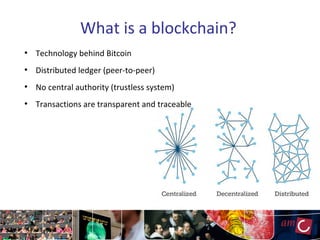
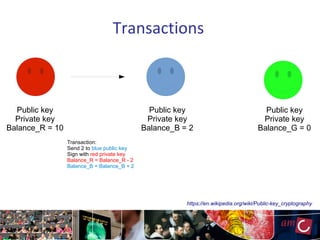
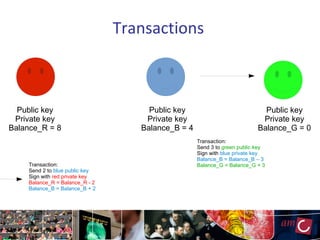
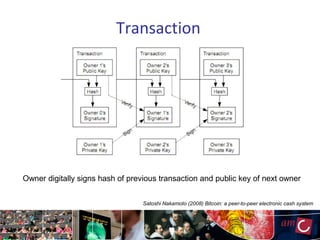
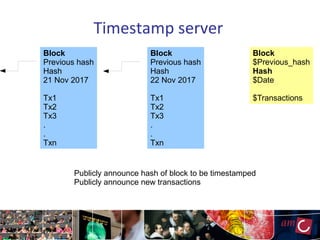
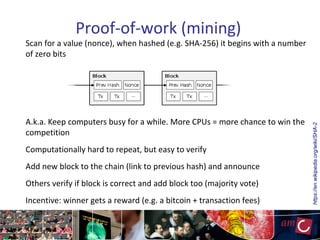
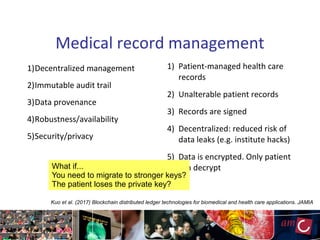
The document provides an overview of blockchain technology, focusing on its mechanisms, strengths, weaknesses, and applications, particularly in life sciences. It touches upon decentralized management, immutable audit trails, and the potential for enhanced data security in sectors like healthcare and education. It also highlights current research areas and practical implementations while discussing challenges and best practices to avoid ineffective blockchain projects.