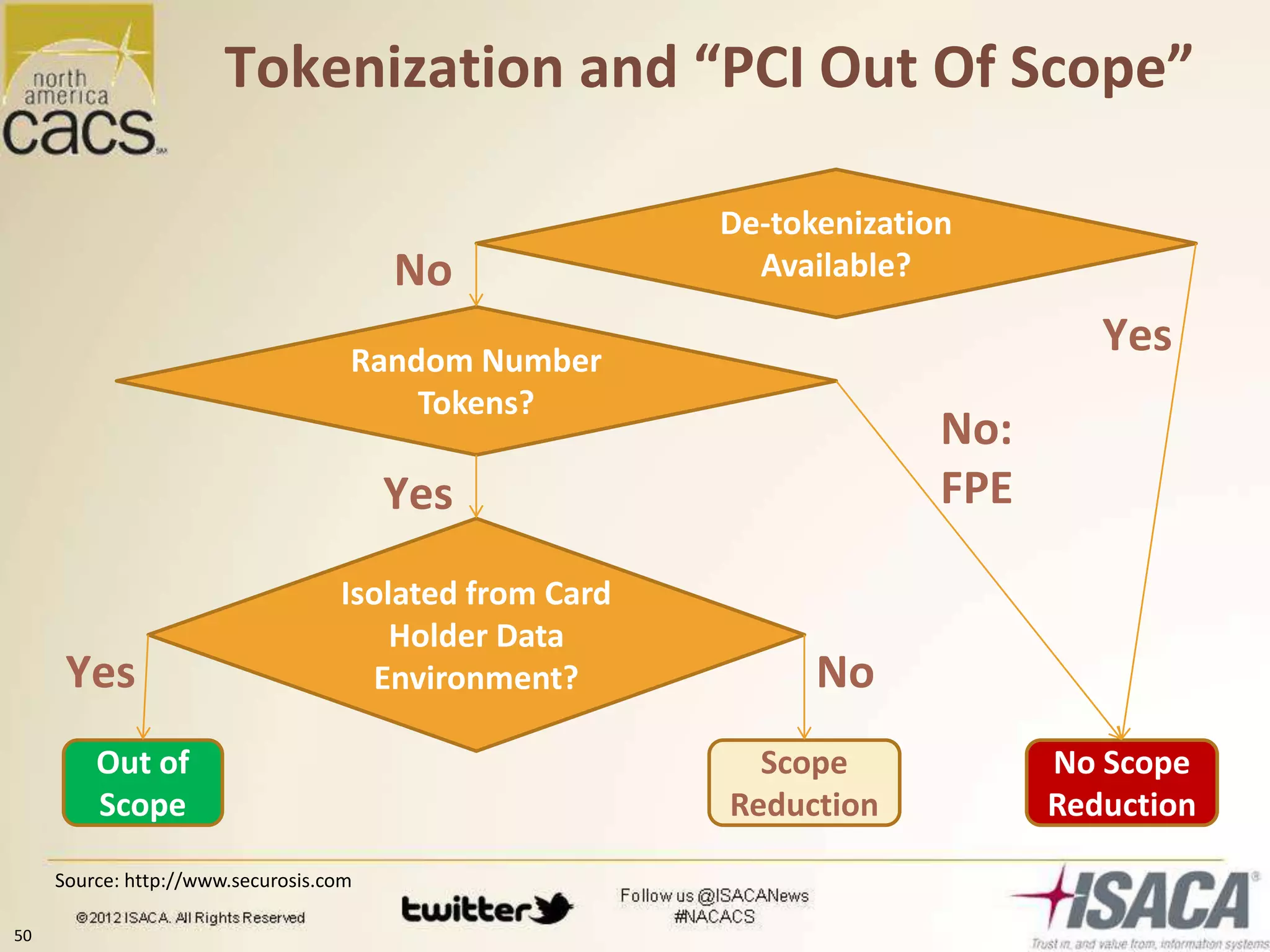
Ulf Mattsson, CTO of Protegrity, discusses securing data through tokenization. He reviews threats to data like SQL injection attacks and organized criminal groups stealing data. Case studies show how tokenization reduces PCI compliance costs and improves security and performance compared to encryption. Vaultless tokenization provides unlimited scalability without collateral impacts. Tokenization is recommended over encryption for securing structured and unstructured data as well as credit cards, medical records, and other sensitive information. Industry guidelines provide best practices for token generation and management.