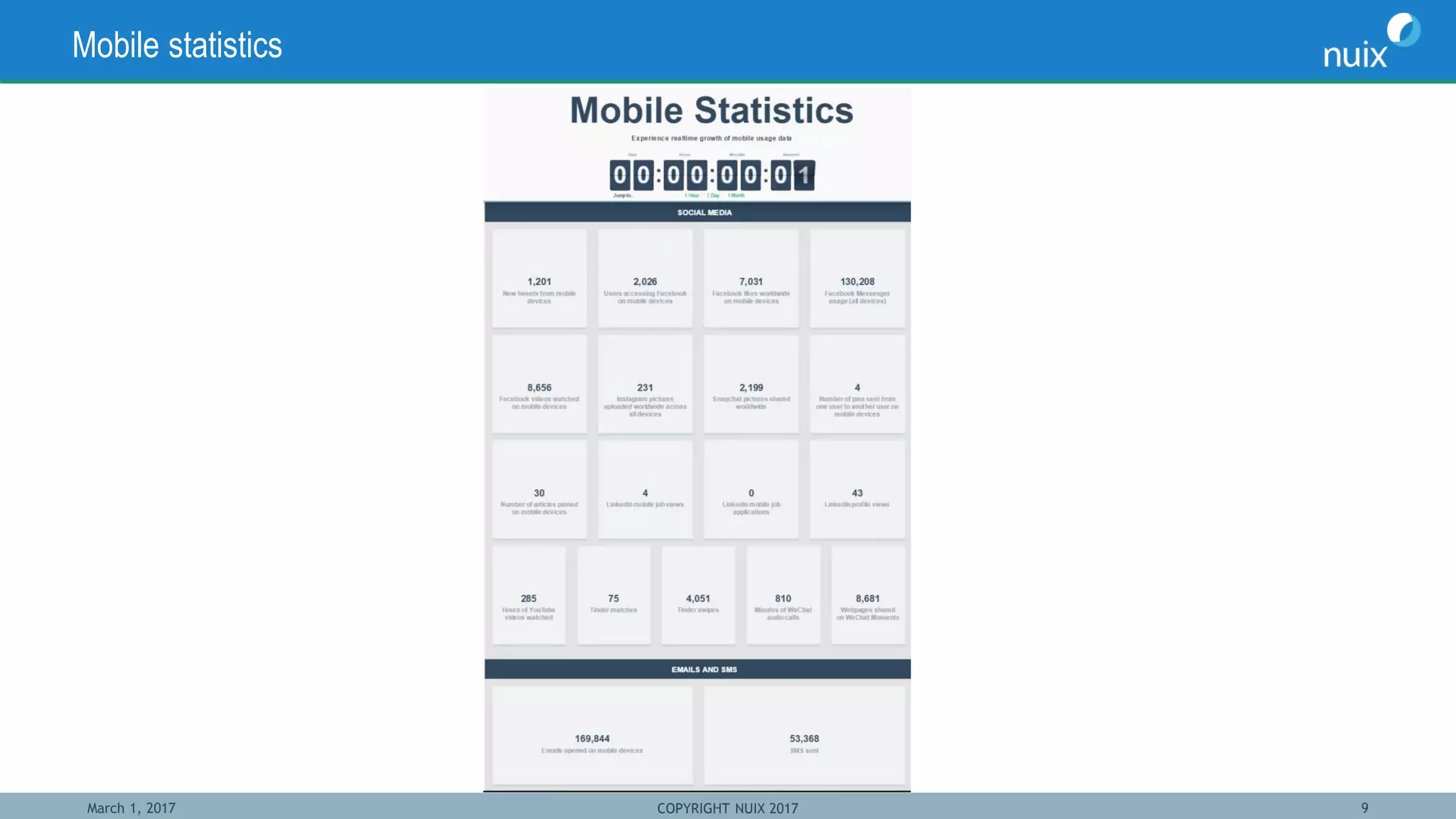
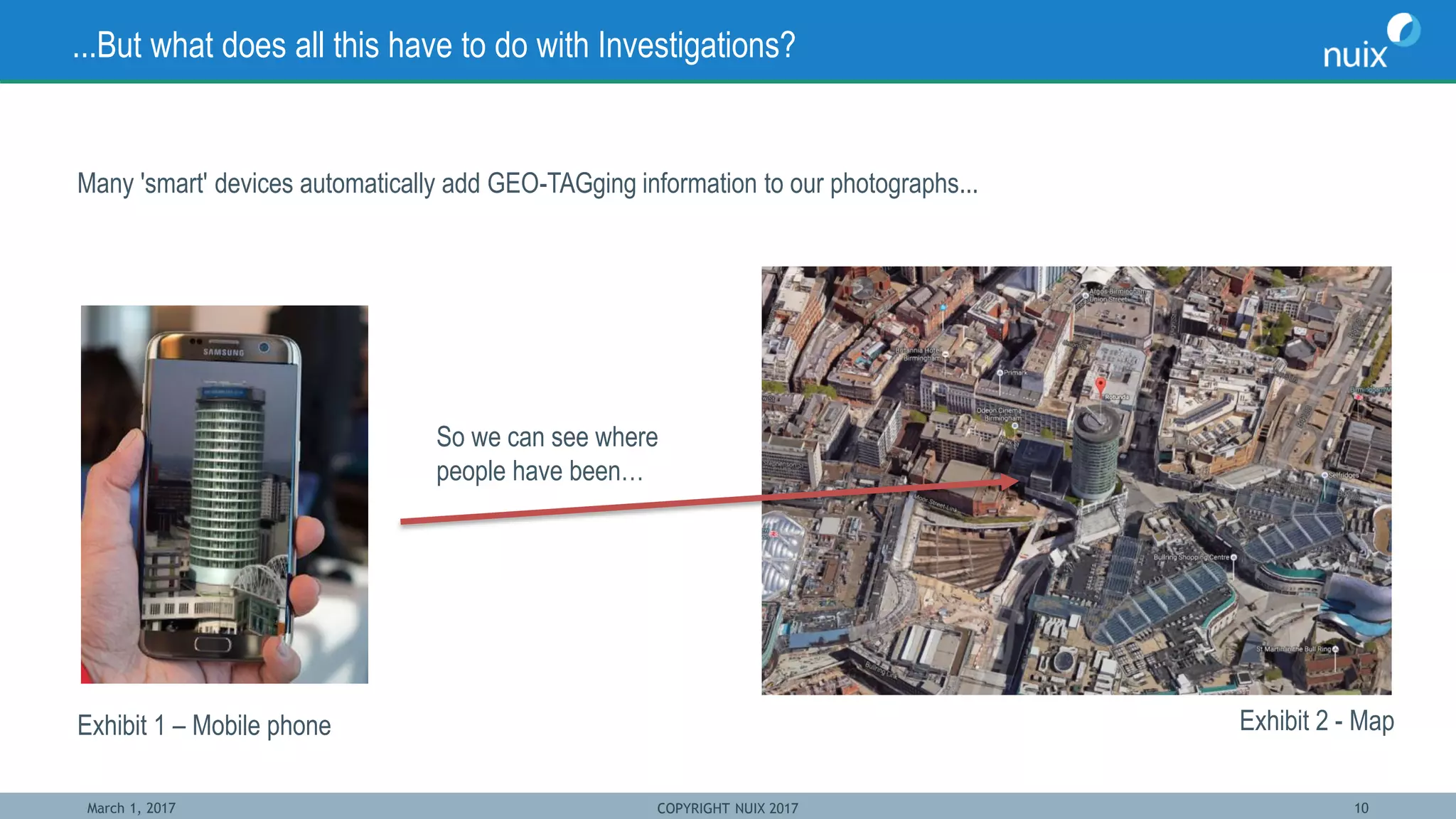
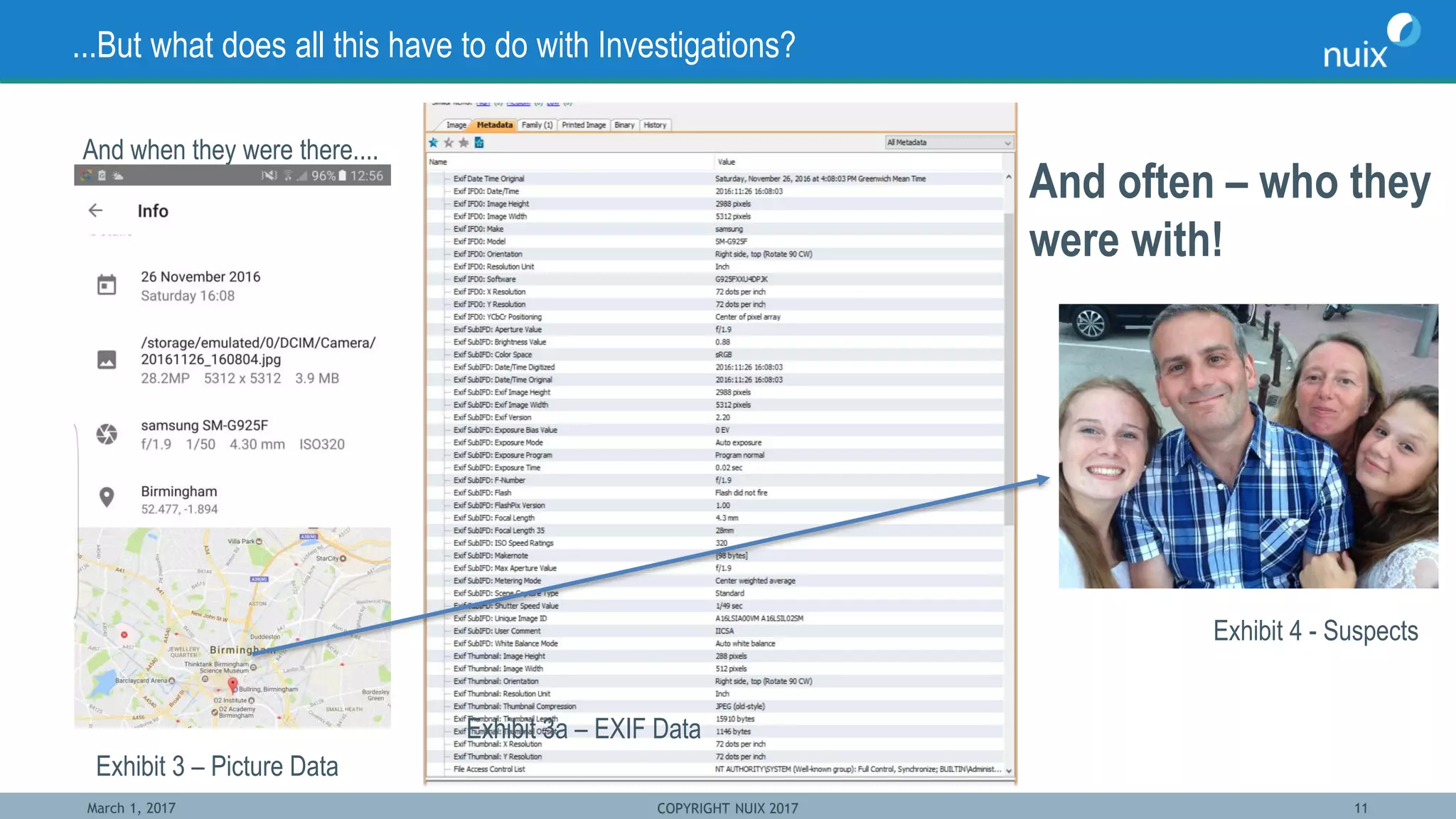
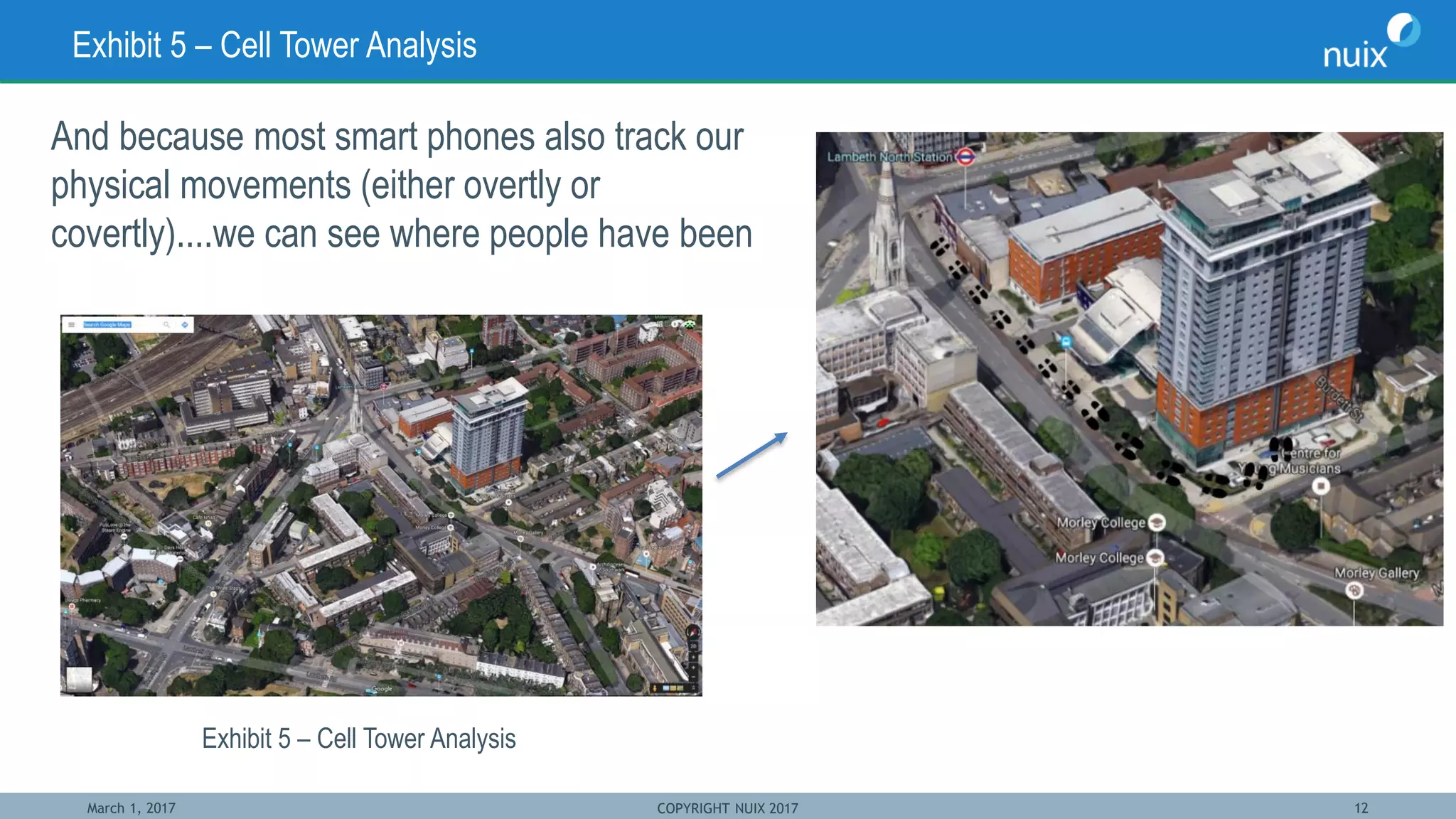
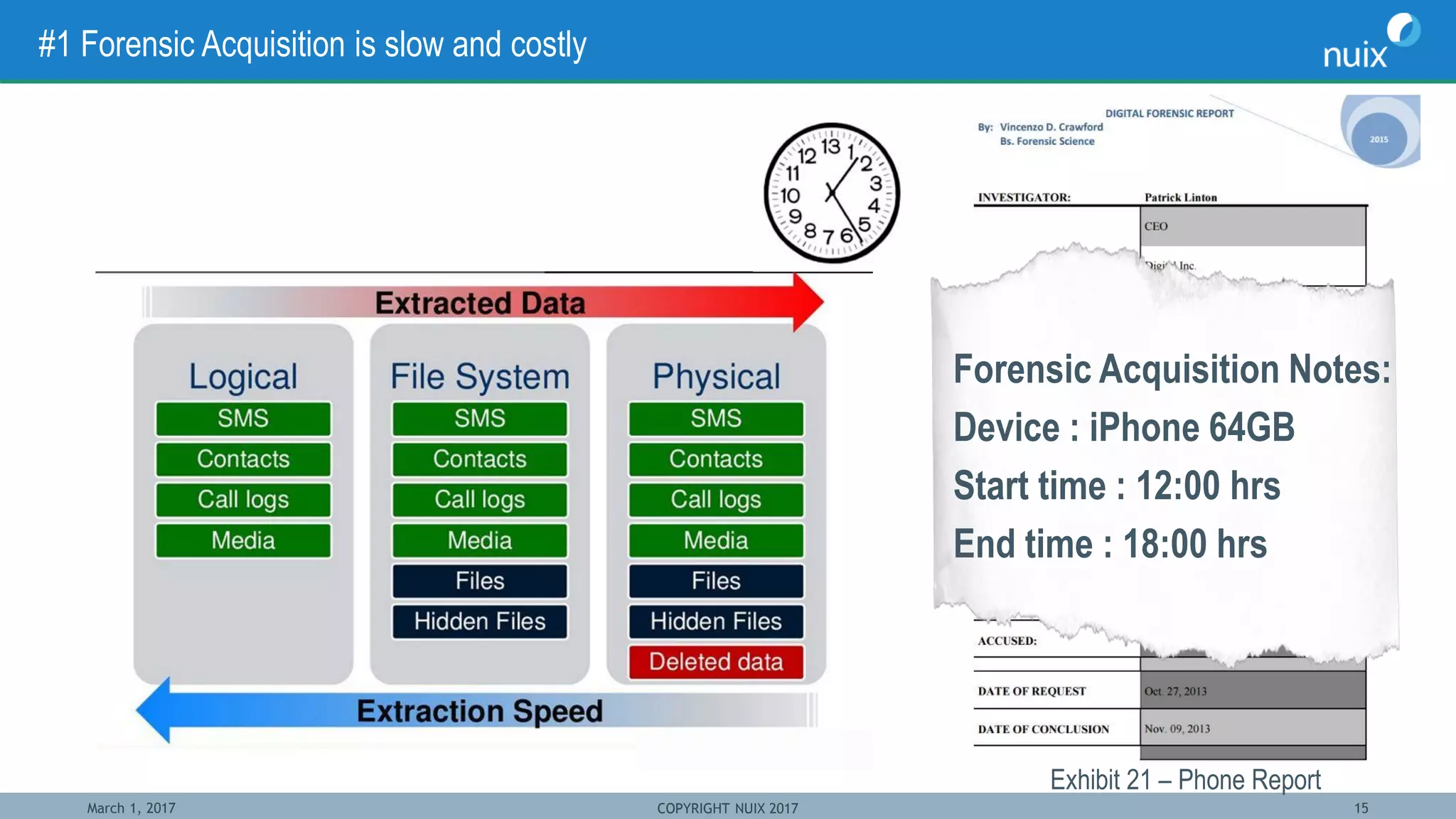
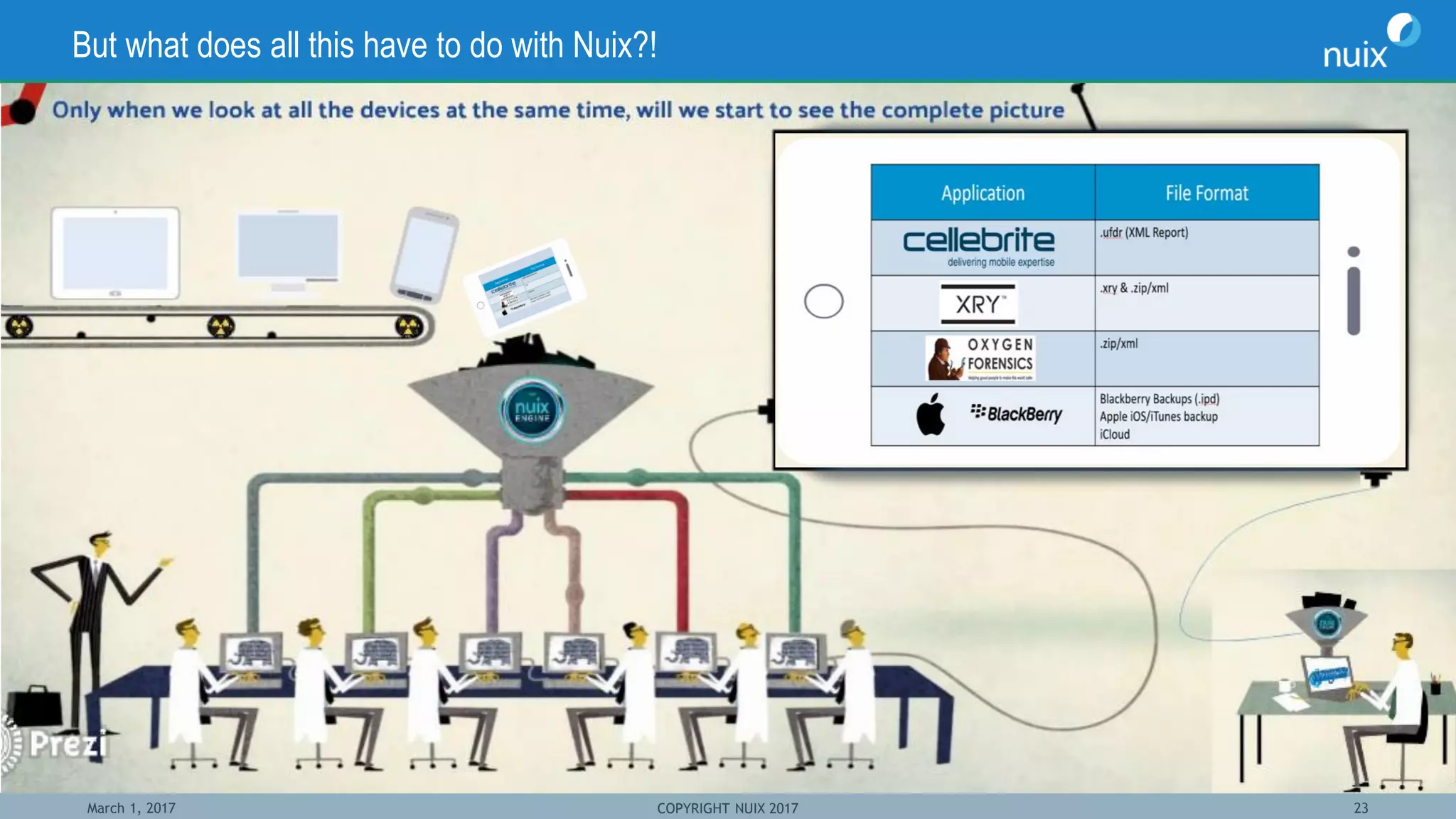
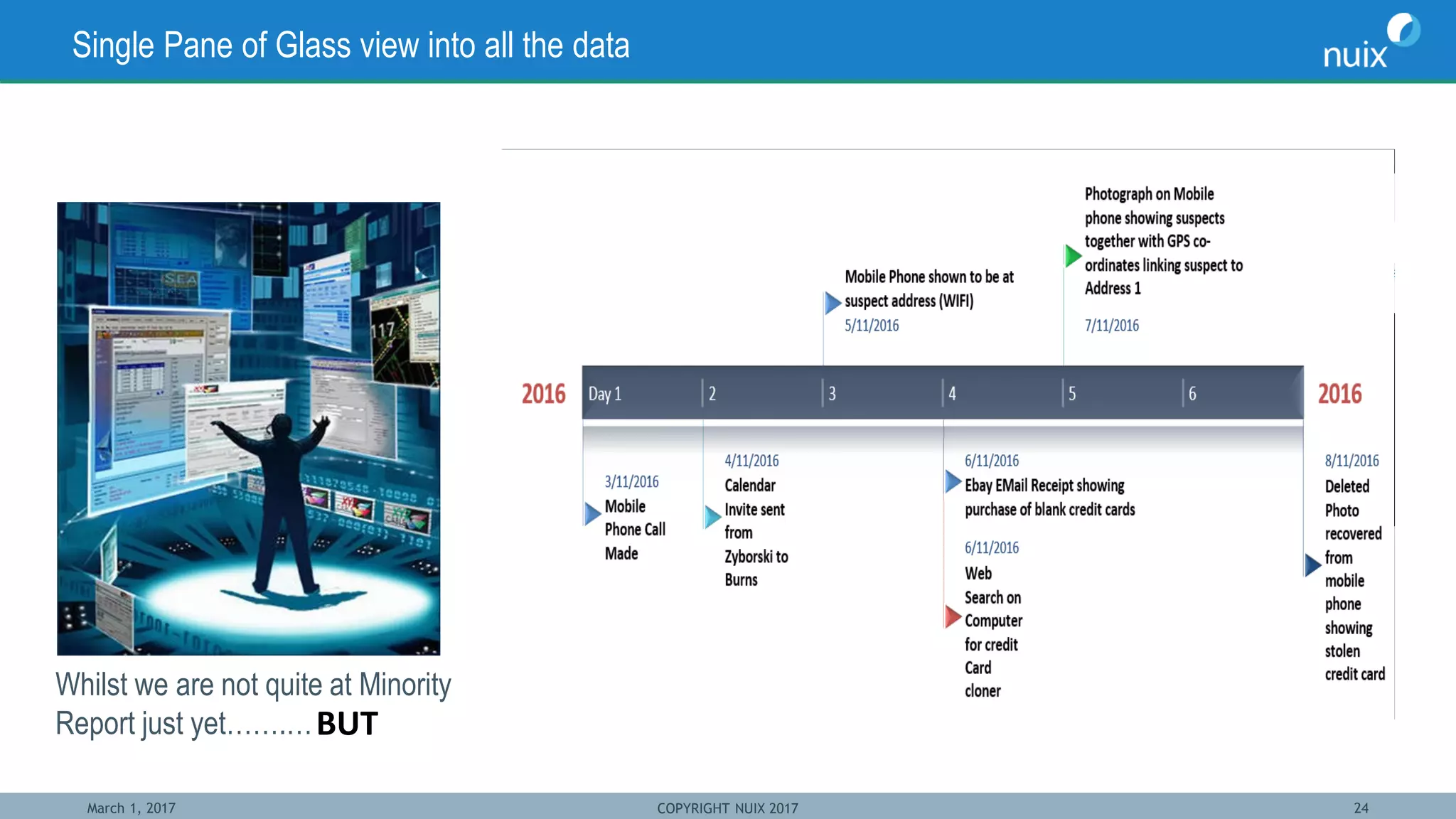
The document discusses the challenges and techniques in bridging mobile and computer forensics, highlighting the expertise of key speakers from Nuix and their solutions for digital investigations. It emphasizes the increasing reliance on mobile devices in forensic investigations, the difficulties in forensic acquisition, and the need for a unified approach to examine evidence across multiple devices. Case studies illustrate how mobile device data can support investigations, demonstrating the importance of integrating these tools to streamline the investigative process.