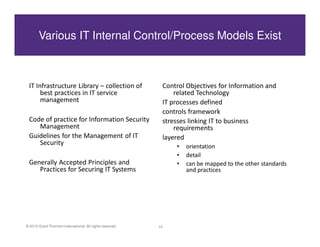
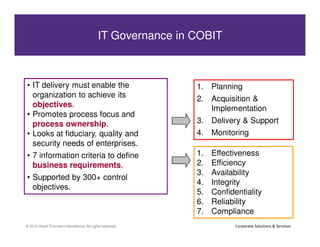
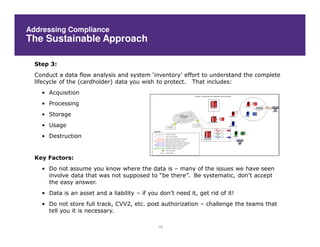
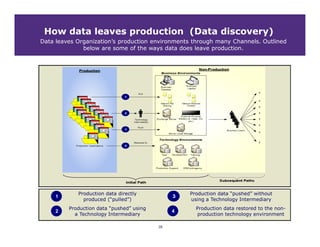
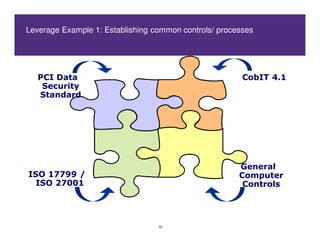
This document discusses achieving effective compliance with the Payment Card Industry Data Security Standard (PCI DSS). It begins by outlining some of the challenges organizations face in securing sensitive data like credit card information. It then provides background on the development of PCI standards in response to significant fraud losses. The document notes that compliance alone does not equal security, and that organizations often take a minimal approach or see compliance as a "check the box" exercise rather than part of an overall security strategy. It emphasizes the need for a holistic, risk-based approach rather than focusing solely on technical controls or compliance. Finally, it suggests some lessons learned and ways to move forward, including understanding data flows, limiting access, and building value beyond just certification.