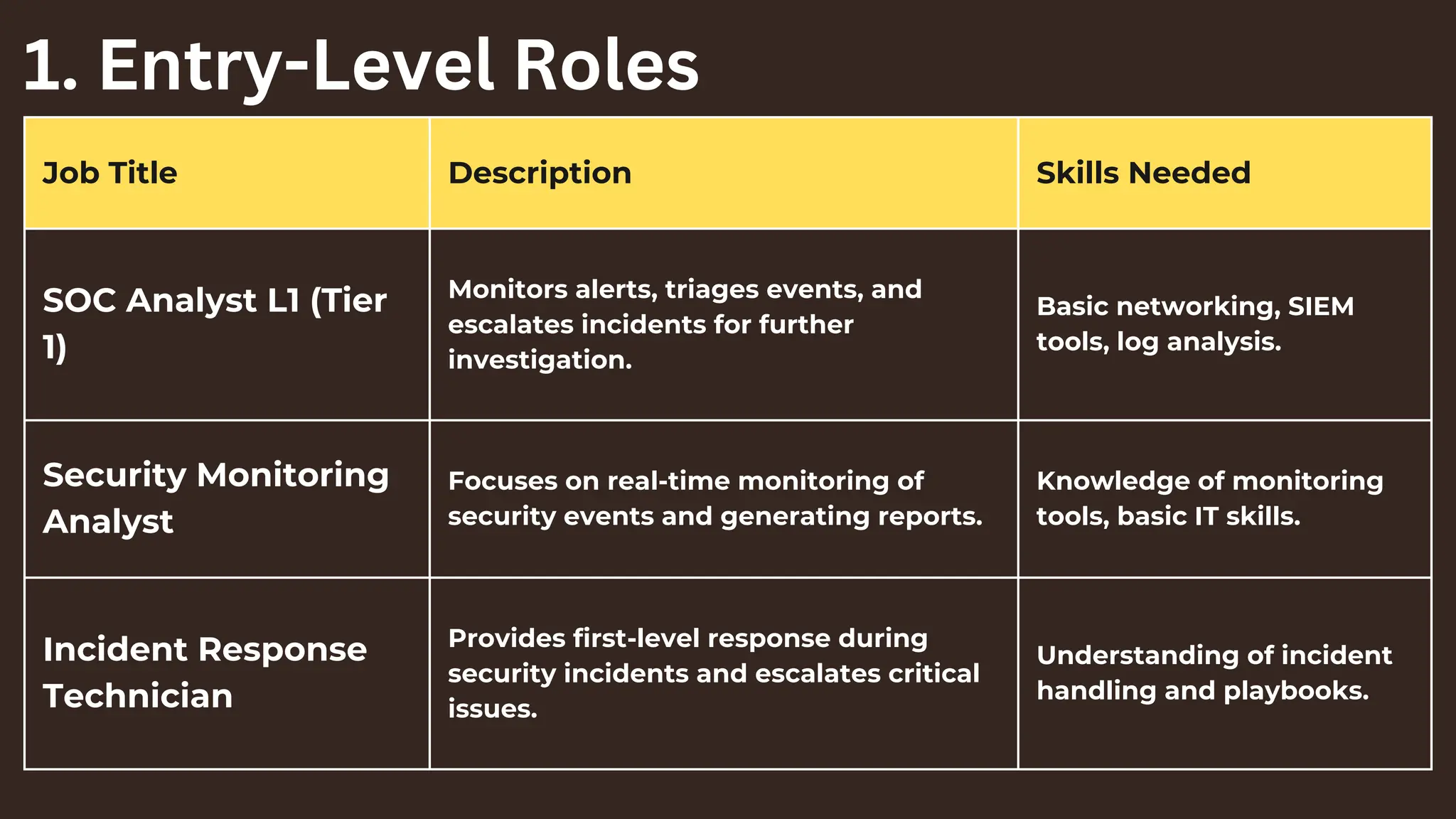
The document outlines various security operations center (SOC) career opportunities for 2025, categorized into entry-level, mid-level, advanced, management, and specialized roles. Each role includes a job title, description, and required skills, ranging from SOC analysts and incident response technicians to roles like cybersecurity operations director and AI/ML security specialists. The content emphasizes the necessary skills and expertise for success in different positions within the cybersecurity field.