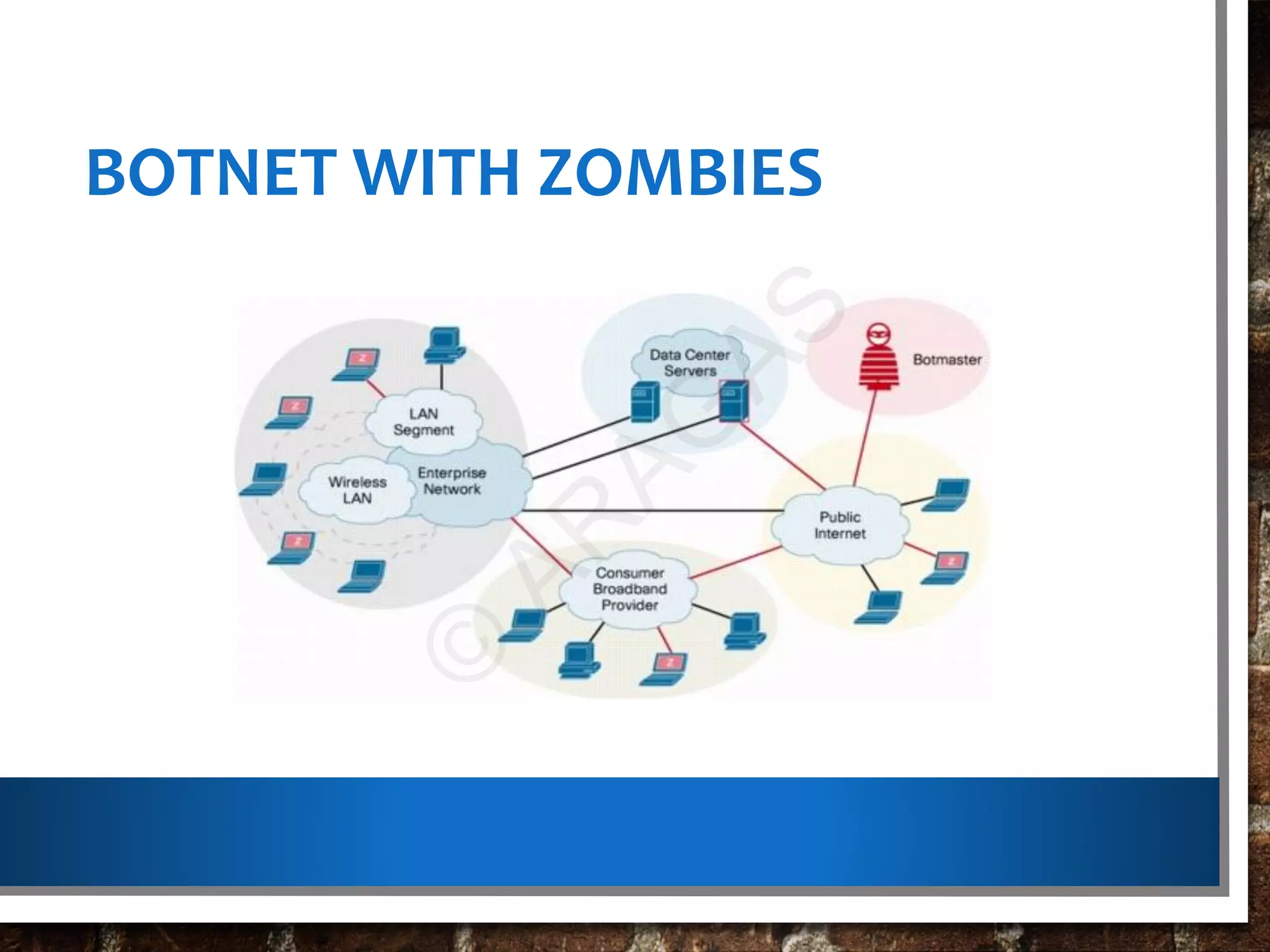
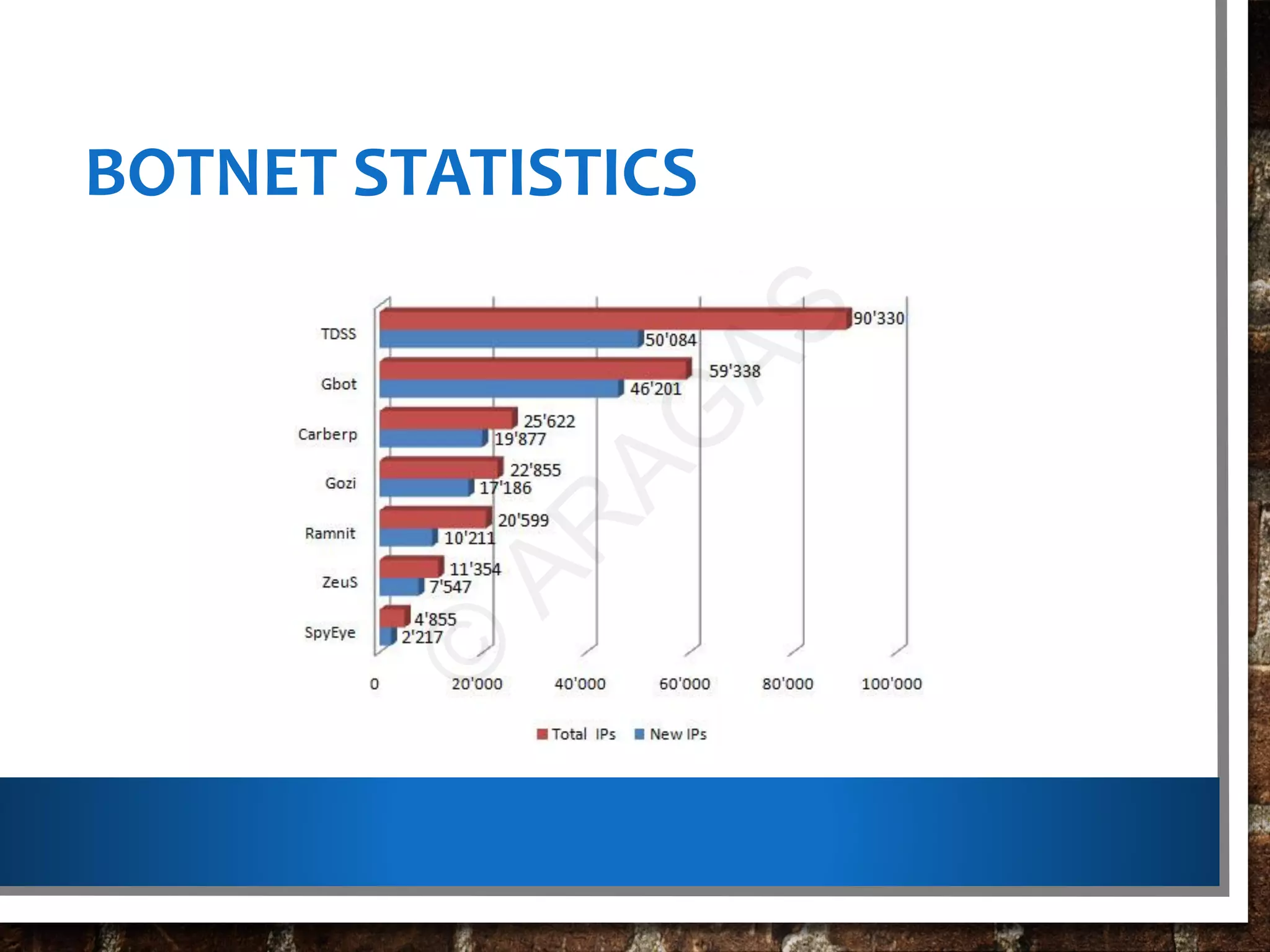
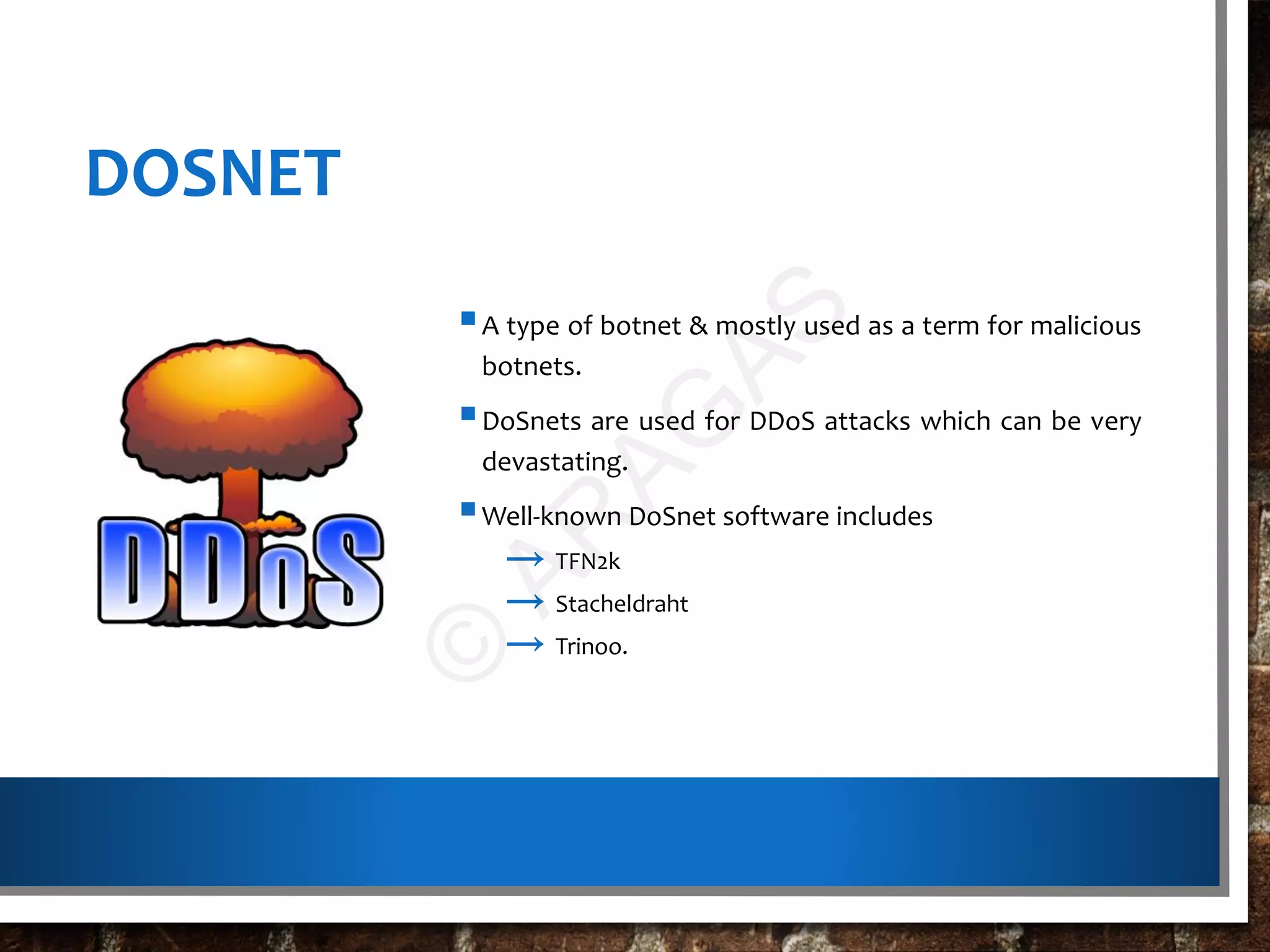
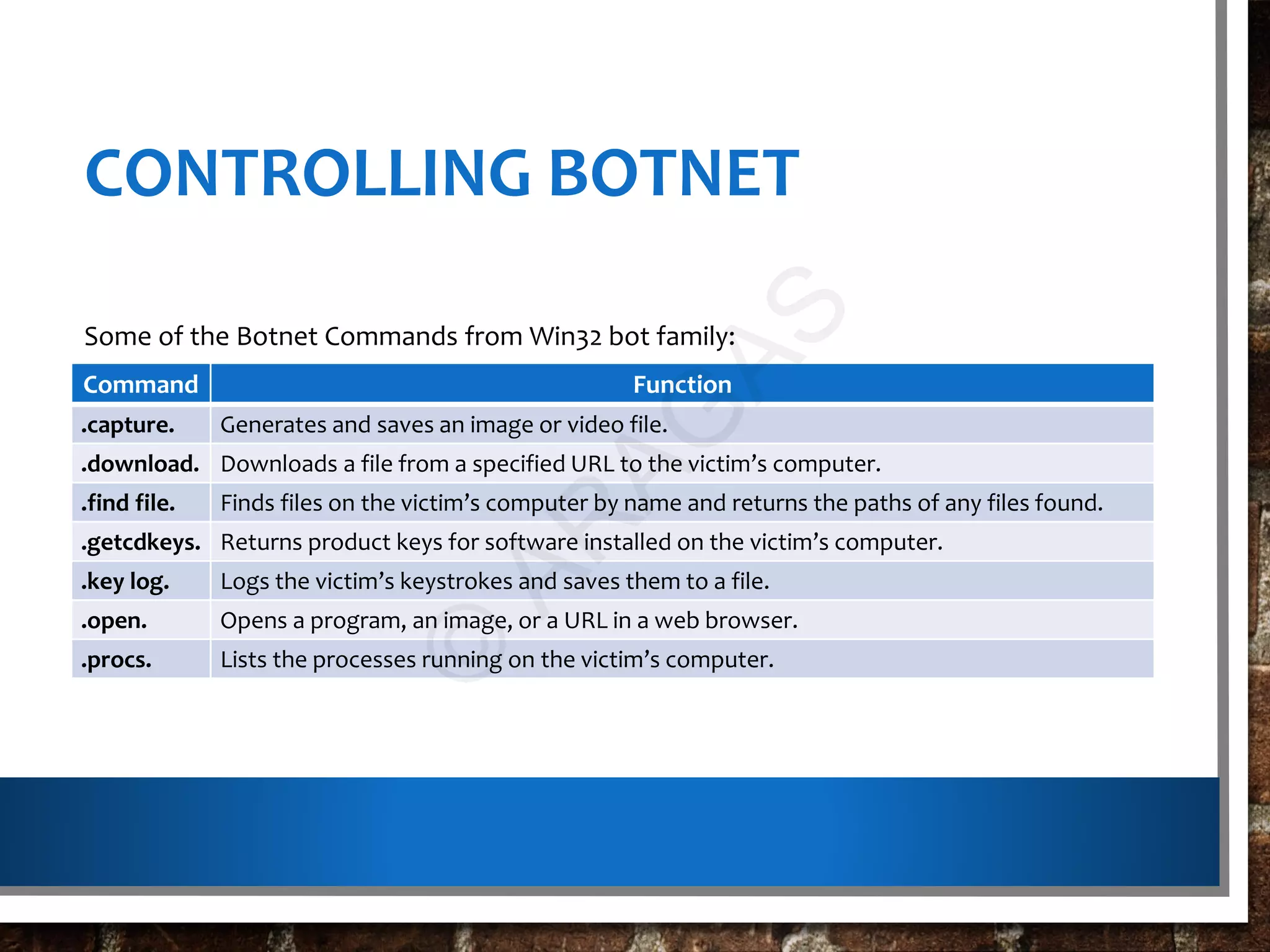
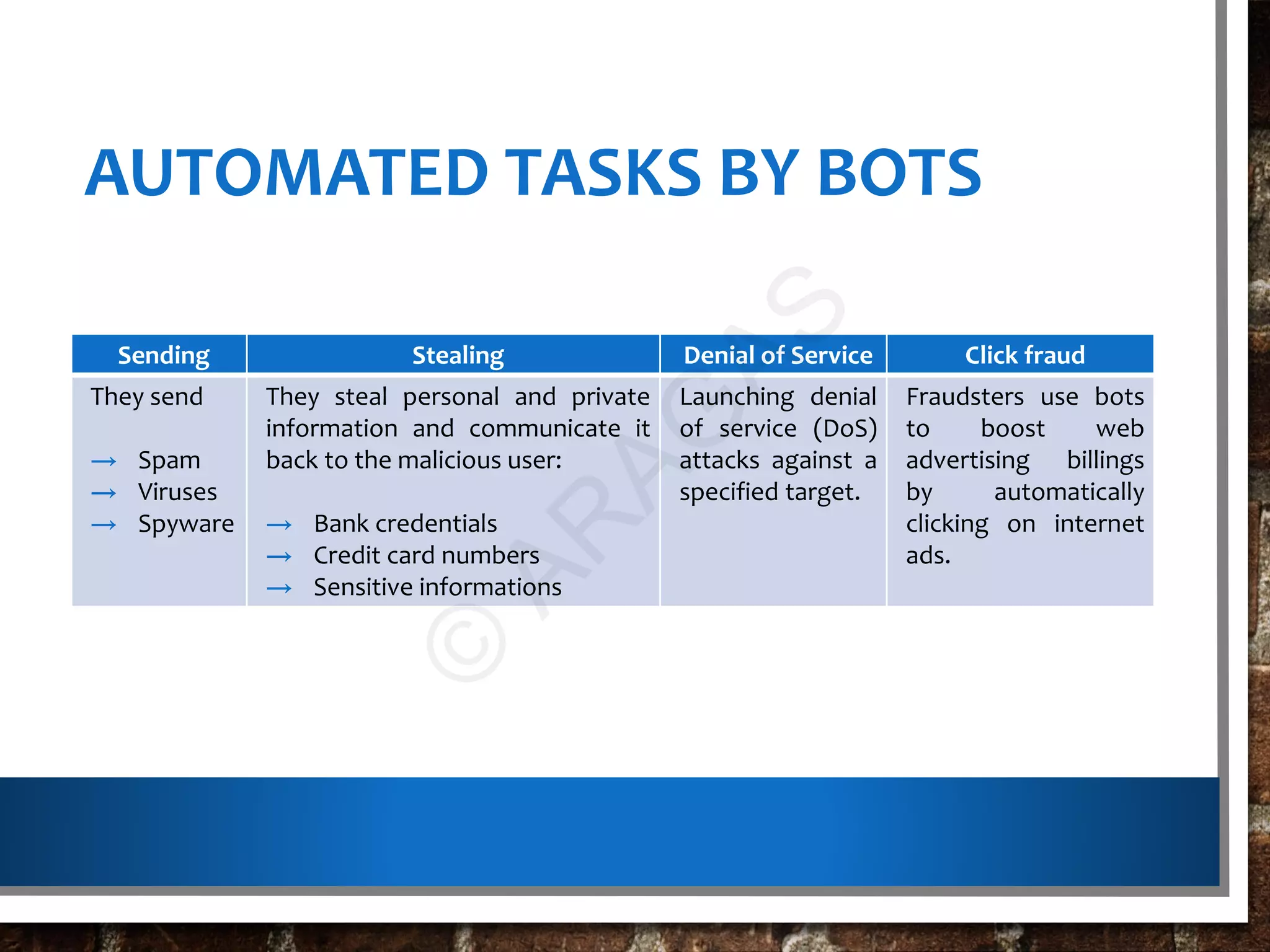
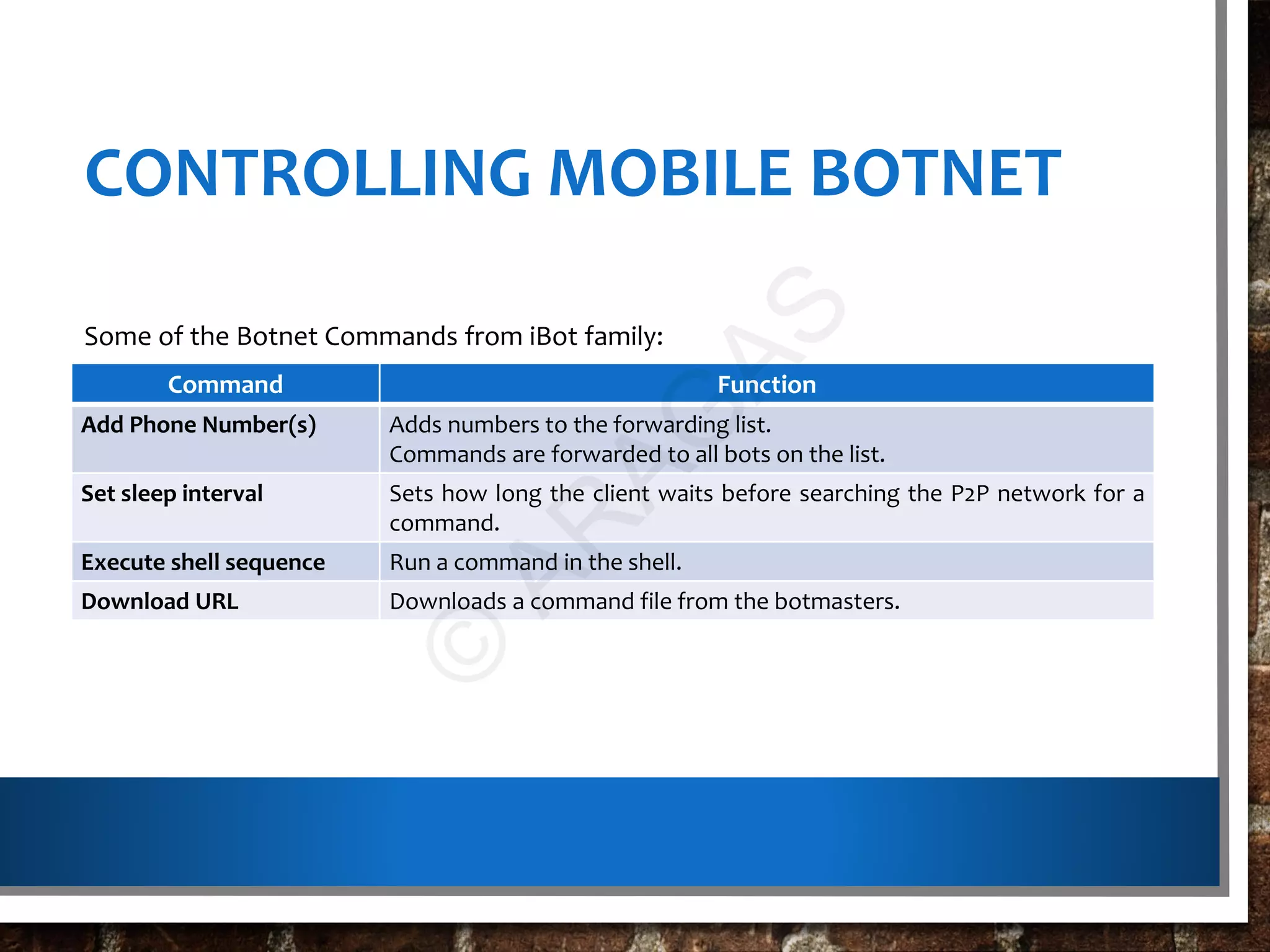
This document discusses botnets, which are networks of compromised computers controlled by cybercriminals without the owners' knowledge. Botnets are created using malware that turns computers into "bots" which can be instructed to perform tasks like sending spam or launching cyberattacks. The document describes how botnets are built, classified, and used illegally for crimes. It also provides information on protecting against and detecting bot infections on computers and mobile devices.