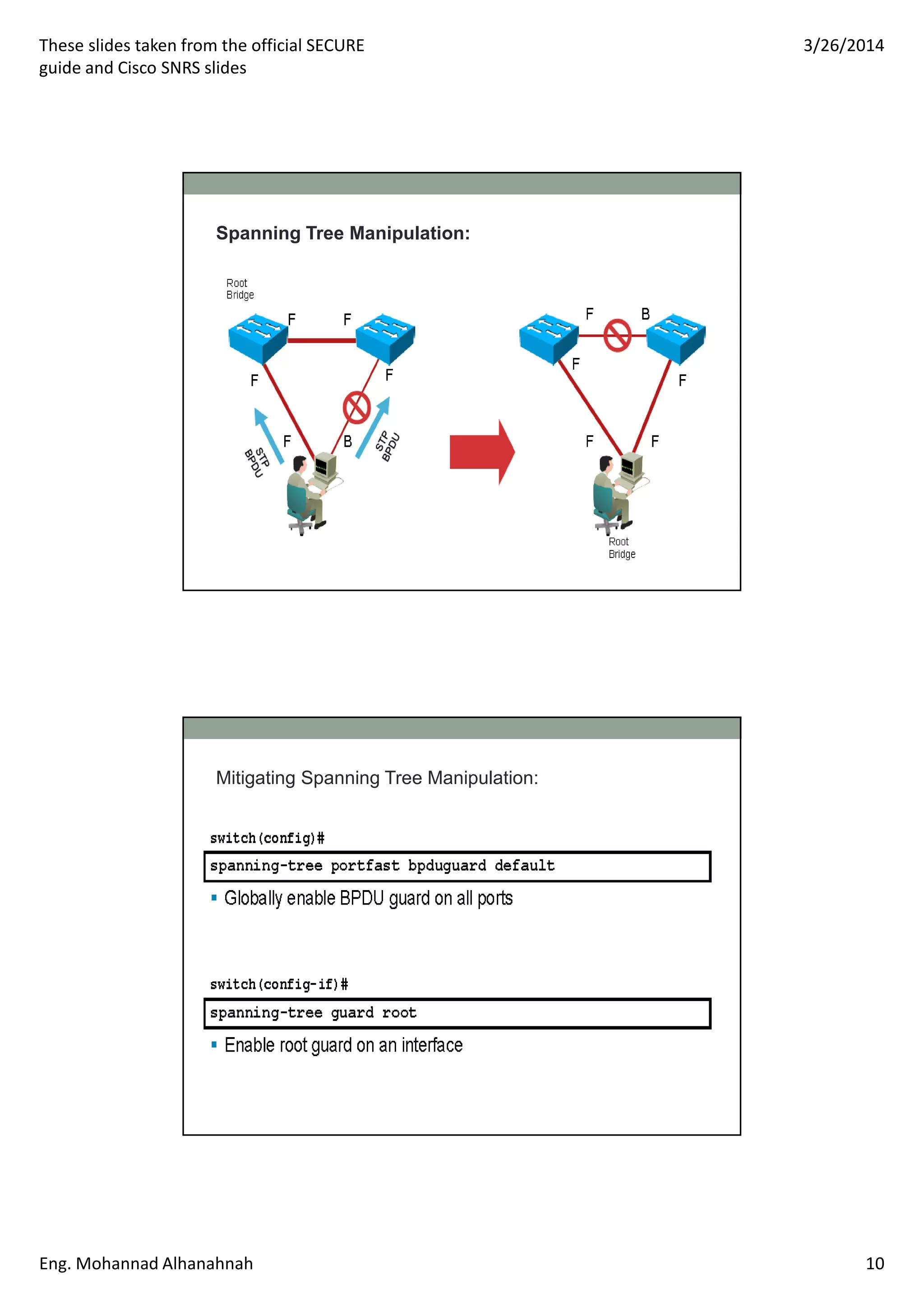
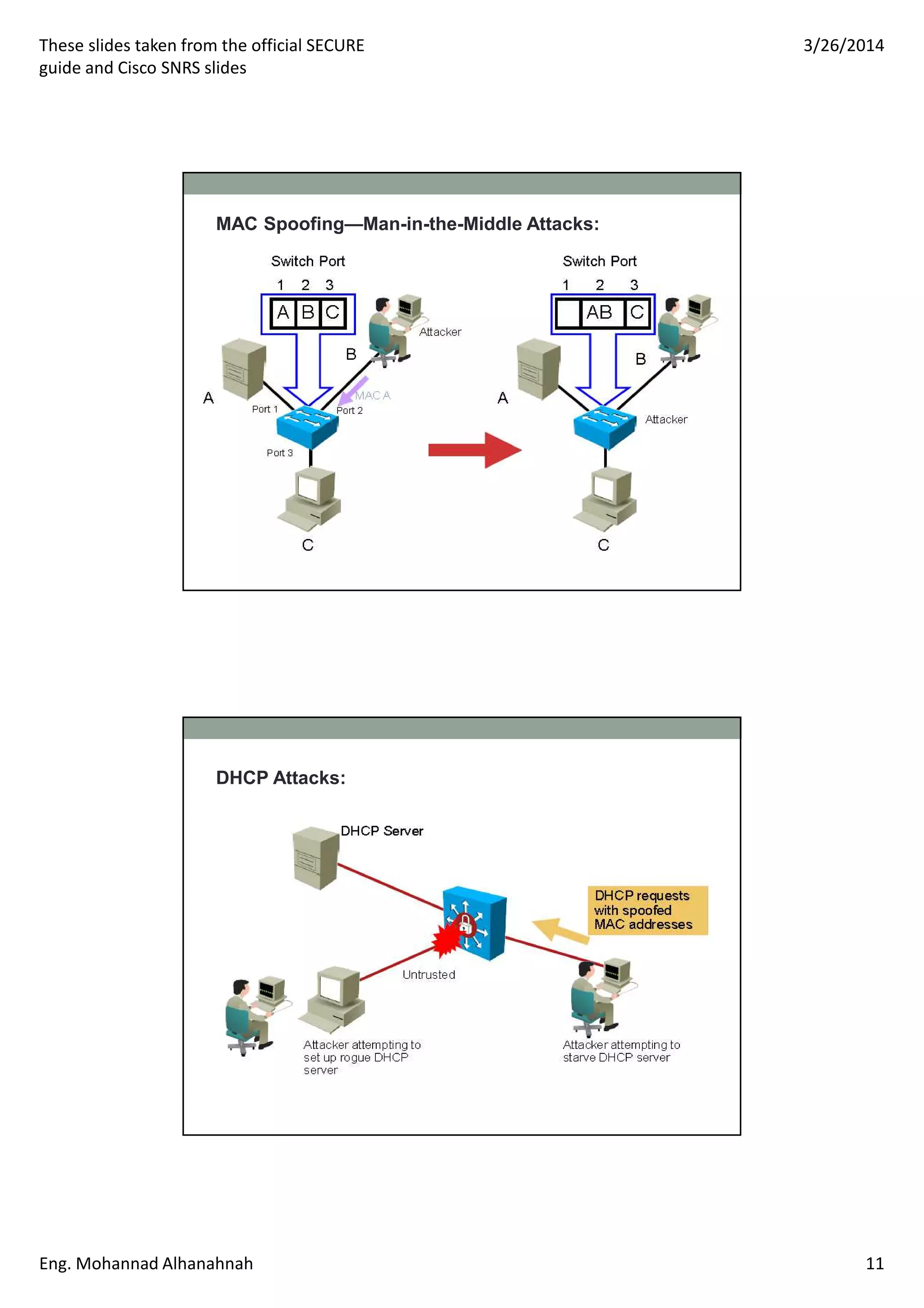
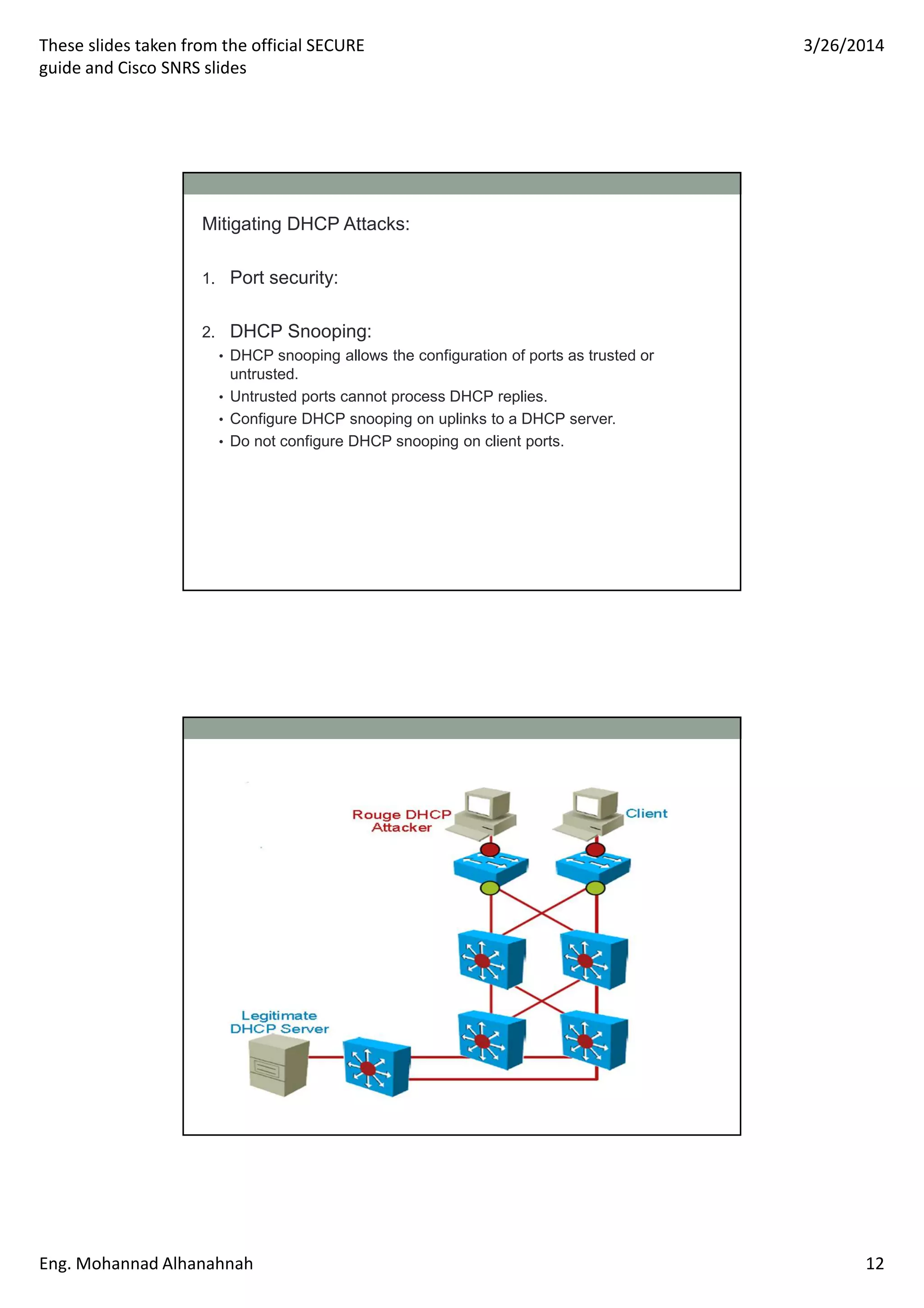
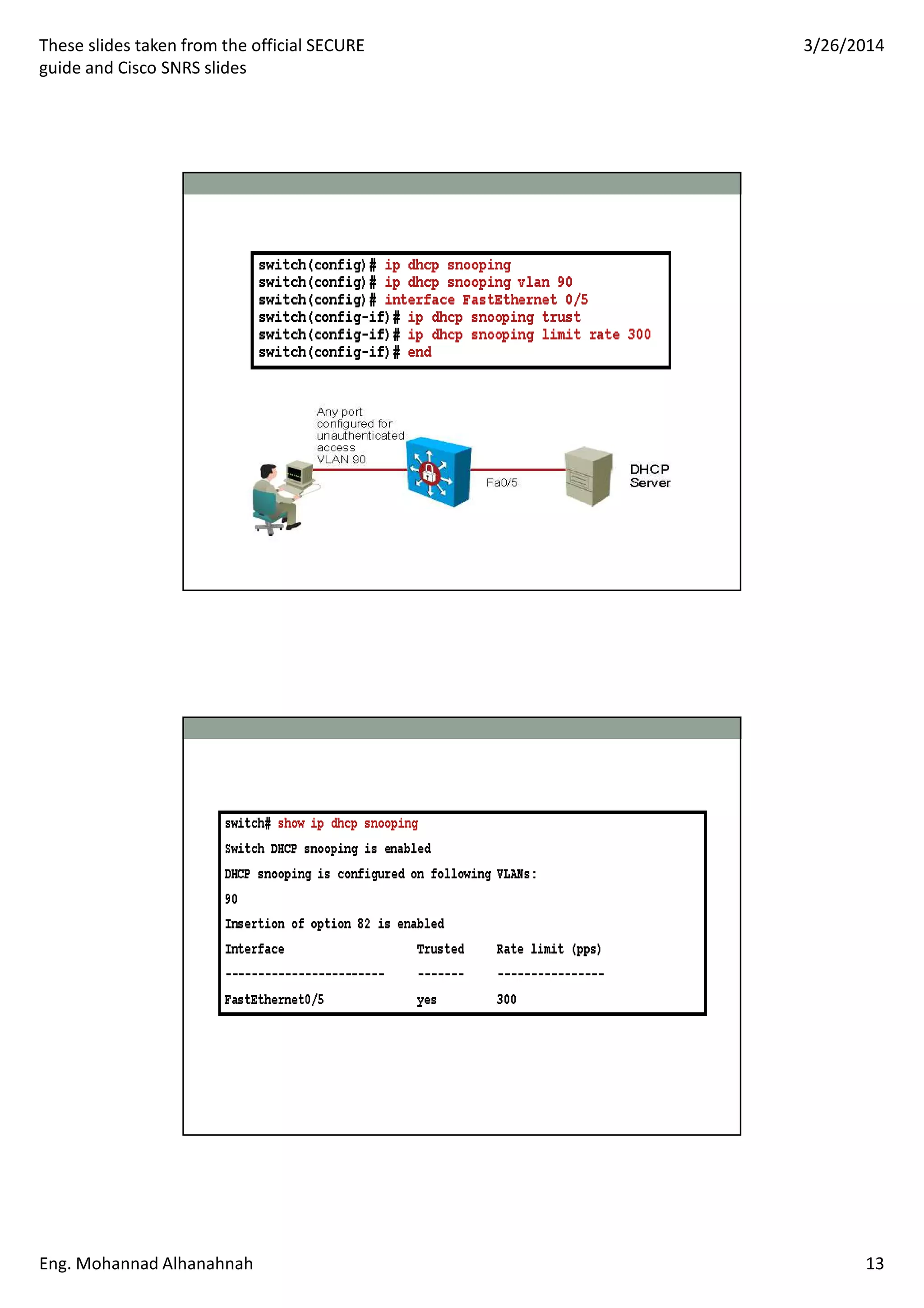
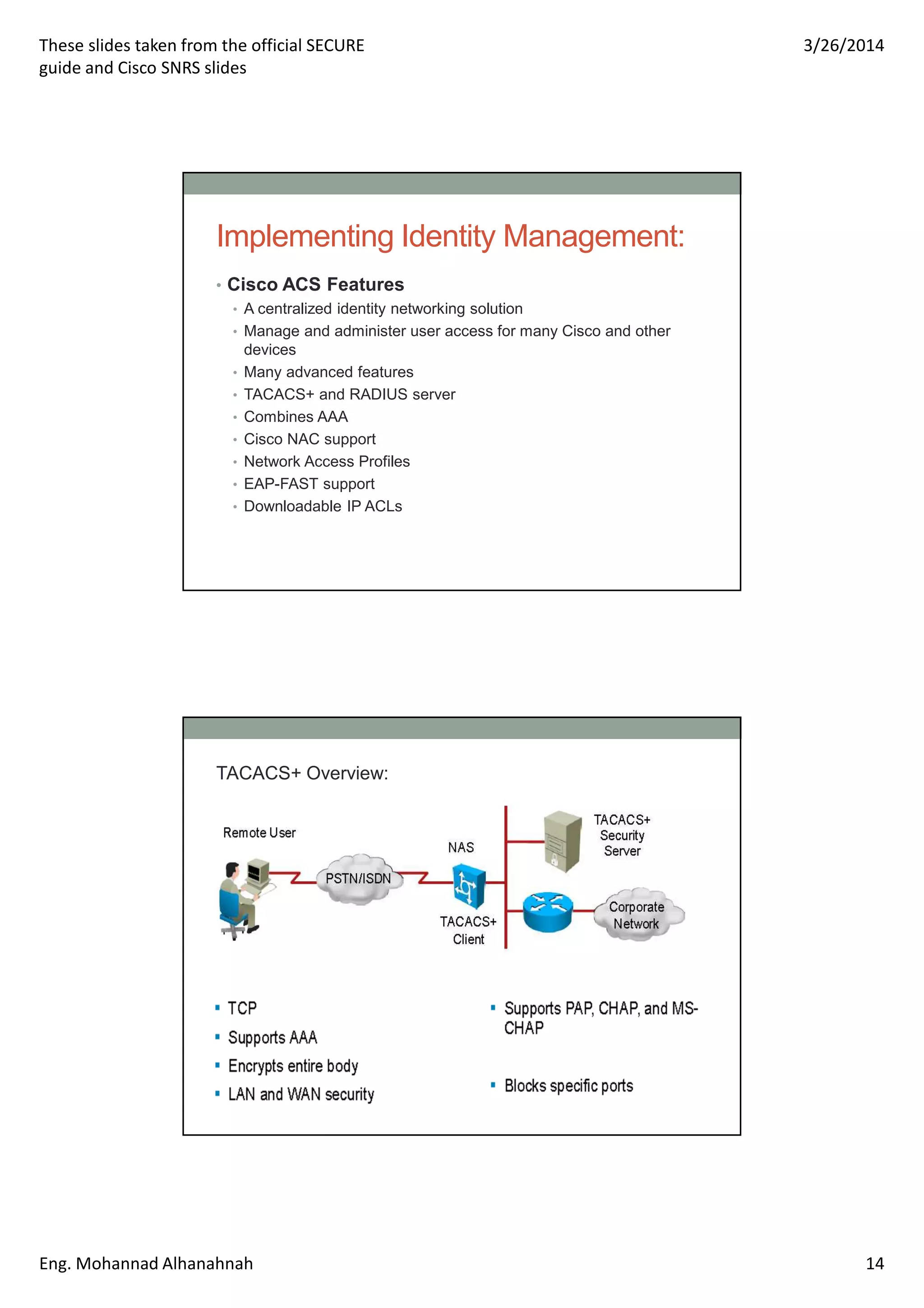
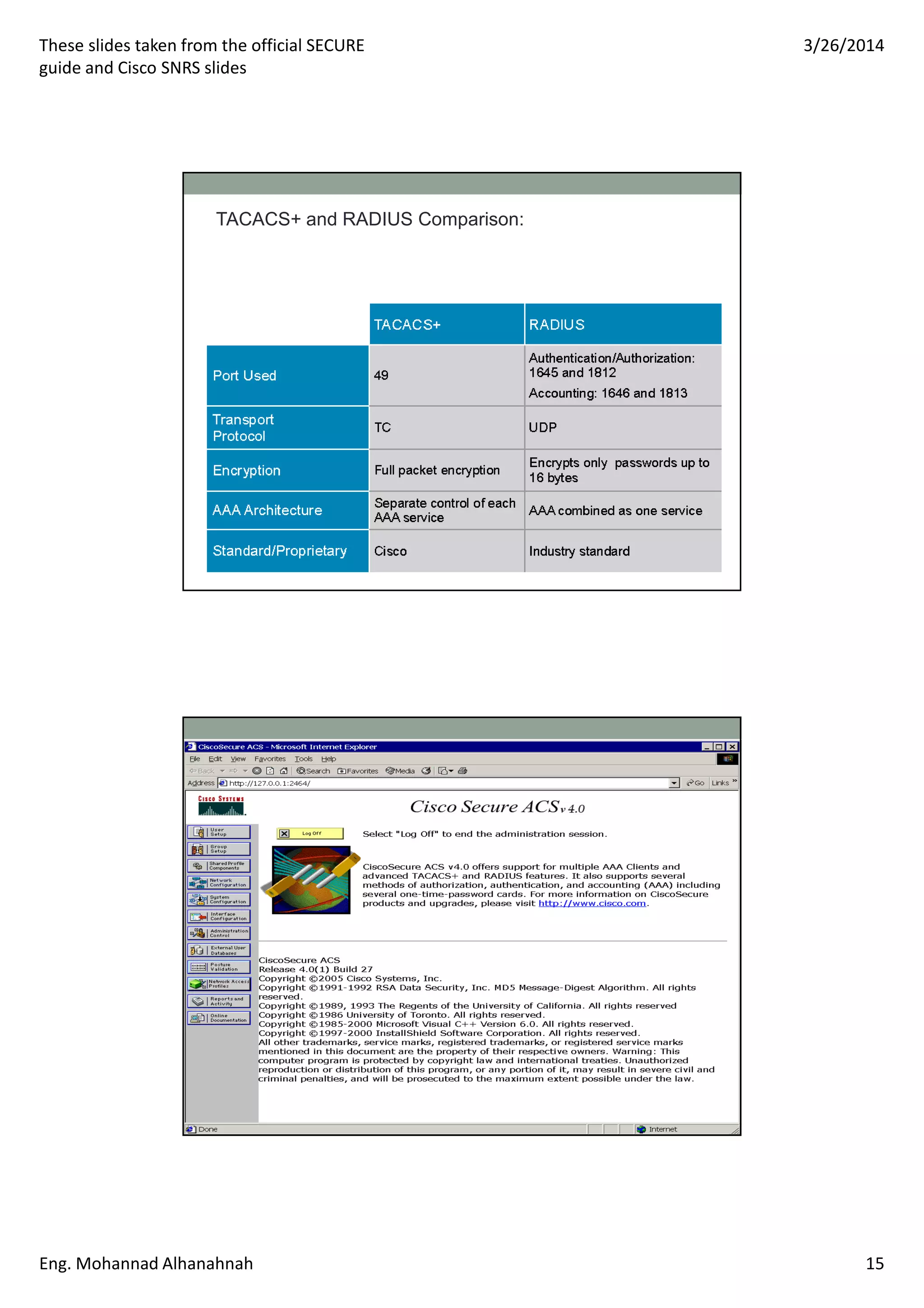
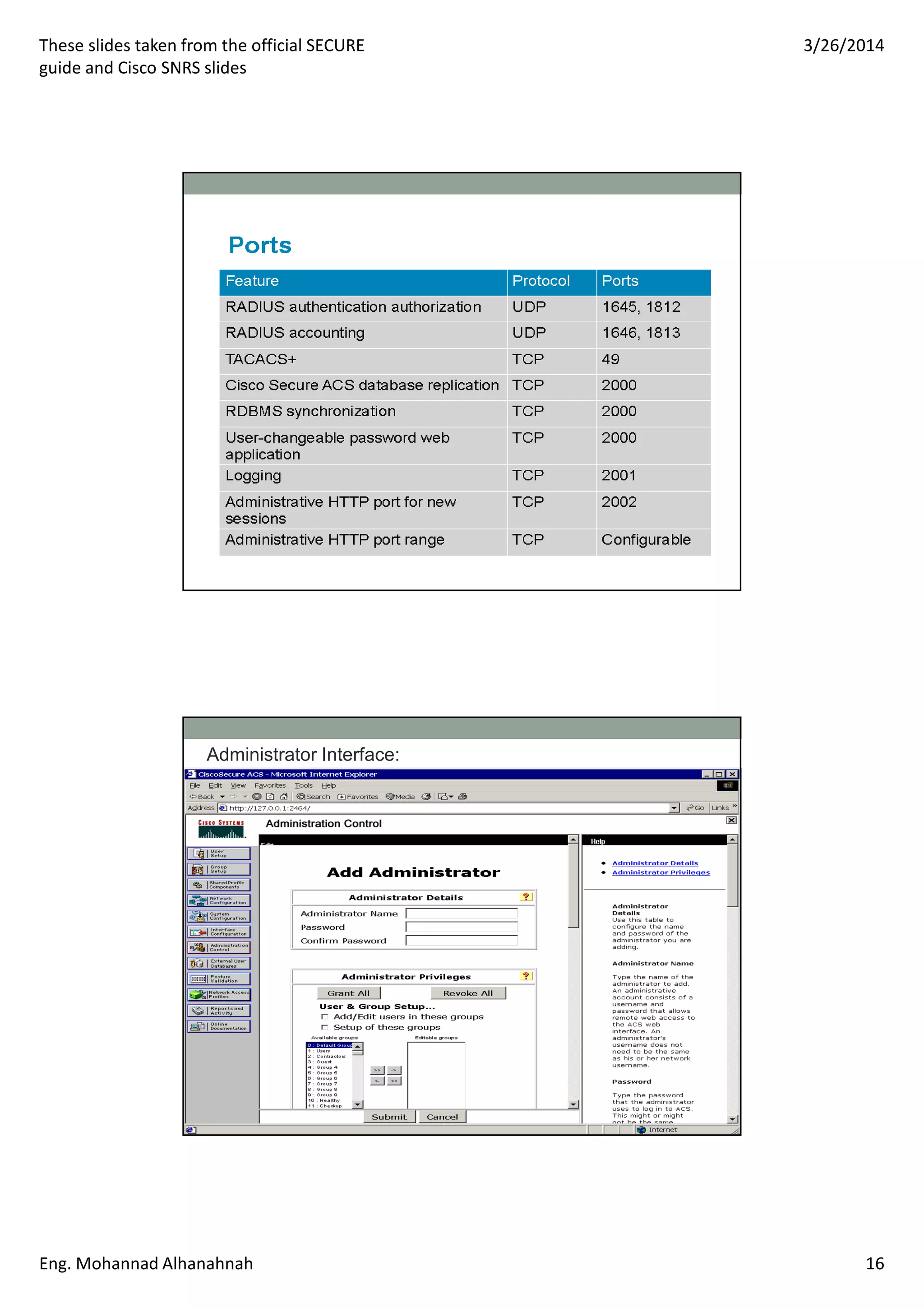
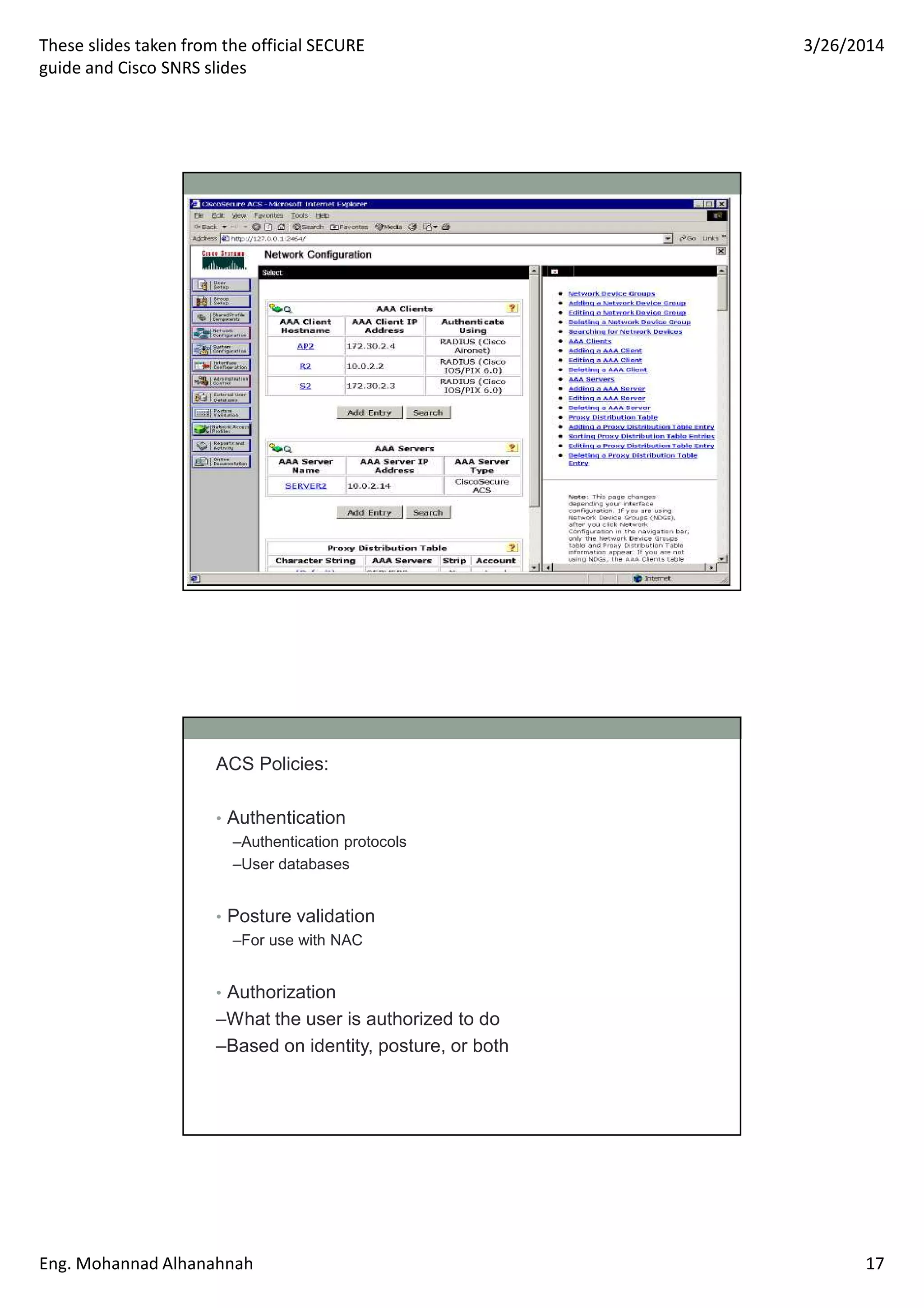
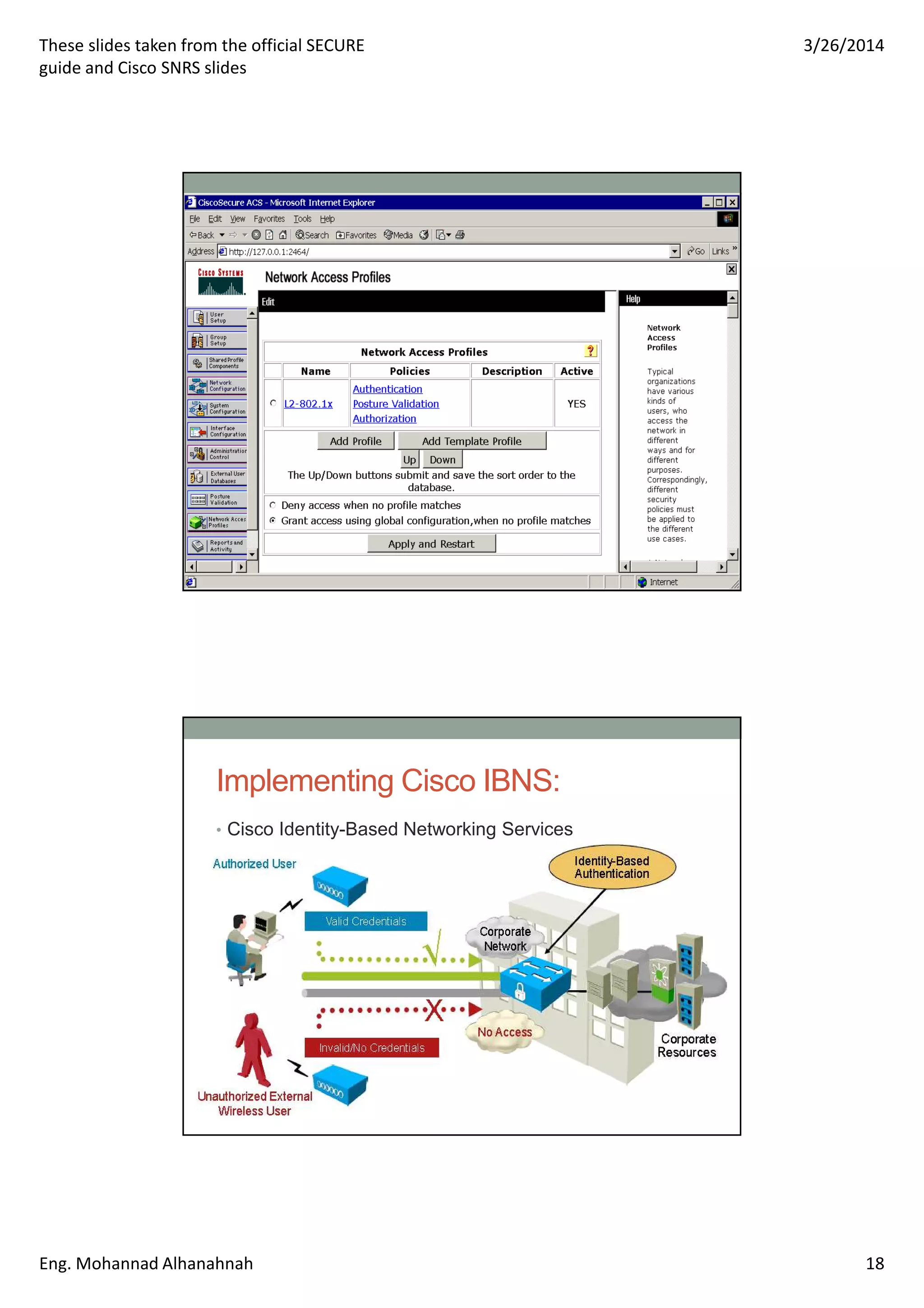
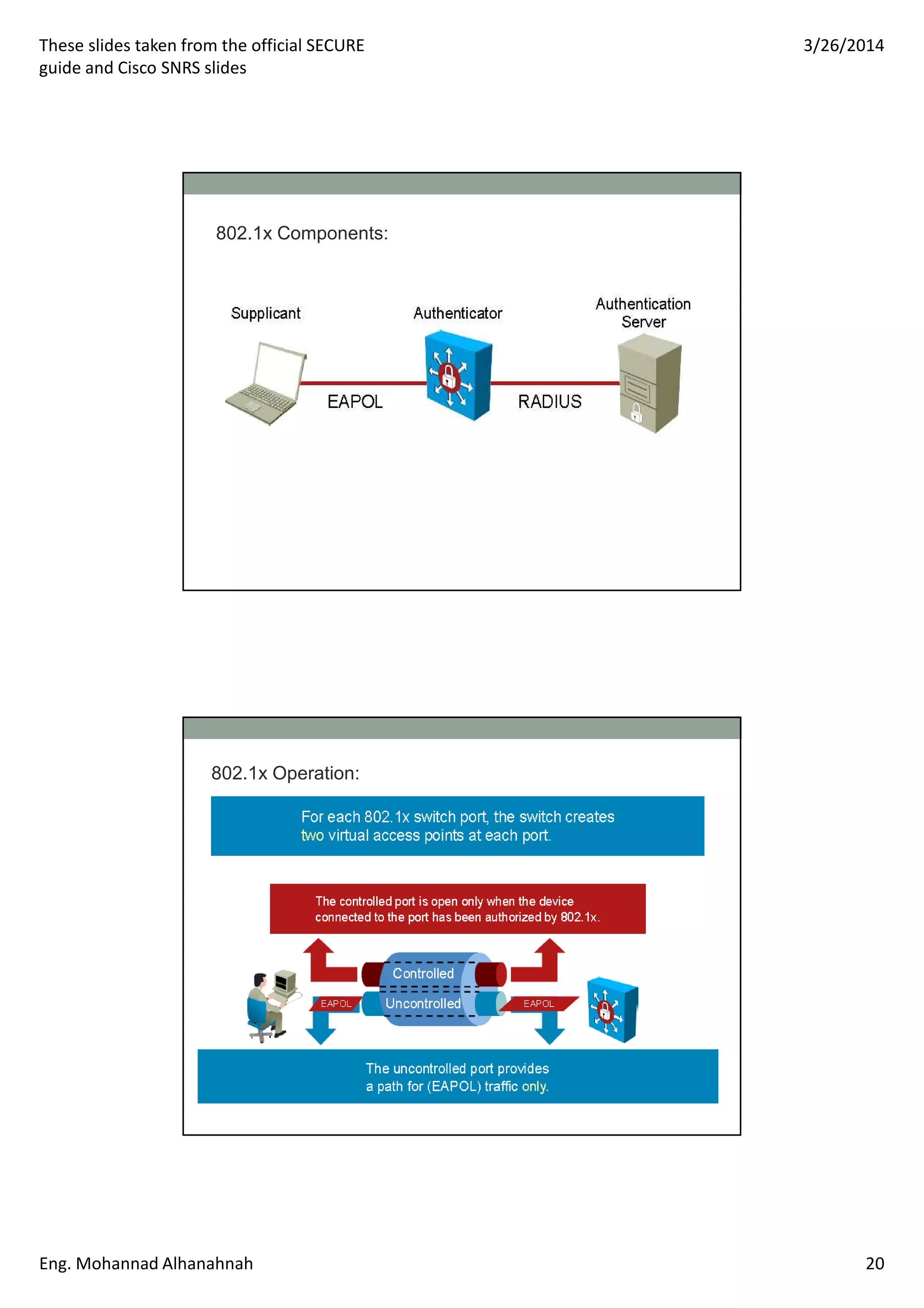
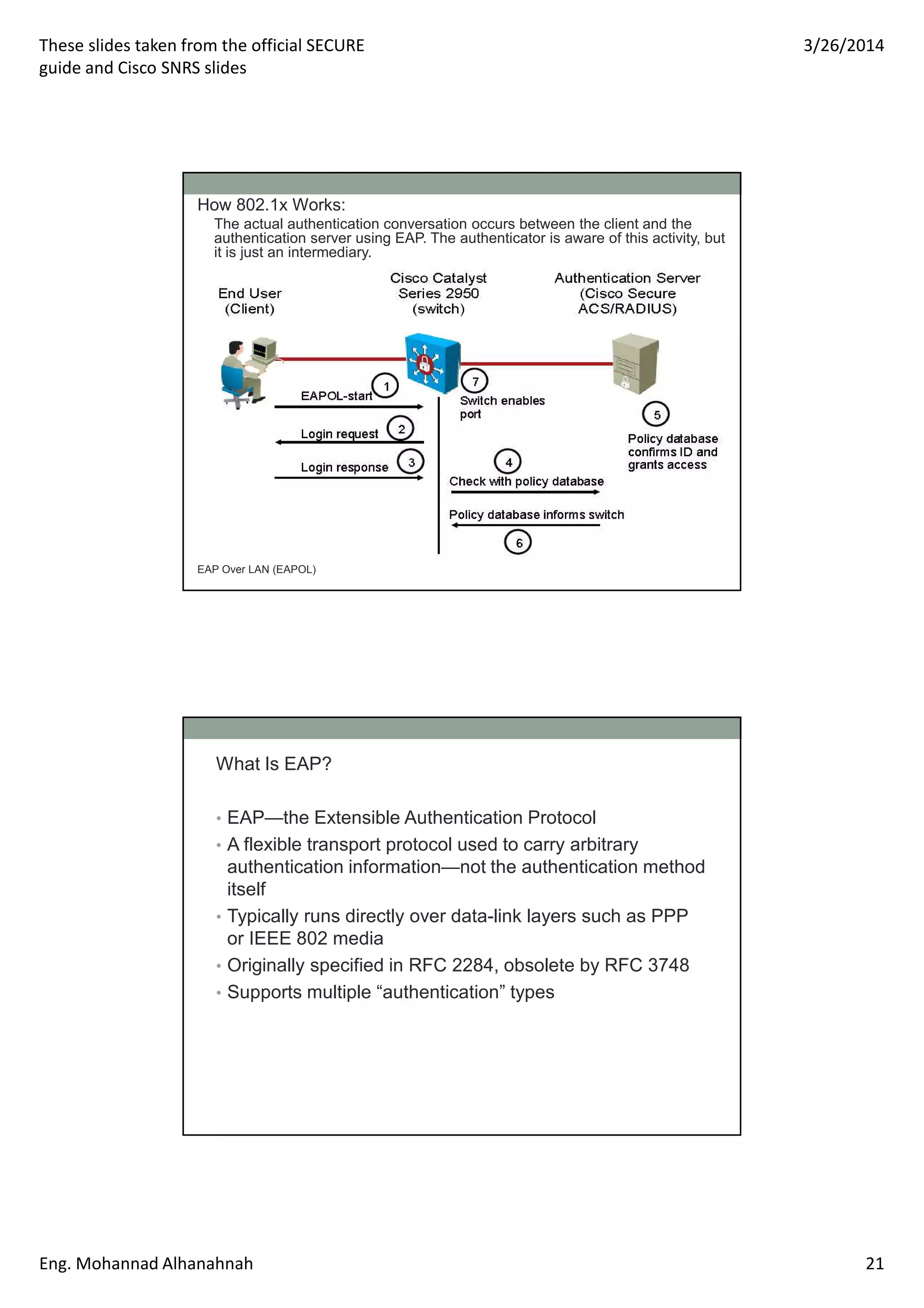
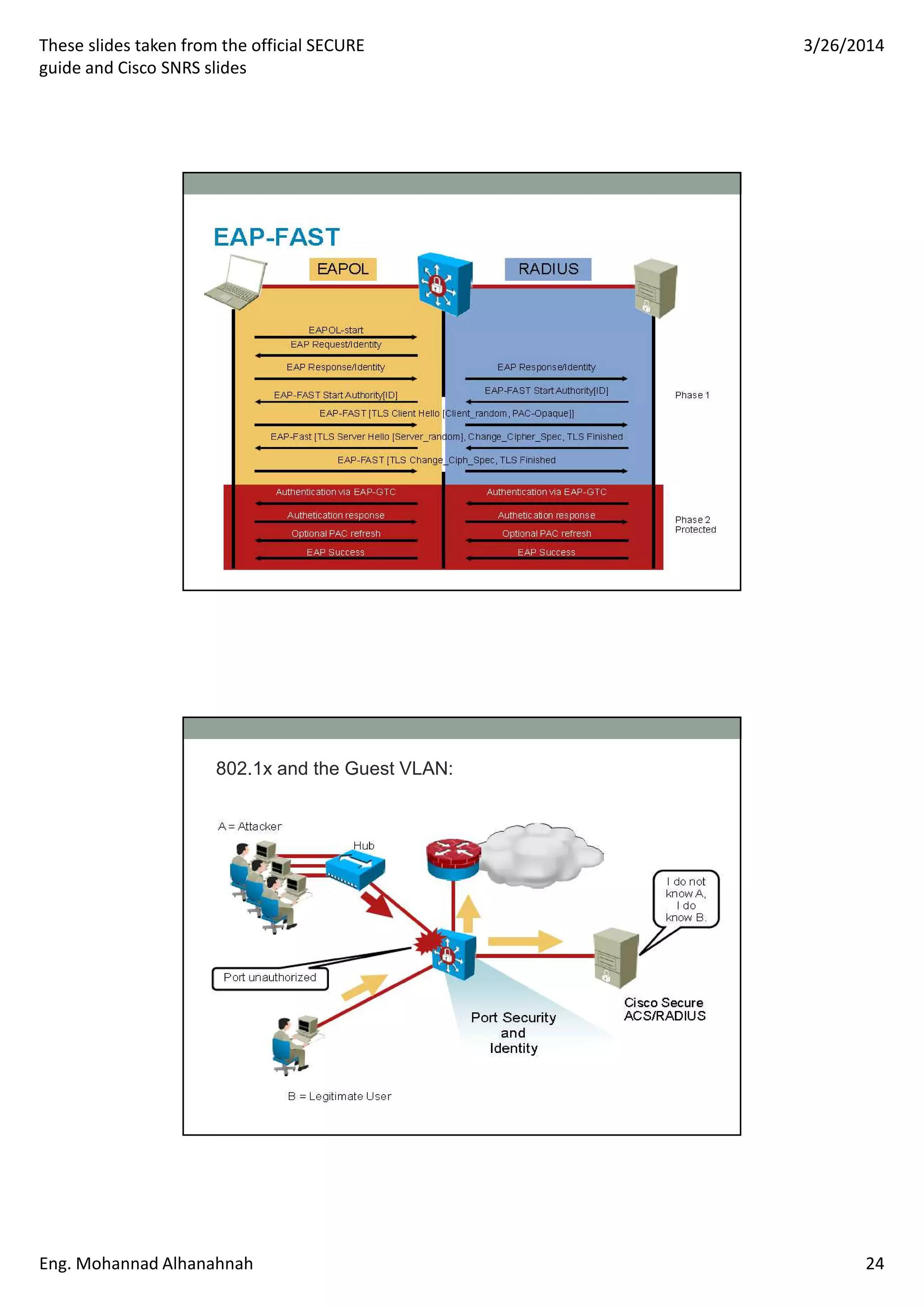
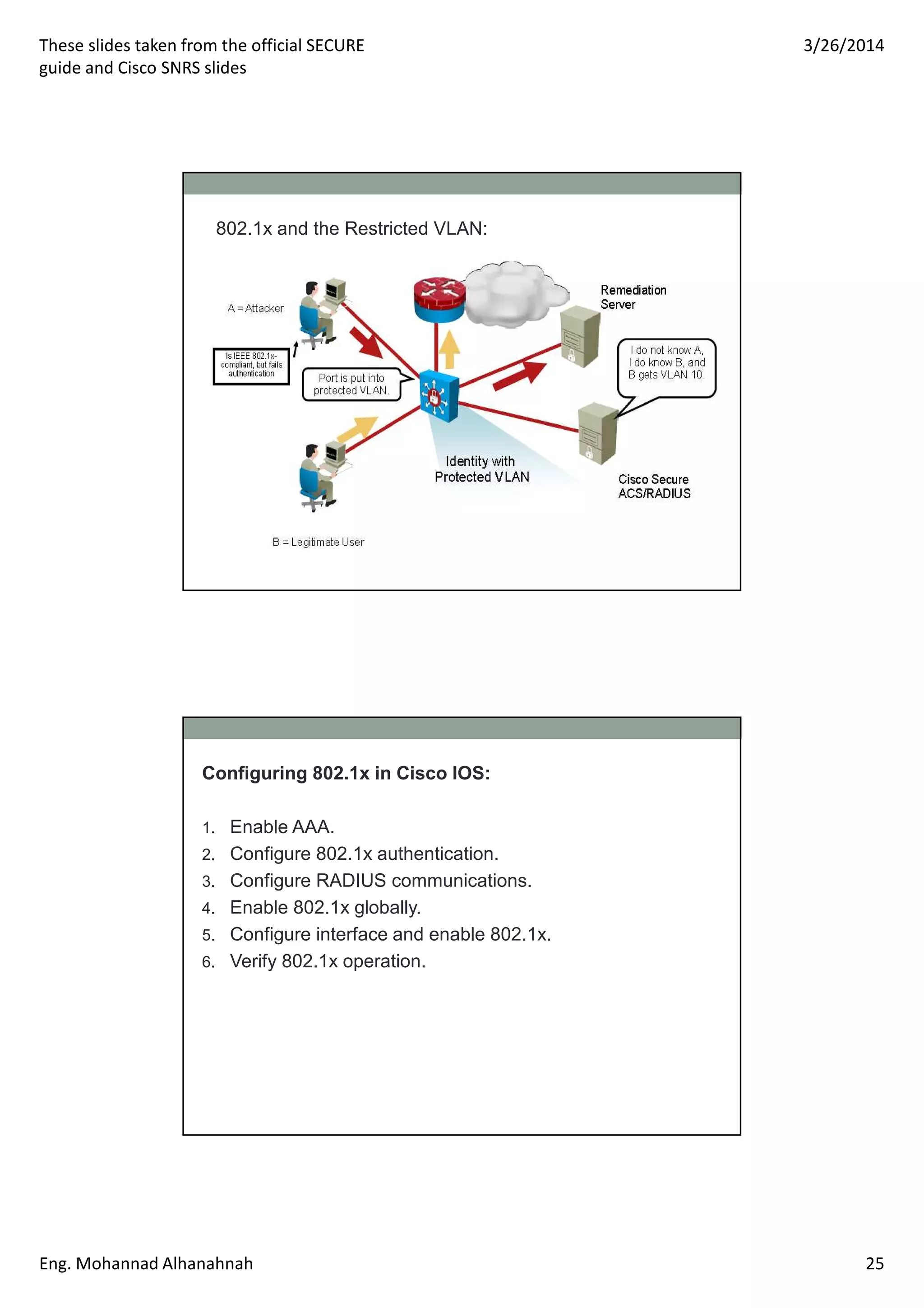
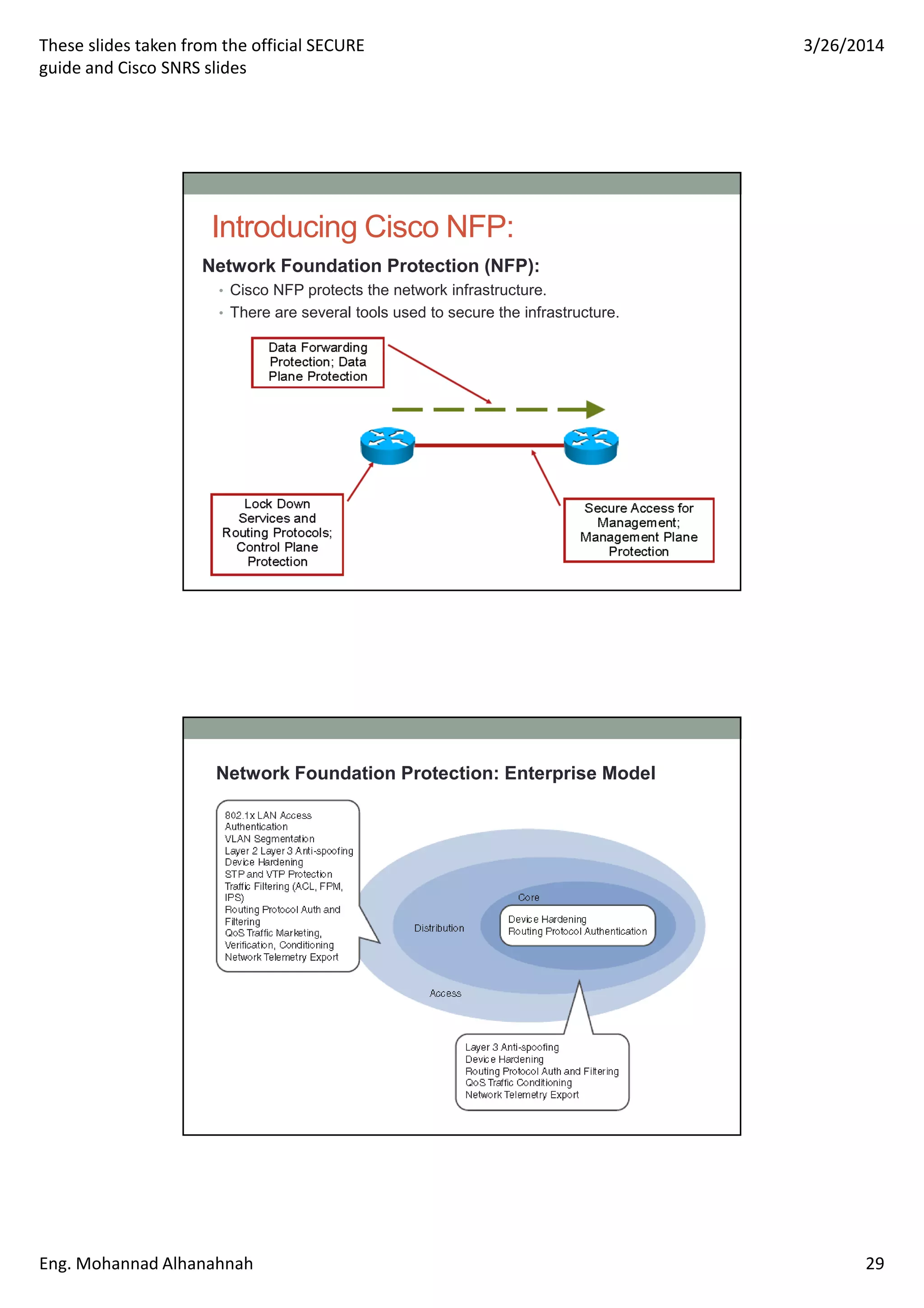
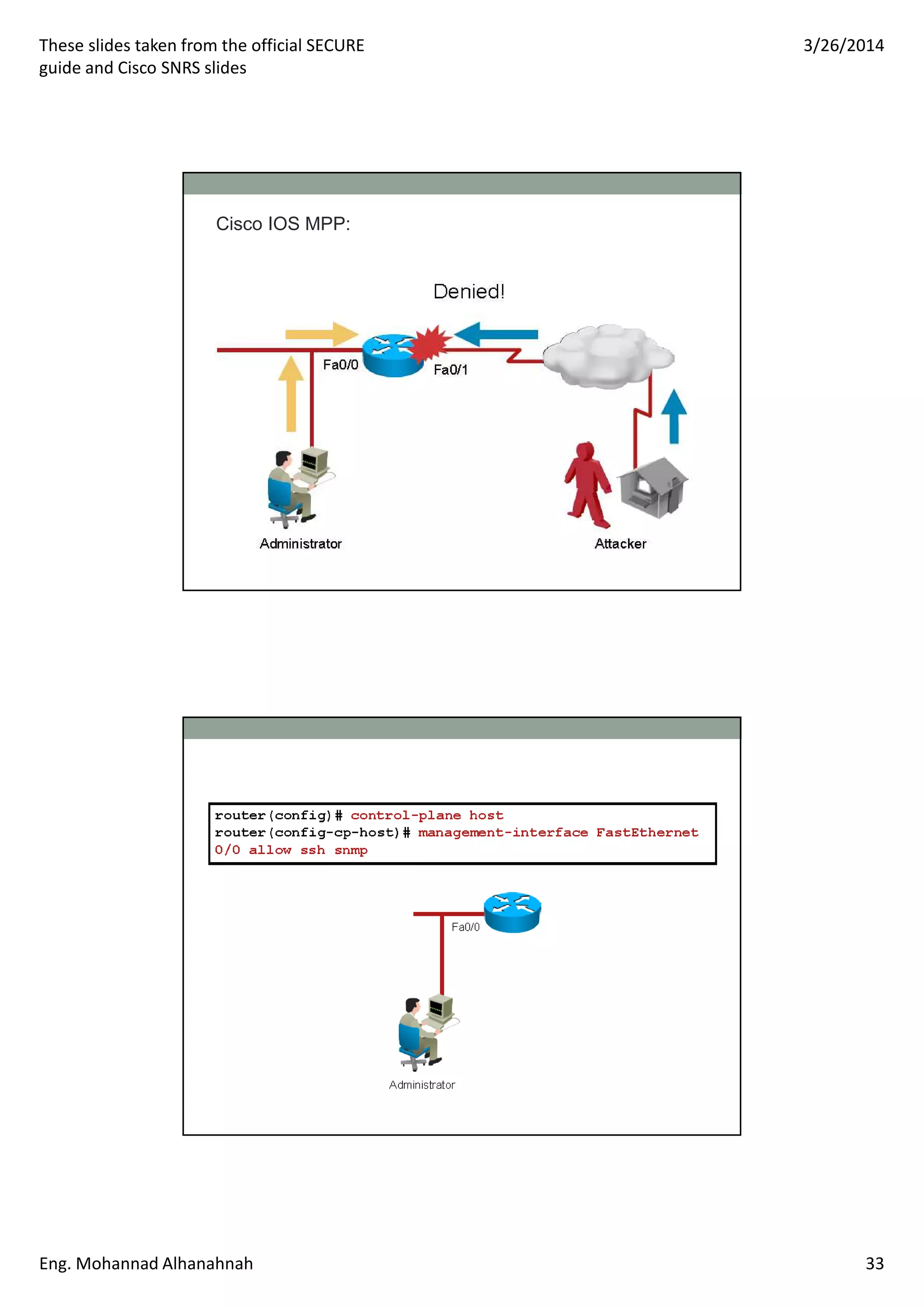
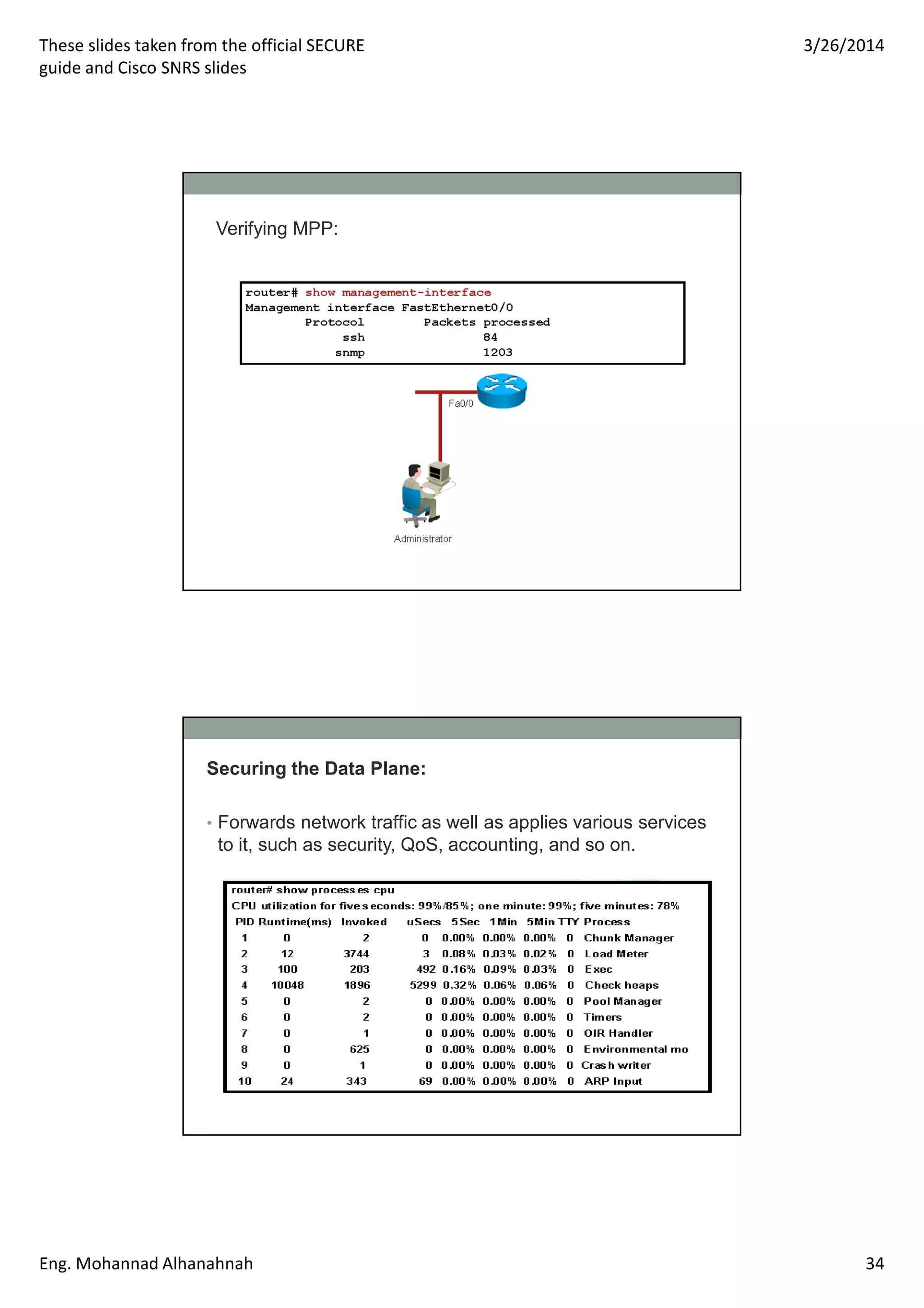
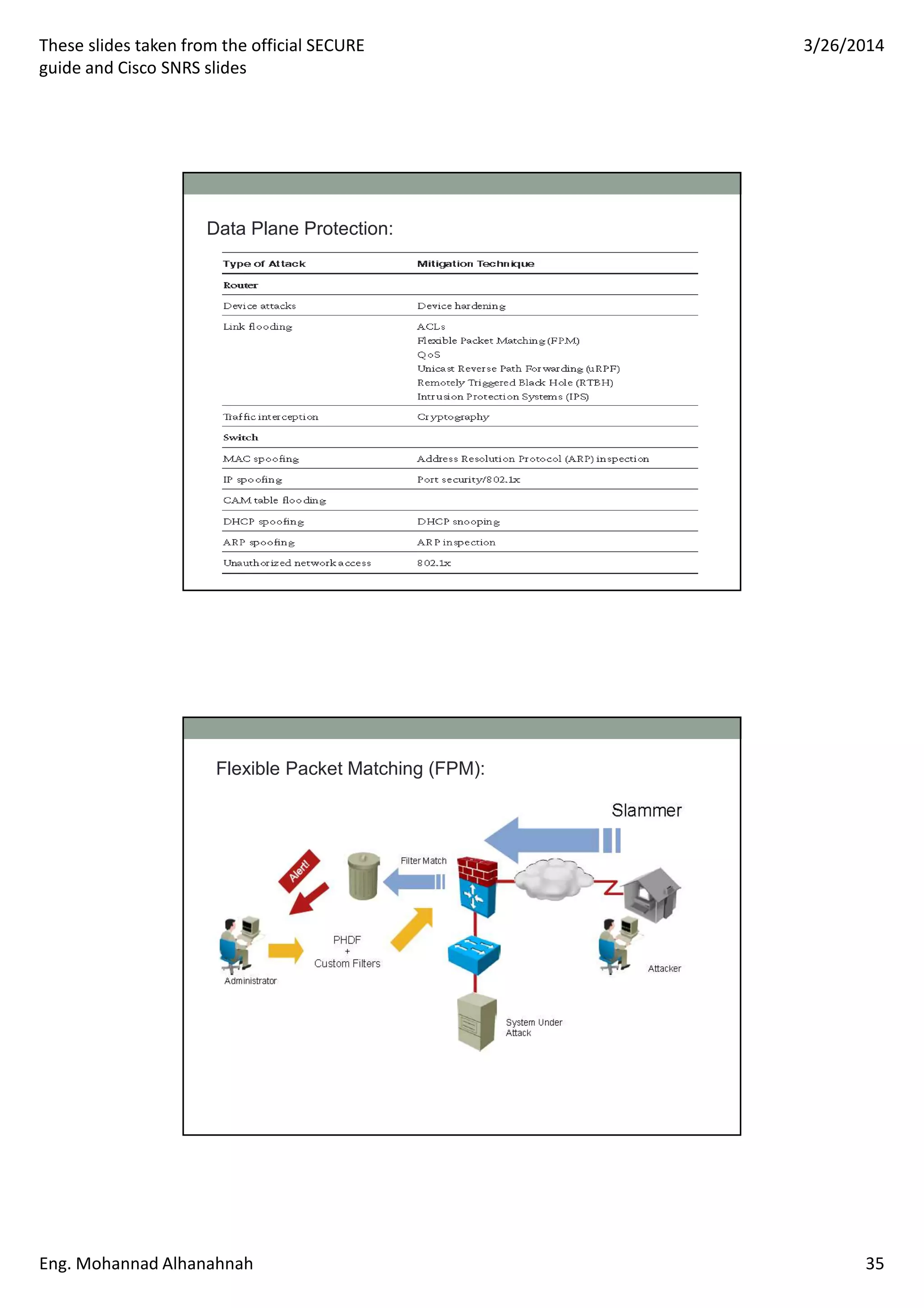
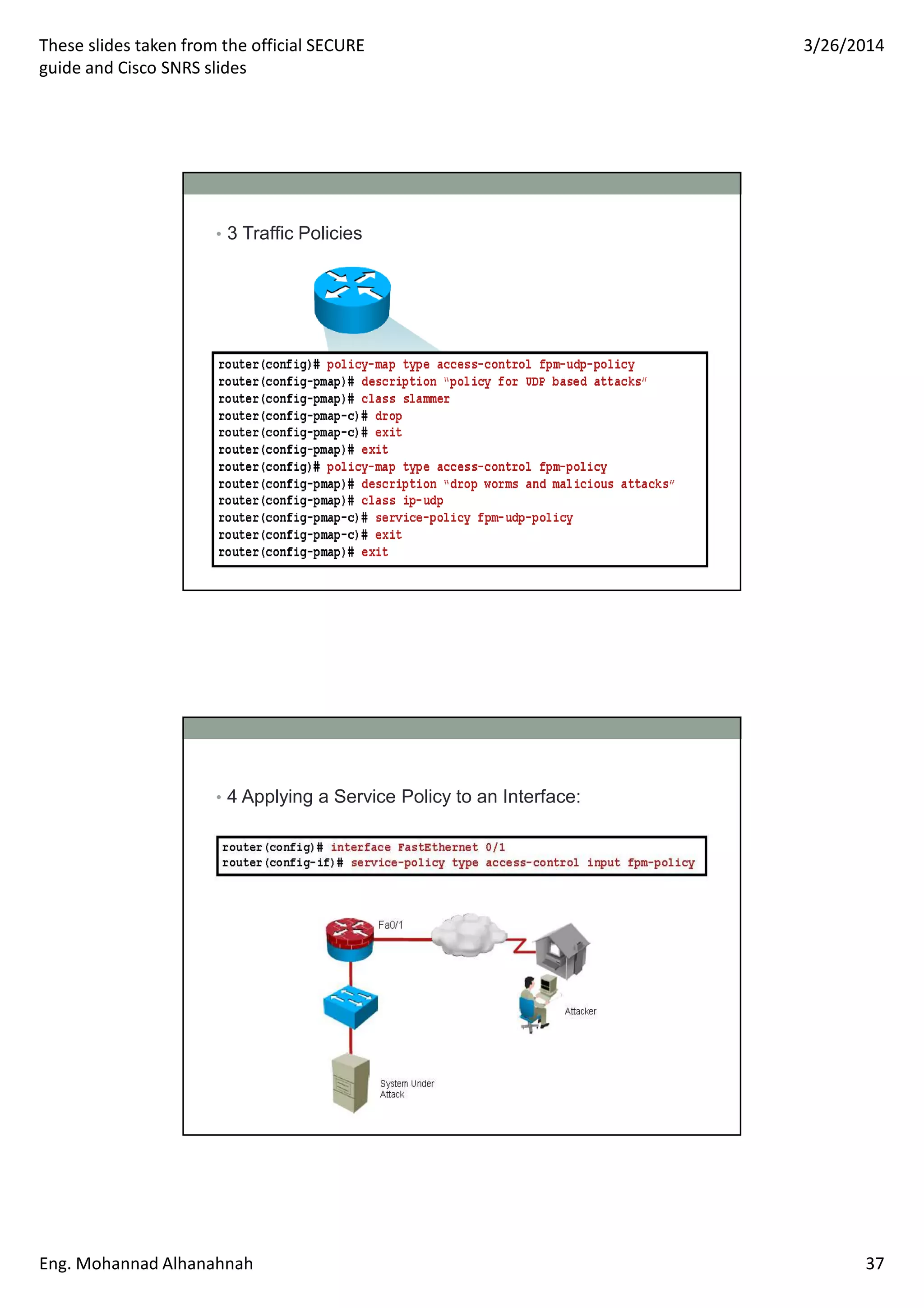
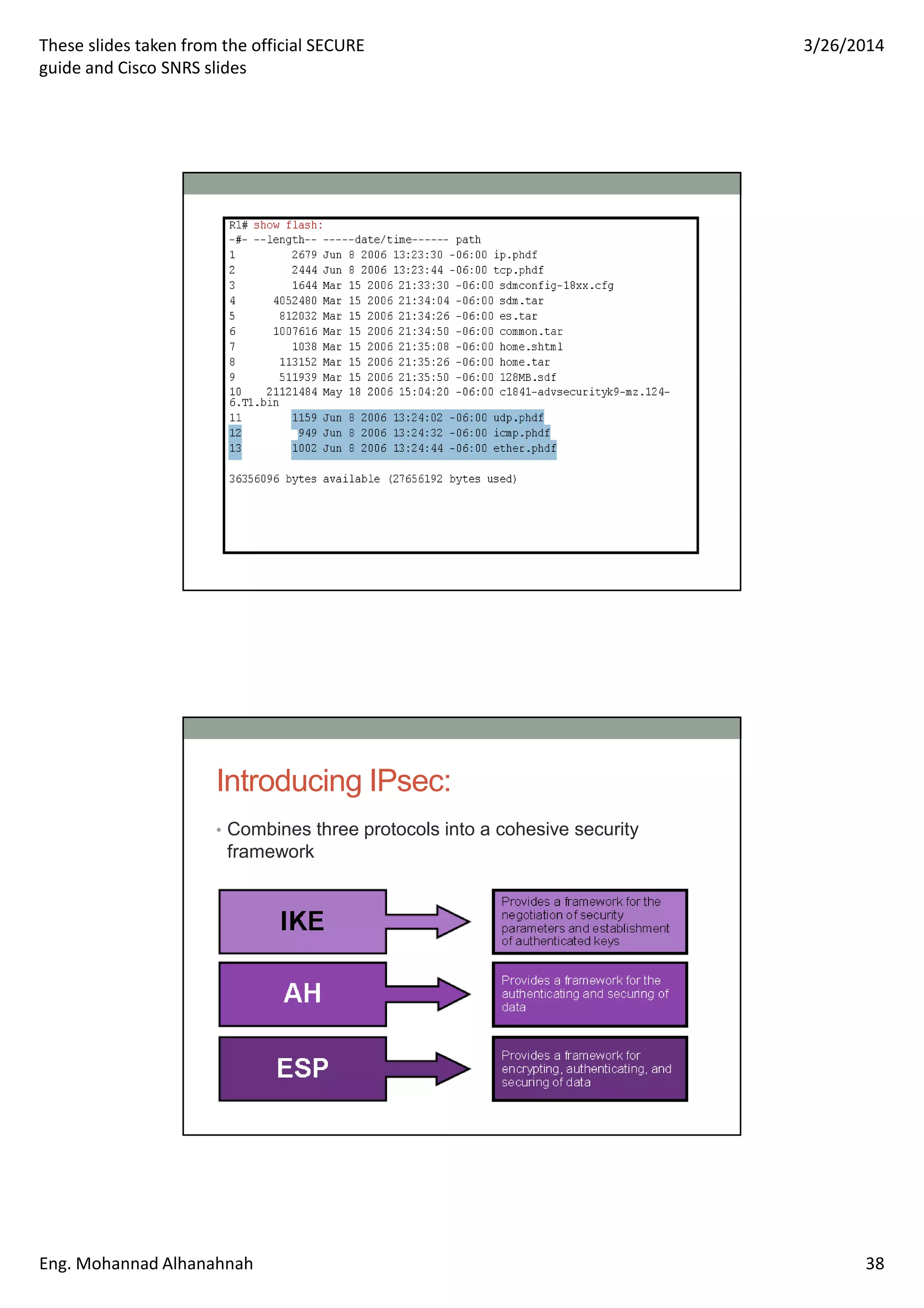
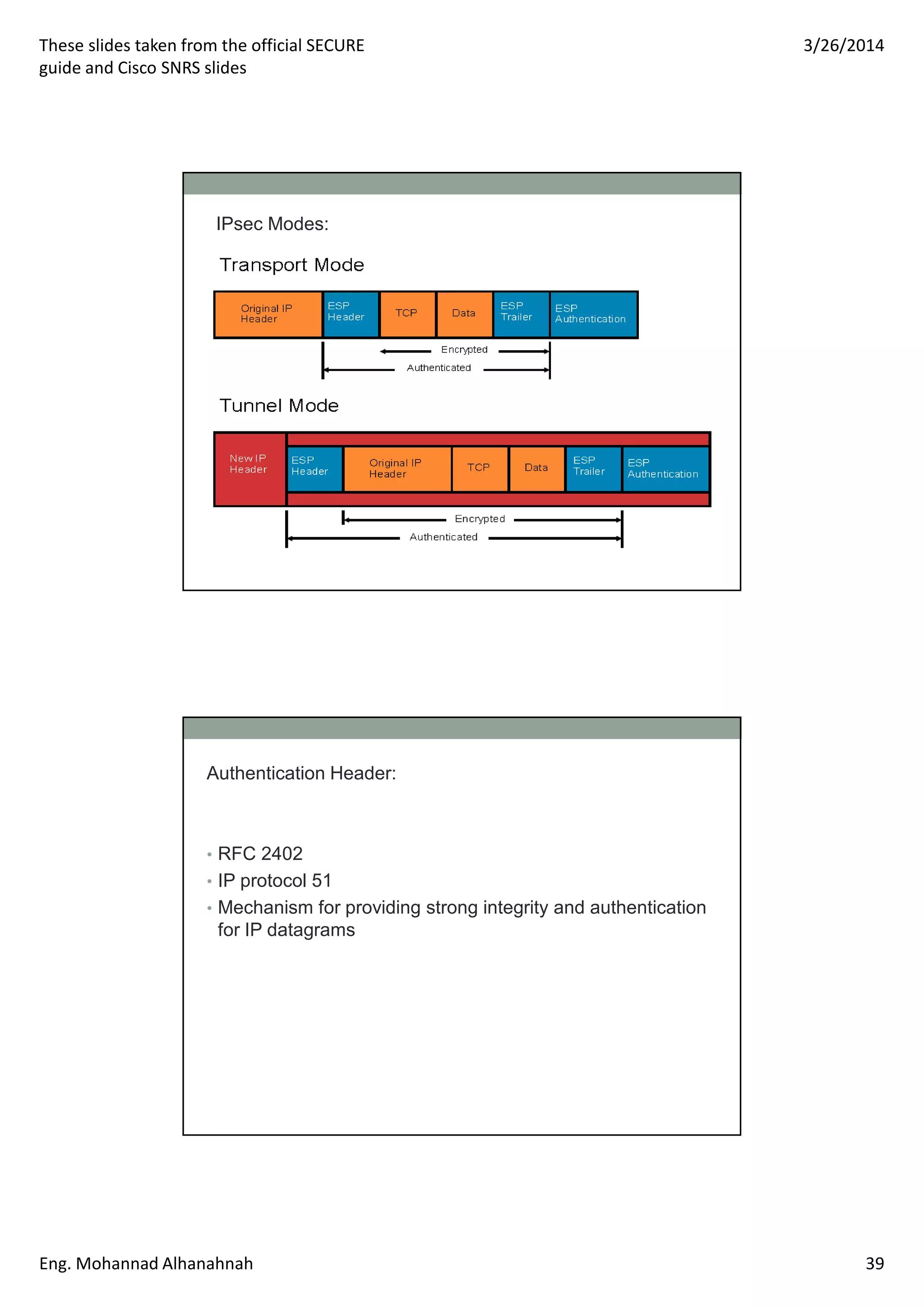
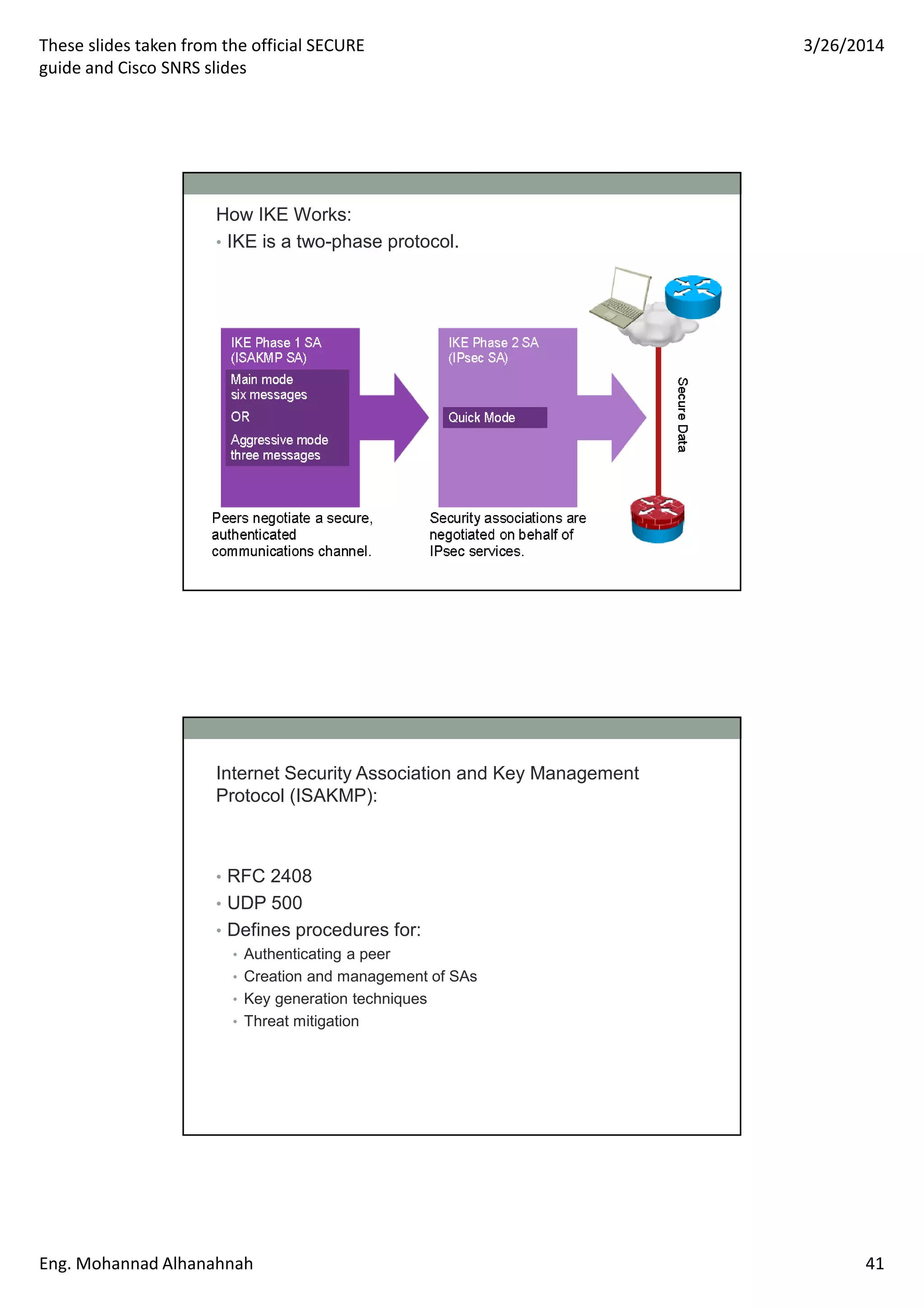
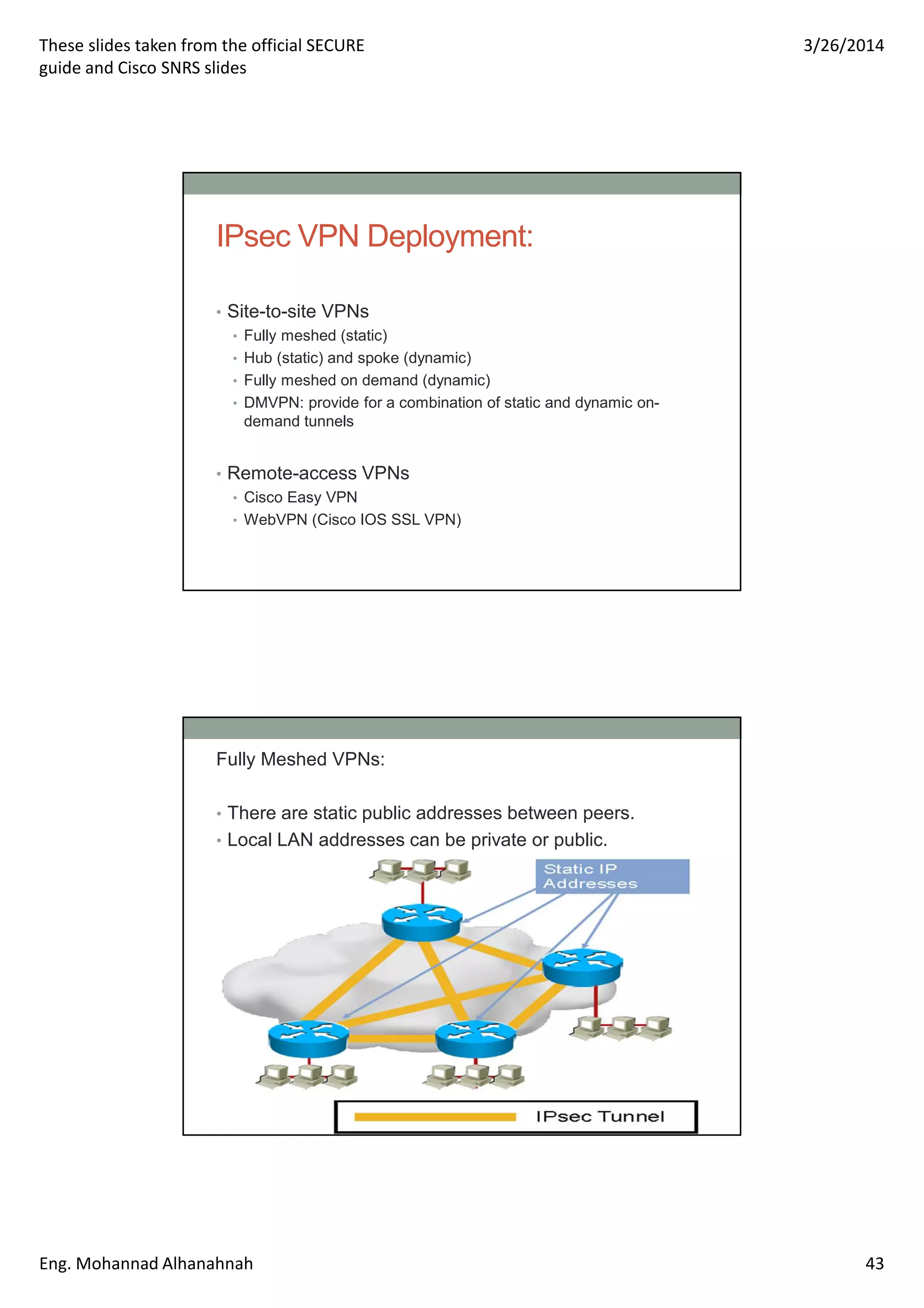
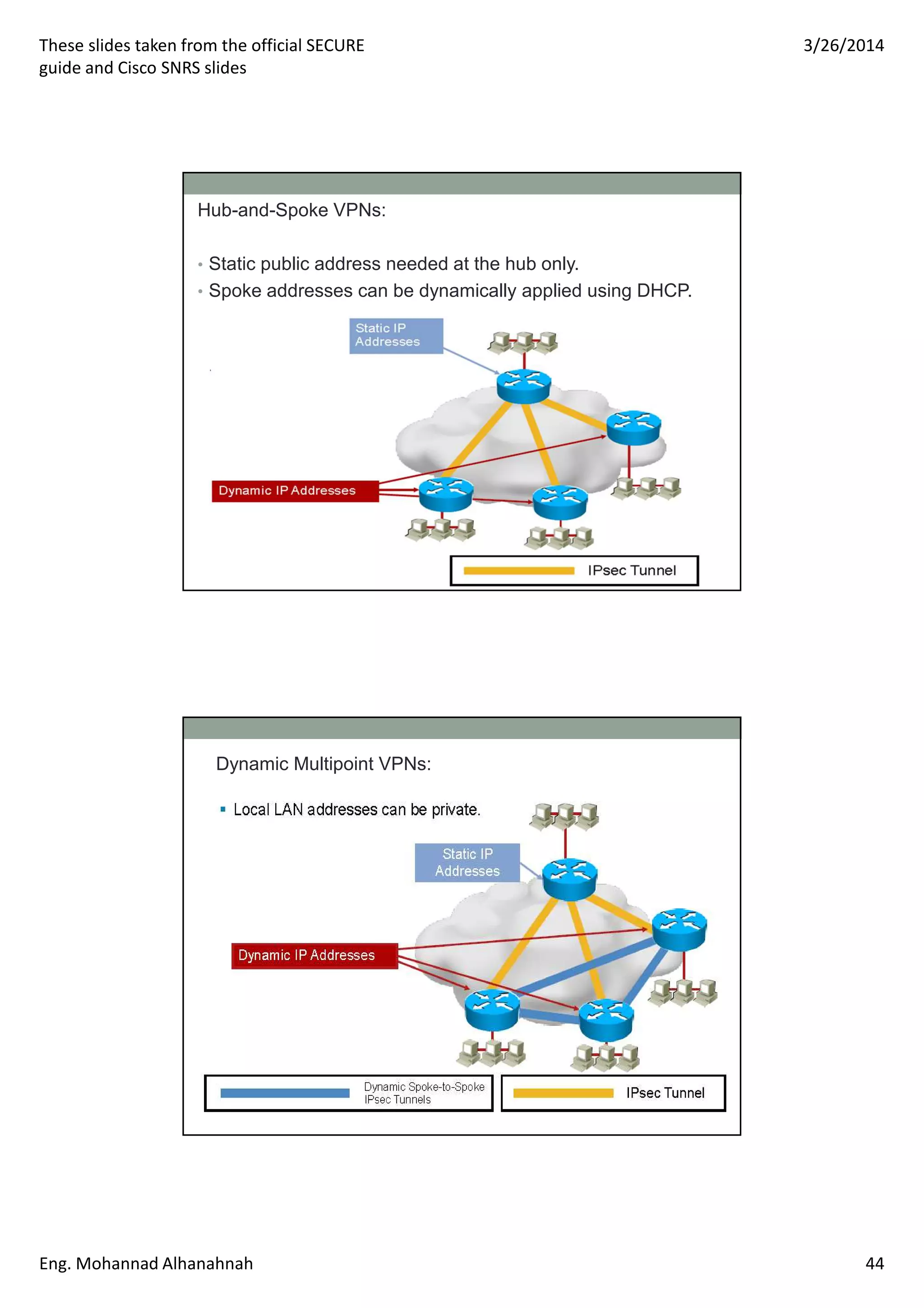
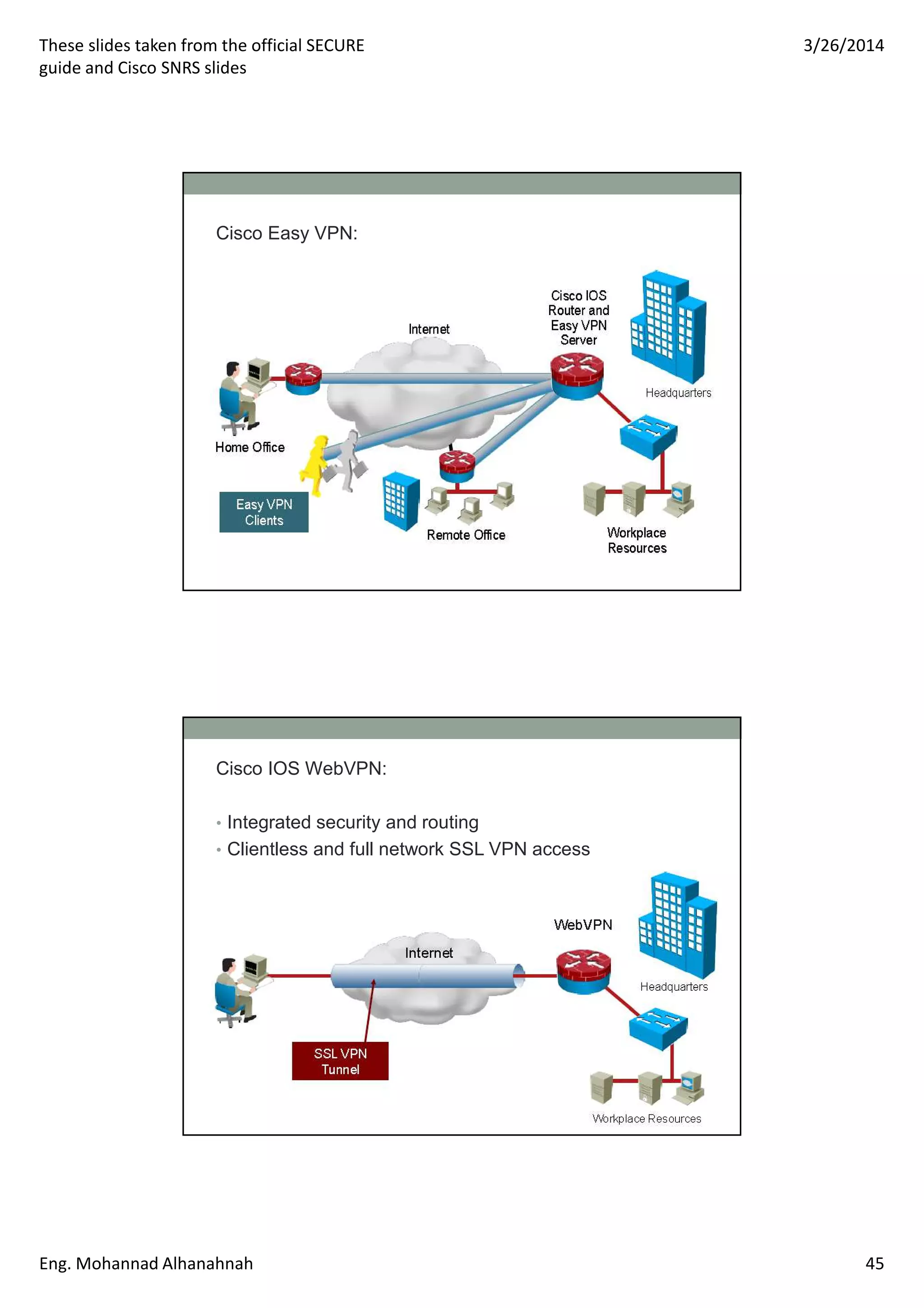
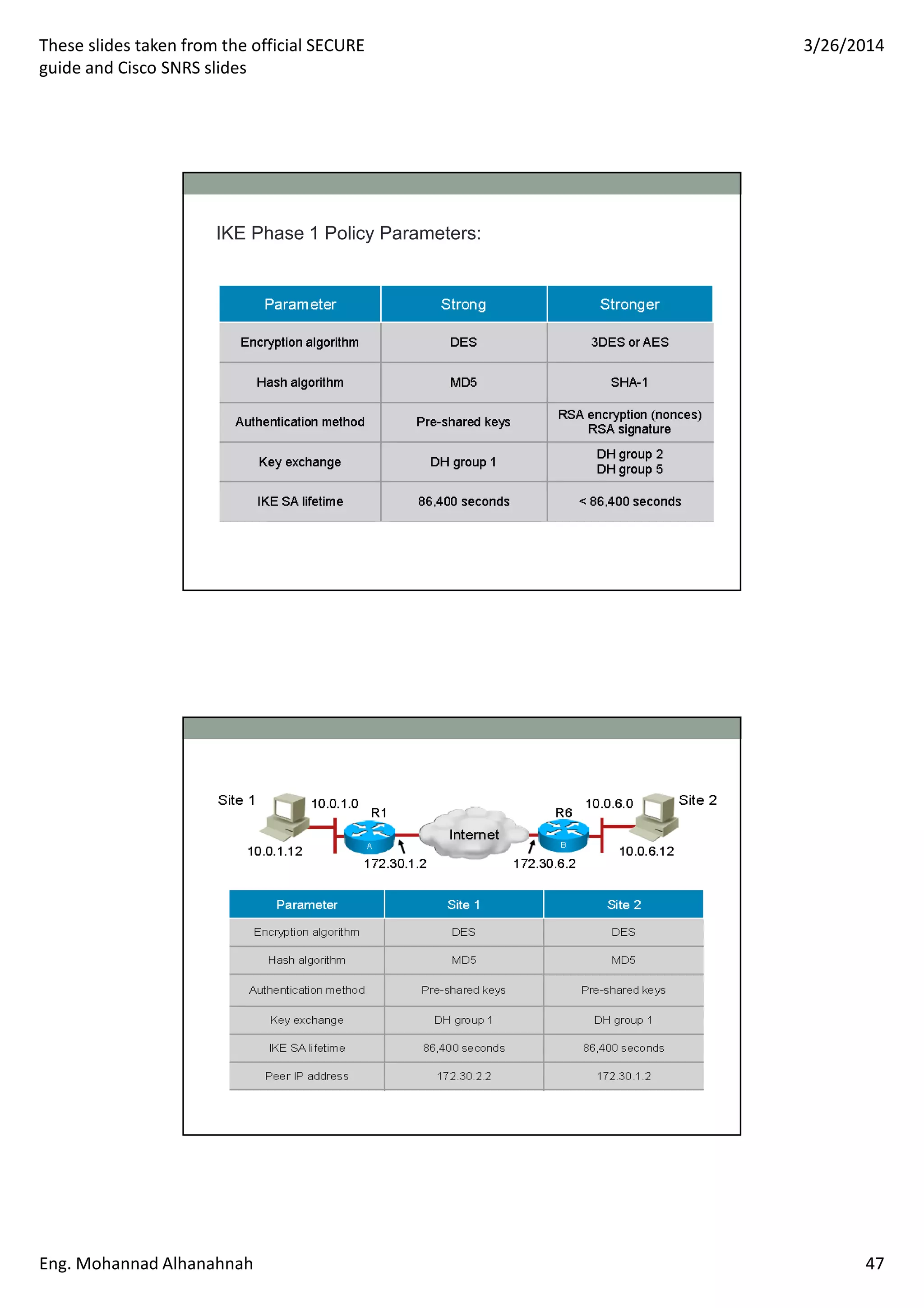
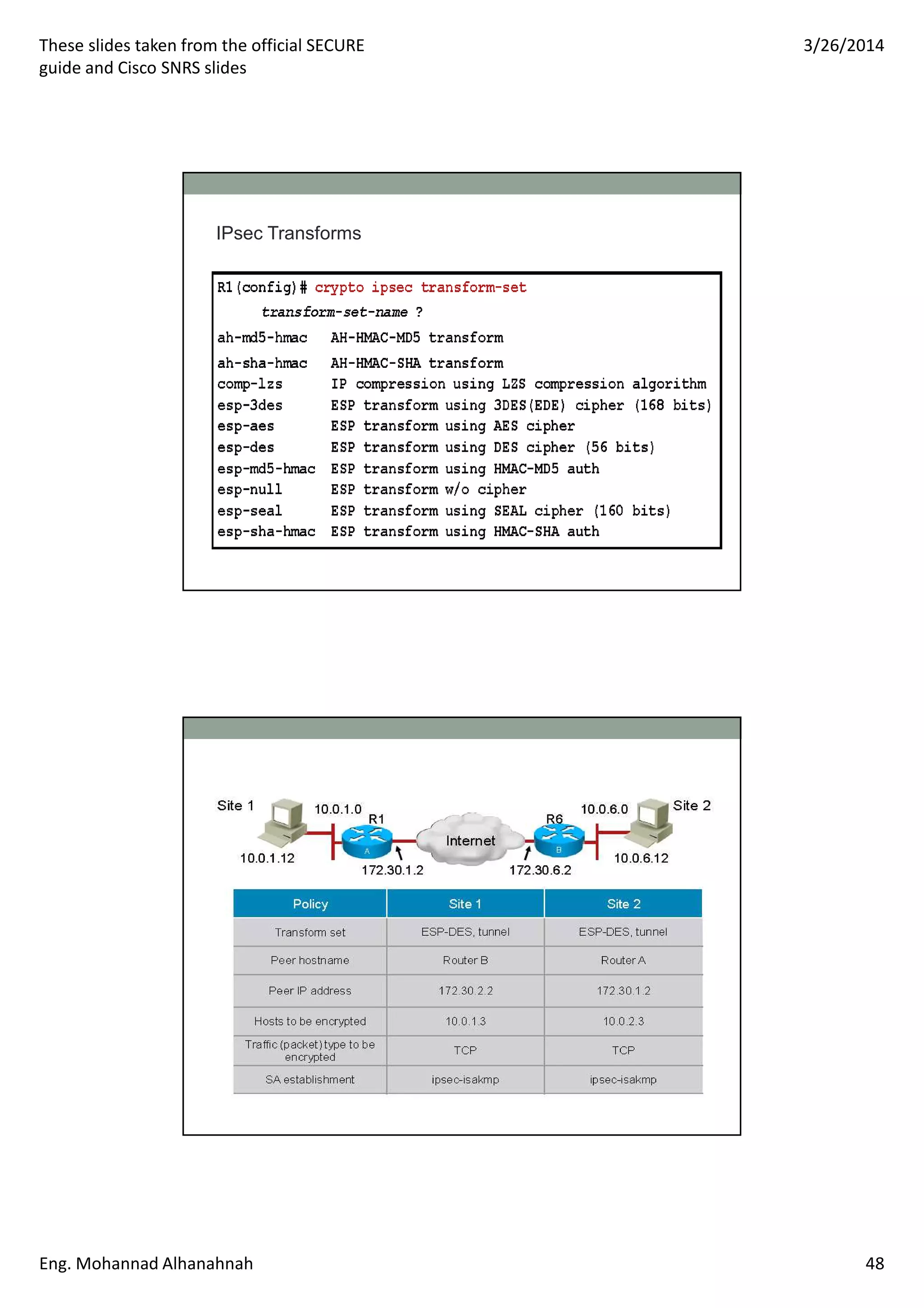
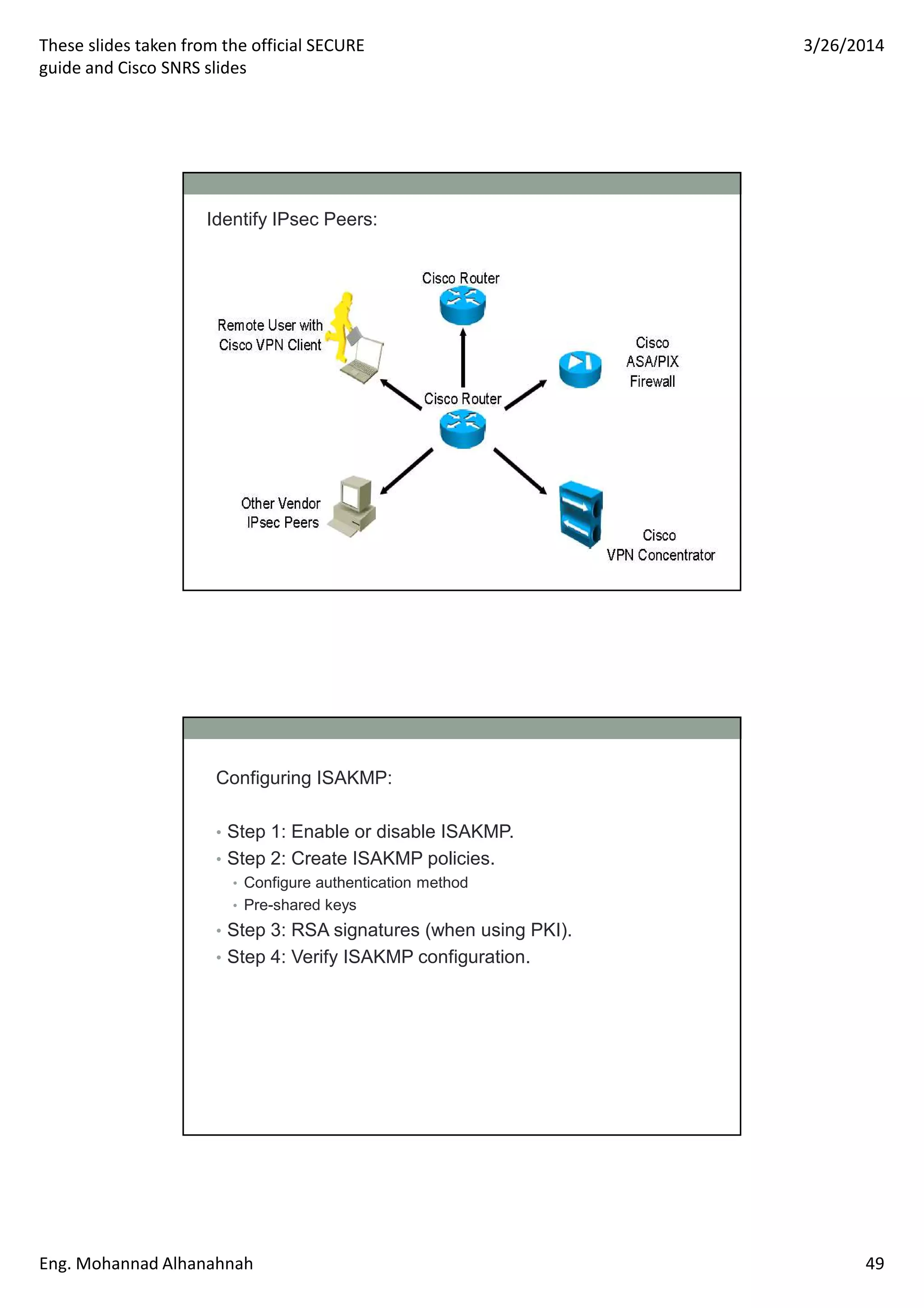
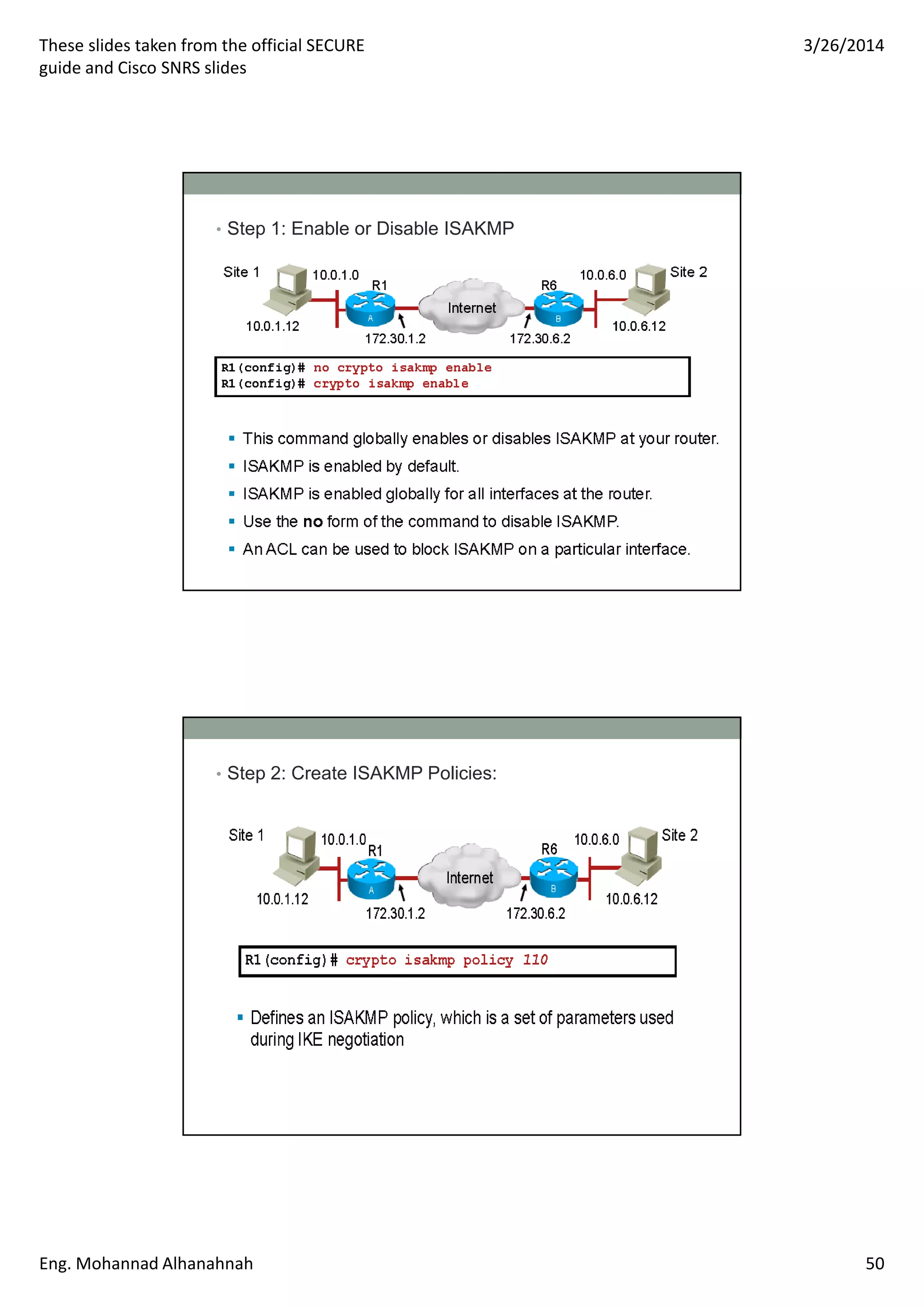
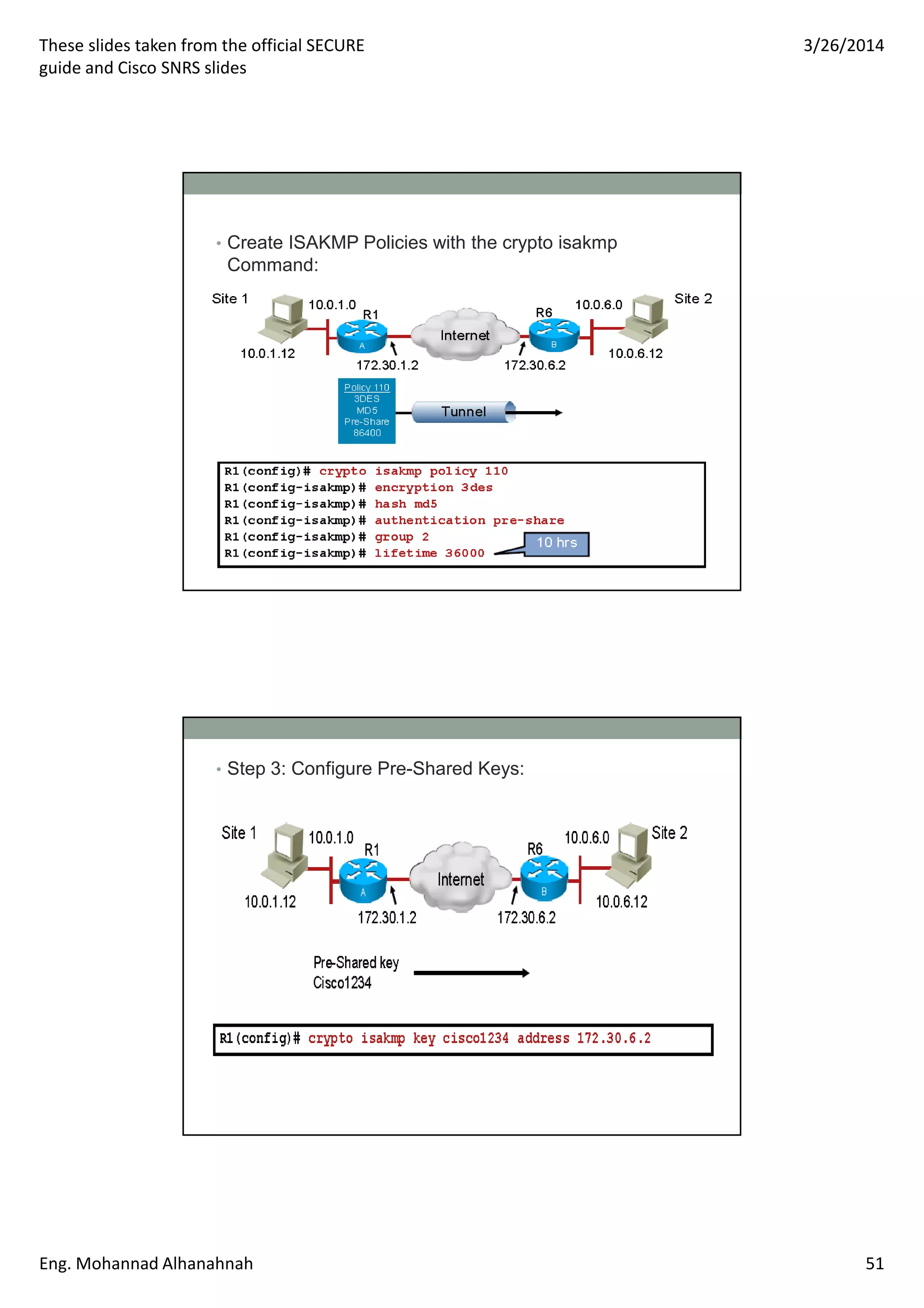
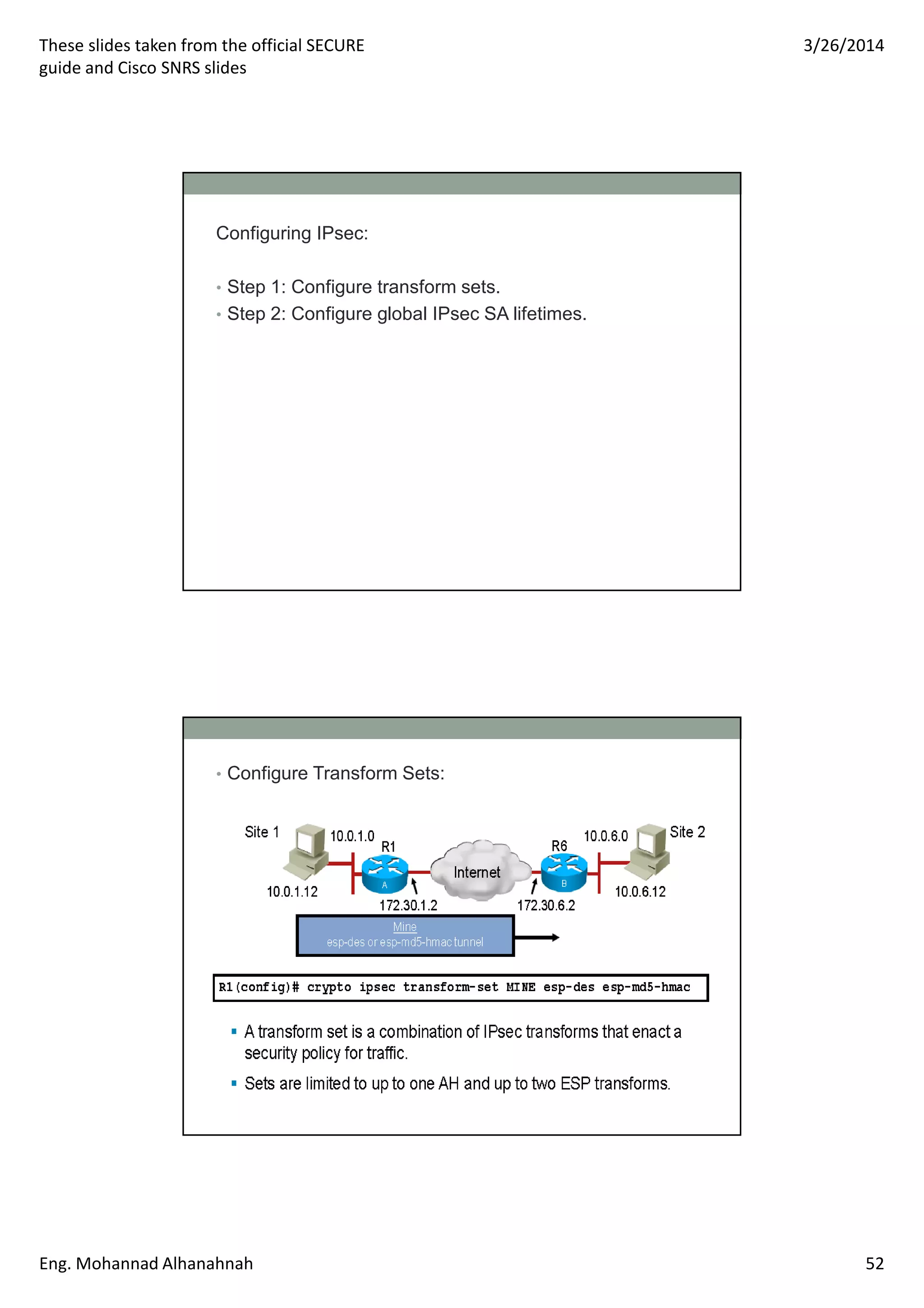
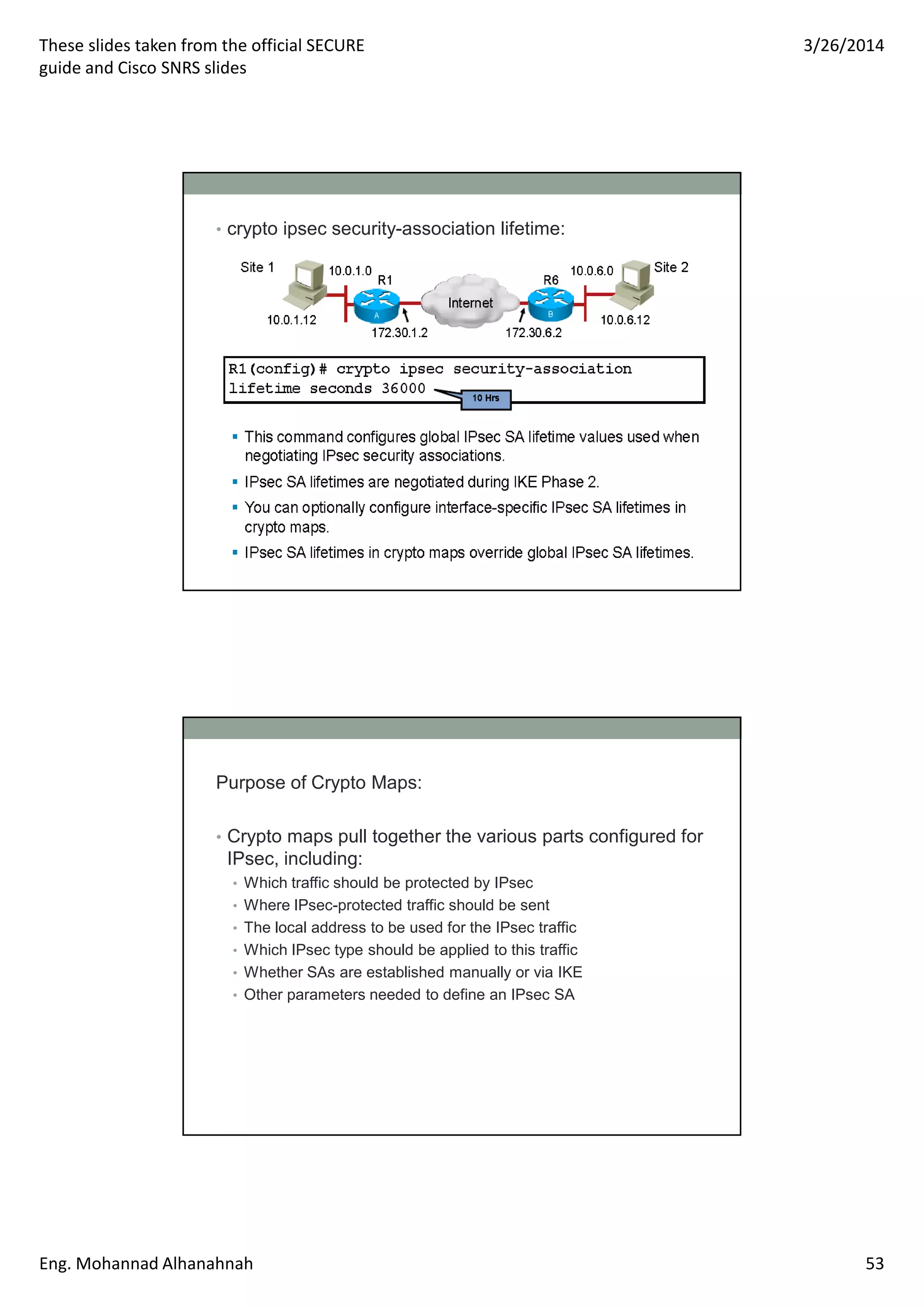
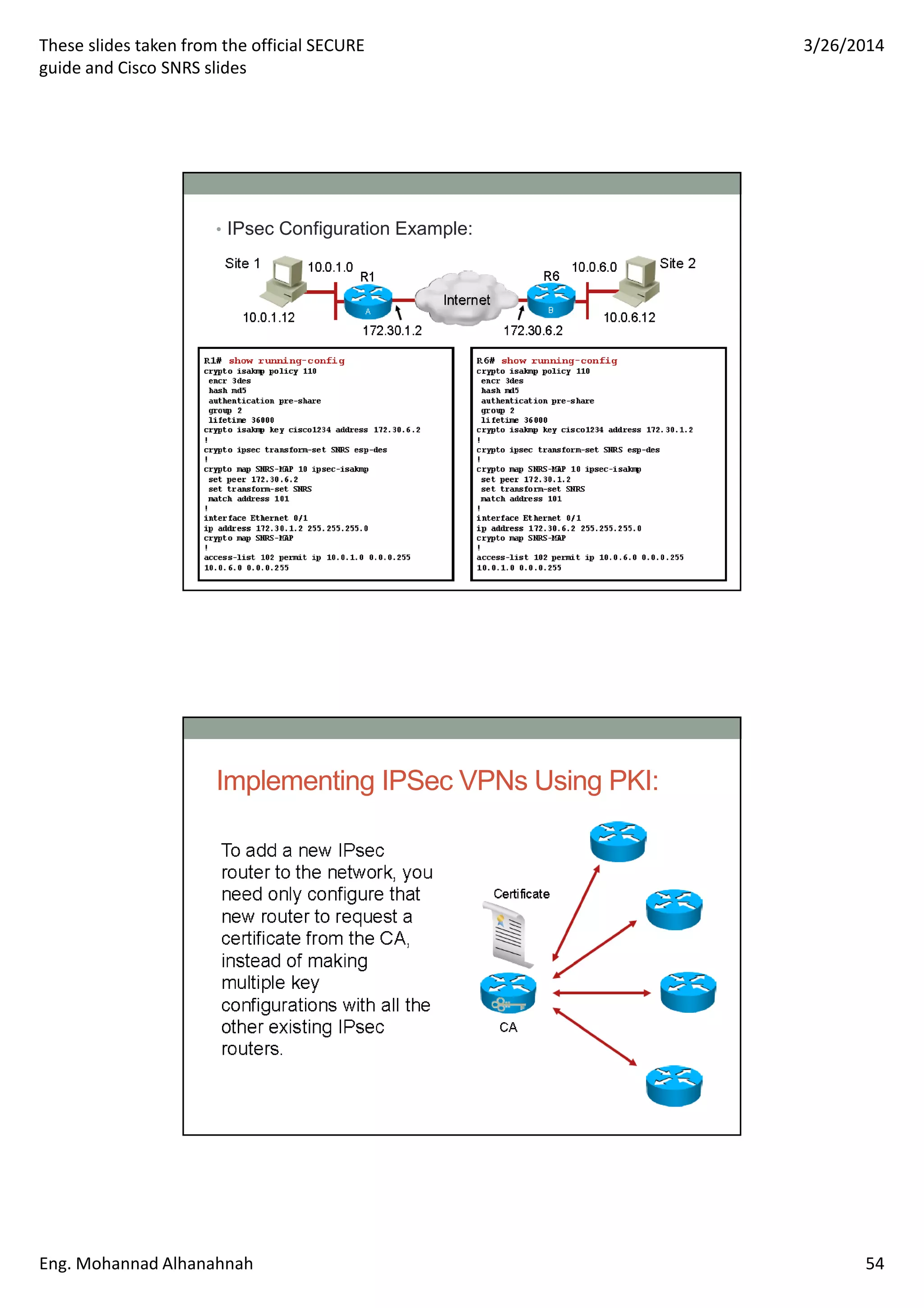
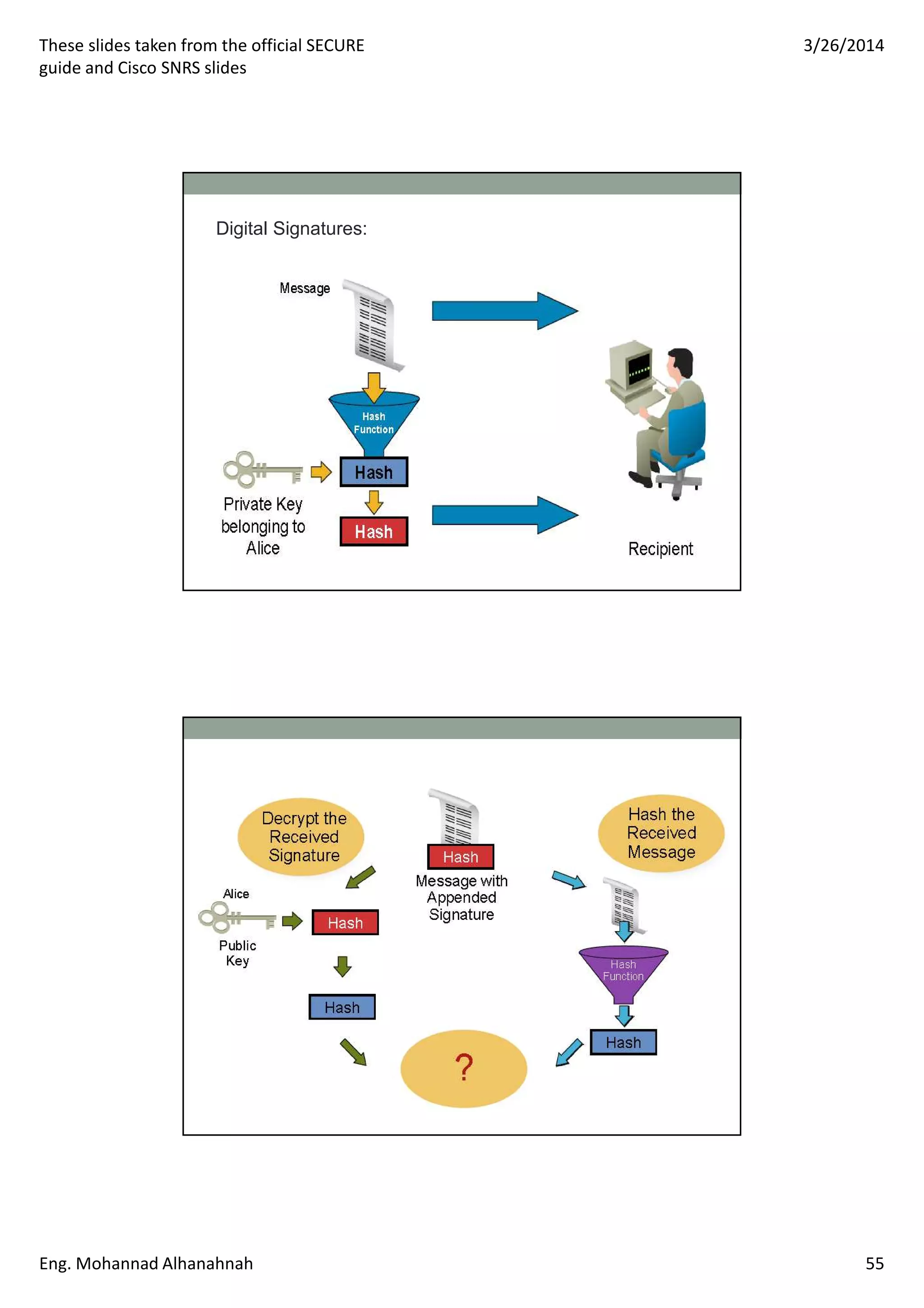
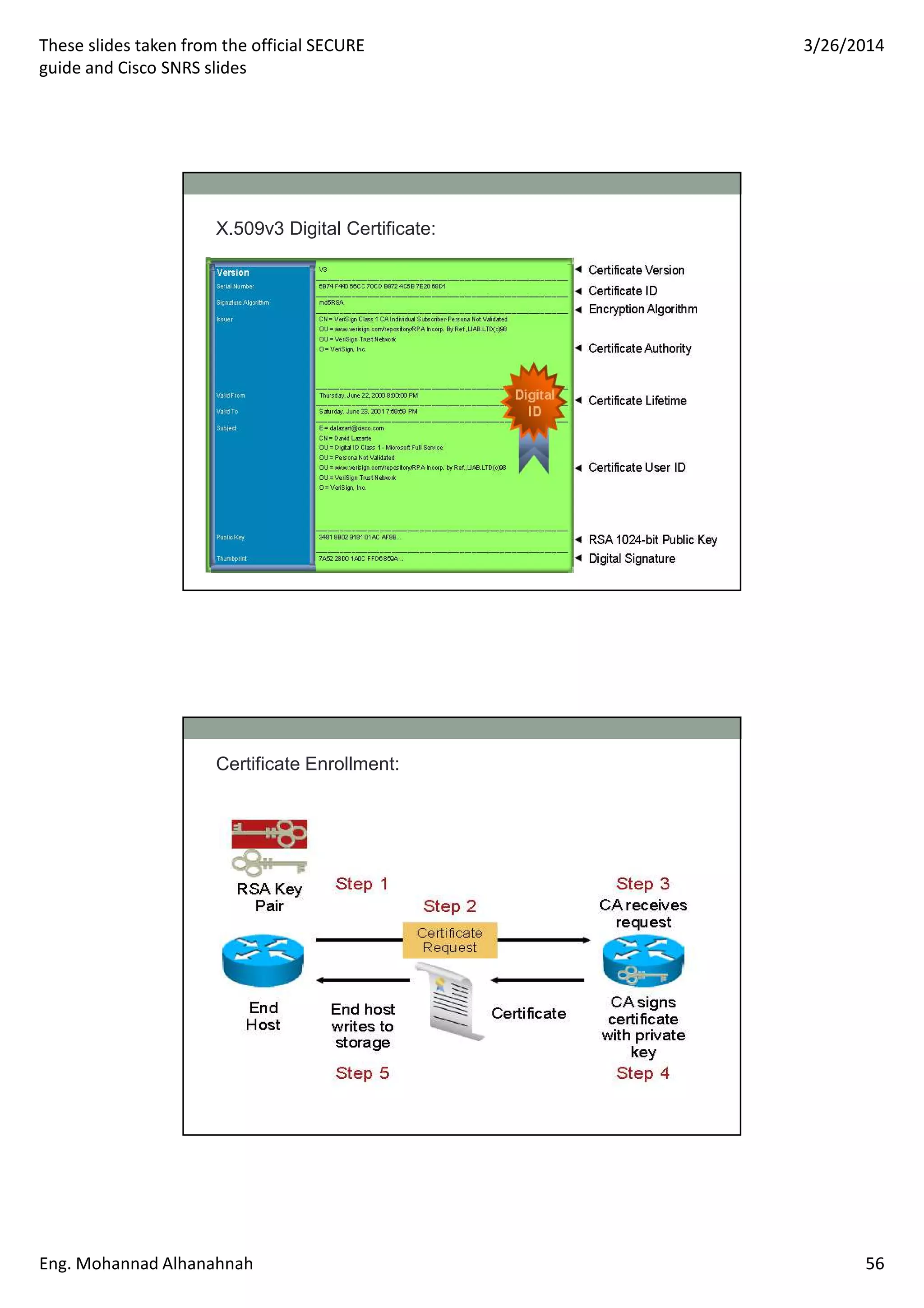
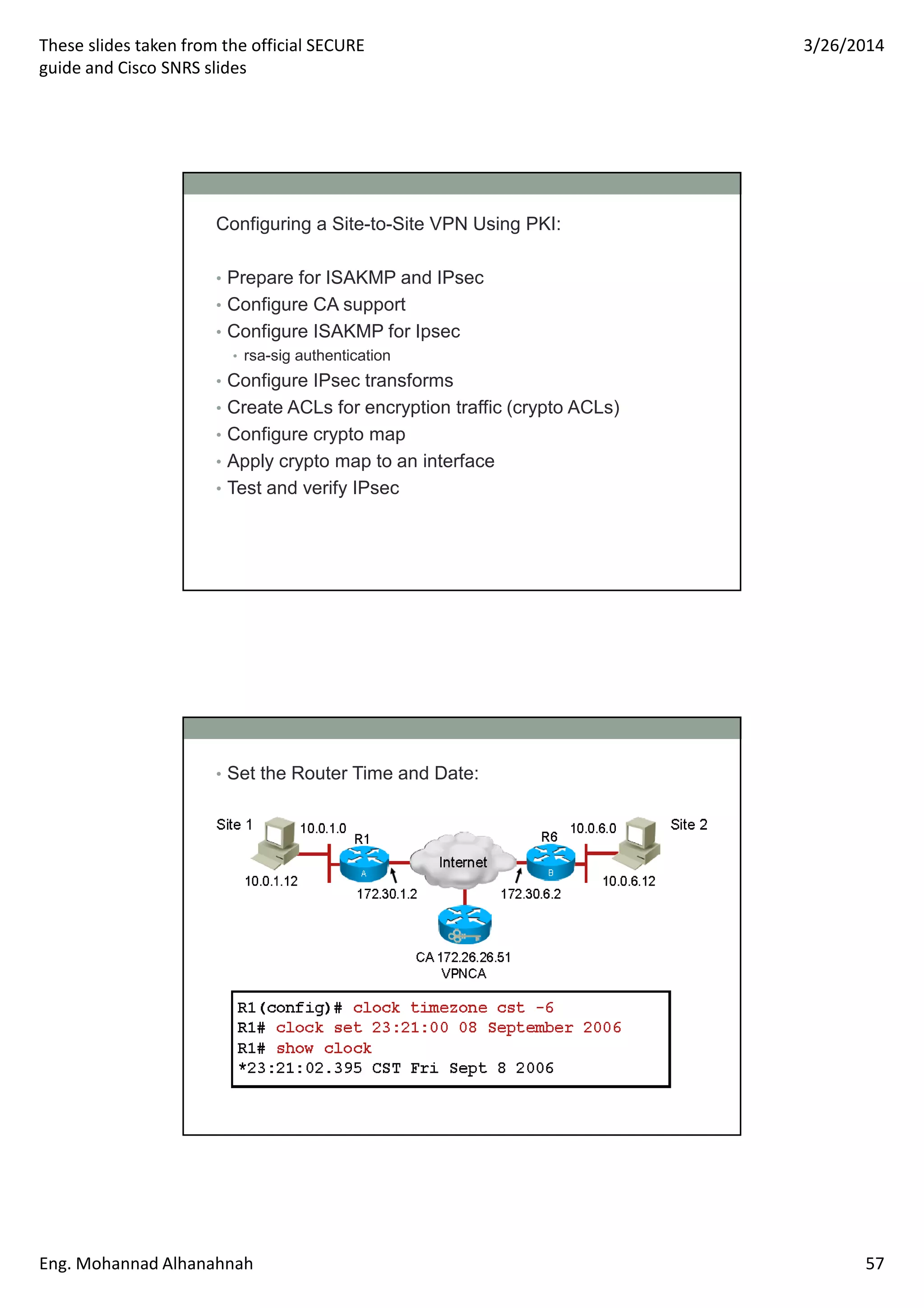
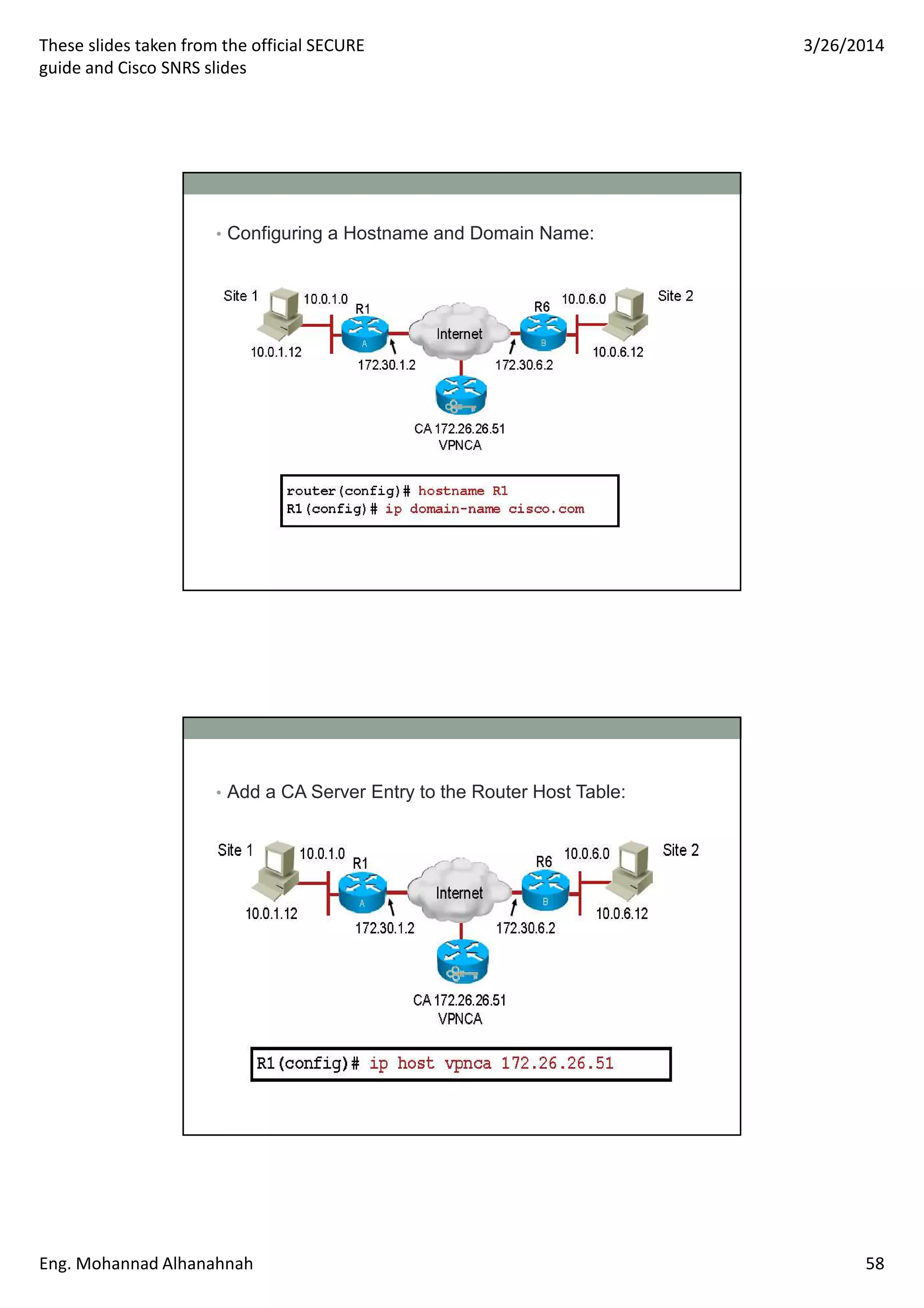
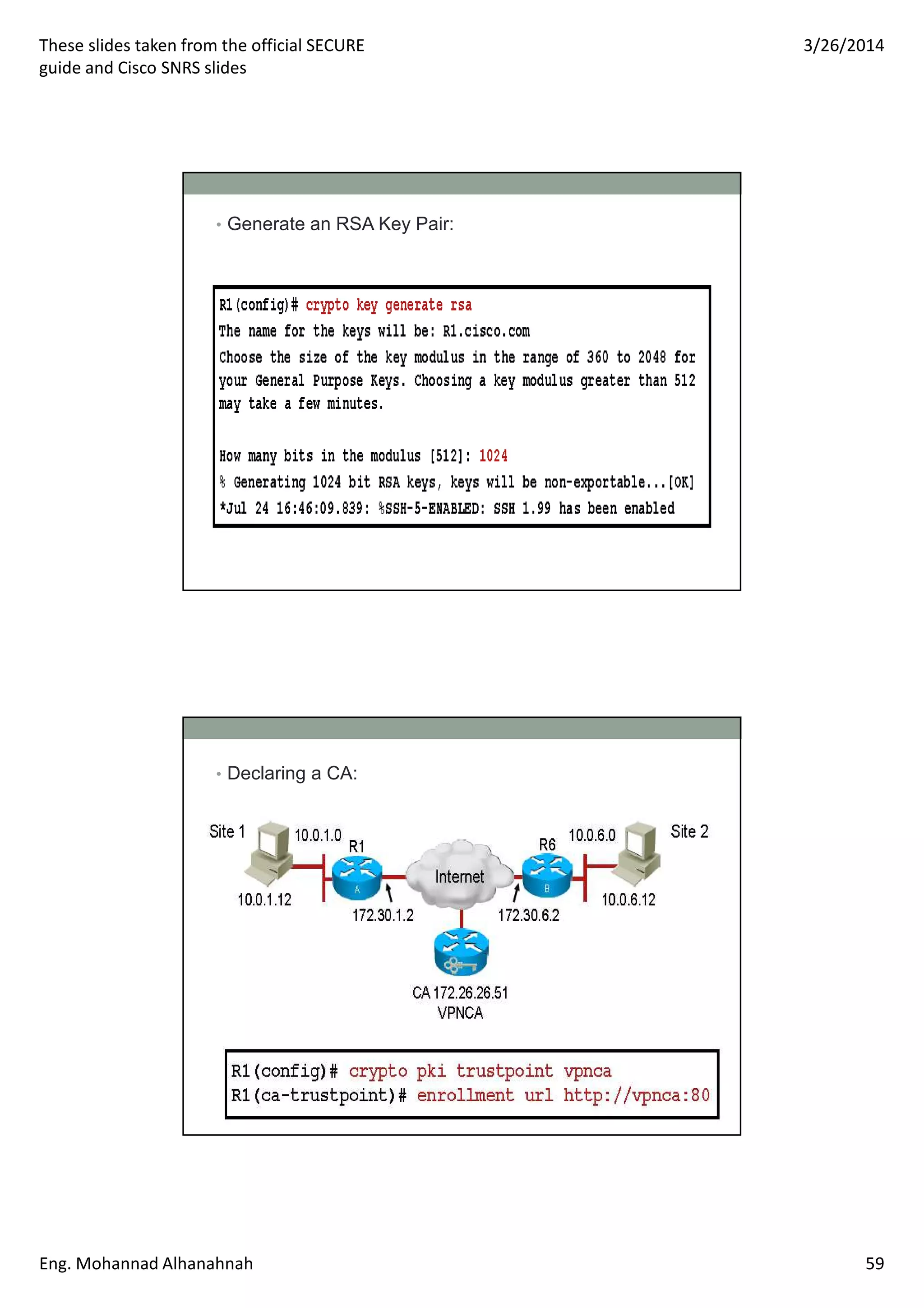
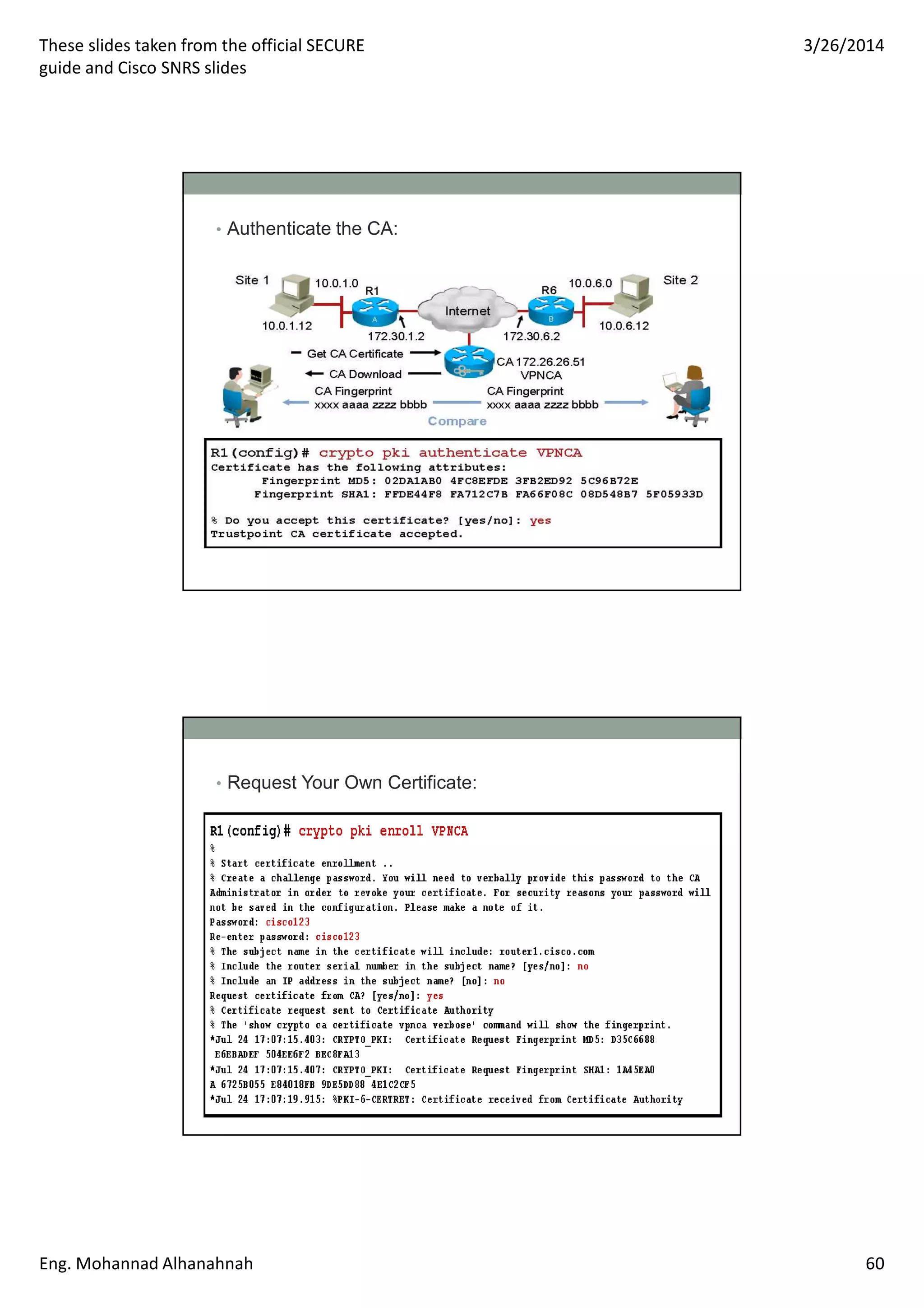
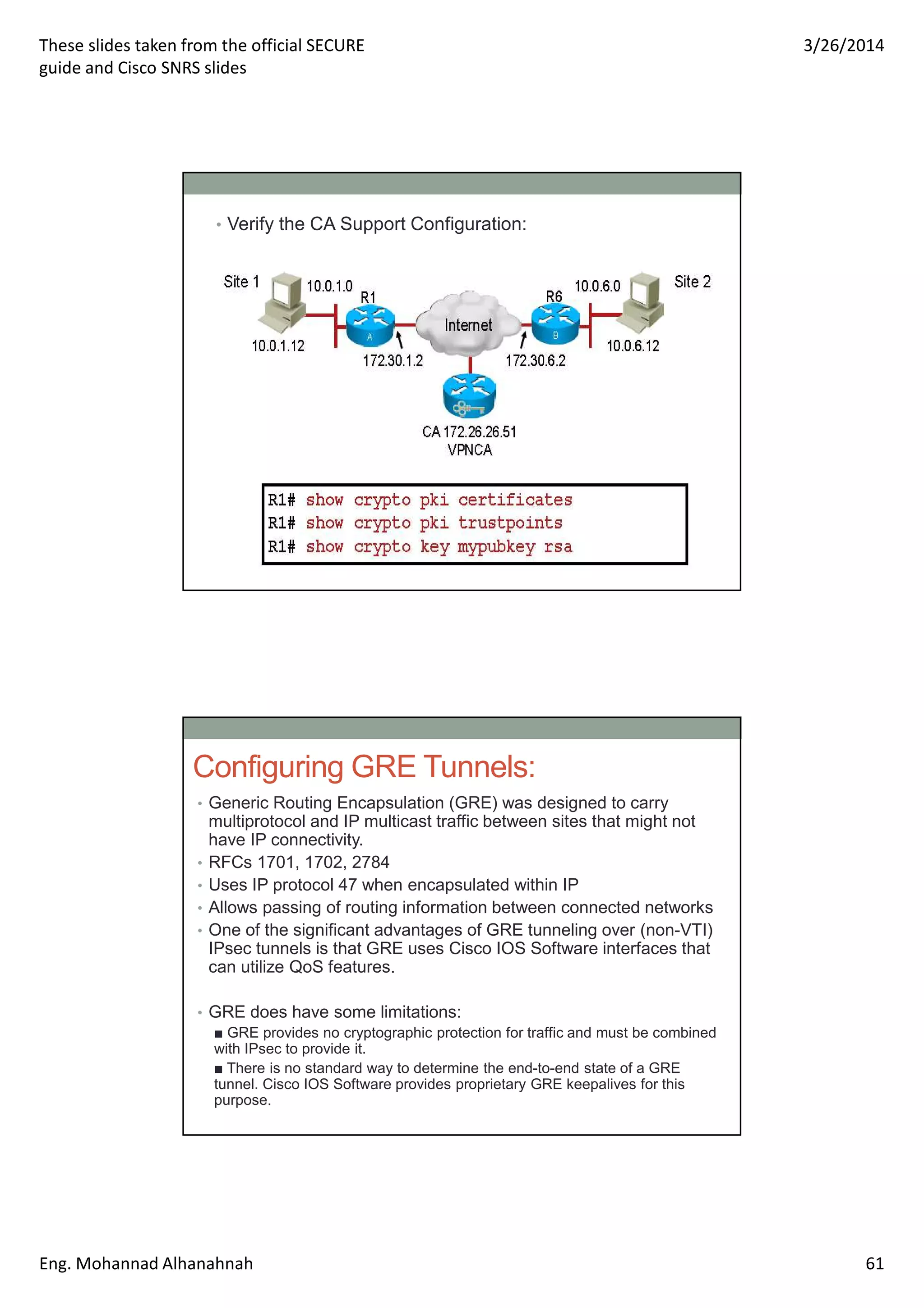
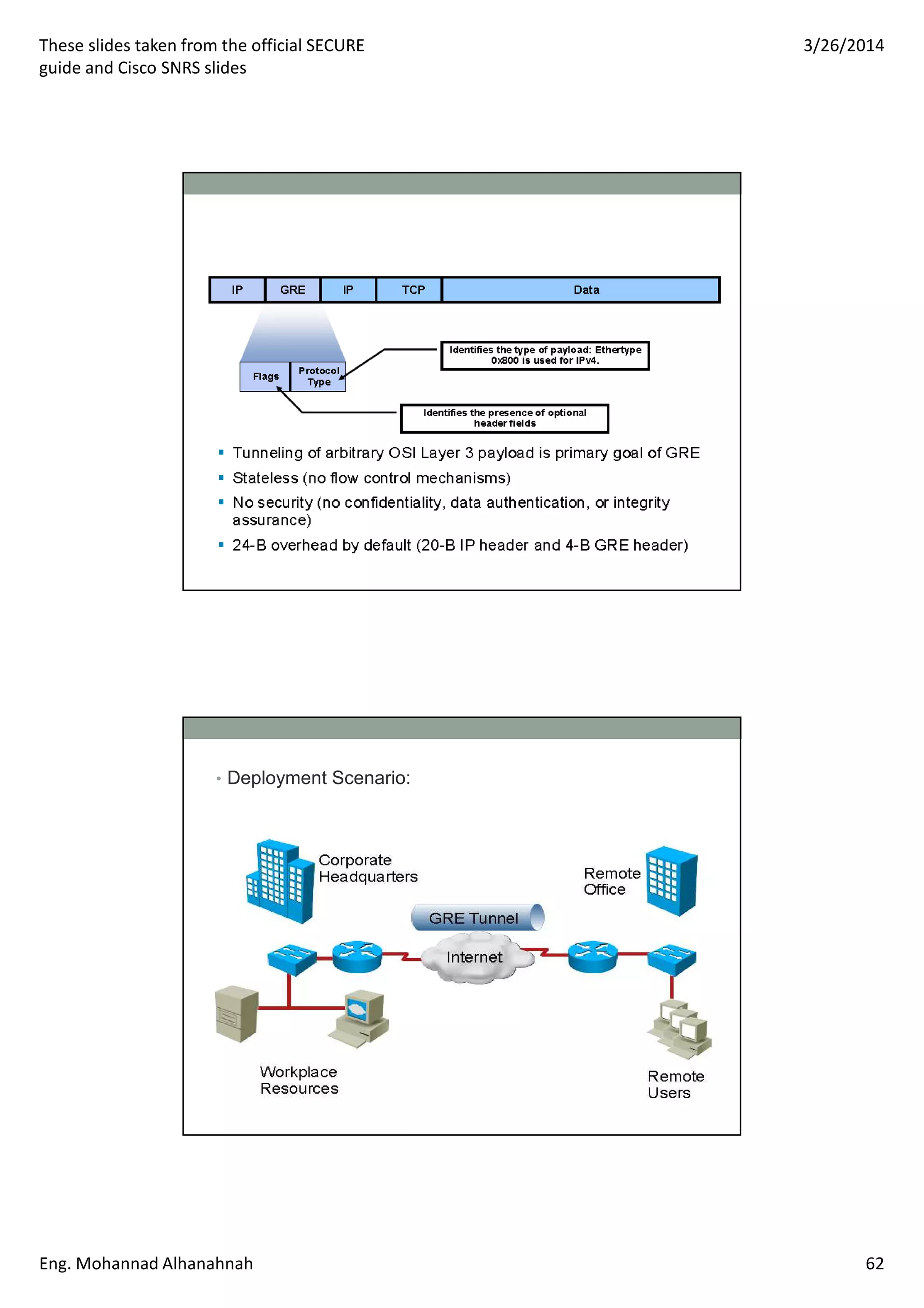
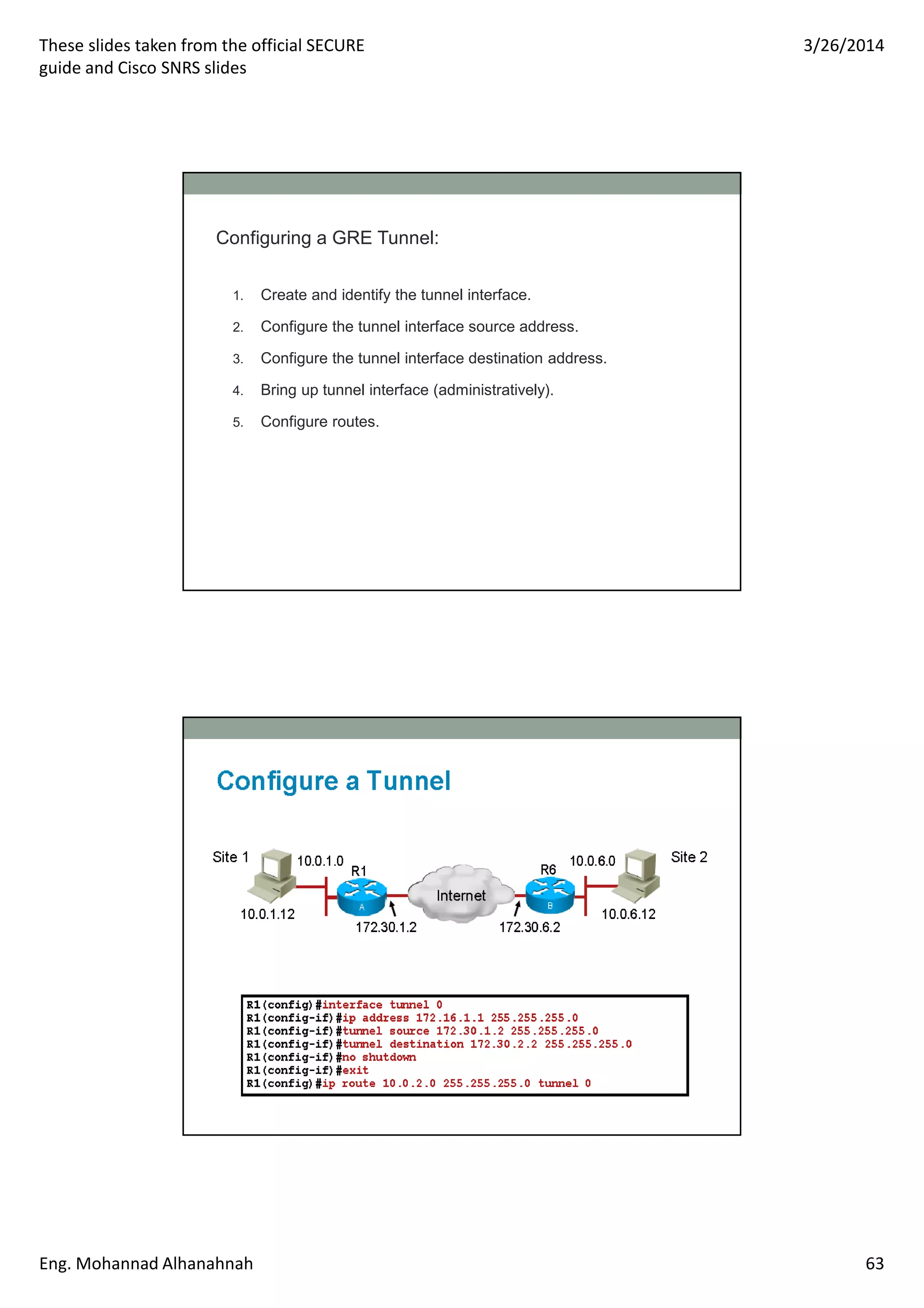
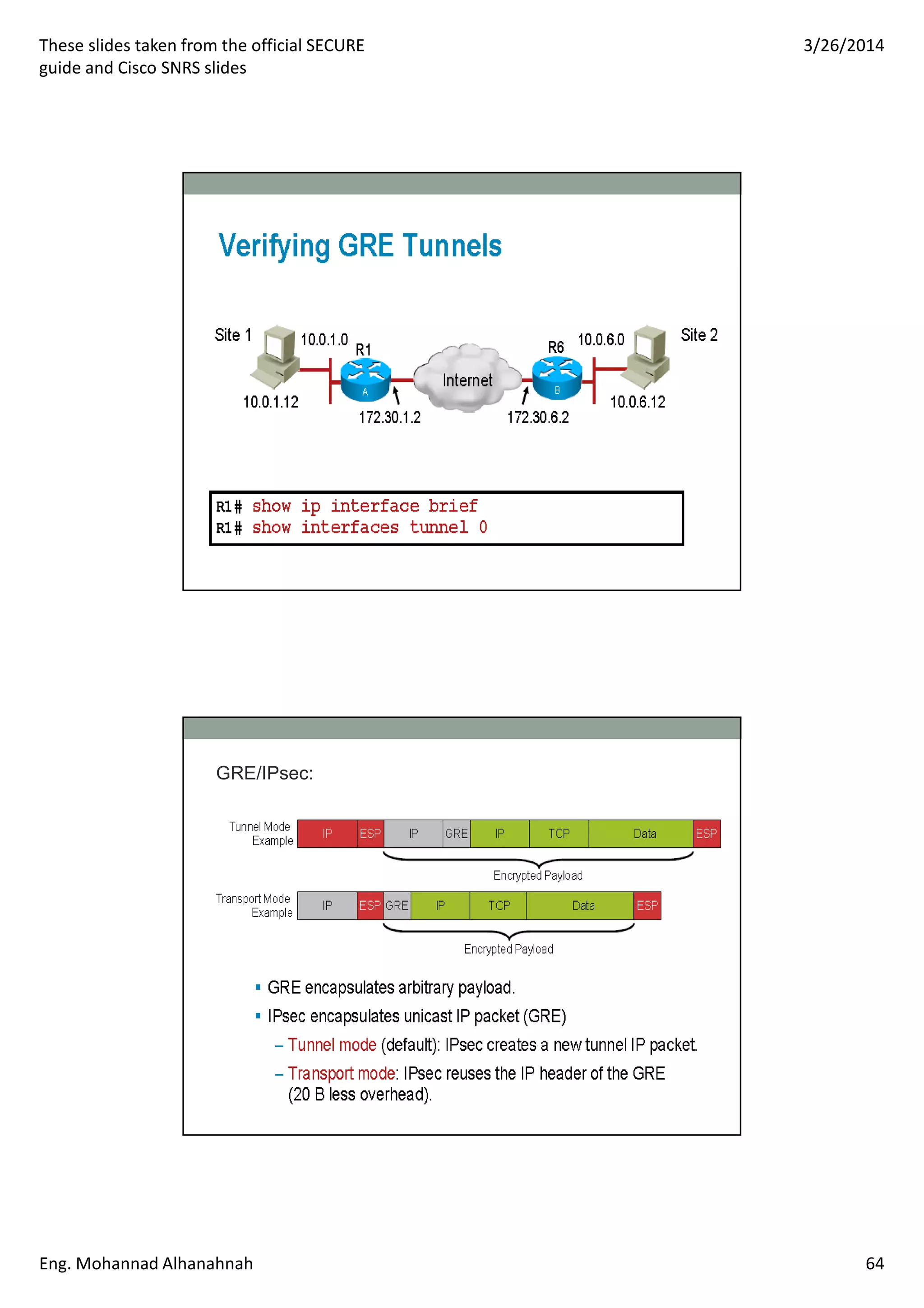
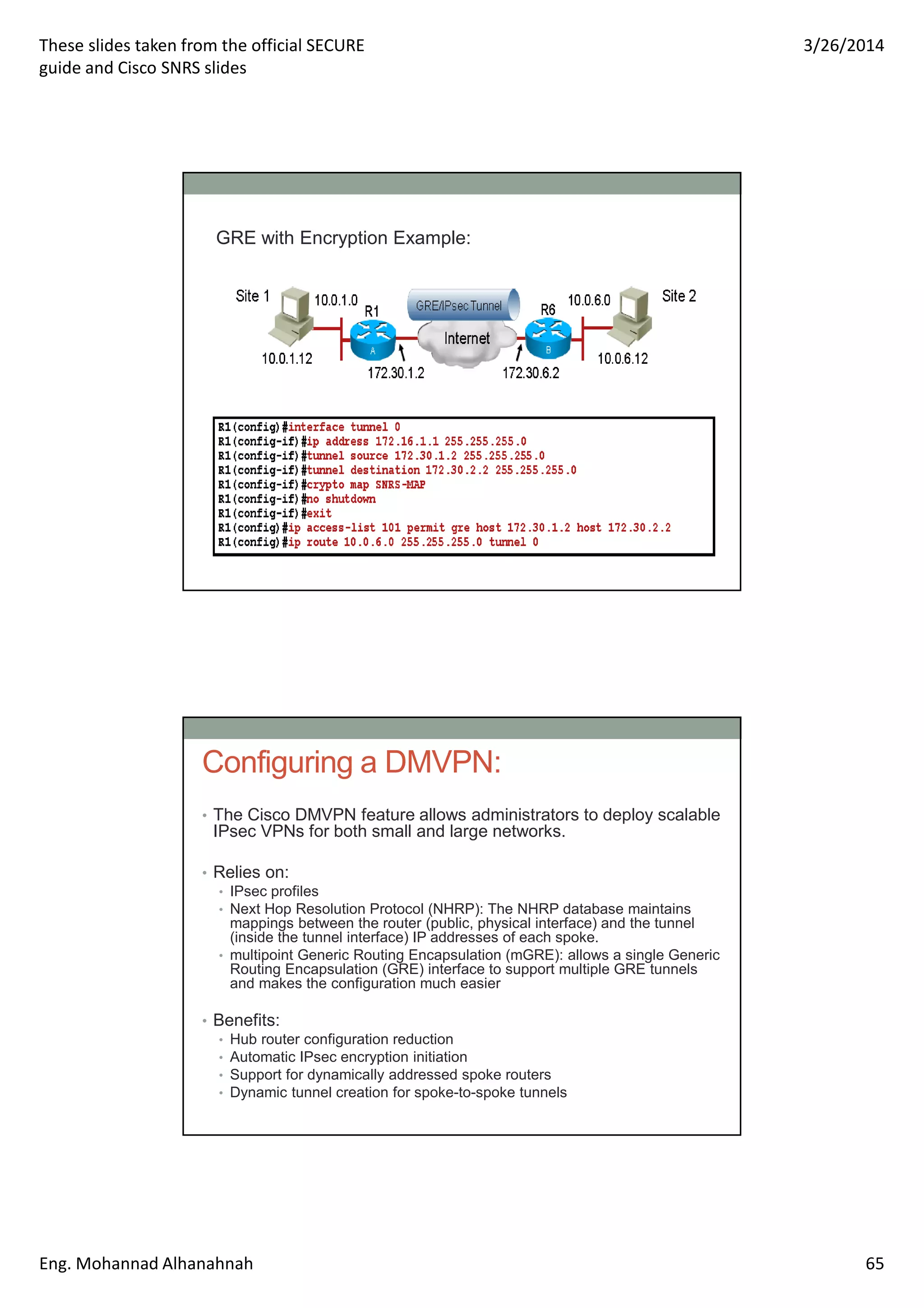
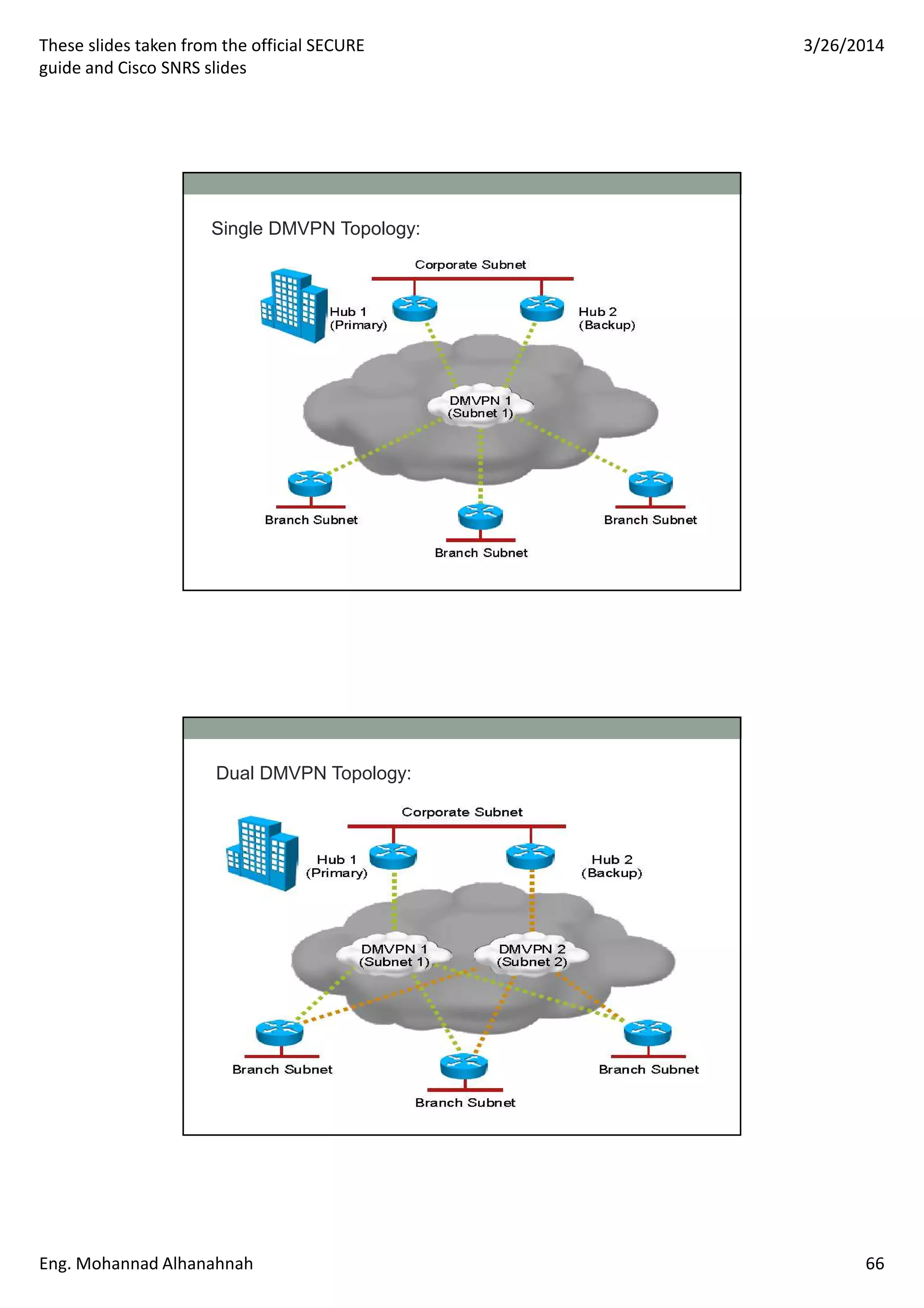
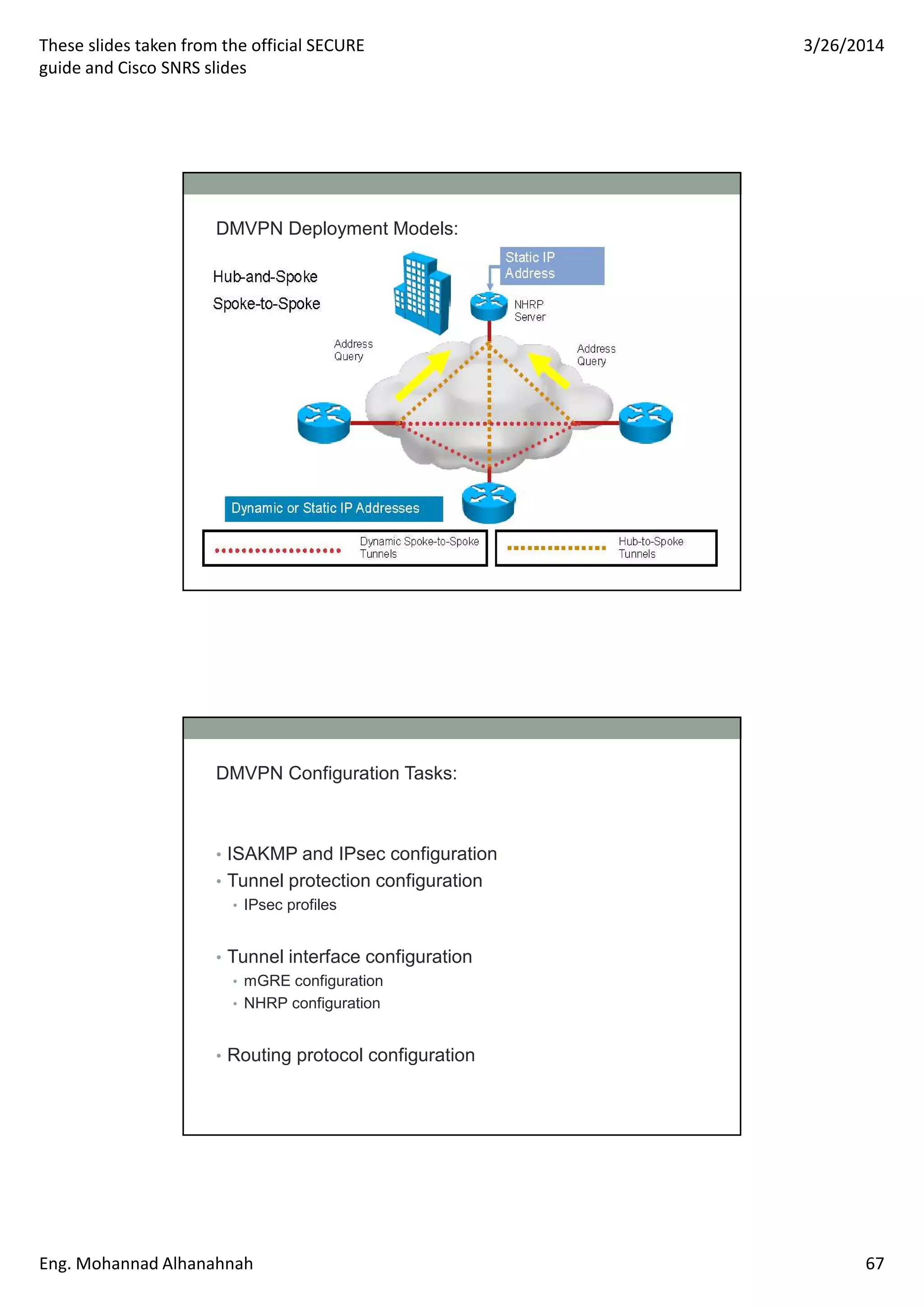
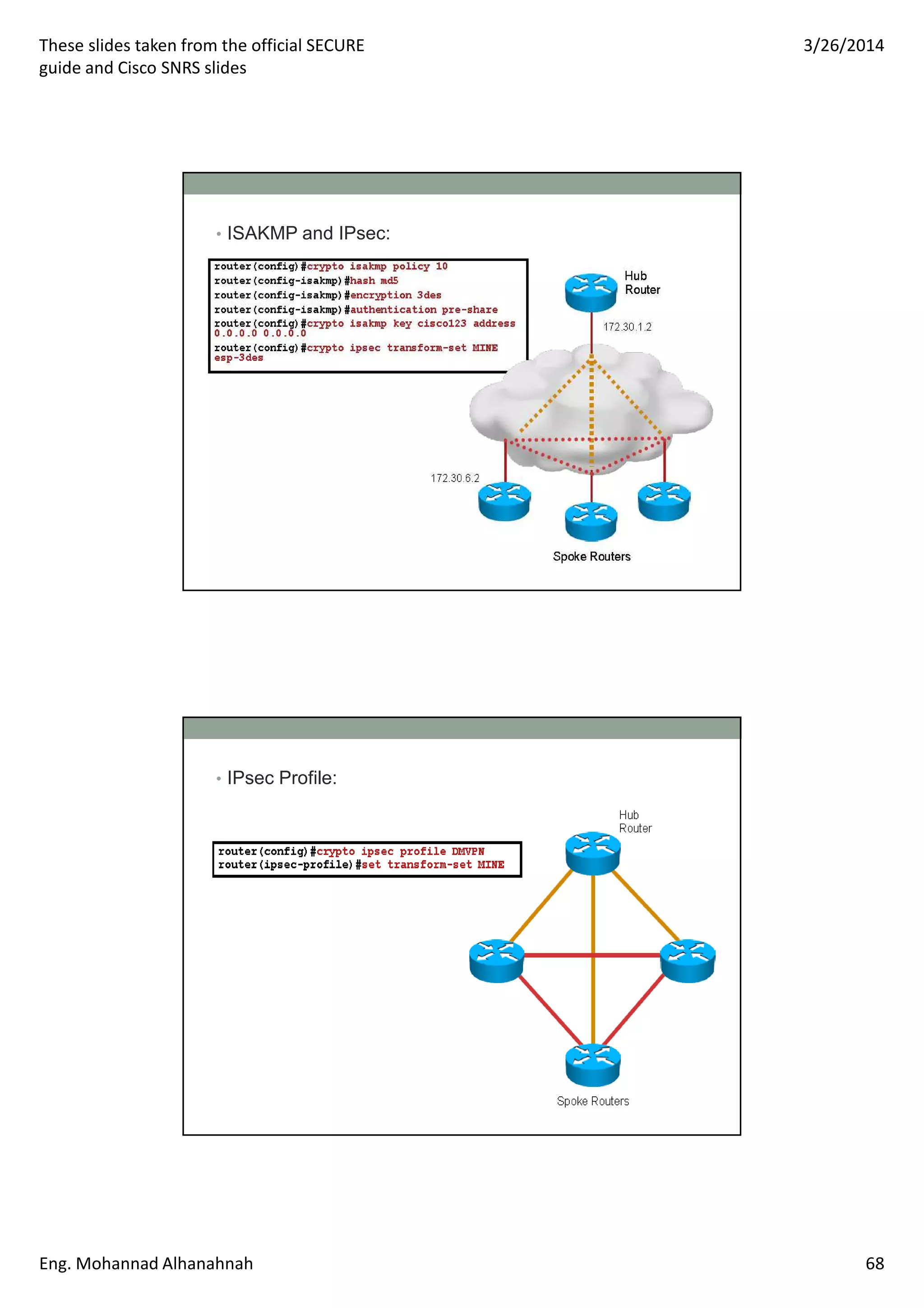
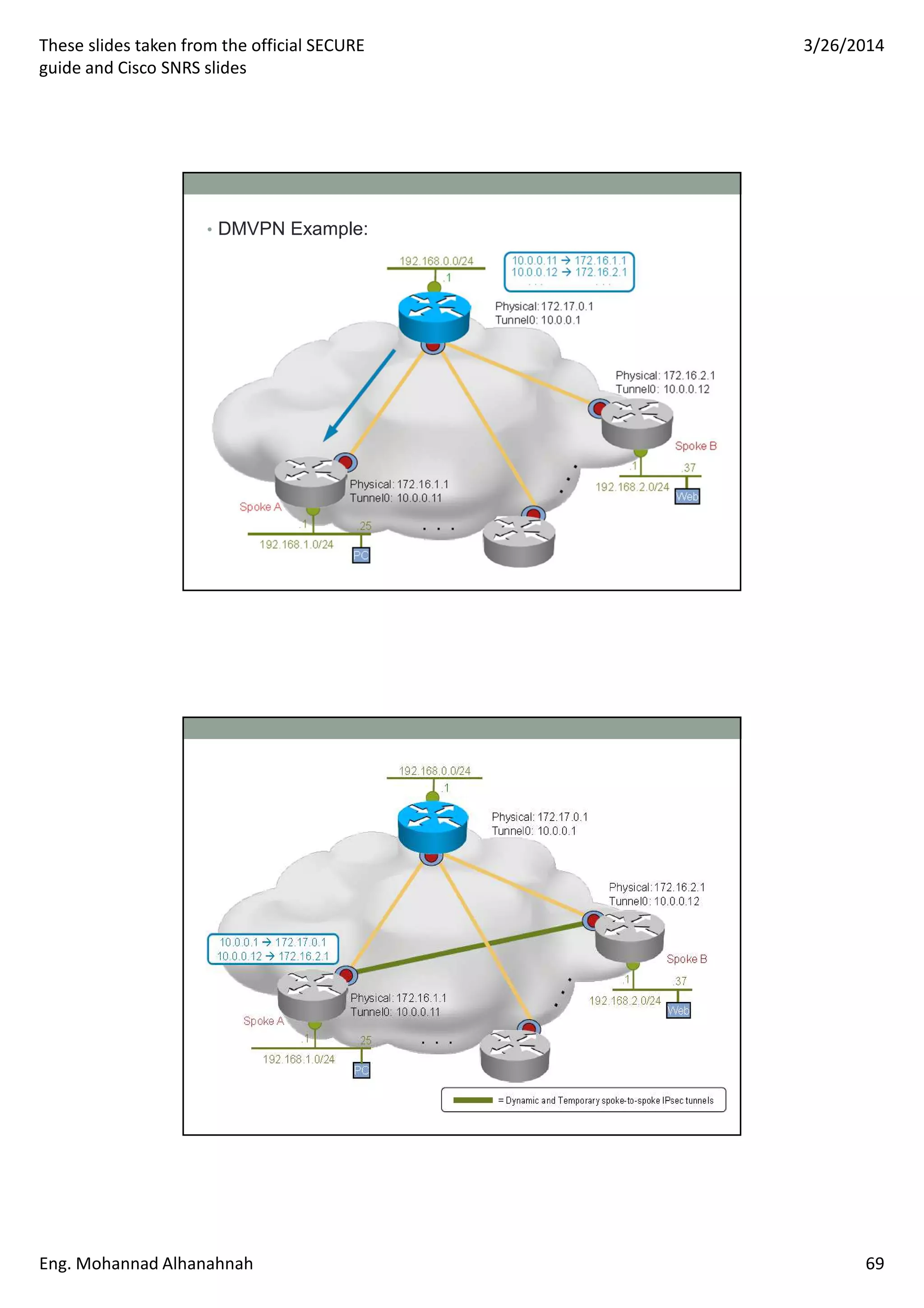
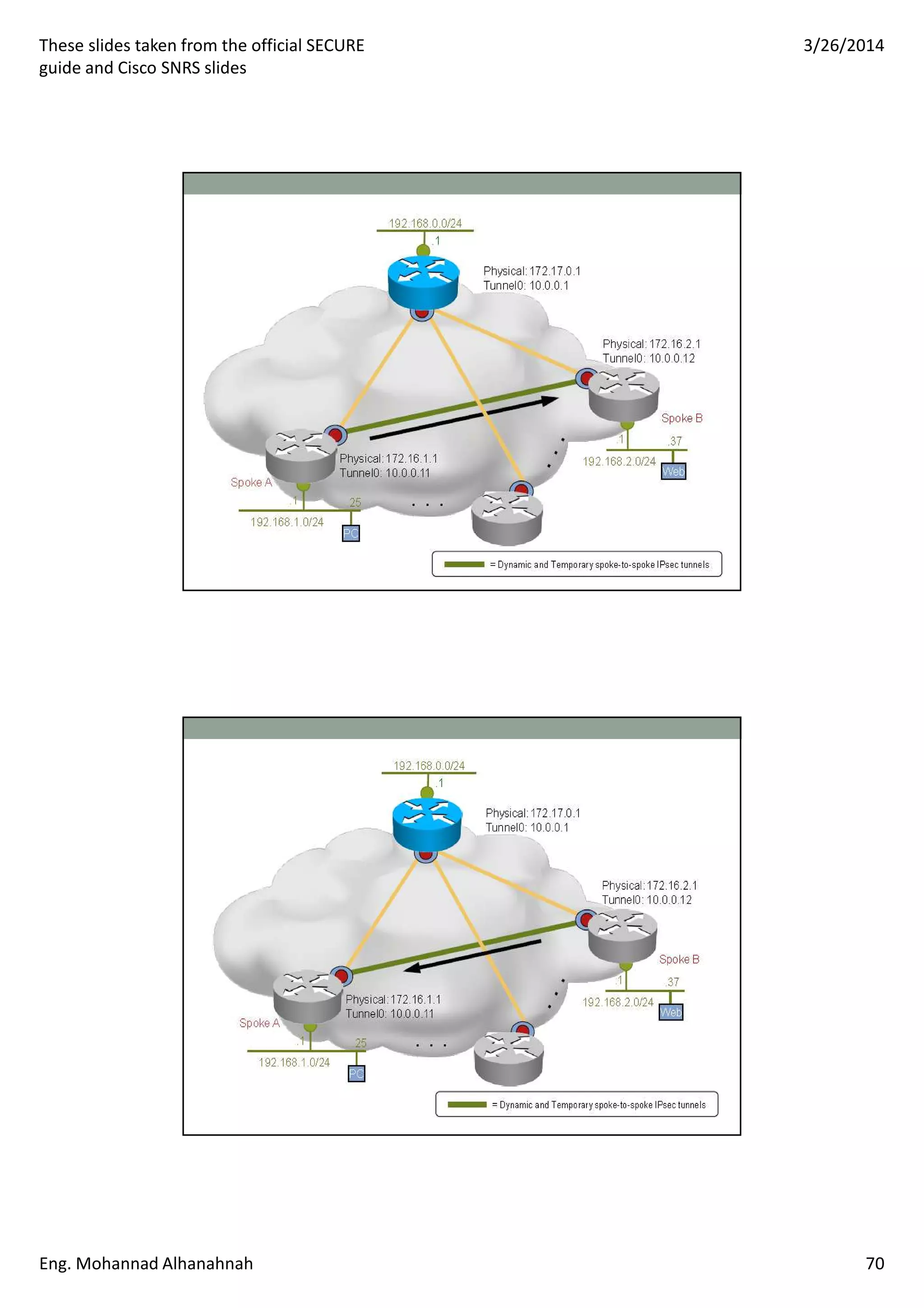
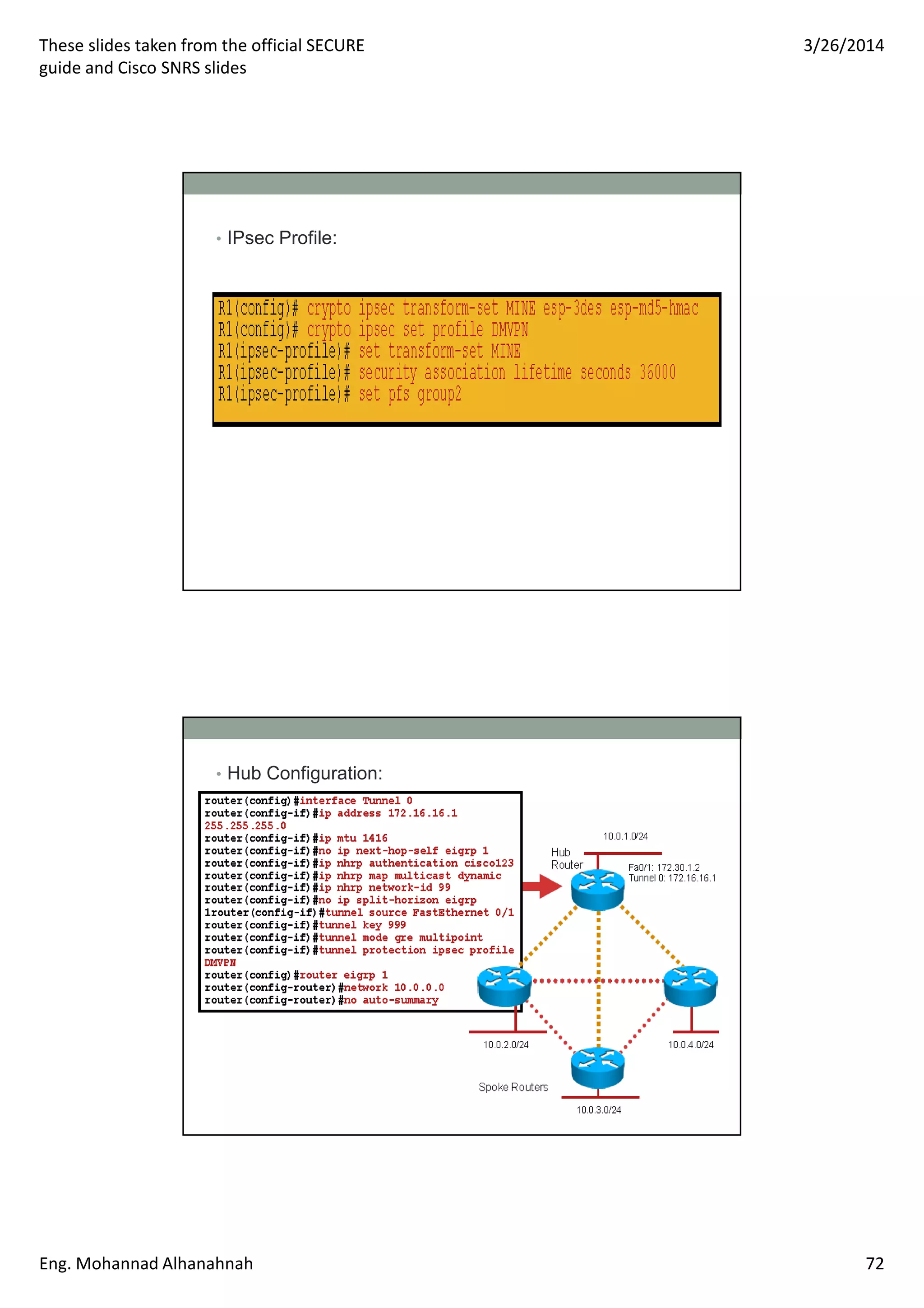
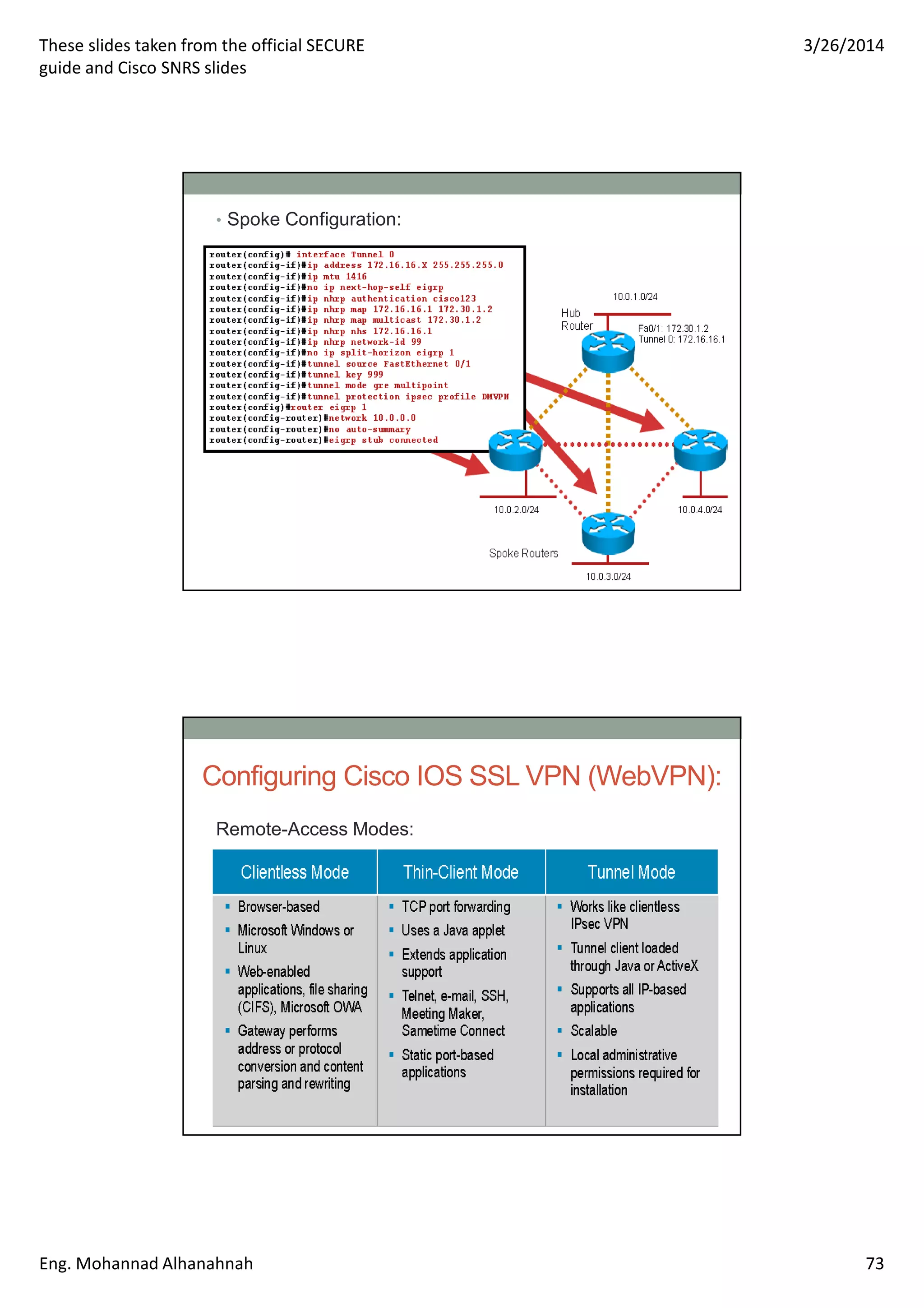
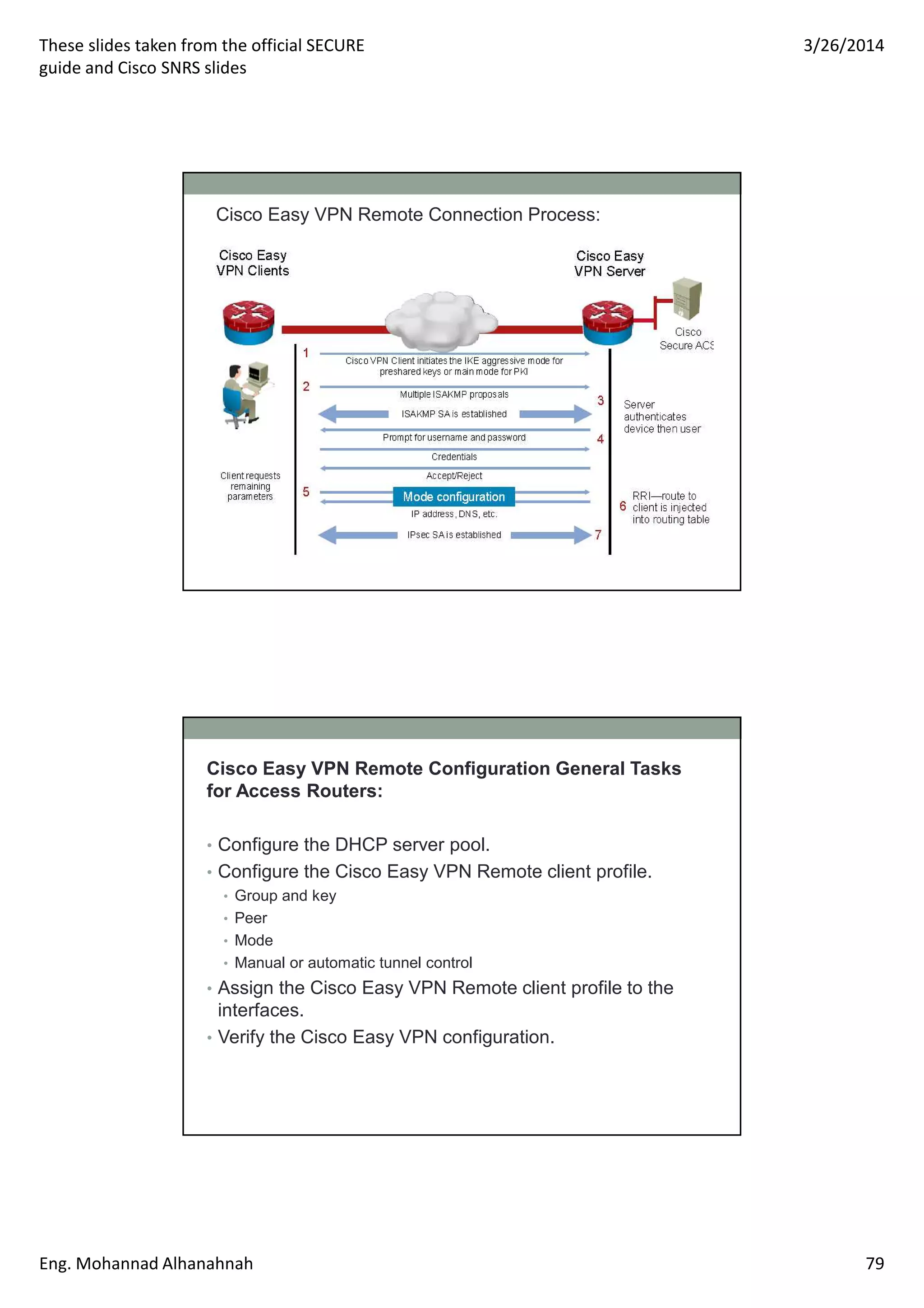
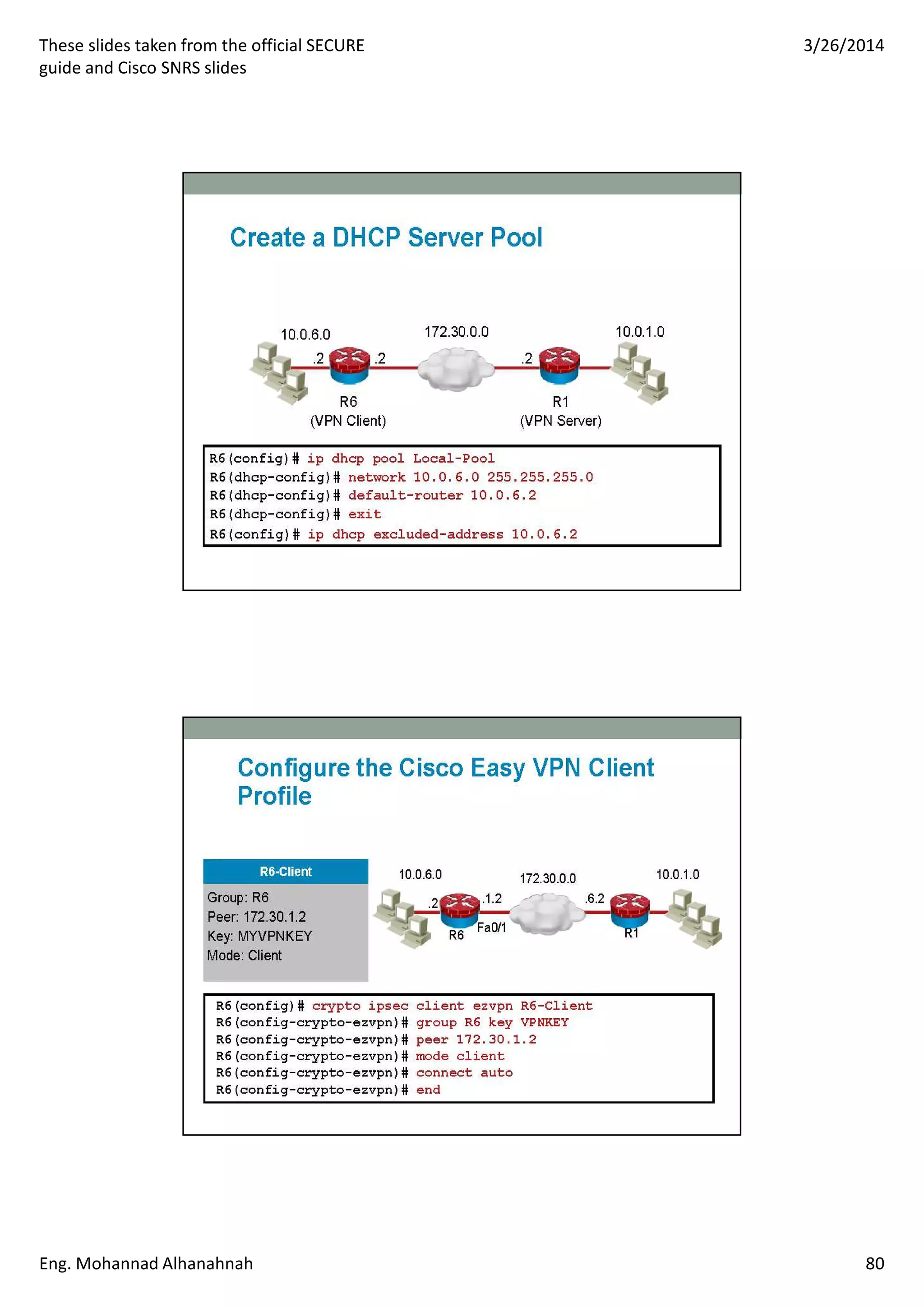
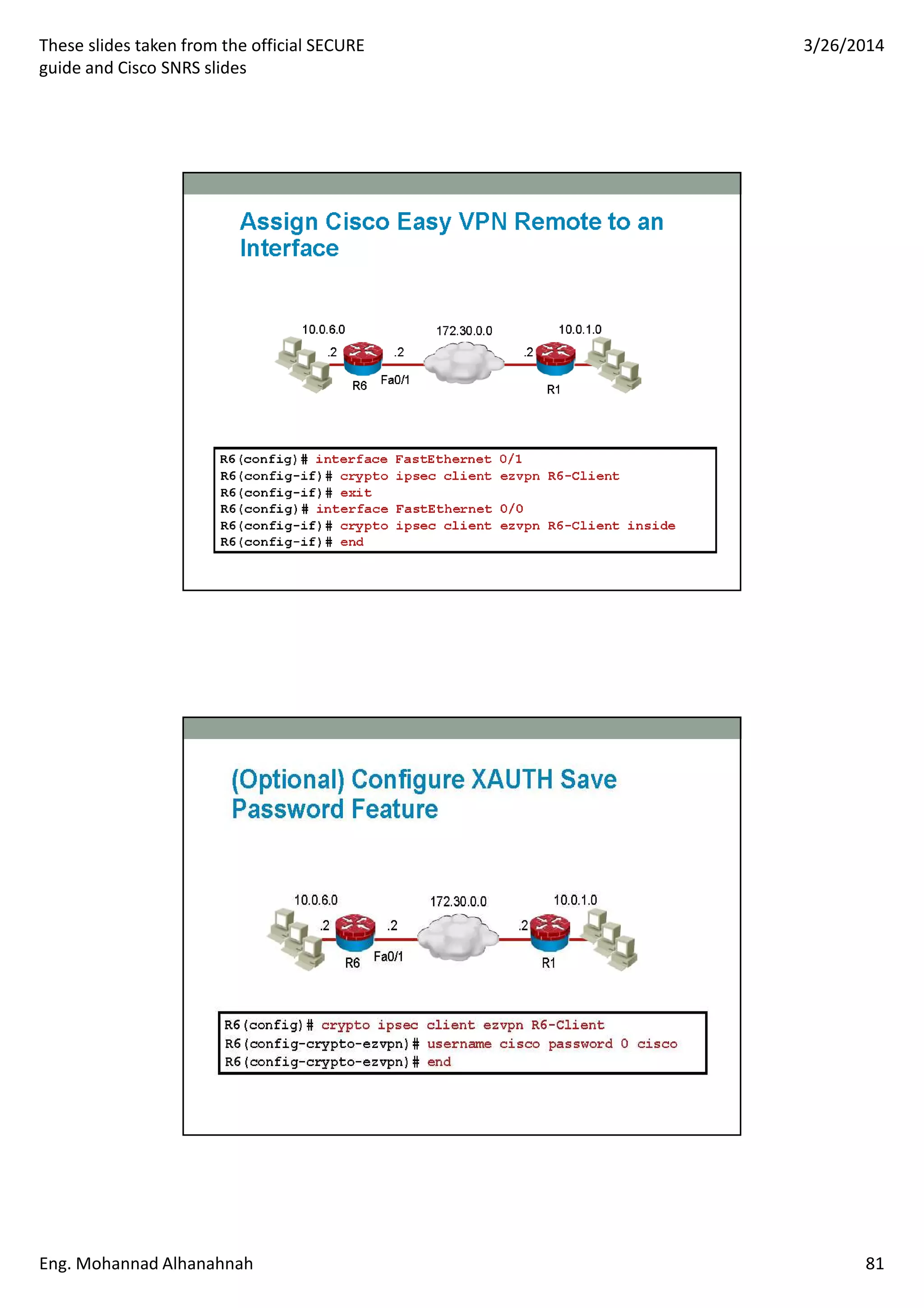
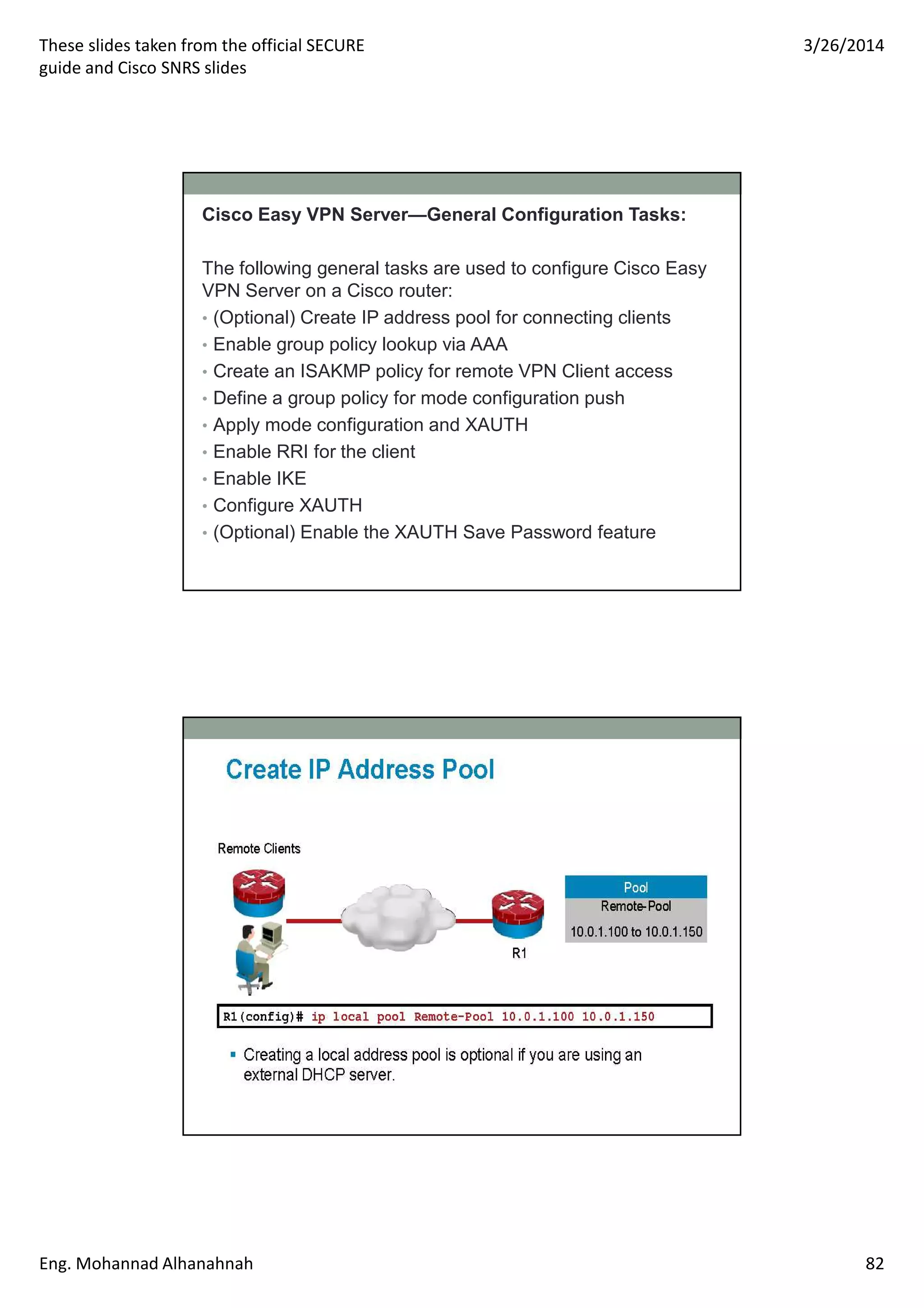
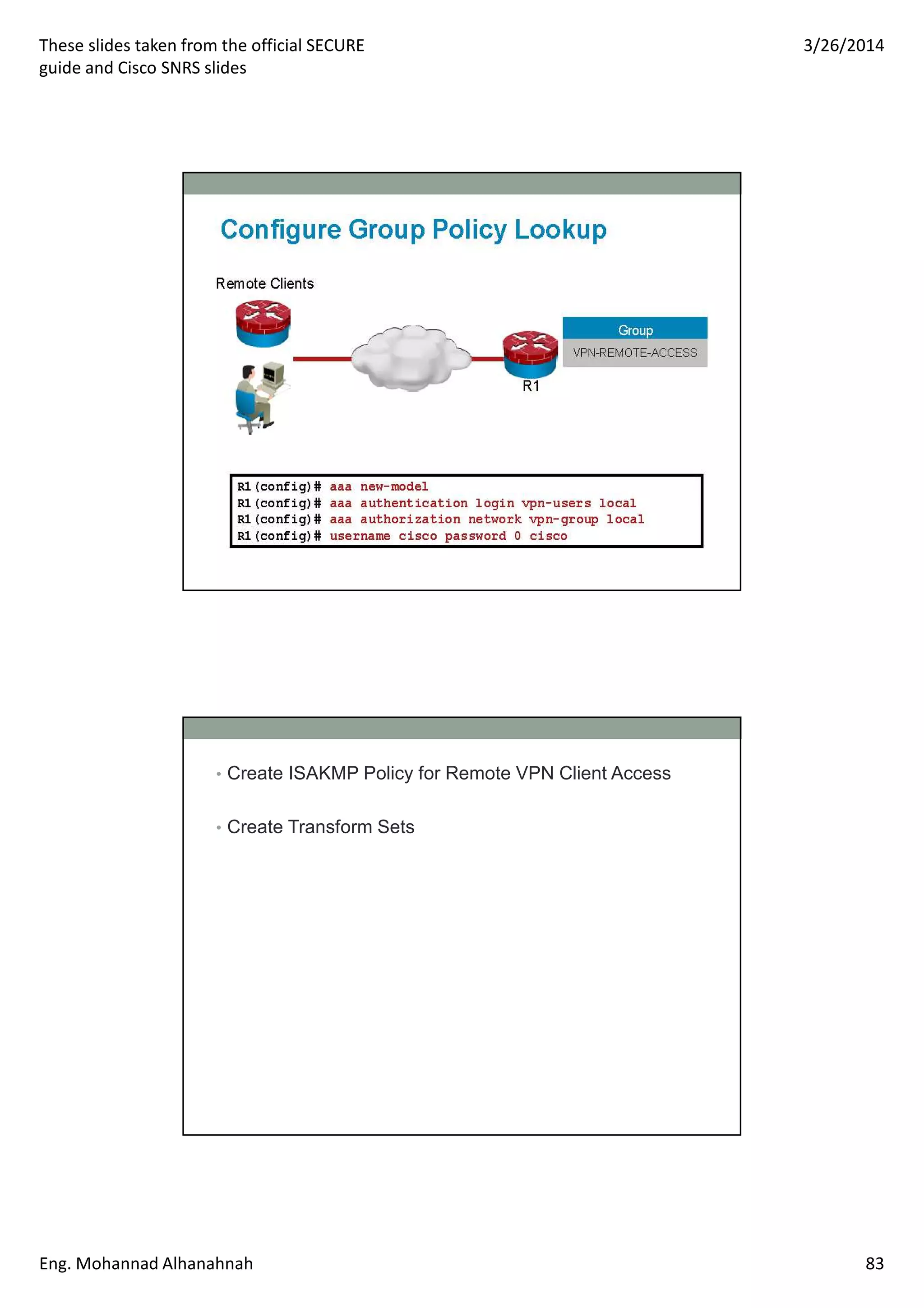
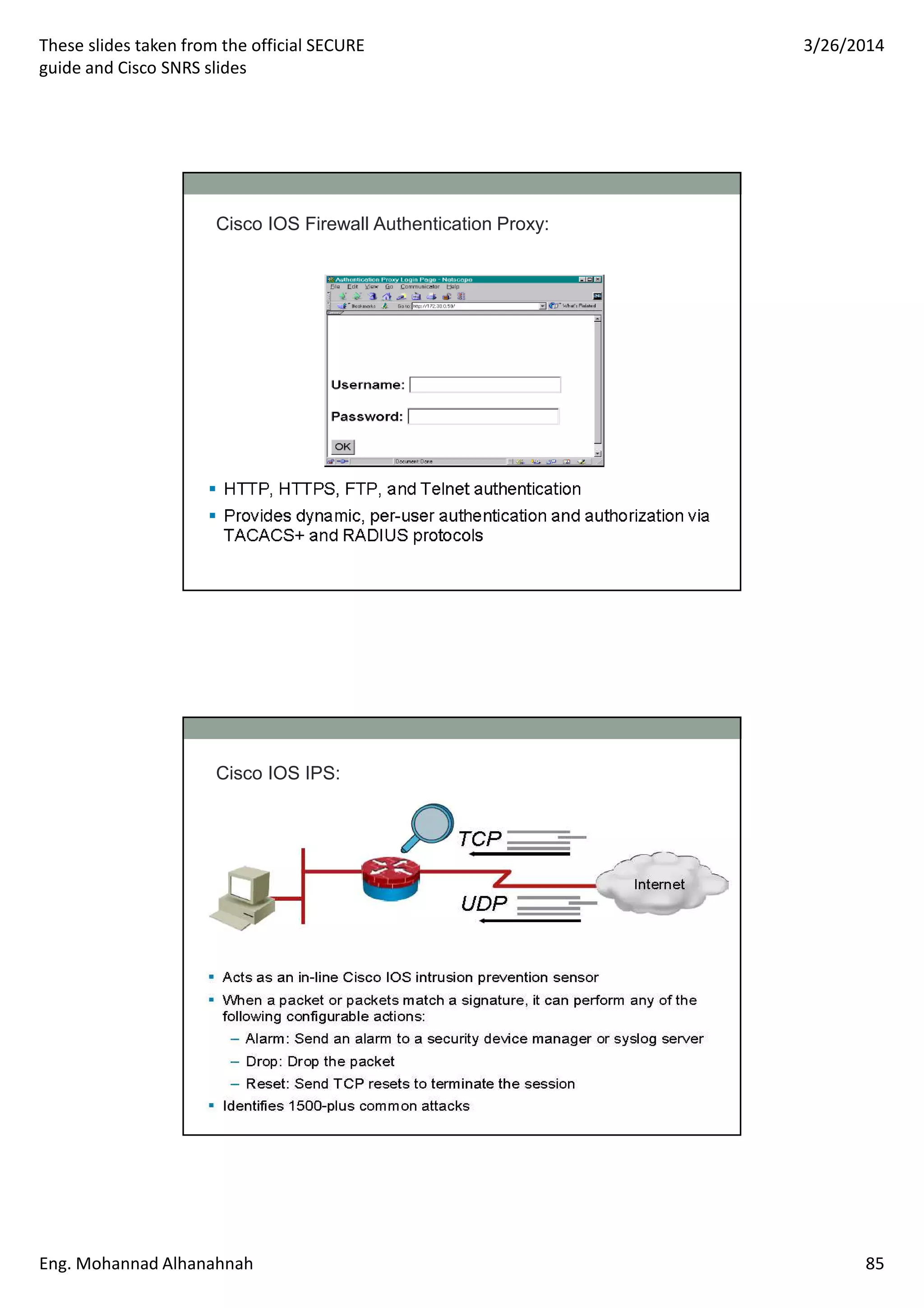
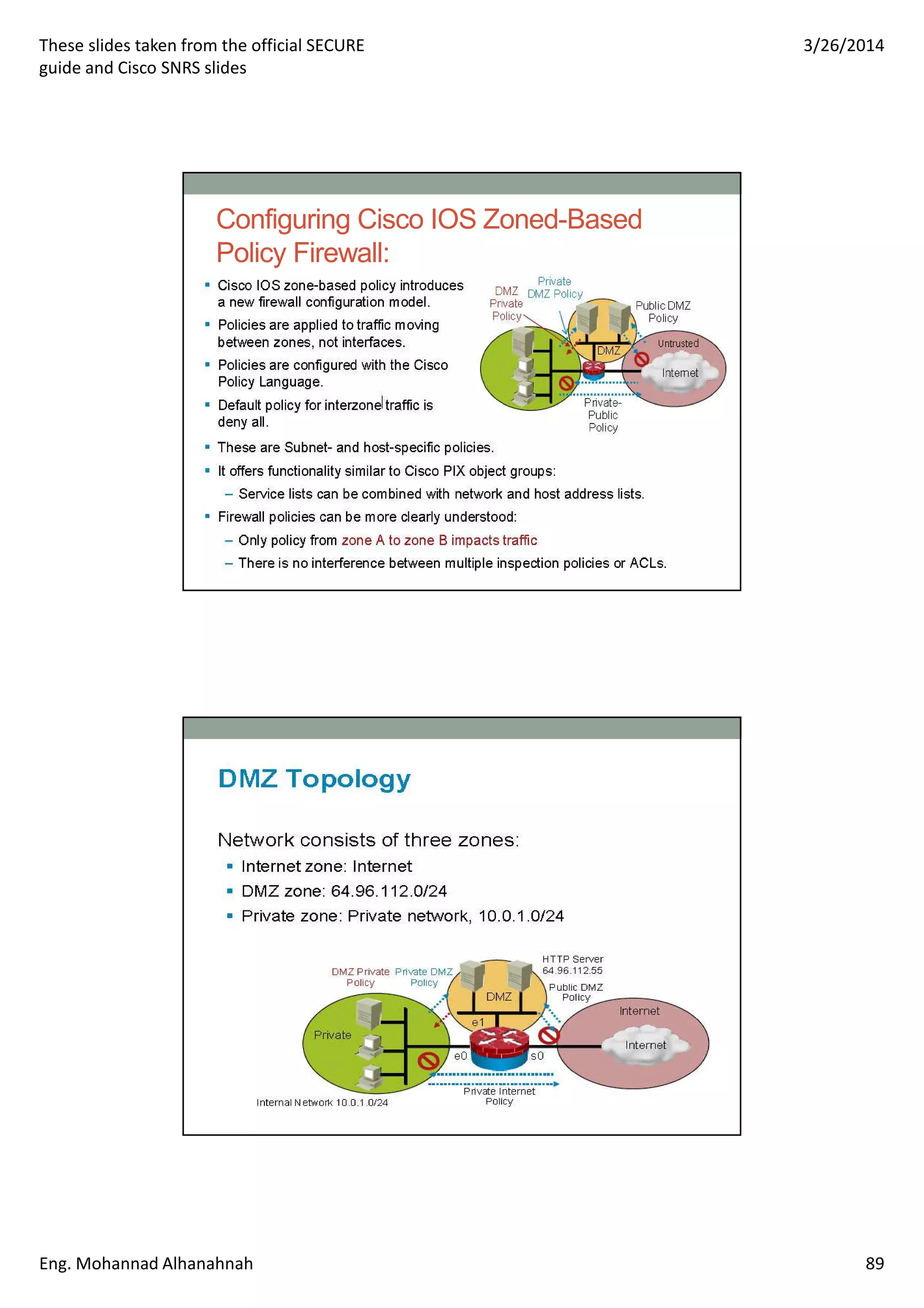
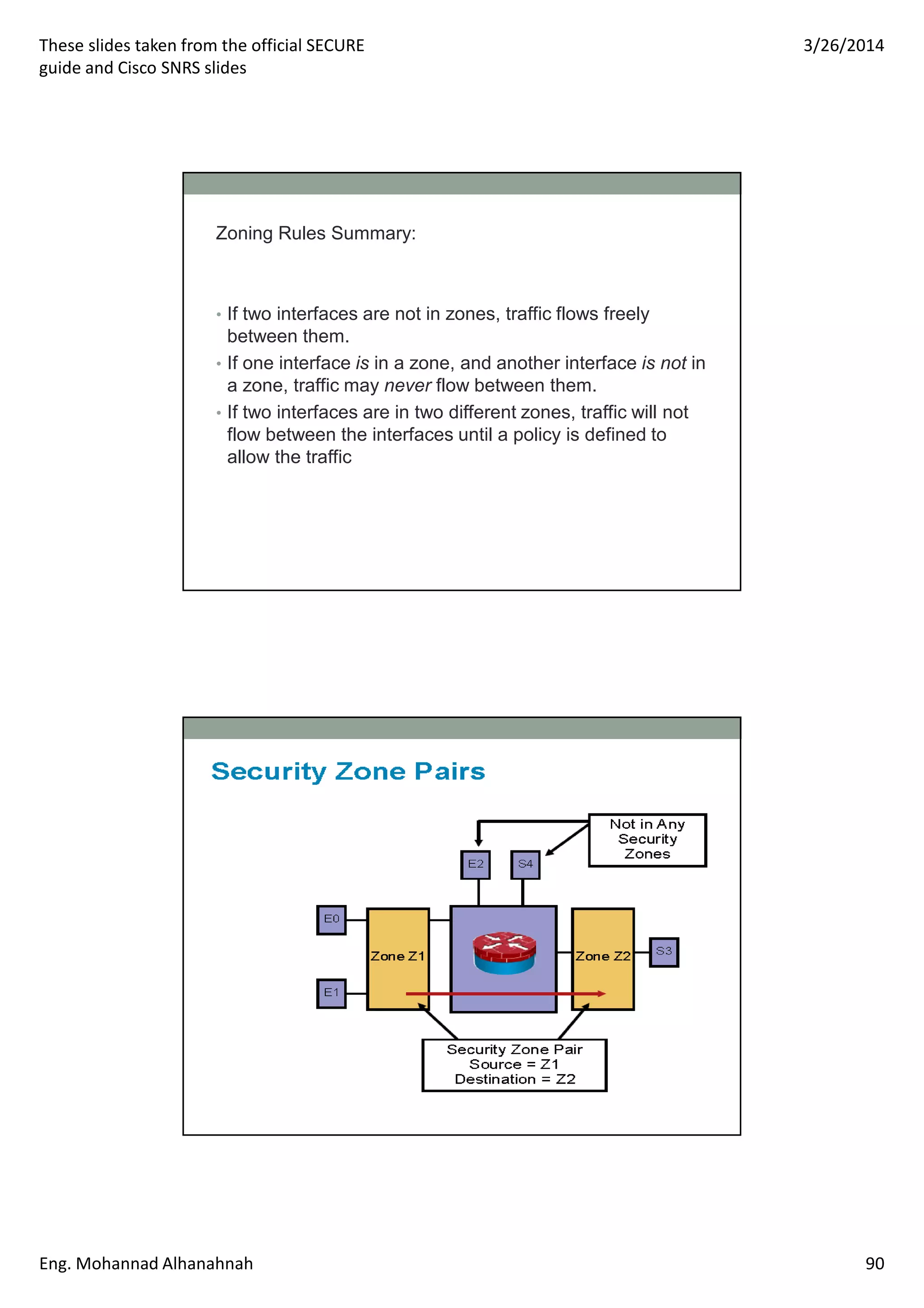
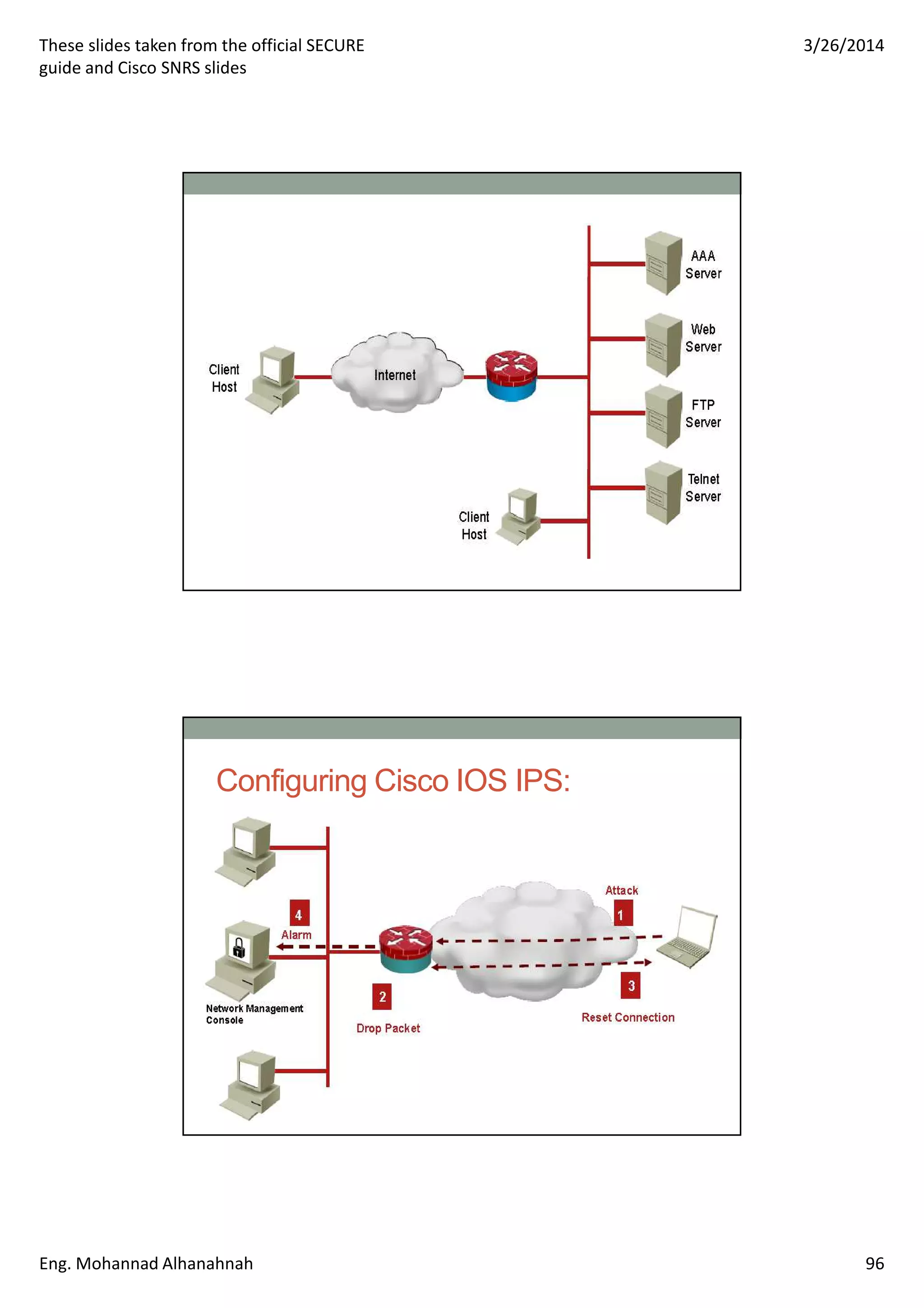
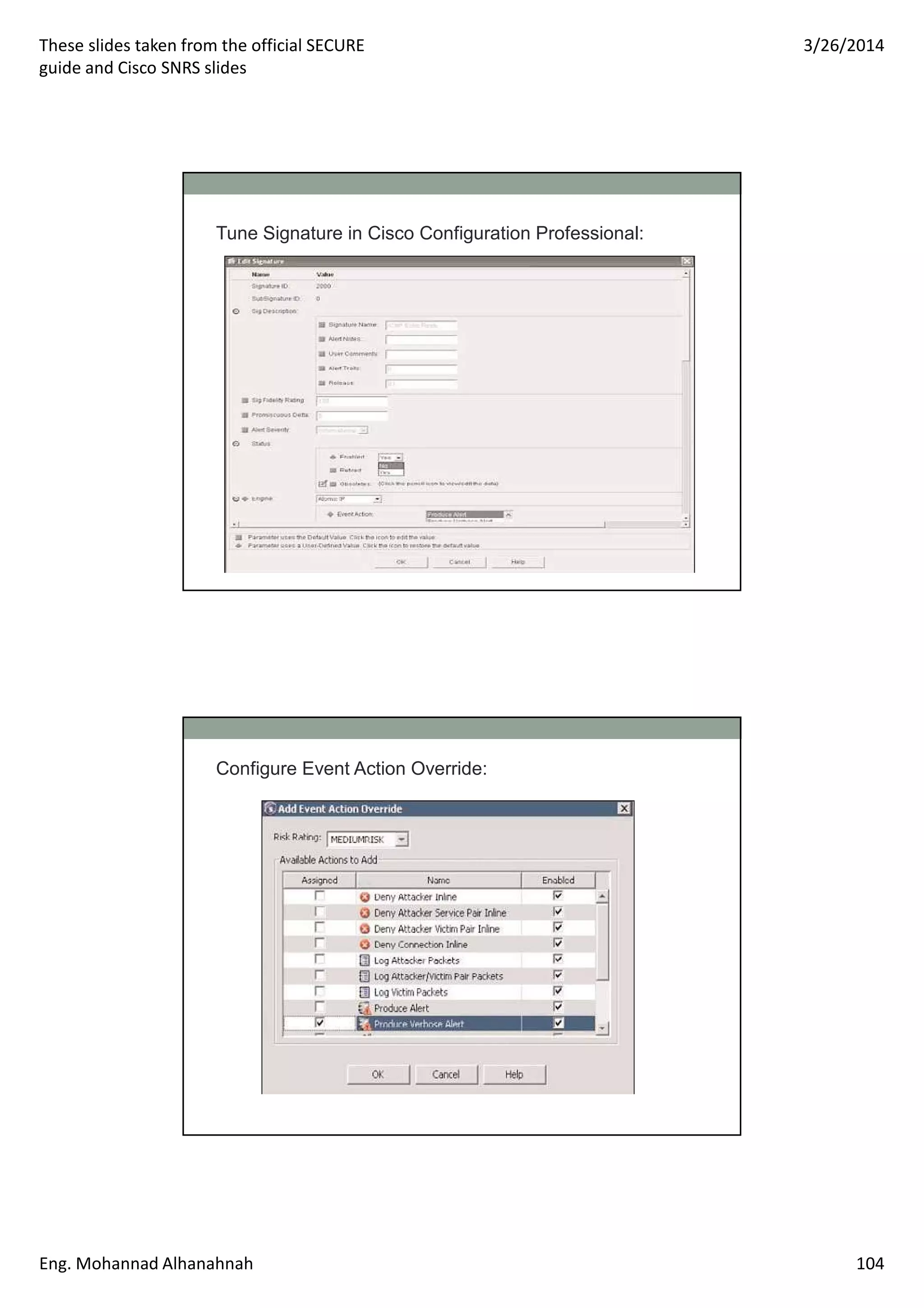
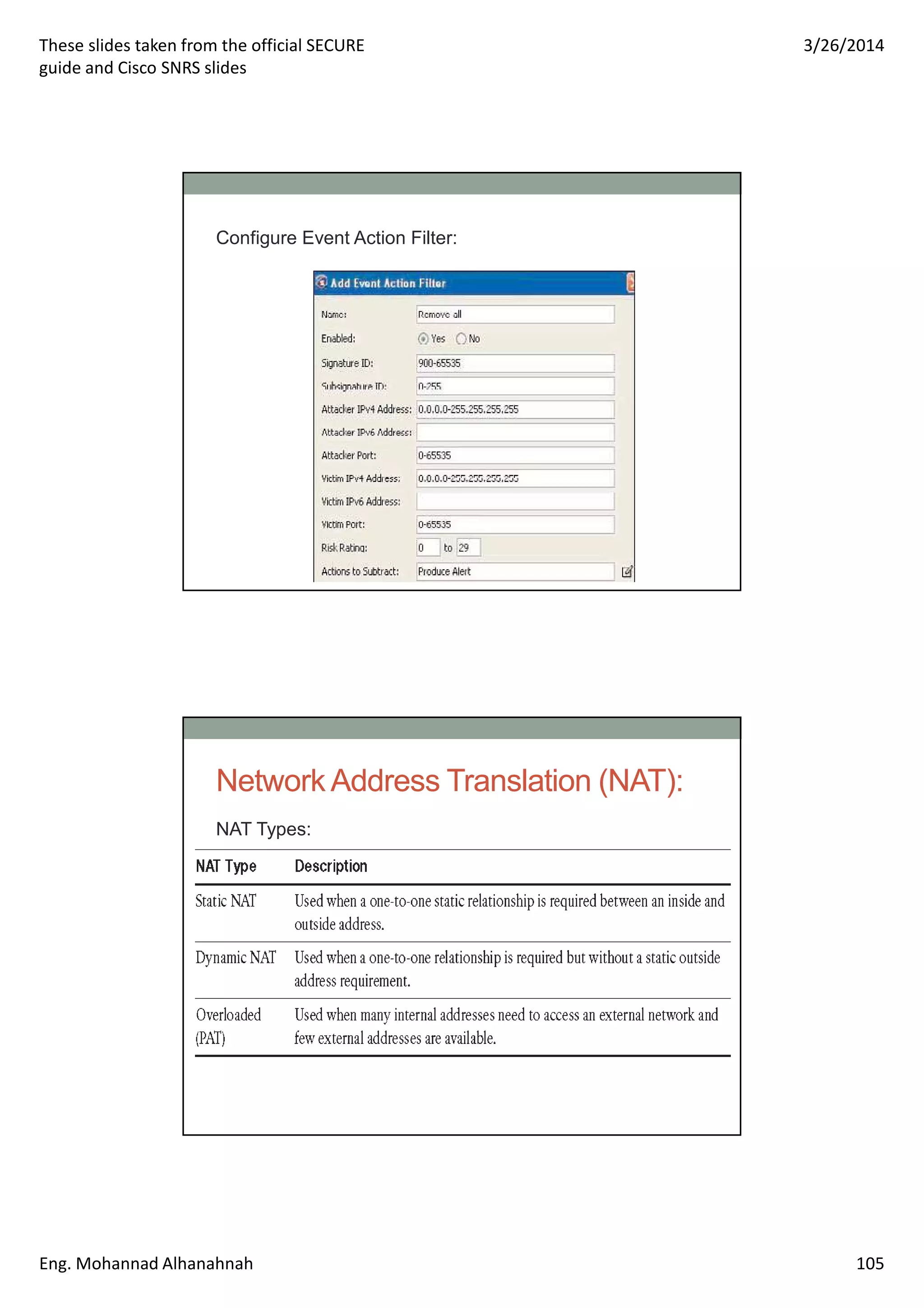
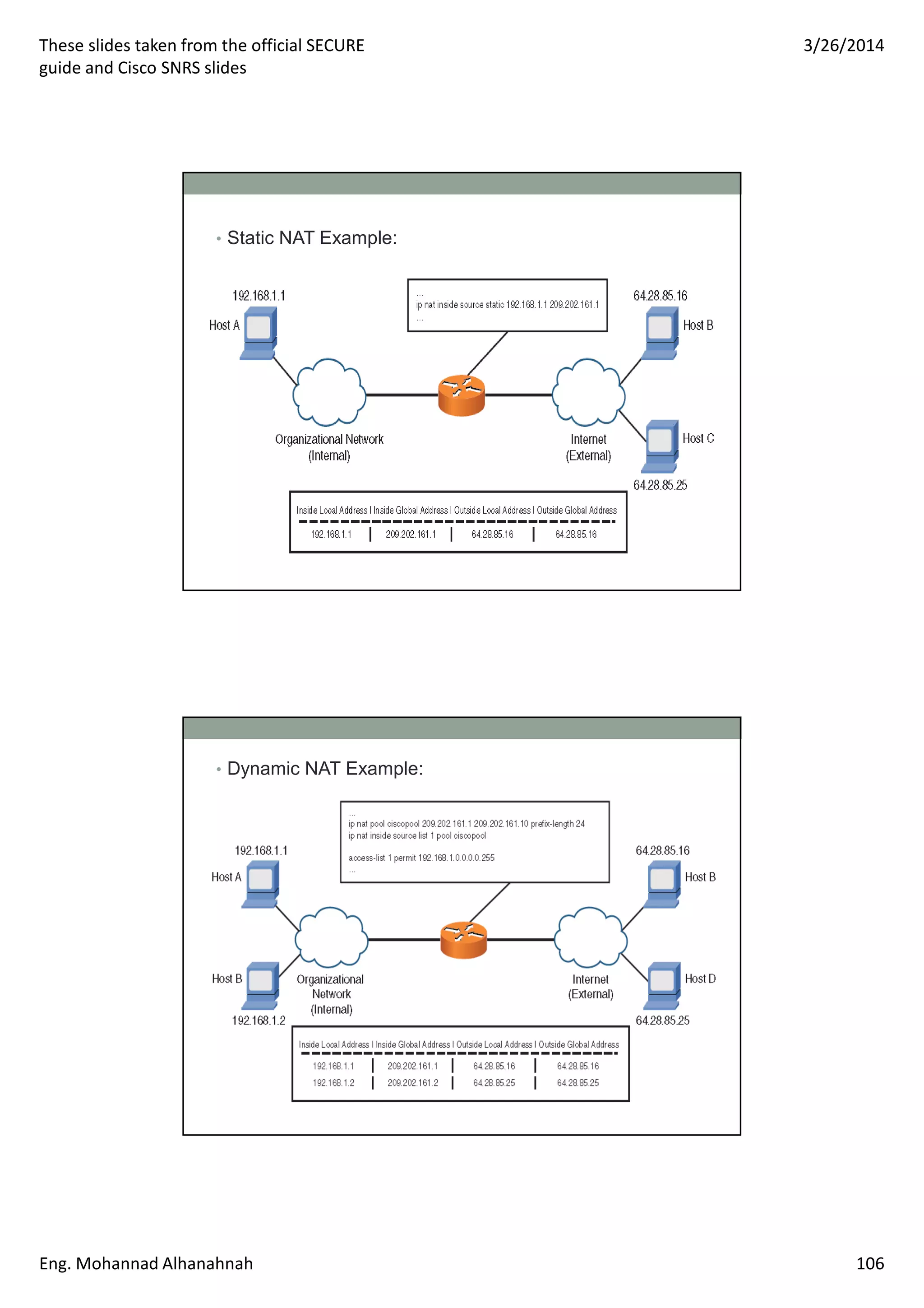
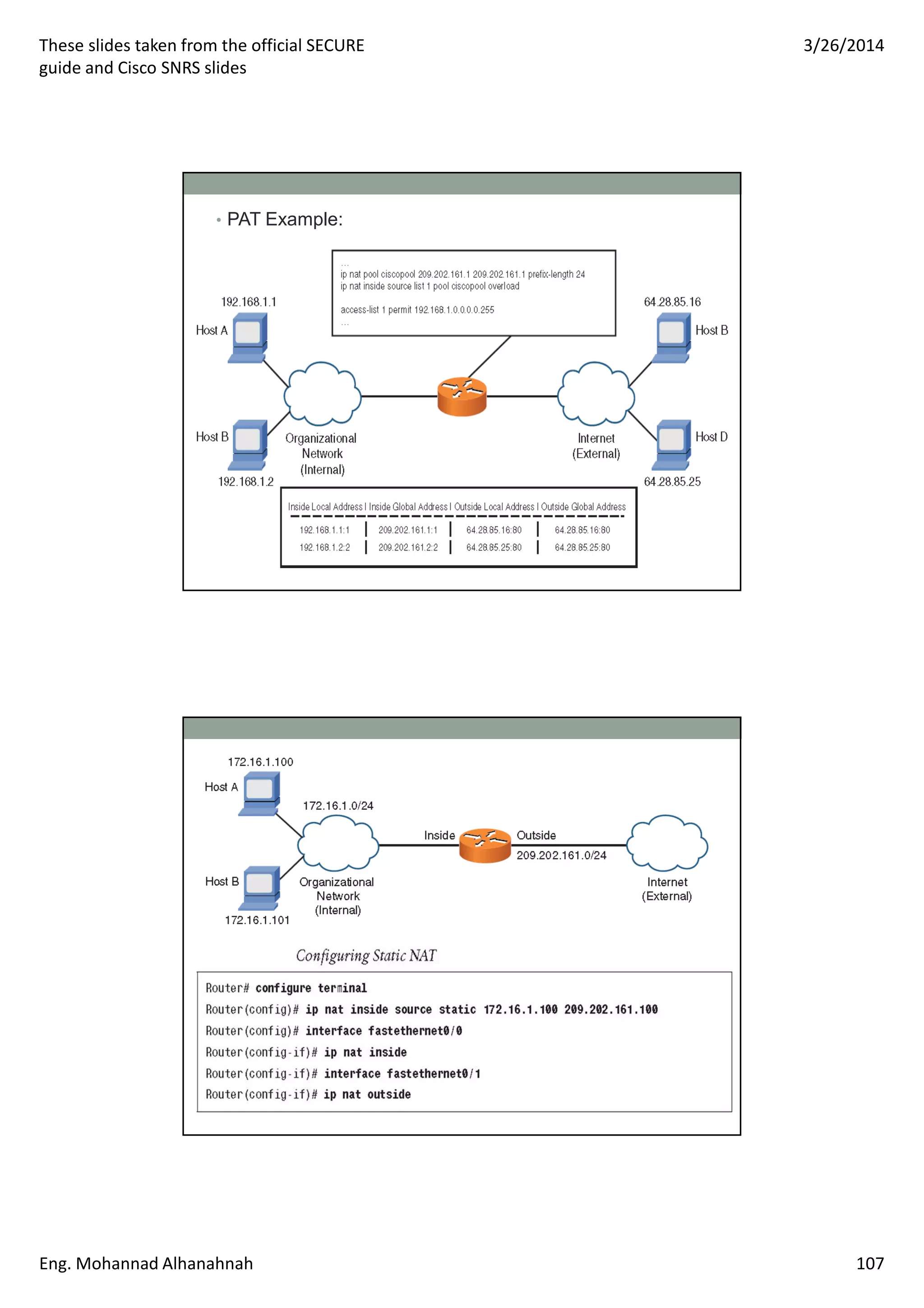
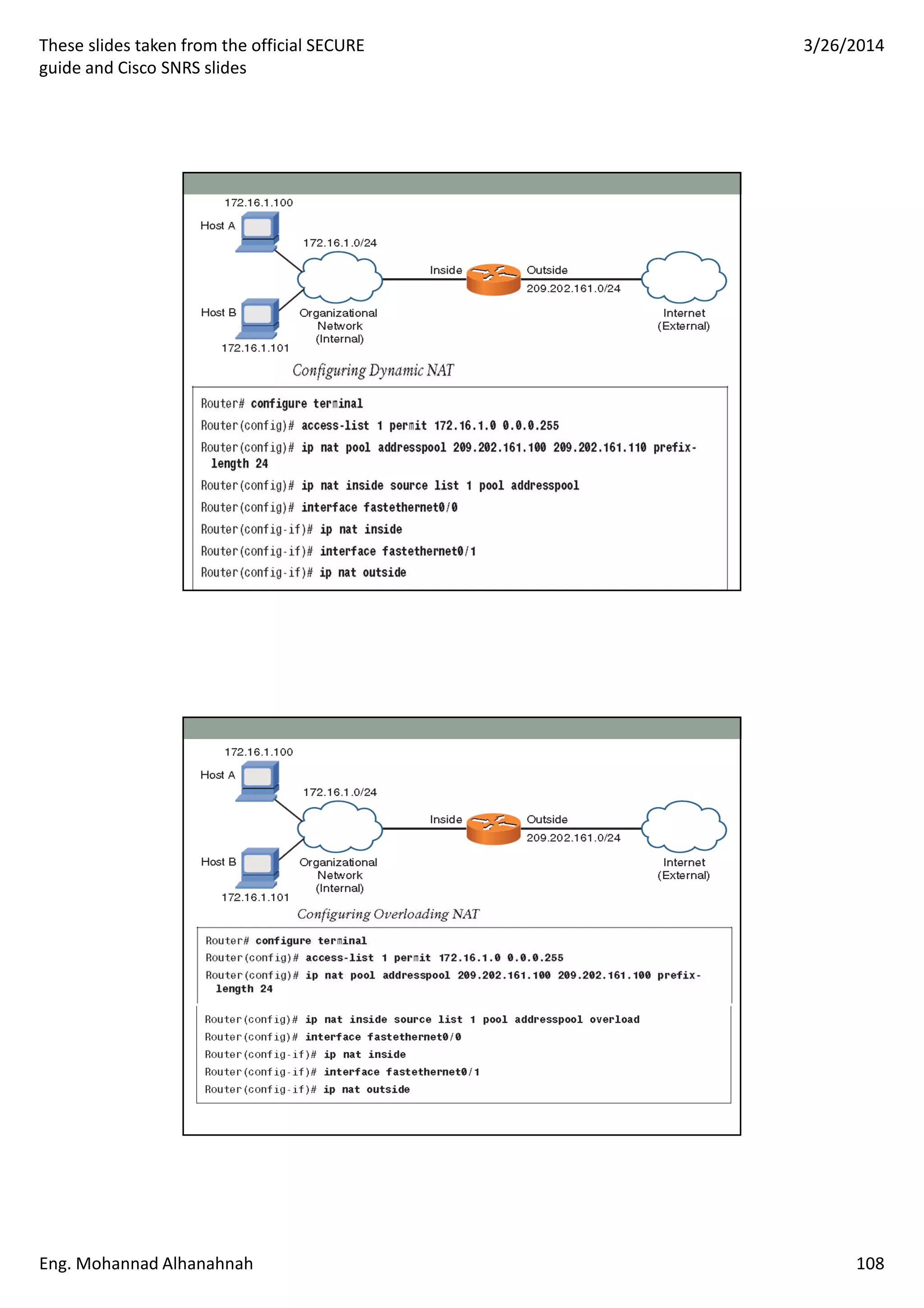
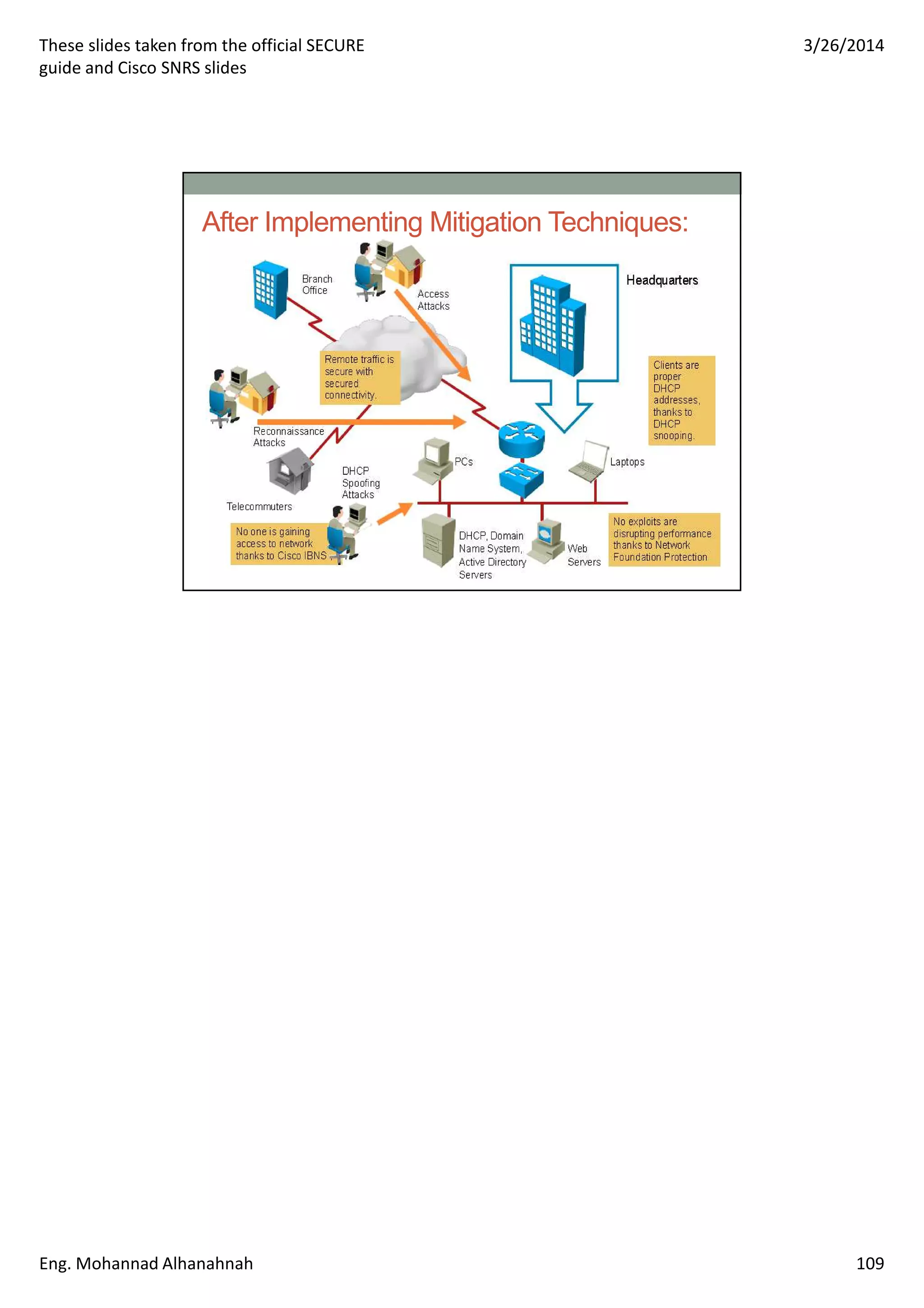
This document discusses network security technologies and Cisco solutions. It covers topics like 802.1X authentication, identity management with Cisco ACS, port security, DHCP snooping, and securing the network infrastructure with Network Foundation Protection. The document appears to be slides from a training course on Cisco's SECURE certification that provides an overview of various network security concepts and Cisco products.