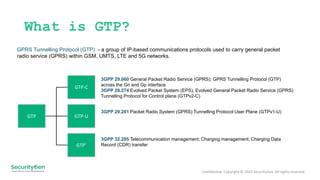
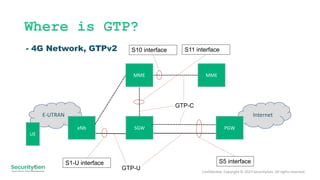
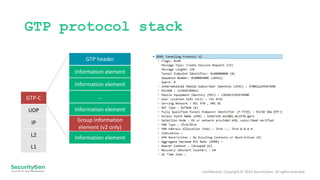
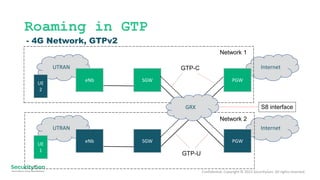
The document discusses vulnerabilities associated with the GPRS Tunneling Protocol (GTP) in 5G and LTE networks, highlighting its widespread use and lack of built-in security measures that can lead to fraud, data interception, and denial of service attacks. It presents alarming statistics indicating that a significant percentage of networks are susceptible to various forms of exploitation. Recommended protection measures include implementing GSMA-recommended security protocols and traffic filtering to enhance network security.