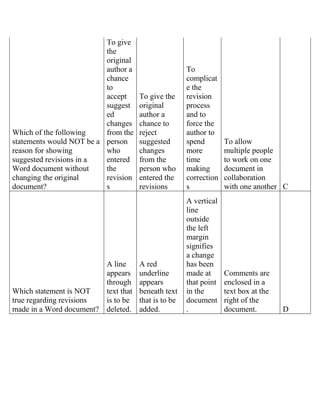
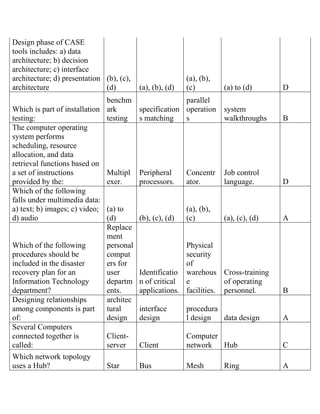
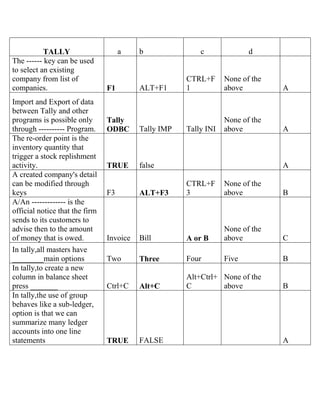
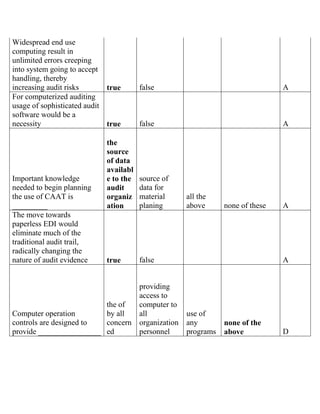
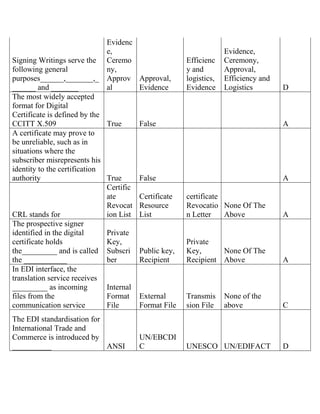
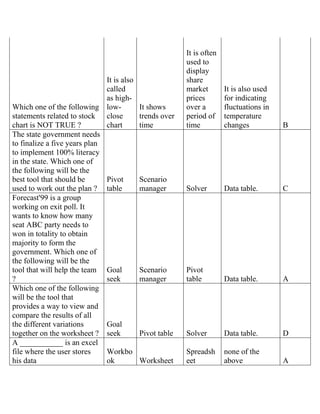
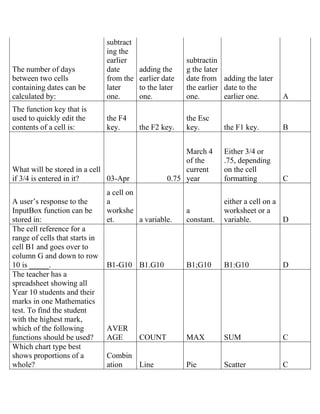
The document contains a series of questions and answers related to the accounting software Tally. It tests knowledge of key functions, reports, and concepts in Tally such as creating vouchers, the group company feature, inventory valuation methods, and default configurations.









































































































































![What type of program
allows an object within an
image to be edited without
affecting other objects?
Paint
program
Draw
program
Filtering
program
Animation
program A
Which of the following
animation effects can be
added to a slide? Fly in From top
Dissolve
in
Fly in, From
top, and
Dissolve in D
Which of the following is
TRUE regarding the
Datasheet?
Once
data is
entered
it
cannot
be
changed
.
Once data is
entered it
can be
changed.
Data
cannot be
entered
into
Datasheet
.
There is no such
thing as a
Datasheet. B
Graphical software tools
that provide complex
analysis of stored data are: OLTP. OLAP. OLST. OLIP. B
Which of the following
statements is TRUE
regarding PowerPoint
diagrams?
You can
change
the
appeara
nce of a
whole
diagram
, but not
individu
al
shapes
of a
diagram
.
You can
change both
the
appearance
of a whole
diagram and
the
individual
shapes of a
diagram.
You
cannot
change
the style
of the
connectin
g lines in
an
Organizat
ion chart.
You cannot
change the color
of the boxes in
an Organization
chart. B
Which keyboard key
combination is used to undo
the previous command(s)?
[Enter+
A] [Shift+Z] [Alt+Z] [Ctrl+Z] D](https://image.slidesharecdn.com/caitttrainingquestion1500-140616084822-phpapp02/85/Ca-itt-training-question-1500-143-320.jpg)