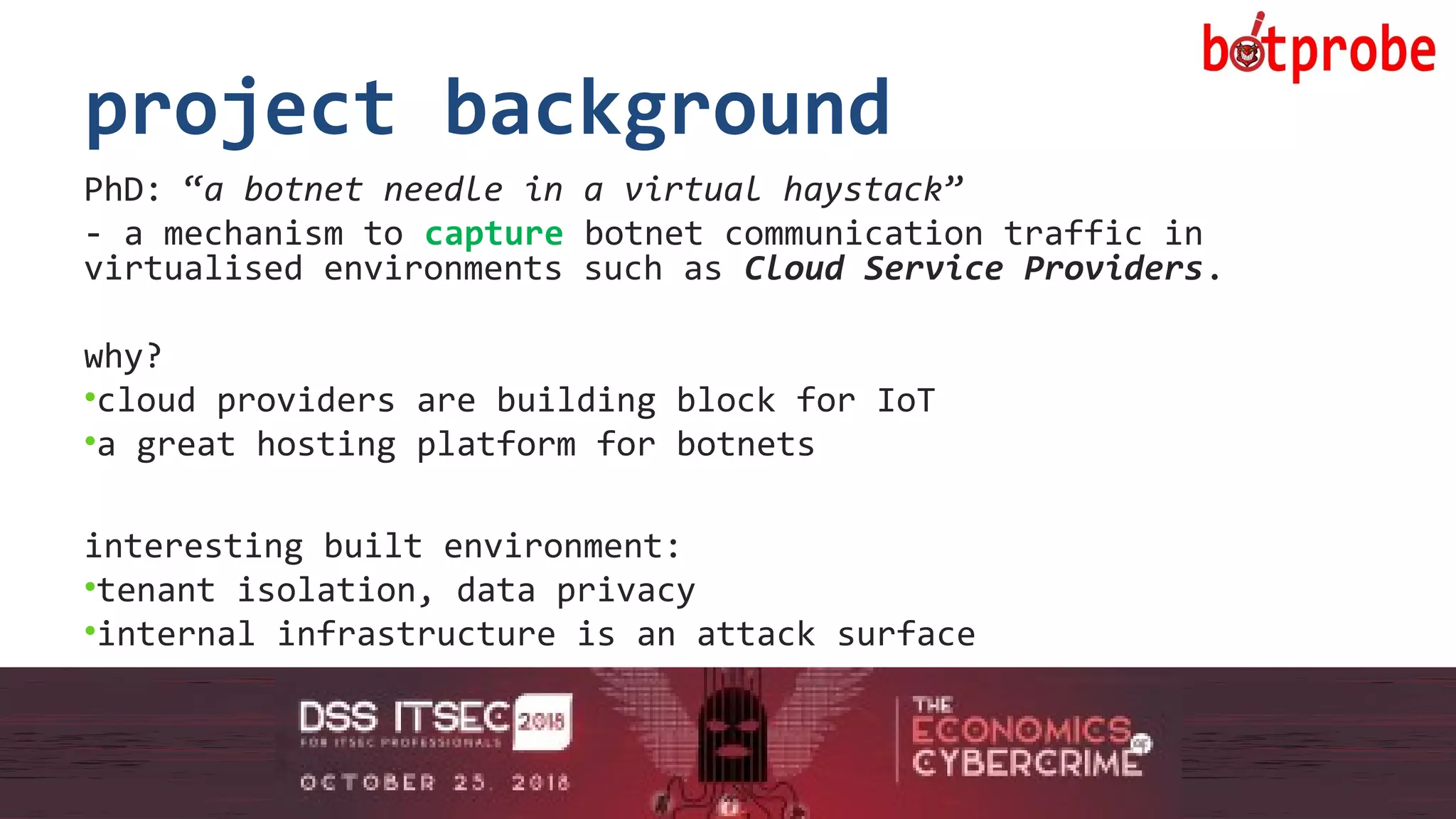
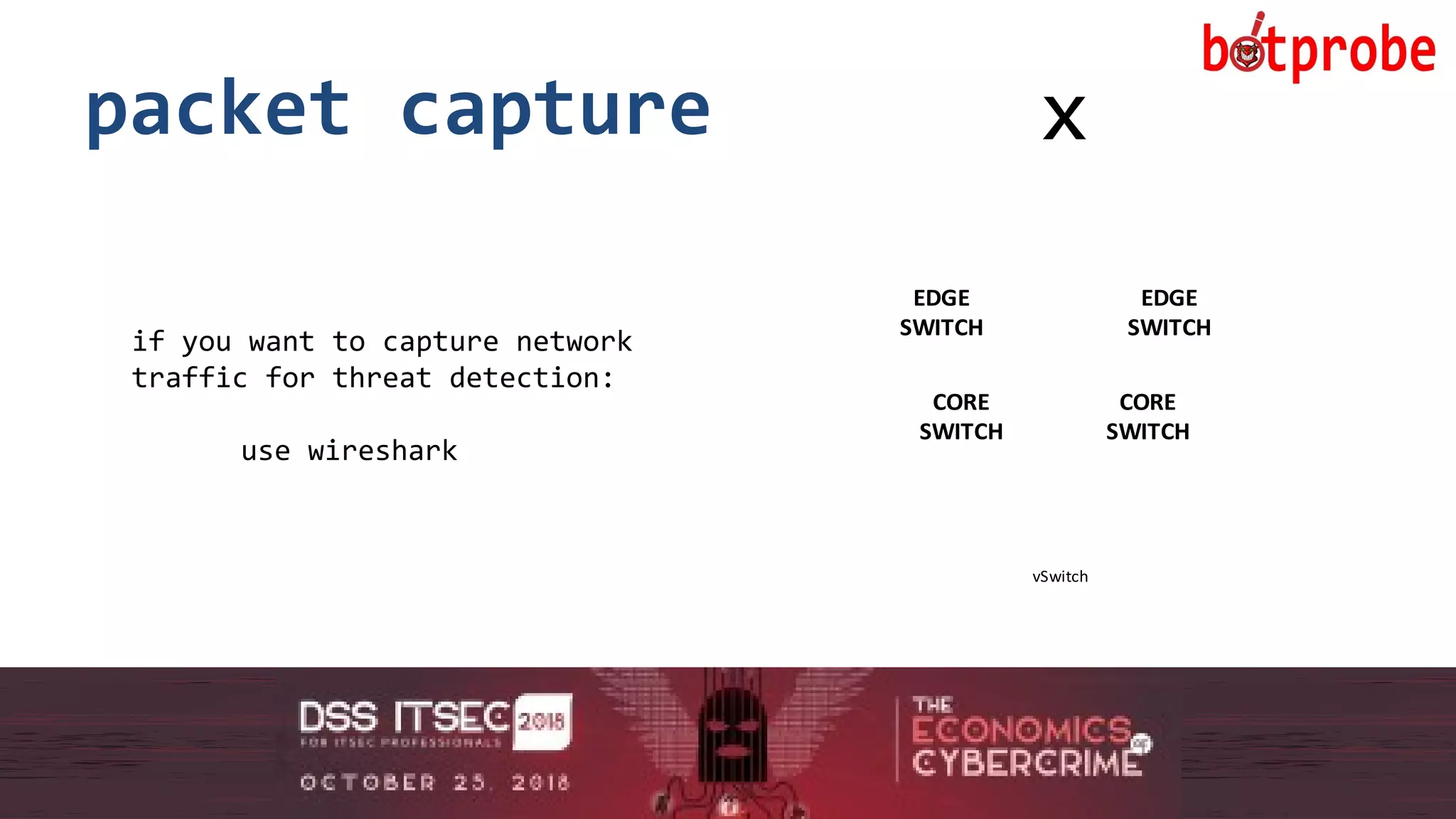
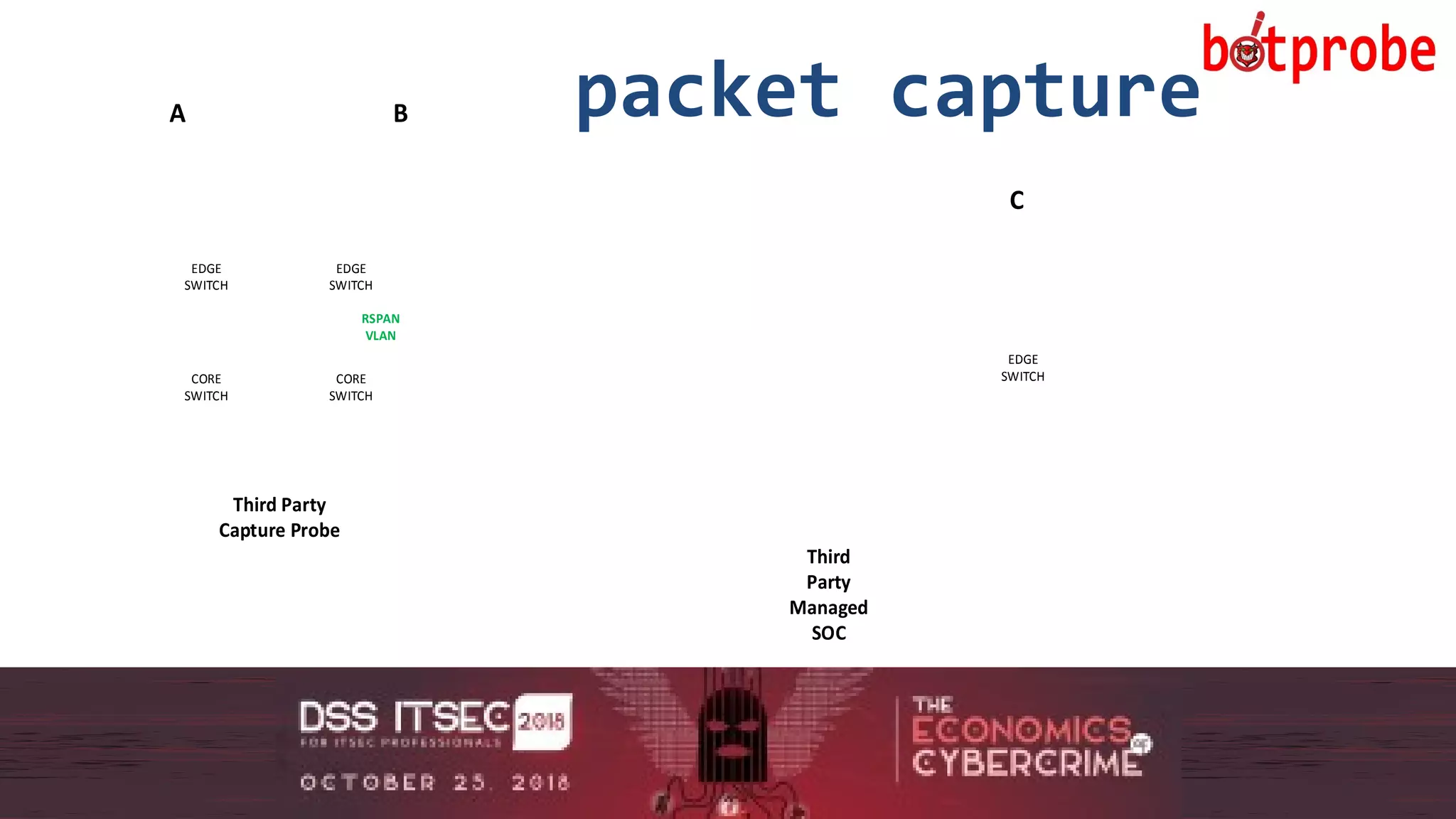
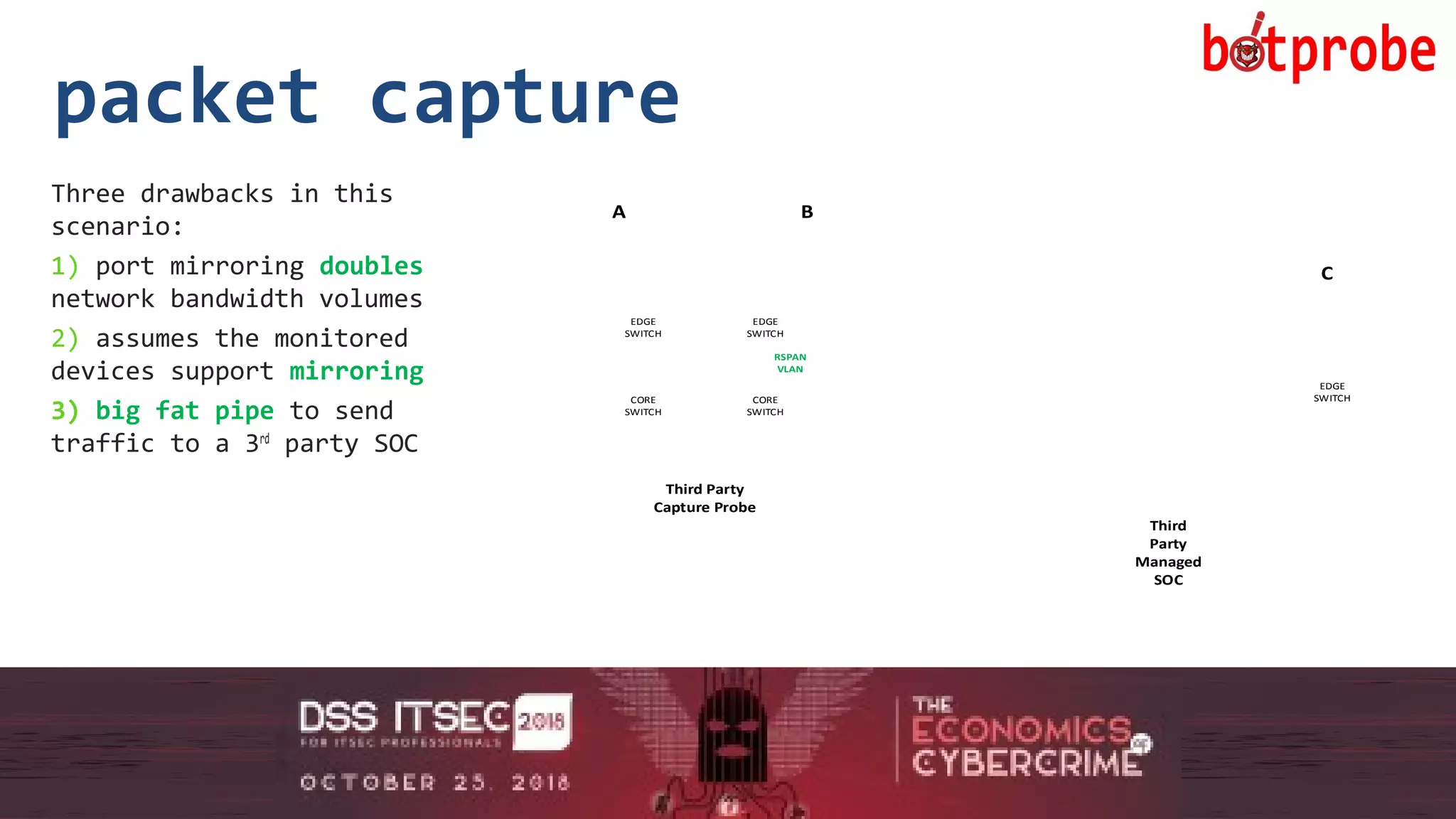
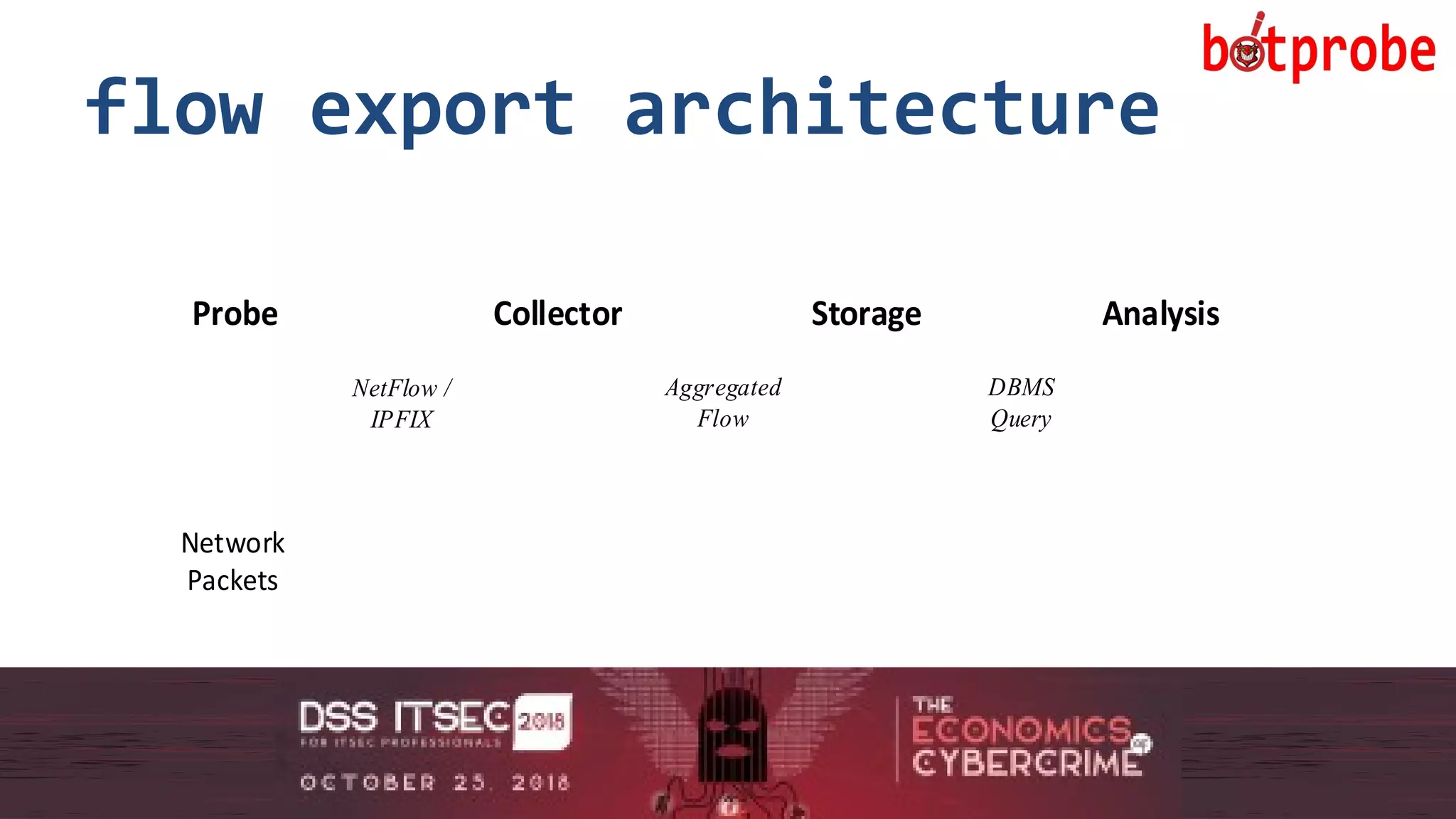
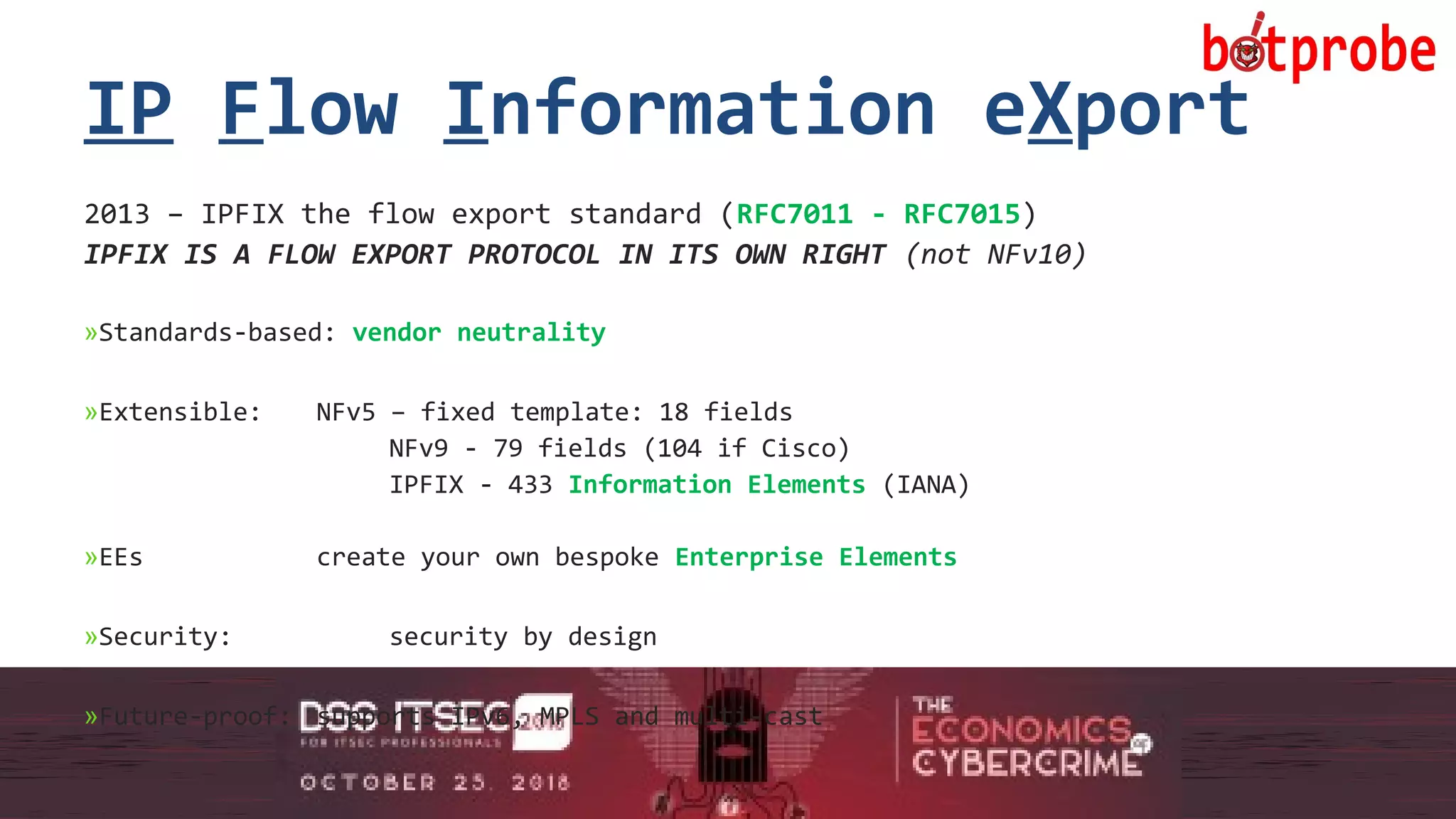
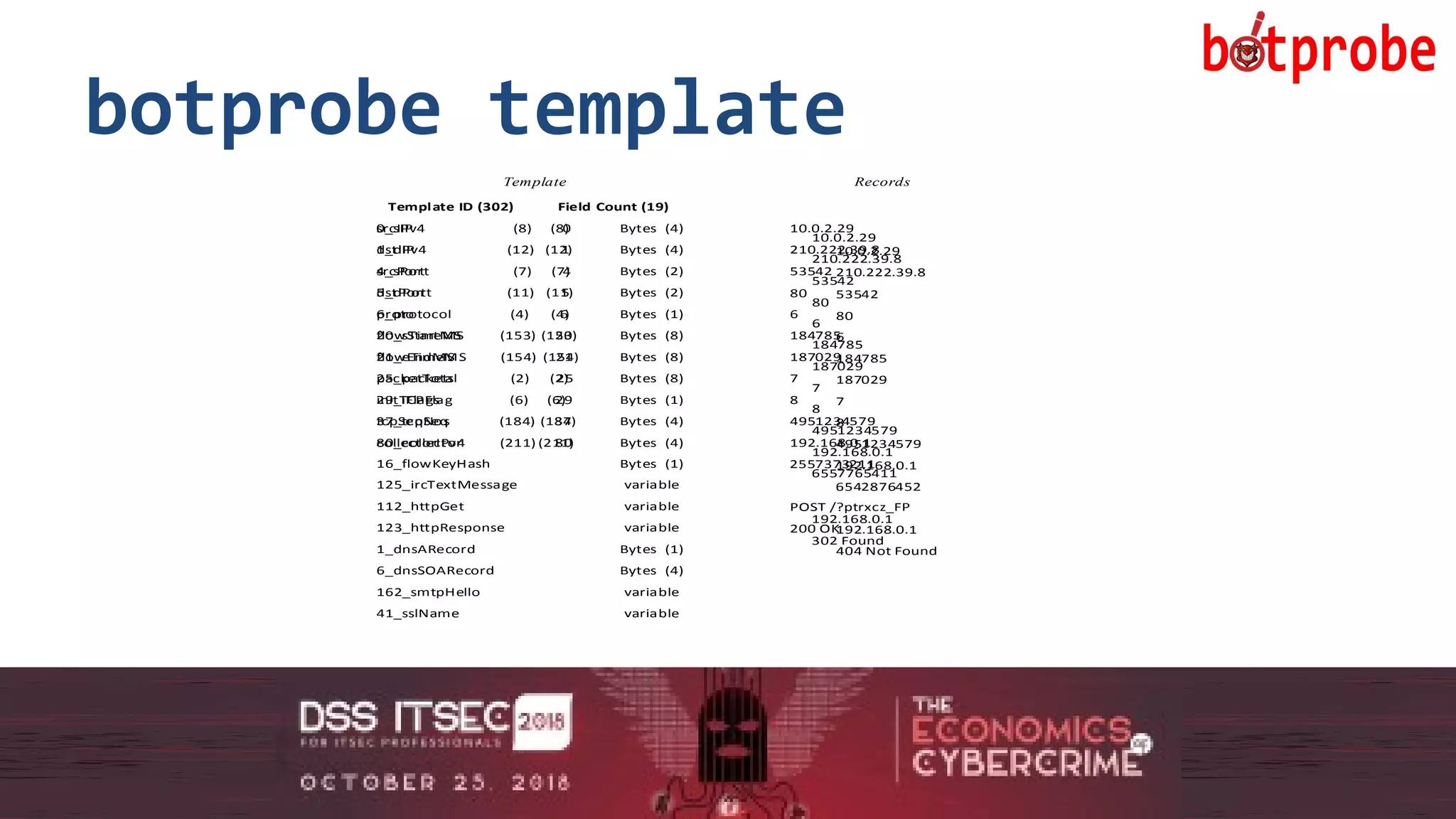
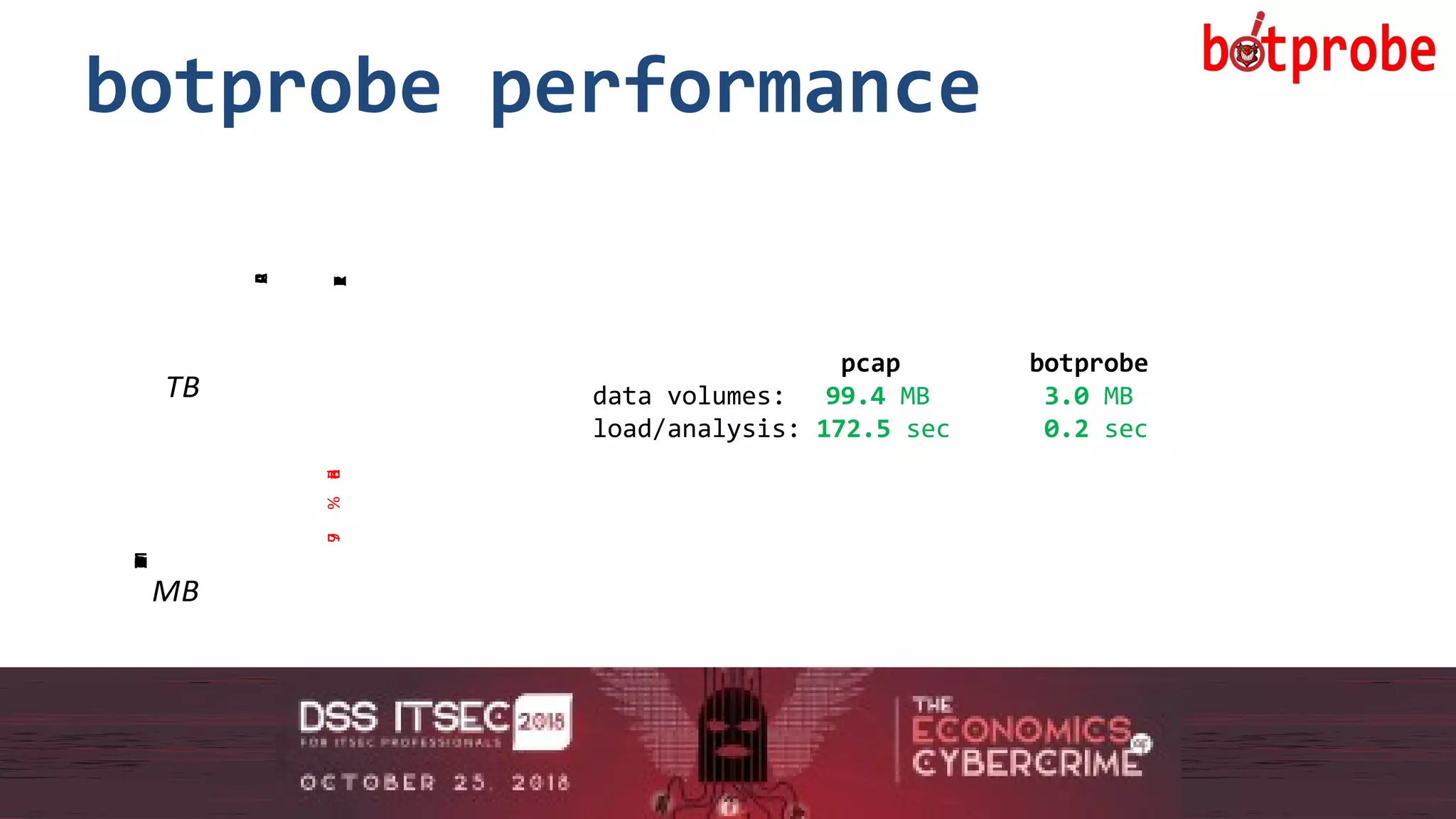
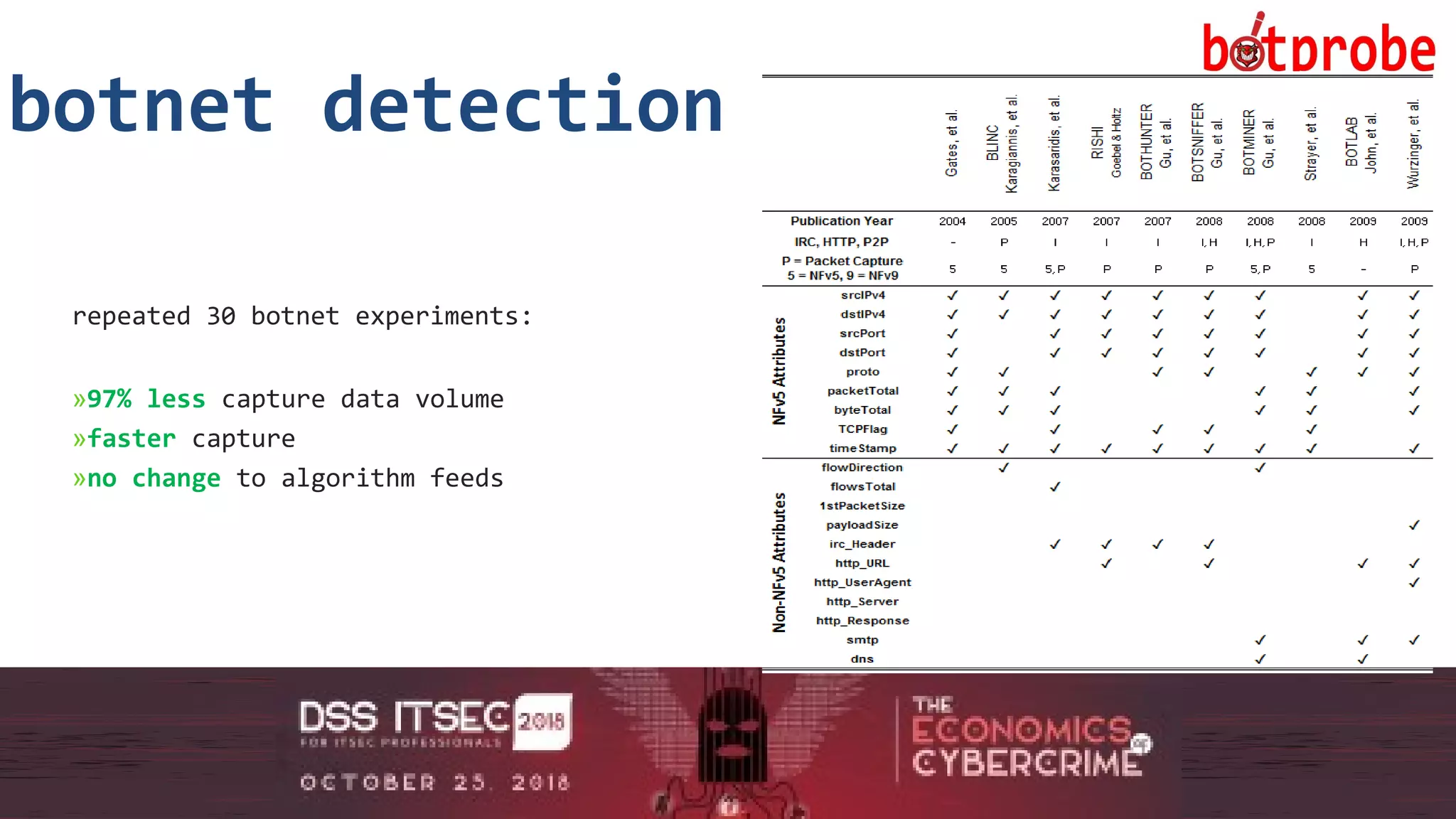
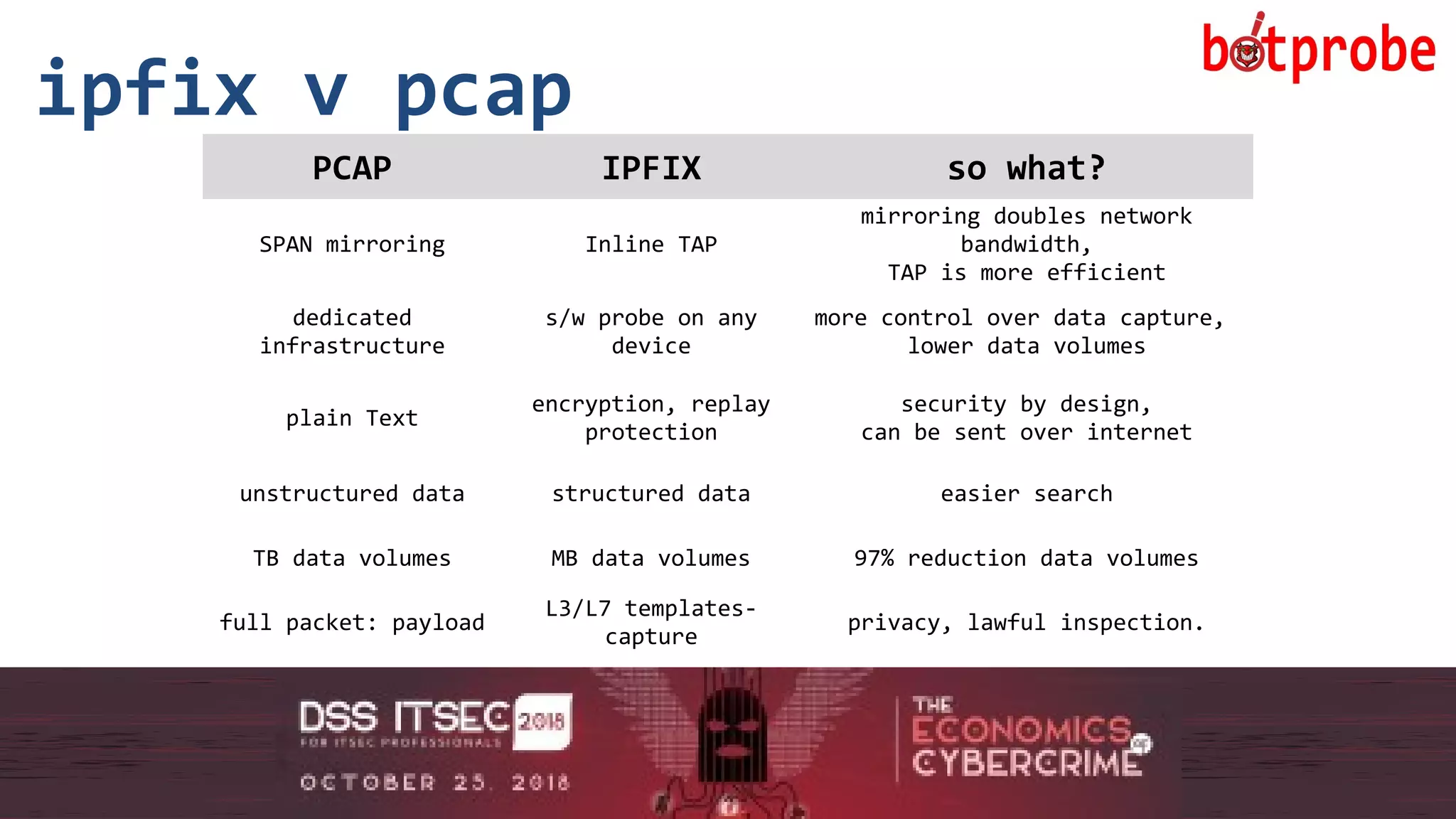
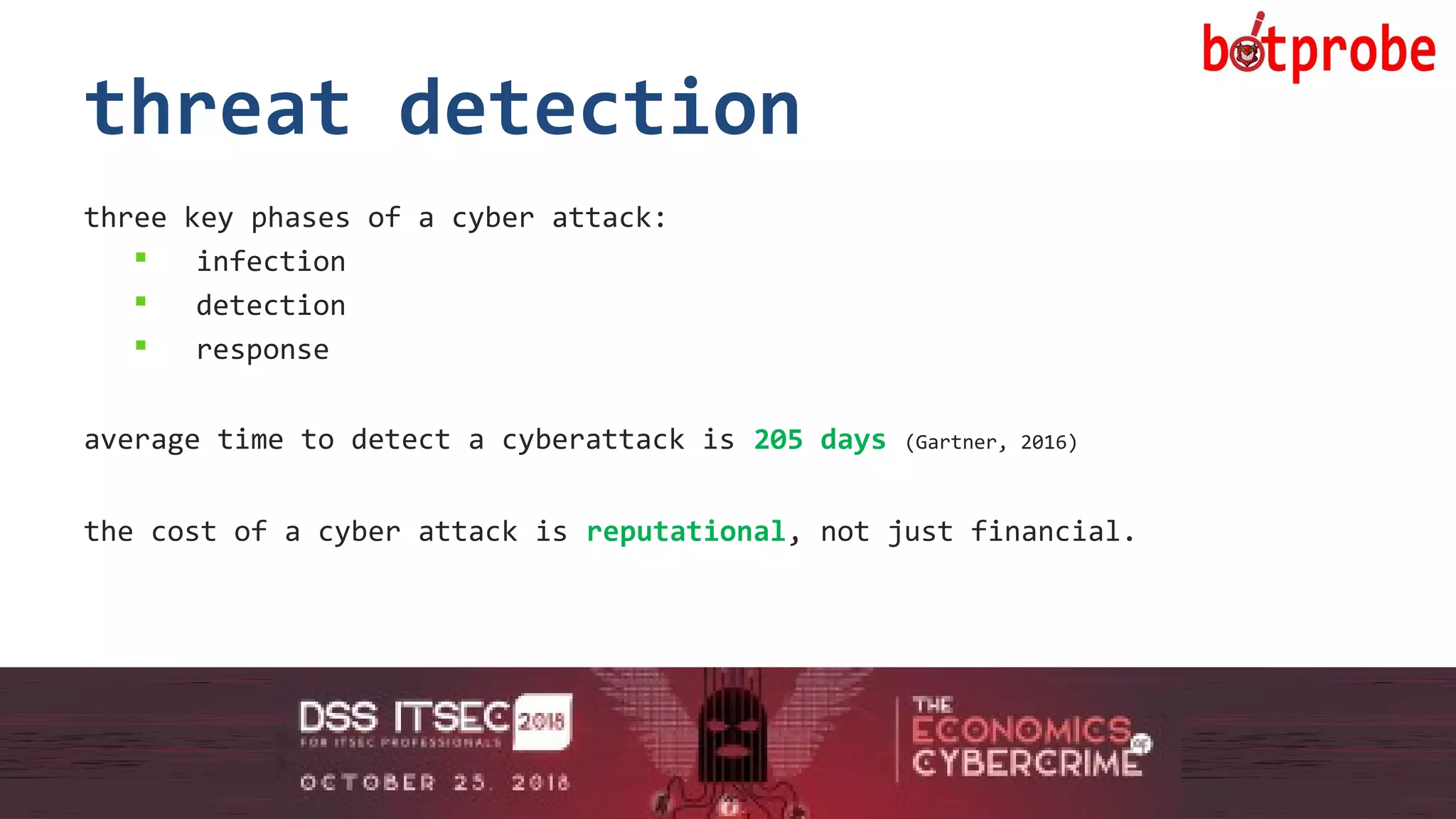
The document presents the Botprobe project, which focuses on a method to capture botnet communication traffic in cloud environments, addressing challenges in threat detection and data capture efficiency. It outlines the evolution of flow protocols from SNMP to IPFIX, emphasizing a significant reduction in data volumes and faster analysis capabilities compared to traditional methods. The paper encourages collaboration and further exploration in utilizing IPFIX templates for various malicious traffic detection applications.



![9
history lesson
1996 – Cisco patented NetFlow
2002 – NetFlow v5
2004 – NetFlow v9
NetFlow was designed for application to network management,
but has limitations when applied to threat detection:
•NFv5 has 18 fixed fields (only 10 useful!)
•header information ONLY
•transport layer is UDP only
•no support for: MPLS, IPv6, VLANs, MAC addresses
•[typically 1:50 sampling rates]
Cisco NFv9 supports (most) of these, but is proprietary.
9](https://image.slidesharecdn.com/botprobe-reducingnetworkthreatintelligencebigdata-181127132516/75/Botprobe-Reducing-network-threat-intelligence-big-data-9-2048.jpg)
![15
case studies
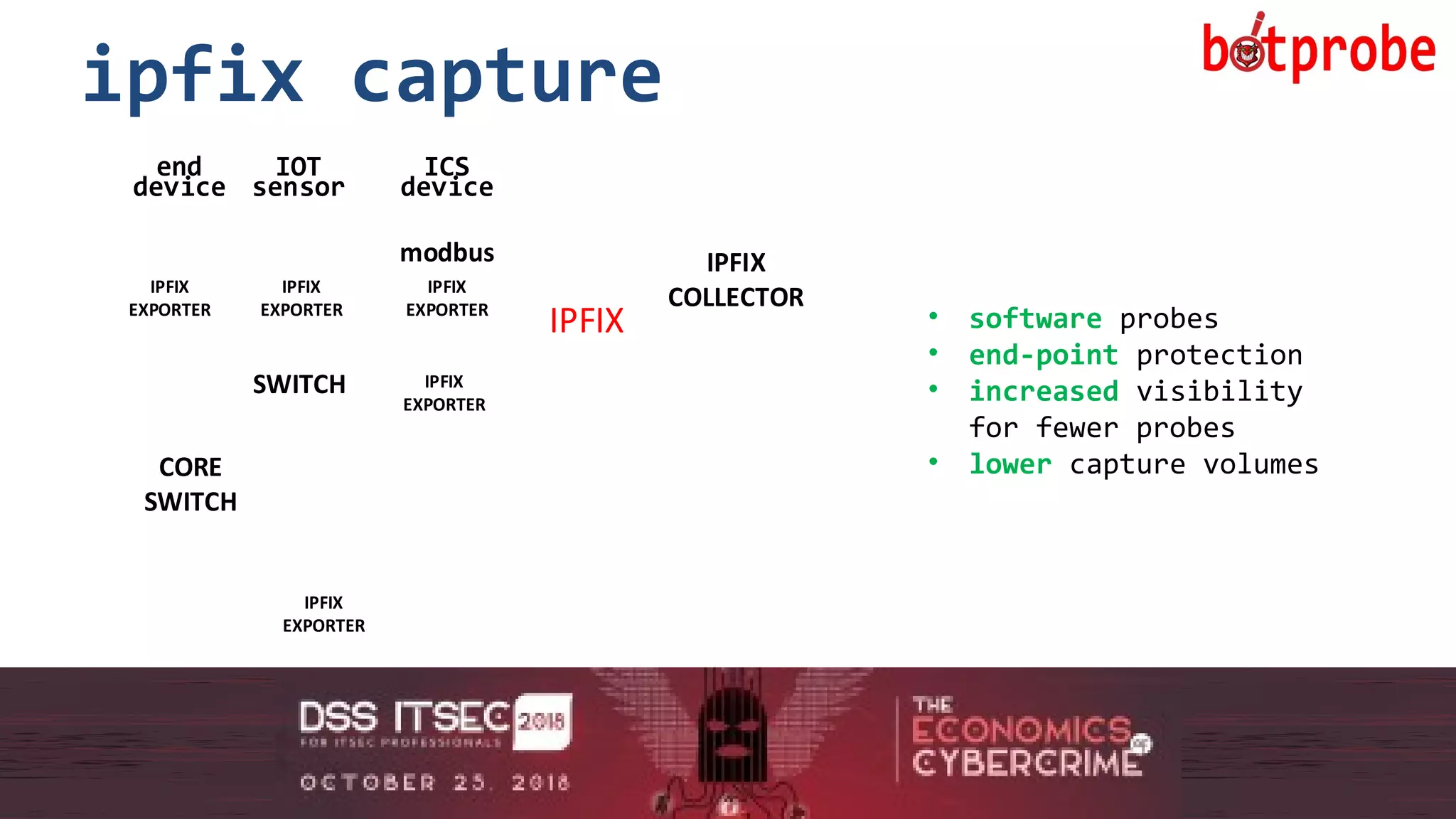
further IPFIX templates:
• botprobe : botnets
• smtpprobe : spam traffic
• httpprobe : malicious http streams
• iotprobe : malicious IoT traffic
• icsprobe : malicious Industrial Control Systems traffic
if an attribute is present in a packet [header or payload], we can capture
it.
15](https://image.slidesharecdn.com/botprobe-reducingnetworkthreatintelligencebigdata-181127132516/75/Botprobe-Reducing-network-threat-intelligence-big-data-15-2048.jpg)


![21
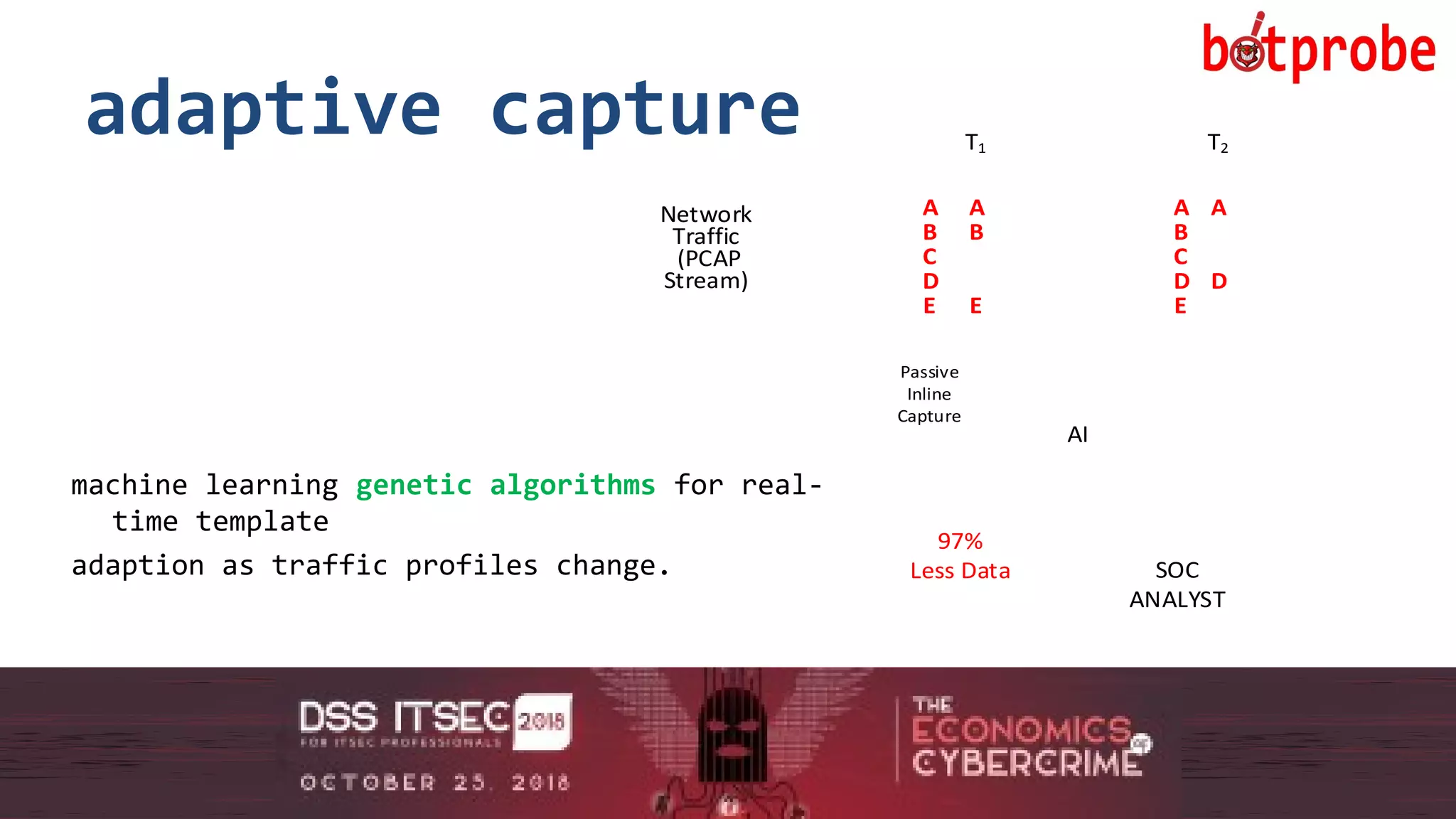
new opportunities
template extensibility + big data reduction =
• automated mitigation
• legal interception
• pre-event forensics
• pcap indexing [flow indexing]
• new detection algorithms [not just for botnets]
21](https://image.slidesharecdn.com/botprobe-reducingnetworkthreatintelligencebigdata-181127132516/75/Botprobe-Reducing-network-threat-intelligence-big-data-21-2048.jpg)
