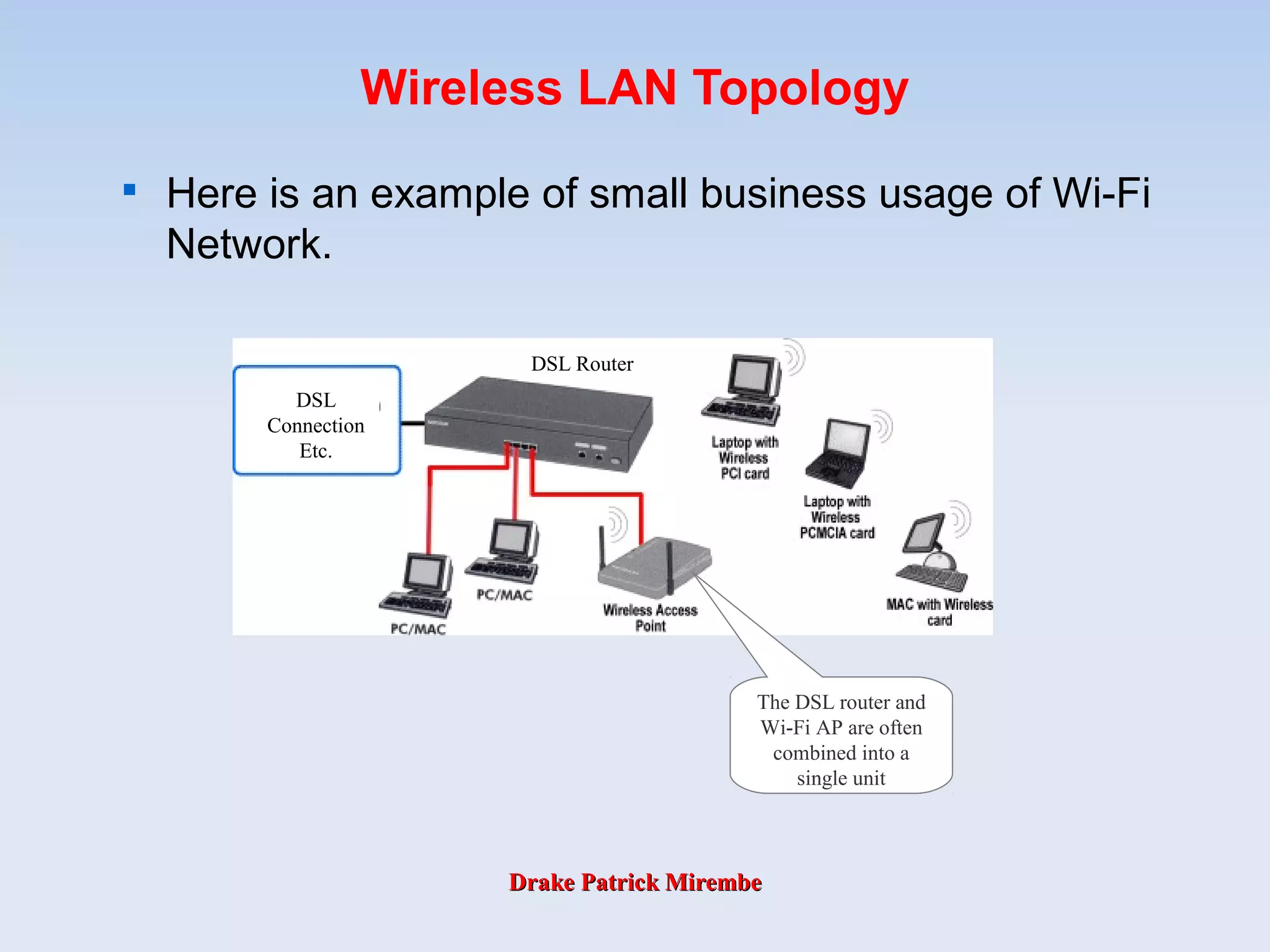
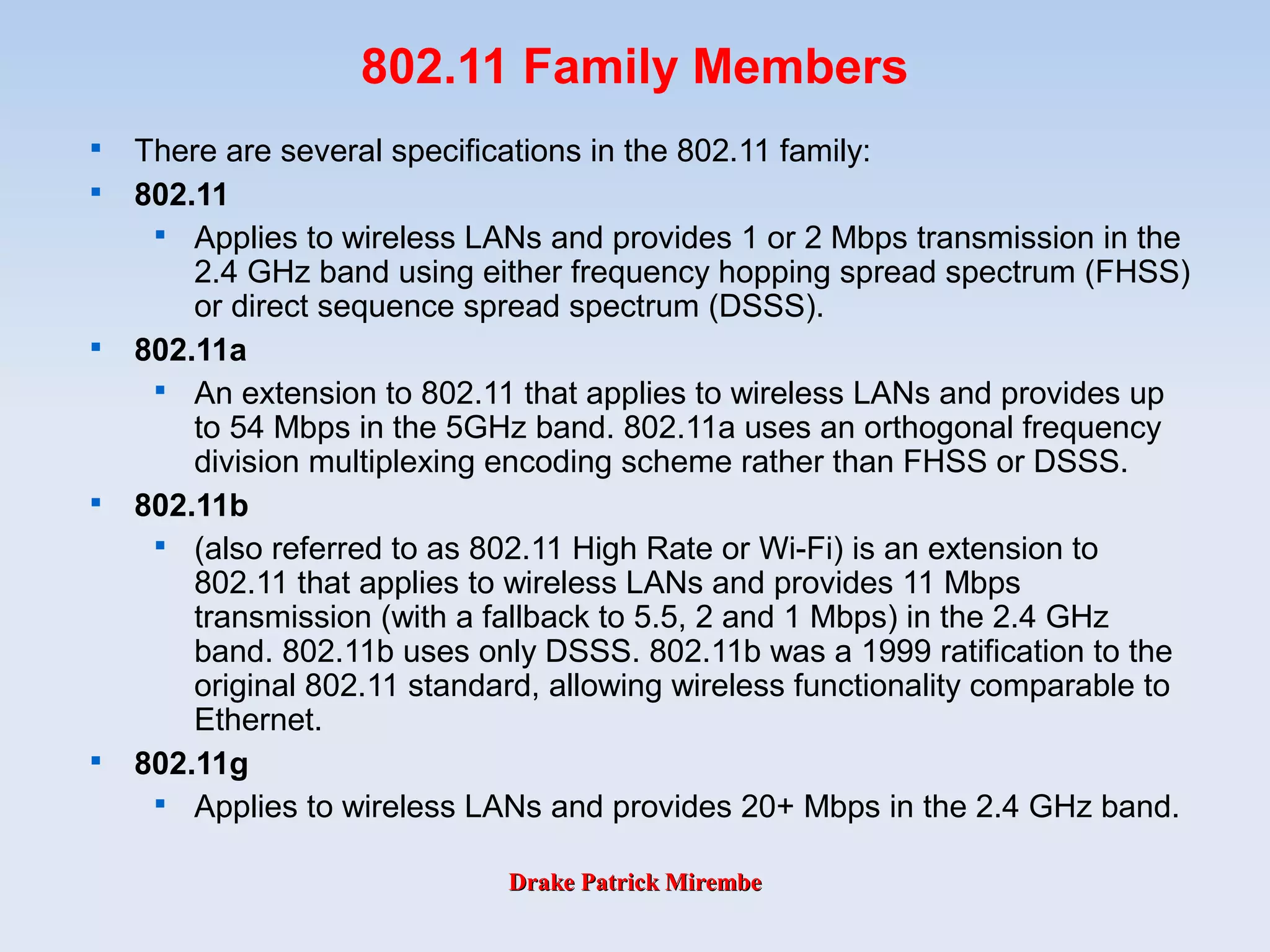
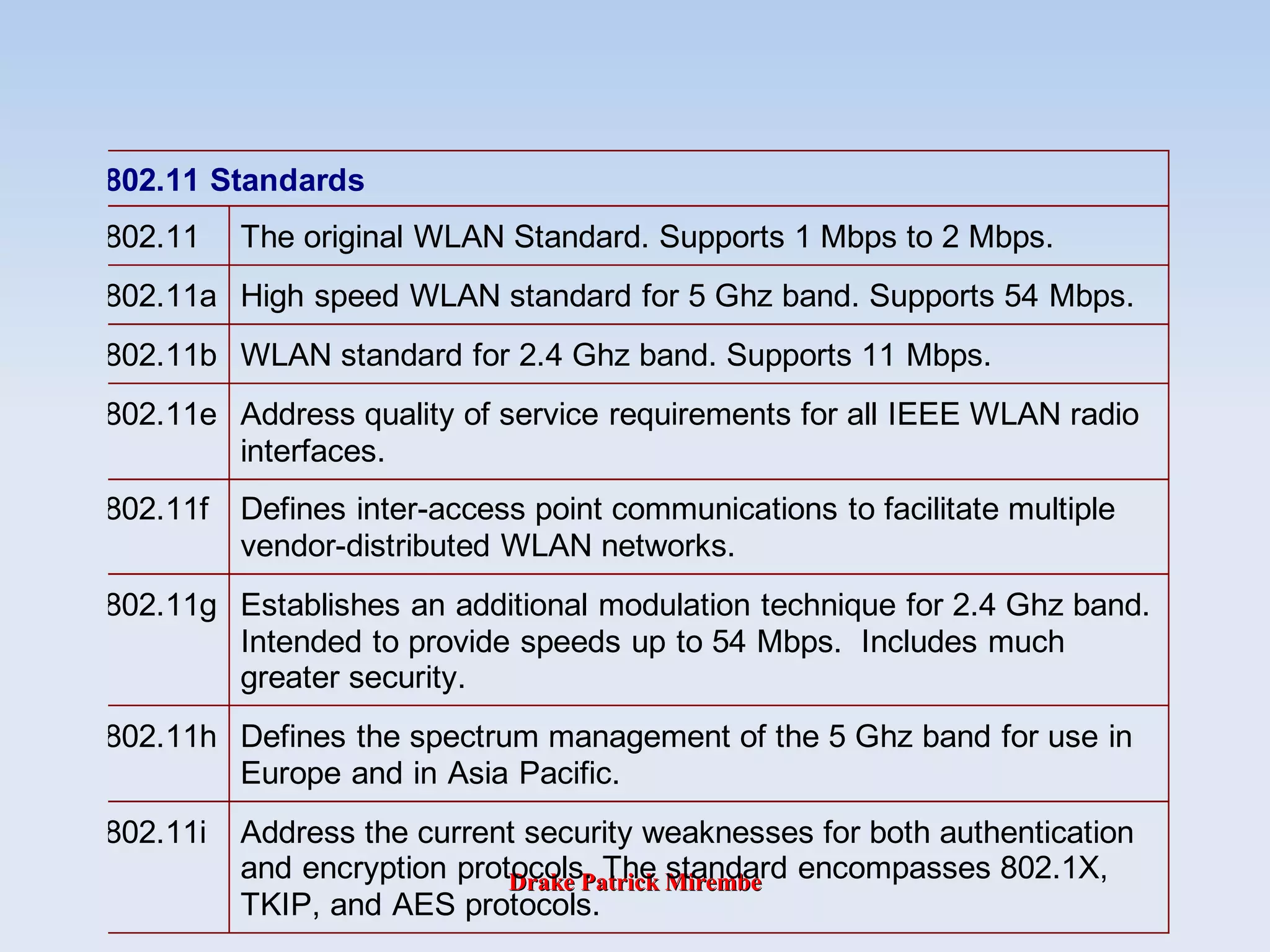
The document discusses Wi-Fi technologies. It describes the 802.11 family of specifications including 802.11, 802.11a, 802.11b and 802.11g. It explains that 802.11 established the original wireless LAN standard, while 802.11a supports speeds up to 54 Mbps in the 5GHz band. 802.11b, also known as Wi-Fi, supports speeds up to 11 Mbps in the 2.4GHz band. Finally, 802.11g operates in the same frequency band as 802.11b but supports speeds over 20 Mbps.

































































![Drake Patrick MirembeDrake Patrick Mirembe
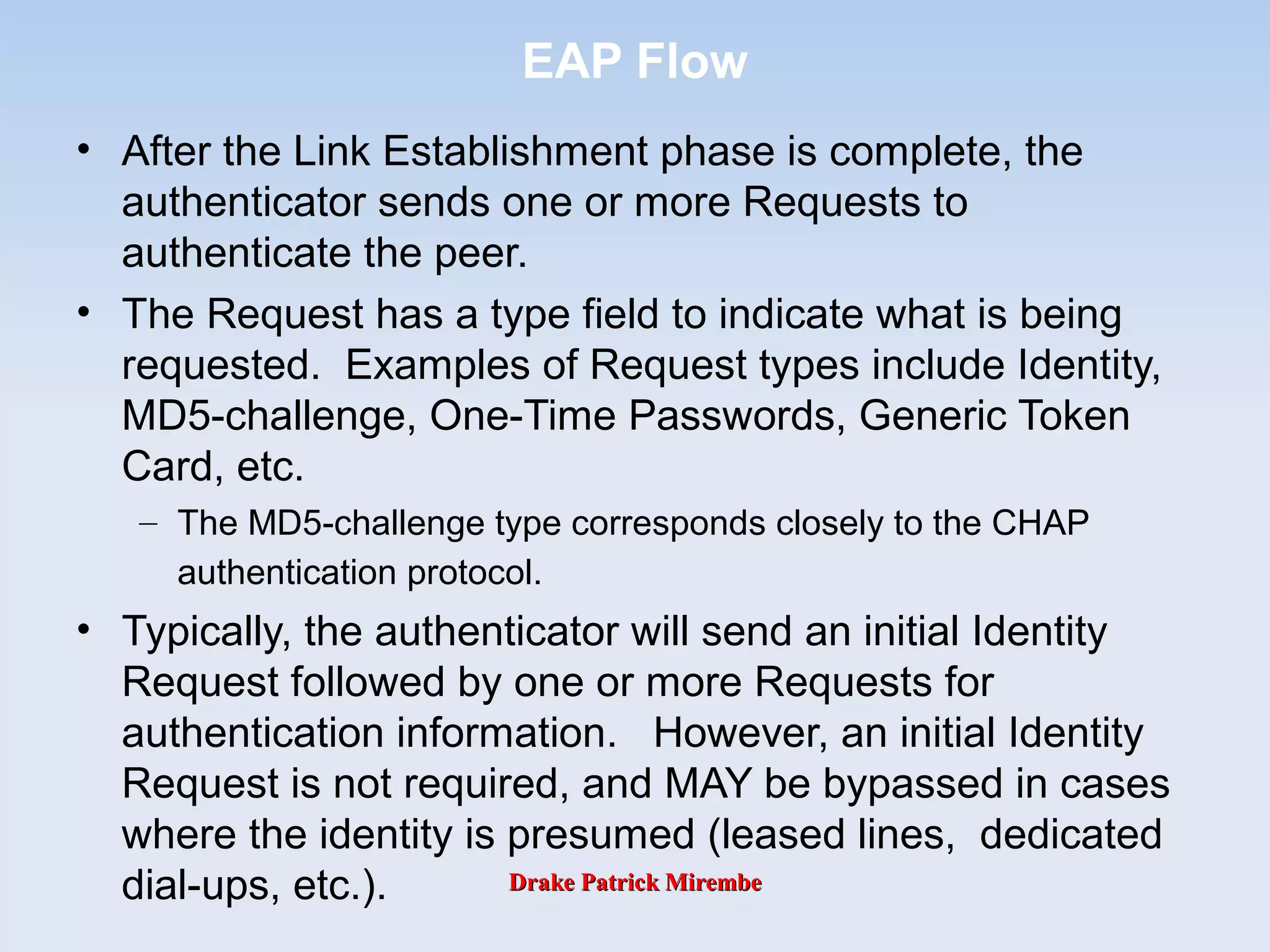
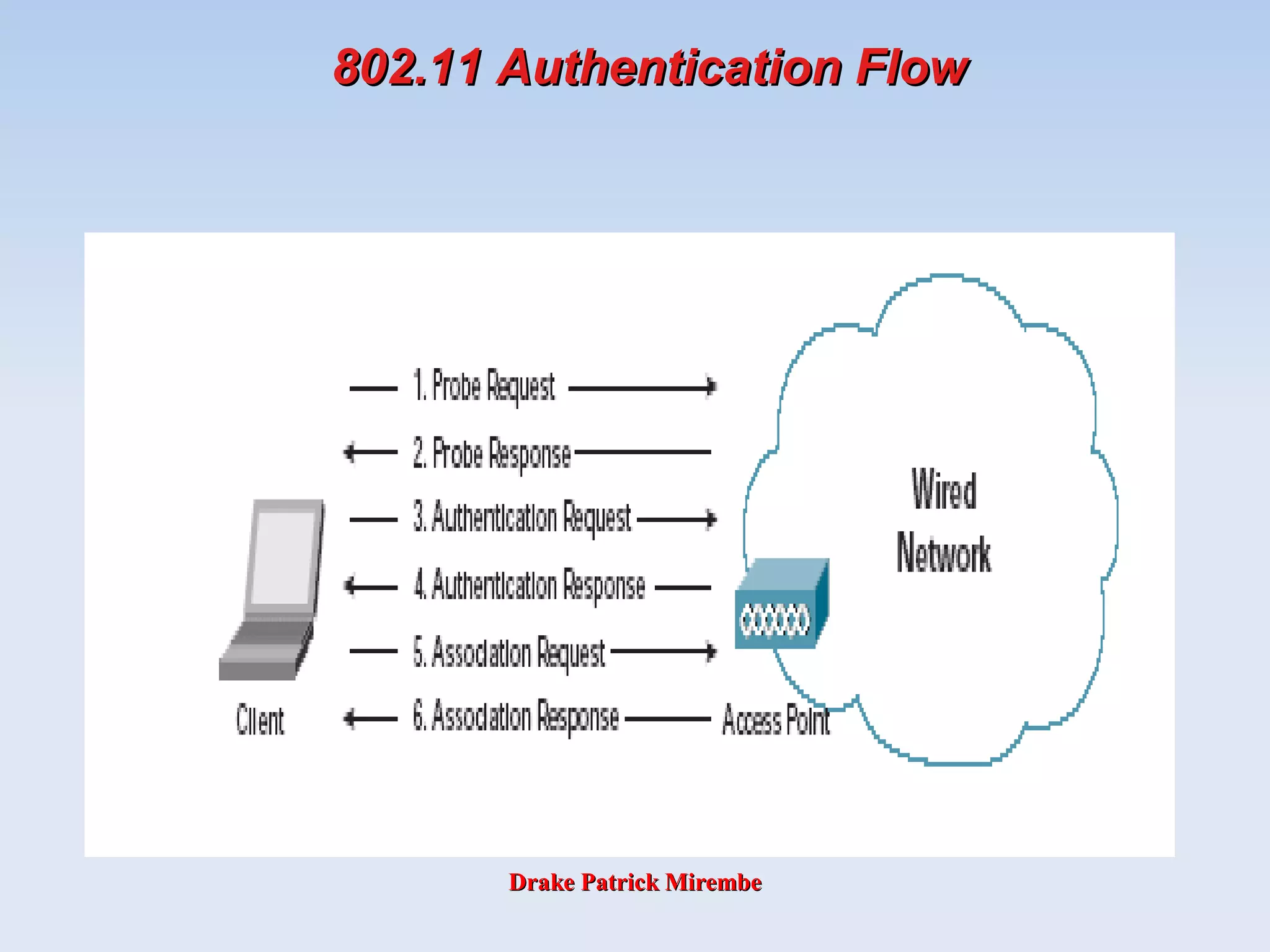
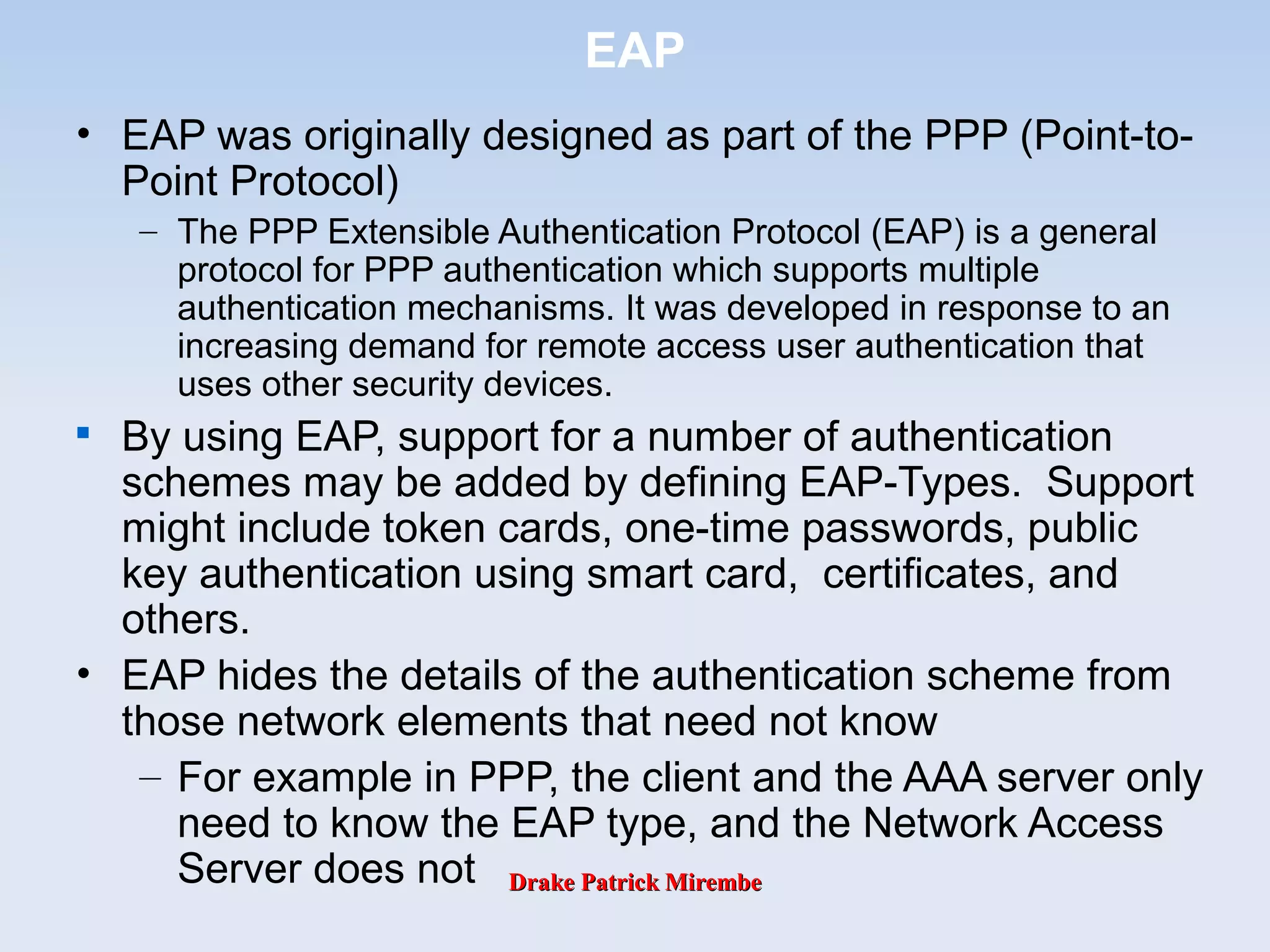
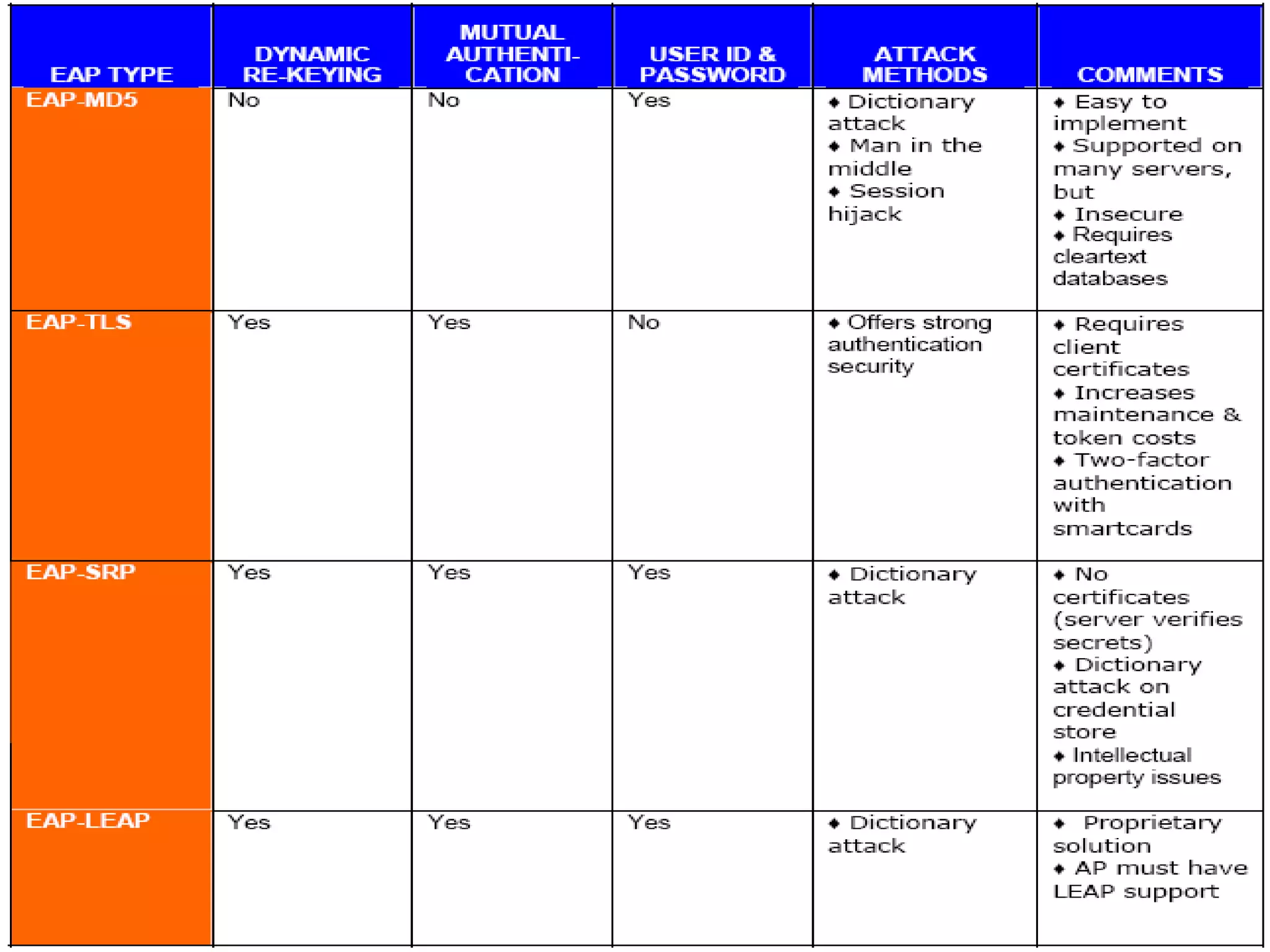
EAP Elements
EAP basically consists of four different protocol
elements:
Request packets (from Authenticator [AP] to client
[Supplicant])
Response packets (from Client to Authenticator)
Success packet
Failure packet
May originate from an AAA server
{](https://image.slidesharecdn.com/bse3106-wifi-171106154406/75/Bse-3106-wifi-87-2048.jpg)