Embed presentation
Downloaded 11 times





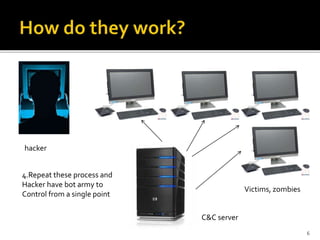


A botnet is a collection of infected computers remotely controlled by a hacker. The hacker infects computers with malicious software that allows them to communicate with a central command and control server over the internet. From this server, the hacker can send commands anonymously to the infected computers, which will then execute tasks without the owners' knowledge. To prevent infection, users should keep software updated, use firewalls, and avoid clicking links in suspicious emails.






